Network attack prevention phantom device establishment method, medium and device
A network attack and establishment method technology, applied in the field of network security, can solve the problems that traps are easily bypassed, camouflage technology cannot camouflage well, and personnel security professional technical requirements are high.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
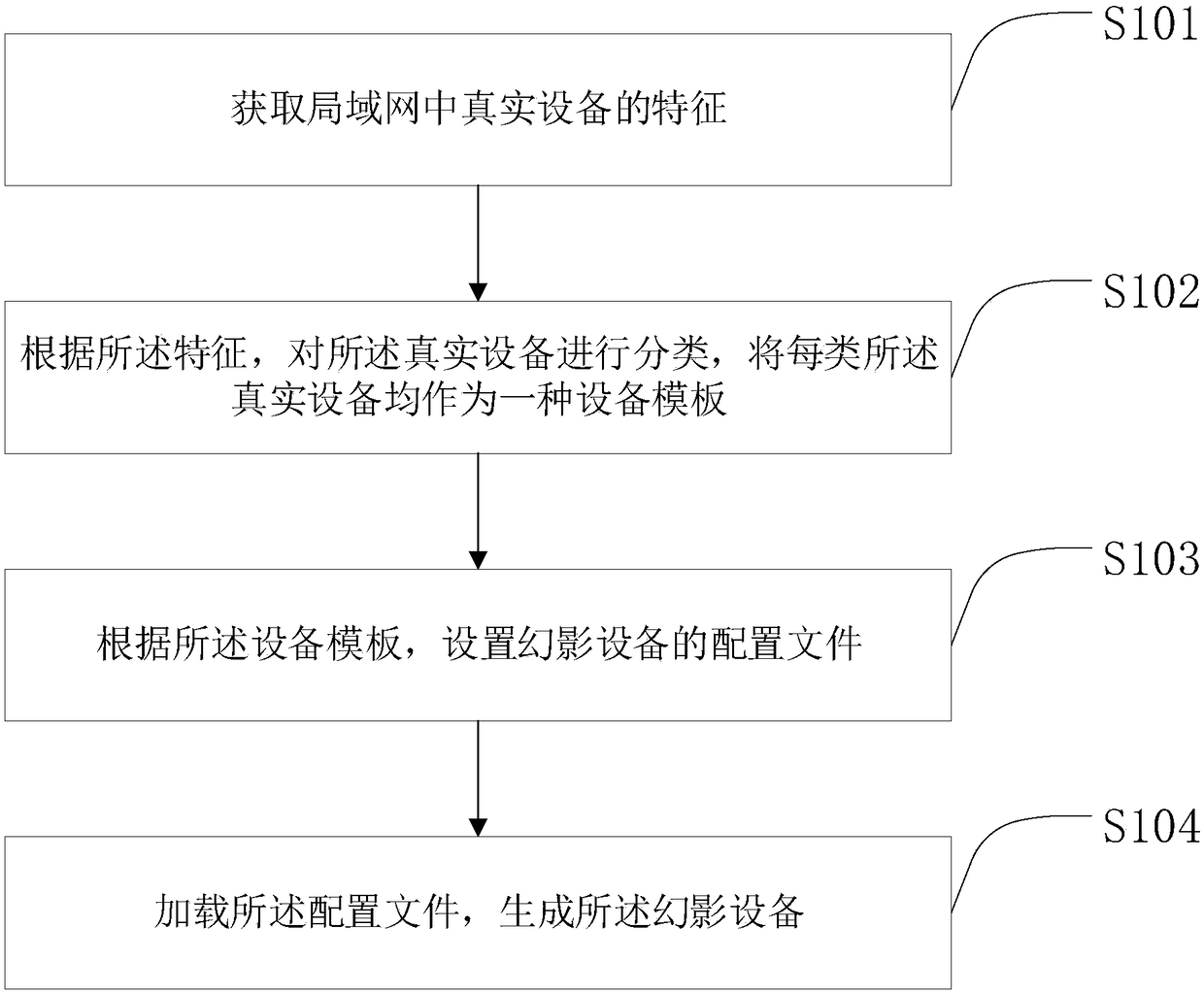
[0054] Please refer to figure 1 , figure 1 It is a flow chart of a method for establishing a phantom device against network attack provided by a specific embodiment of the present invention. The method for establishing a phantom device against network attack provided by this embodiment includes:
[0055] Step S101: Obtain features of real devices in the local area network.
[0056] Step S102: Classify the real devices according to the features, and use each type of real devices as a device template.
[0057] Step S103: Set the configuration file of the phantom device according to the device template.
[0058] Step S104: Load the configuration file to generate the phantom device.
[0059] Wherein, the feature may include: device type, operating system, operating system fingerprint, open port, vendor feature, and the like.
[0060] Classify each real device in the LAN according to its characteristics, and a category corresponds to a device template. For example, one operati...
no. 2 example
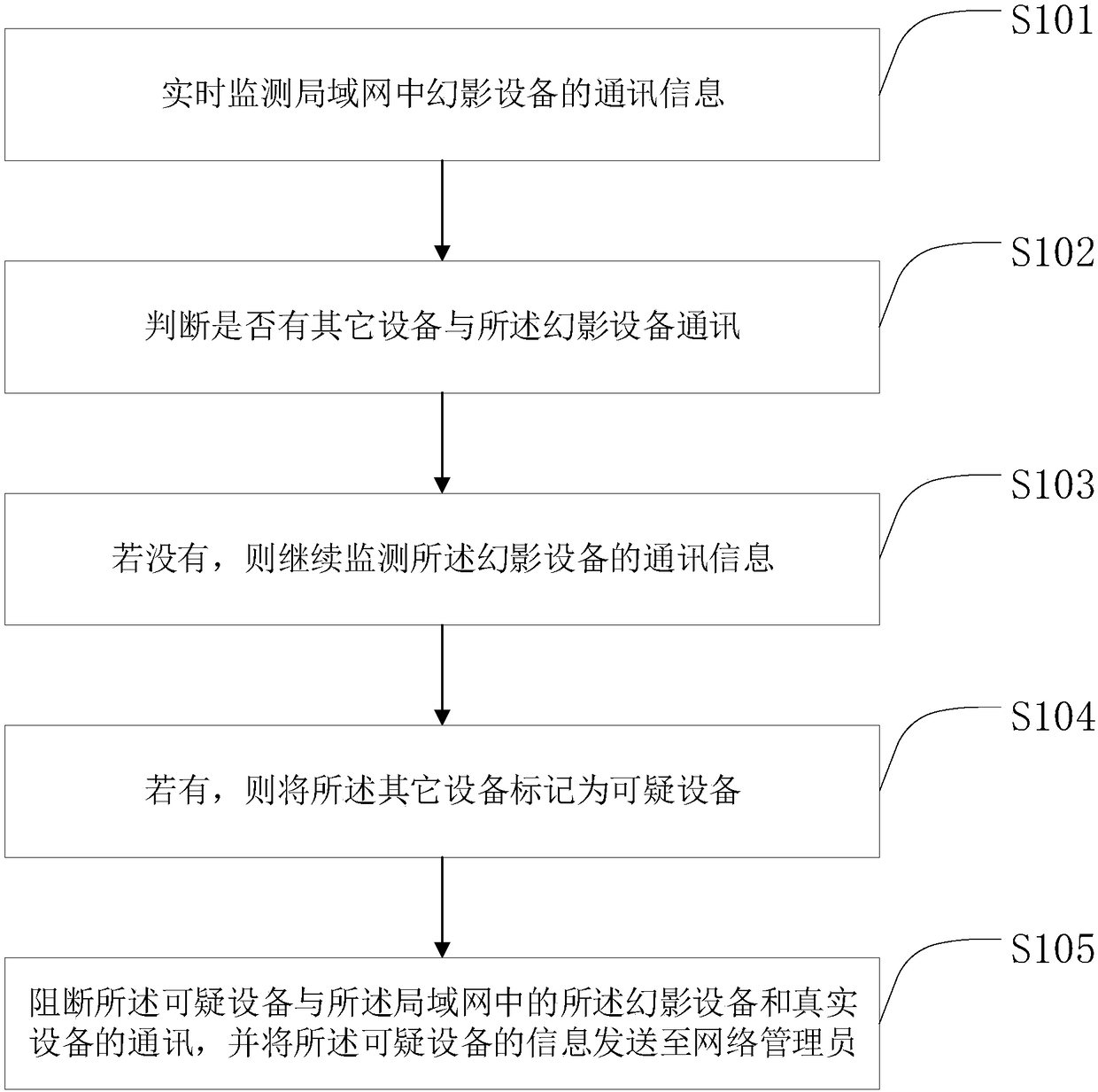
[0092] The present invention corresponding to the first embodiment also provides a method for preventing network attacks, please refer to figure 2 , which is a schematic diagram of a method for preventing network attacks provided by an embodiment of the present invention.
[0093] A method for preventing network attacks provided by the second embodiment of the present invention includes:
[0094] Step S101: Monitor the communication information of the phantom device in the local area network in real time; wherein, the phantom device is established by the method described in the first embodiment;
[0095] Step S102: judging whether there are other devices communicating with the phantom device;
[0096] Step S103: If not, continue to monitor the communication information of the phantom device;
[0097] Step S104: If yes, mark the other devices as suspicious devices;
[0098] Step S105: blocking the communication between the suspicious device and the phantom device and the re...
no. 3 example
[0108] In the above-mentioned first embodiment, a method for establishing a phantom device for preventing network attacks is provided. In combination with the above-mentioned first embodiment, the third embodiment of the present invention provides a computer-readable storage medium on which a computer program is stored. When the program is executed by the processor, the method for establishing a phantom device for preventing network attacks provided by the above-mentioned first embodiment is implemented.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com