Implementation method and device for generating key pair in embedded system
An embedded system, a technology for generating keys, applied in the field of information security, which can solve problems such as hidden dangers and irresistibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
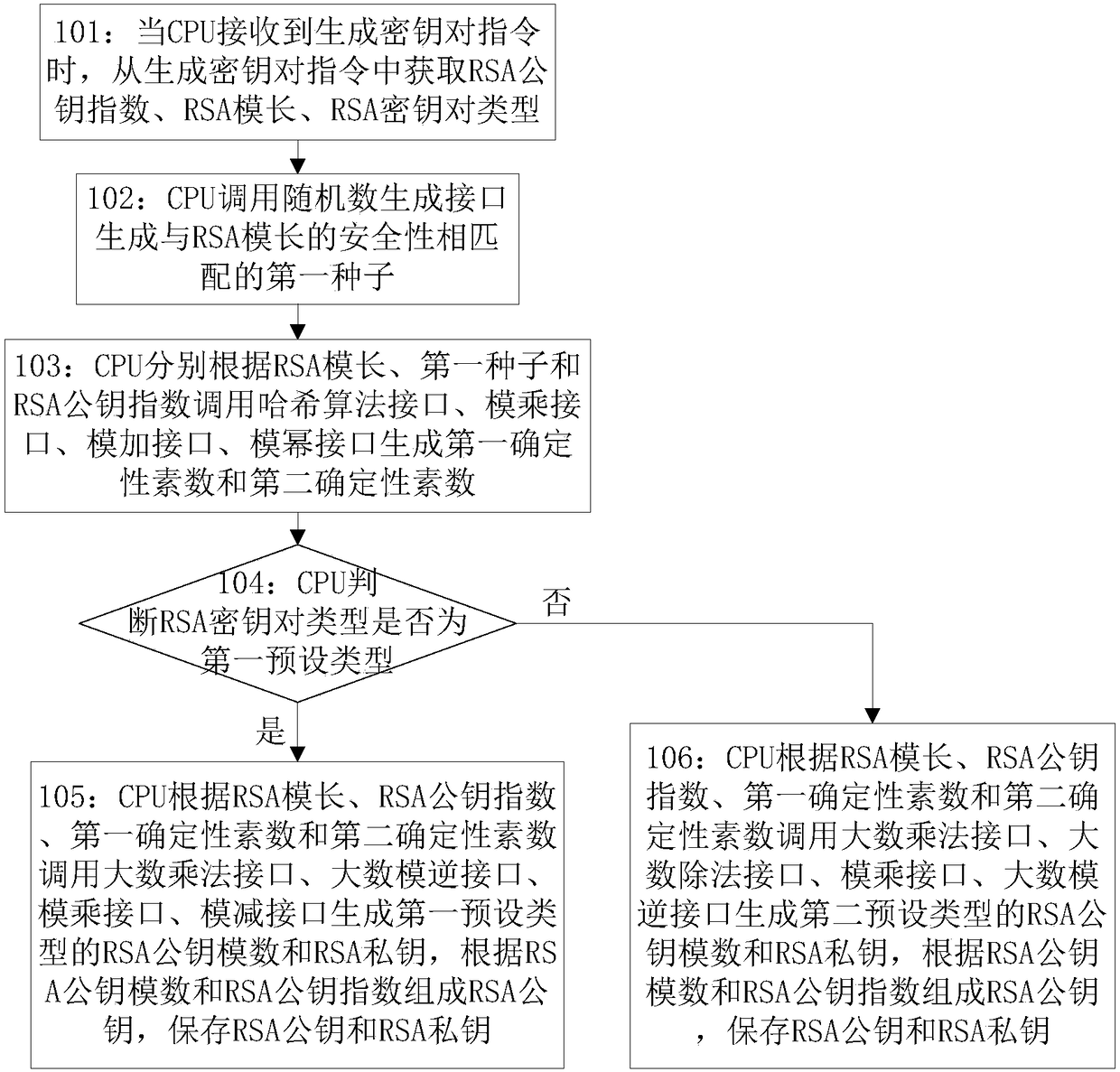
[0139] Embodiment 1 of the present invention provides an implementation method for generating a key pair, such as figure 1 shown, including:
[0140] Step 101: when the CPU receives the command to generate a key pair, obtain the RSA public key index, RSA modulus length, and RSA key pair type from the command to generate a key pair;
[0141] For example, the RSA module length in this embodiment is 1024, the RSA public key index is 0x010001, and the RSA key pair type is the CRT type;
[0142] Step 102: the CPU invokes the random number generation interface to generate the first seed matching the security of the RSA modulus length;
[0143] For example, the first seed generated in this embodiment is 0x1111111111111111111111111111111111111;
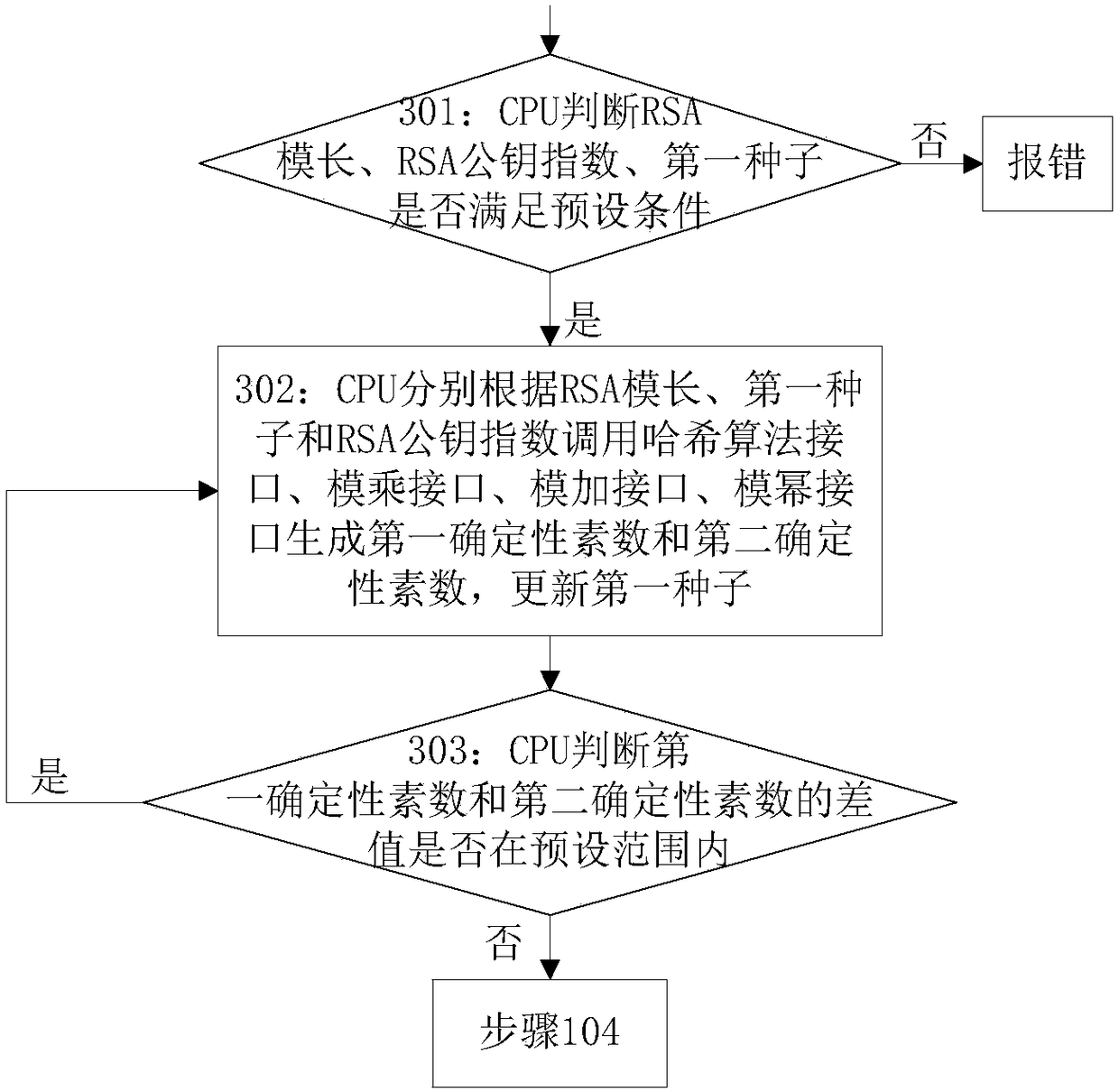
[0144] In this embodiment, step 102 includes:
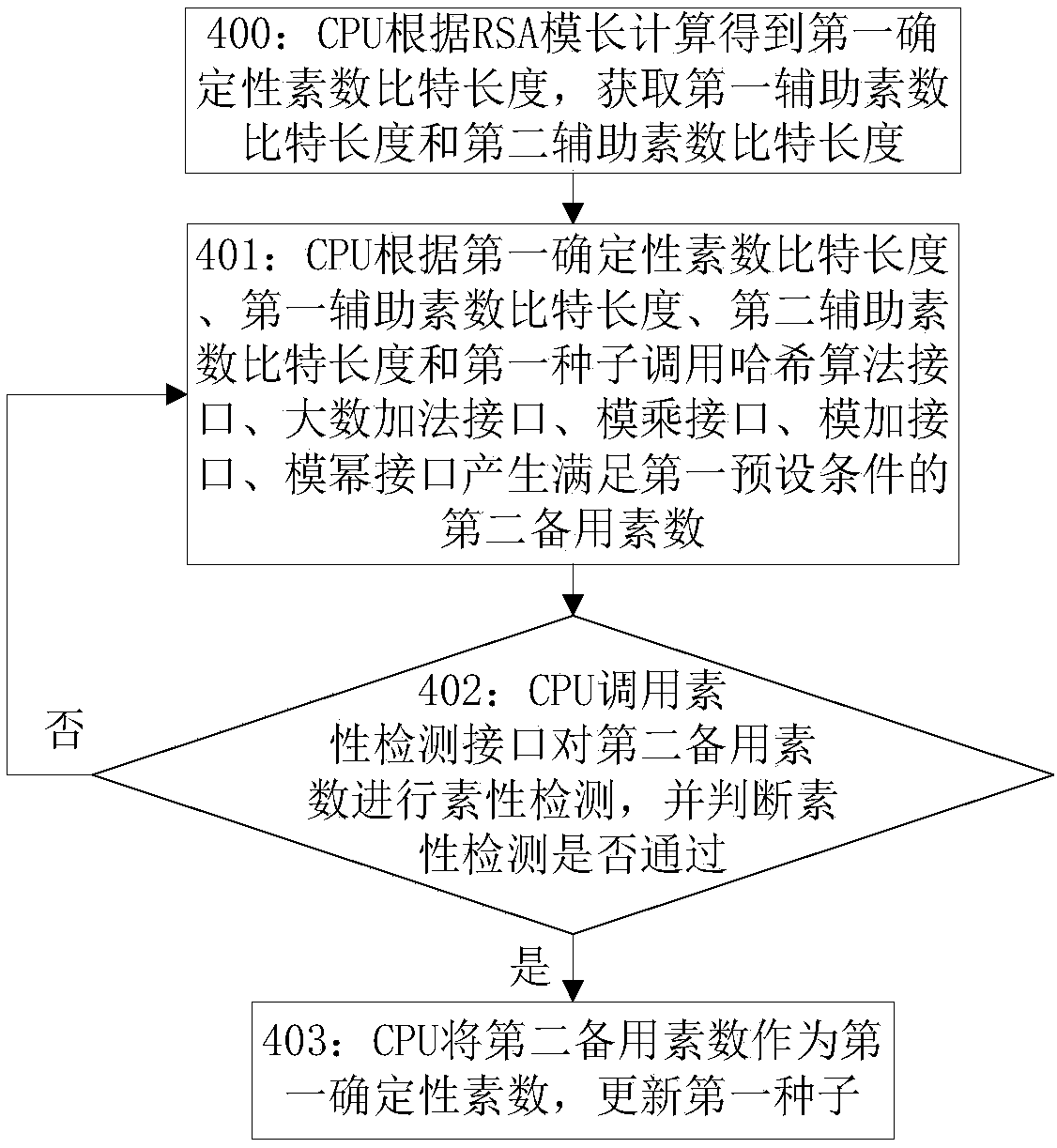
[0145] Step 201: the CPU calculates the security bit strength of the RSA algorithm according to the RSA modulus length;
[0146] For example, the security bit strength in this embodiment is ...
Embodiment 2
[0245] Embodiment 2 of the present invention provides an implementation device for generating a key pair in an embedded system, such as Figure 6 shown, including:
[0246] The first obtaining module 601 is used to obtain the RSA public key index, RSA modulus length, and RSA key pair type from the generating key pair instruction when receiving the generating key pair instruction;
[0247] The first generation module 602 is used to call the random number generation interface to generate the first seed that matches the security of the RSA modulus length;
[0248] Specifically, the first generating module 602 in this embodiment includes:
[0249] The first calculation submodule is used to calculate the security bit strength of the RSA algorithm according to the RSA modulus length;
[0250] The first generation submodule is used to call the random number generation interface to generate the first seed corresponding to the security bit strength of the RSA algorithm.
[0251] The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com