A memory management method and system
A memory management and memory technology, applied in the Internet field, can solve problems such as insufficient memory
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0067] According to an embodiment of the present invention, an embodiment of a memory management method is provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, although A logical order is shown in the flowcharts, but in some cases the steps shown or described may be performed in an order different from that shown or described herein.
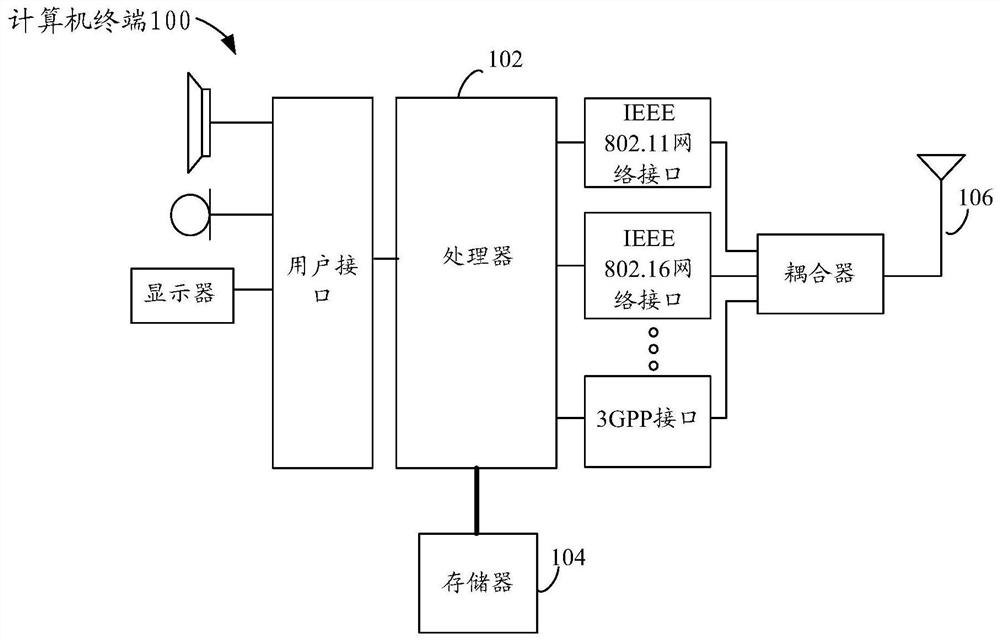
[0068] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, figure 2 It is a block diagram of the hardware structure of the computer terminal according to the memory management method of the embodiment of the present invention. Such as figure 2 As shown, the computer terminal 100 may include one or more (only one is shown in the figure) processors ...
Embodiment 2
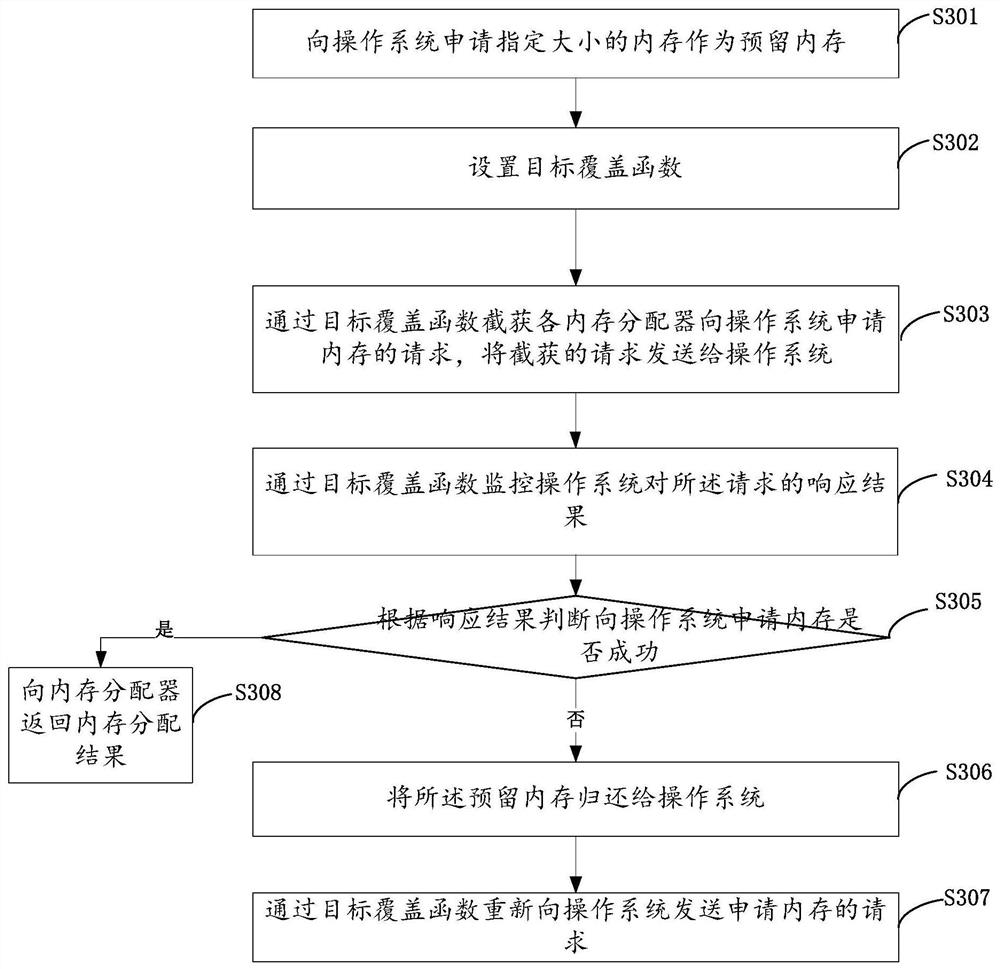
[0098] Such as Figure 5 As shown, the present invention provides another memory management method, including:
[0099] Step S501 , applying to the operating system for memory of a specified size as reserved memory.
[0100] Step S502, setting a target coverage function.
[0101] Step S503, intercepting requests from memory allocators to the operating system to apply for memory through the target overlay function, and sending the intercepted requests to the operating system.
[0102] Step S504, monitor the response result of the operating system to the request through the target coverage function.
[0103] Step S505, judging whether the memory application to the operating system is successful according to the response result. If applying for memory from the operating system fails, execute step S506, and if successful, execute step S508.
[0104] Step S506, returning the reserved memory to the operating system.
[0105]Step S507, resending the request for memory applicatio...
Embodiment 3
[0153] Such as Figure 6 As shown, the present invention also provides a memory management system, comprising:
[0154] The reserved memory application module 601 is used to apply to the operating system for memory of a specified size as reserved memory;
[0155] A target coverage function setting module 602, configured to set a target coverage function;
[0156] The request interception module 603 is used to intercept each memory allocator's request for memory from the operating system through the target coverage function, and sends the intercepted request to the operating system; the response monitoring module is used to monitor the operating system's response to the operating system through the target coverage function. The response result of the request;
[0157] A judging module 604, configured to judge whether the memory application to the operating system is successful according to the response result;
[0158] A reserved memory returning module 605, configured to re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com