Anti-leakage group key negotiation system and method in group communication
A group communication and key negotiation technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as incomplete side channel key leakage, achieve no hardware support, high practicability, and use convenient effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to facilitate those of ordinary skill in the art to understand and implement the present invention, the present invention will be further described in detail below in conjunction with the accompanying drawings and examples. It should be understood that the implementation examples described here are only used to illustrate and explain the present invention, and are not intended to limit this invention.
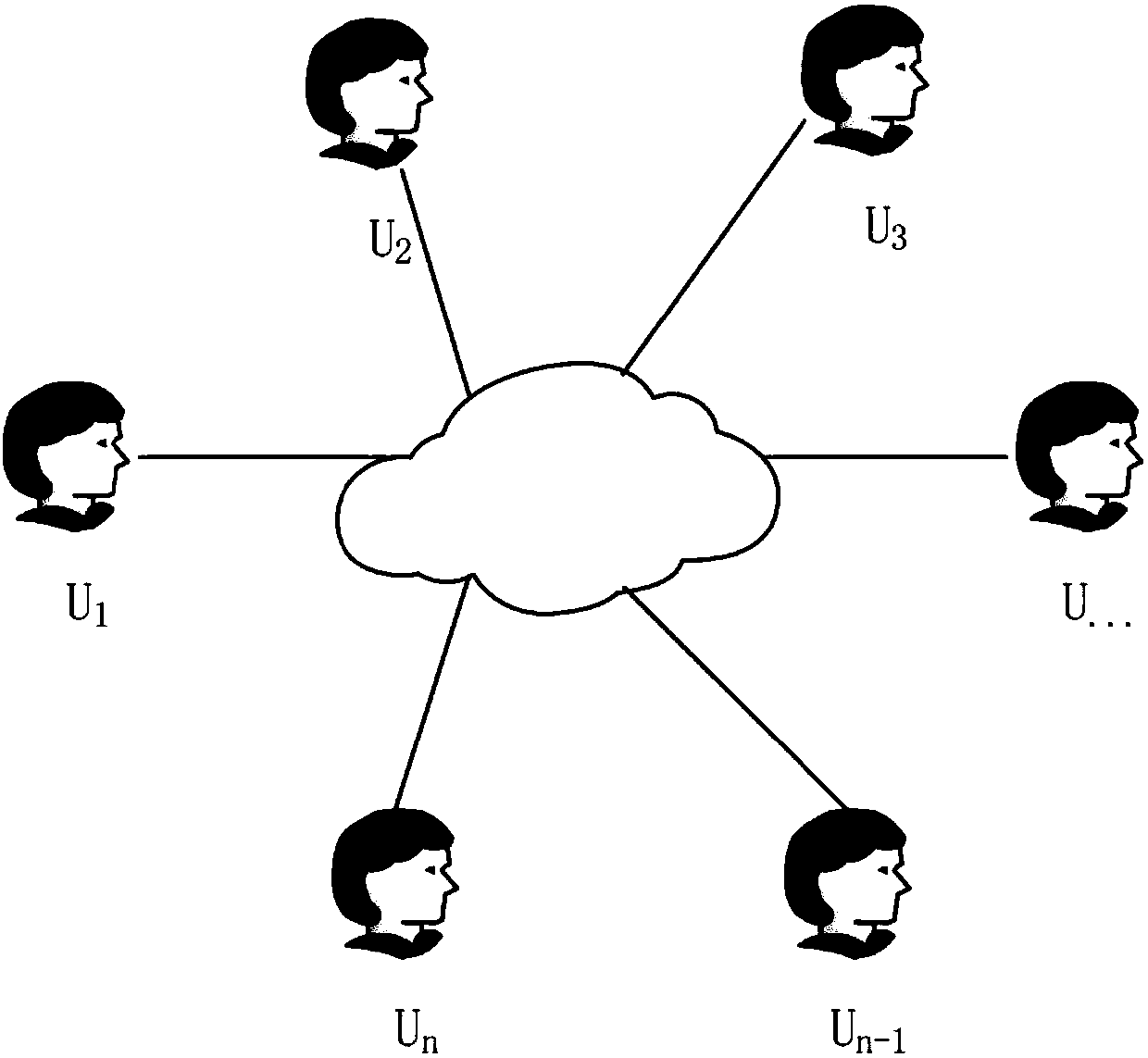
[0034] please see figure 1 , an anti-leakage group key negotiation system in group communication provided by the present invention, the system has n users, and all users share a password pw; Random oracle; protocol participants are networked devices participating in the protocol; the adversary is a probabilistic polynomial time algorithm, through which to simulate various attacks that may occur in the network; random oracle simulates the adversary's possible attacks in the network through communication with the adversary information obtained.
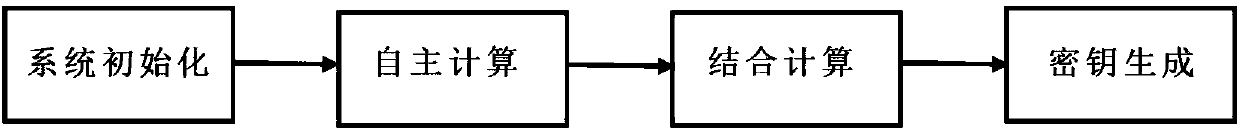
[0035] please s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com