A mobile app push data collection method and terminal
A collection method and collection terminal technology, applied in the Internet field, can solve the problems of mobile terminal security that need to be investigated, and achieve good security controllability, high versatility, and various types of effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
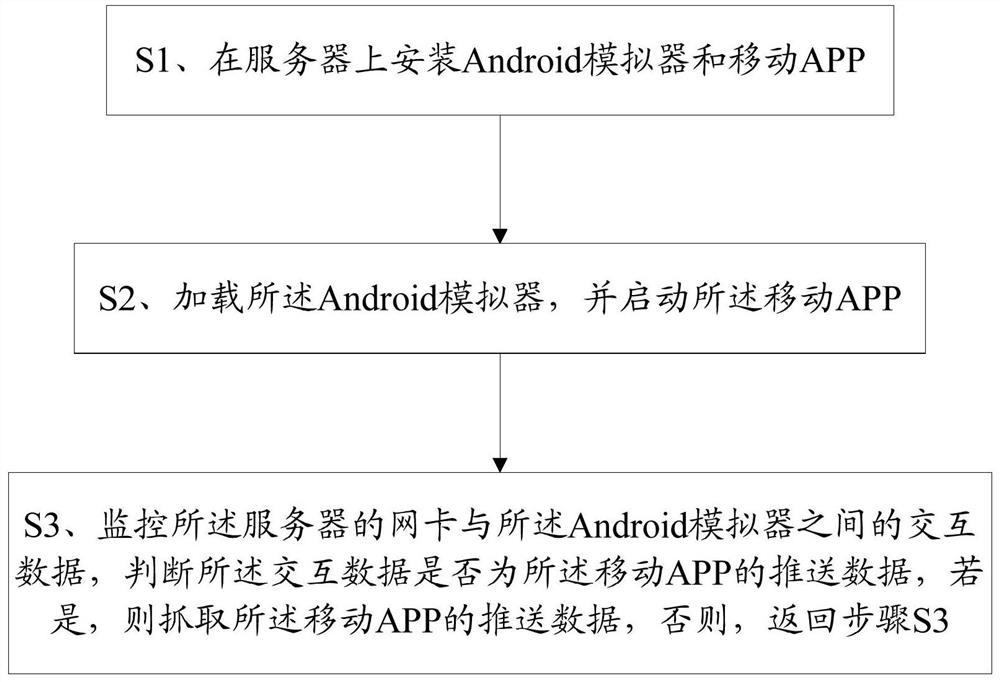
[0063] Please refer to figure 1 , a method for collecting mobile APP push data, comprising the steps of:
[0064] S1, Android emulator and mobile APP are installed on the server;
[0065] Among them, the Android emulator is used as the carrier of the APP, and the mobile APP that needs to be pushed to collect data is installed. The Android emulator can be an official emulator version, compatible with most APPs, or a customized emulator, including Android native emulator SDK, Android emulators issued by various other manufacturers, etc., after installation, configure the running port and firewall settings of the Android emulator on the server;
[0066] After installing the mobile APP, initialize the collection service, including presetting the header and tail markers of various push data packets;
[0067] S2, loading the Android emulator, and starting the mobile APP;
[0068] Run the mobile APP specified in the emulator through the ADB command line;
[0069] S3. Monitoring t...
Embodiment 2
[0082] The difference between the described embodiment and the first embodiment is that: when performing the initialization collection service, data decryption information is included;
[0083] When the push data of the mobile APP is captured, it is judged whether the captured push data belongs to the push data of the APP in the preset encrypted push APP list, and if so, the push data is decrypted according to the data decryption information After decryption, it is parsed.
Embodiment 3
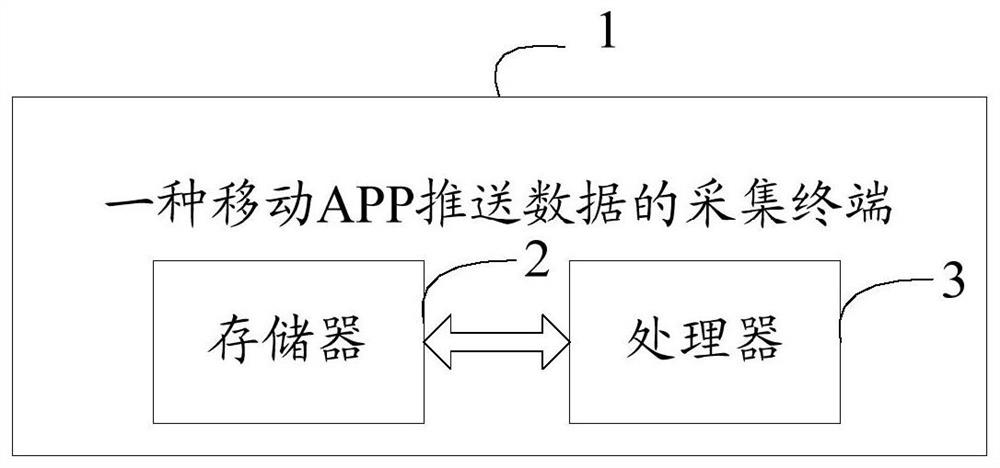
[0085] Please refer to figure 2 , a collection terminal 1 for mobile APP pushing data, including a memory 2, a processor 3, and a computer program stored on the memory 2 and operable on the processor 3, and the processor 3 executes the computer program The steps in the first embodiment are realized during the program.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com