Bluetooth pairing code allocation method, system, terminal, server and vehicle-mounted device
A Bluetooth pairing and cloud server technology, applied in the field of Bluetooth pairing, can solve the problems of weak anti-DOS attack ability, poor security, cumbersome operation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
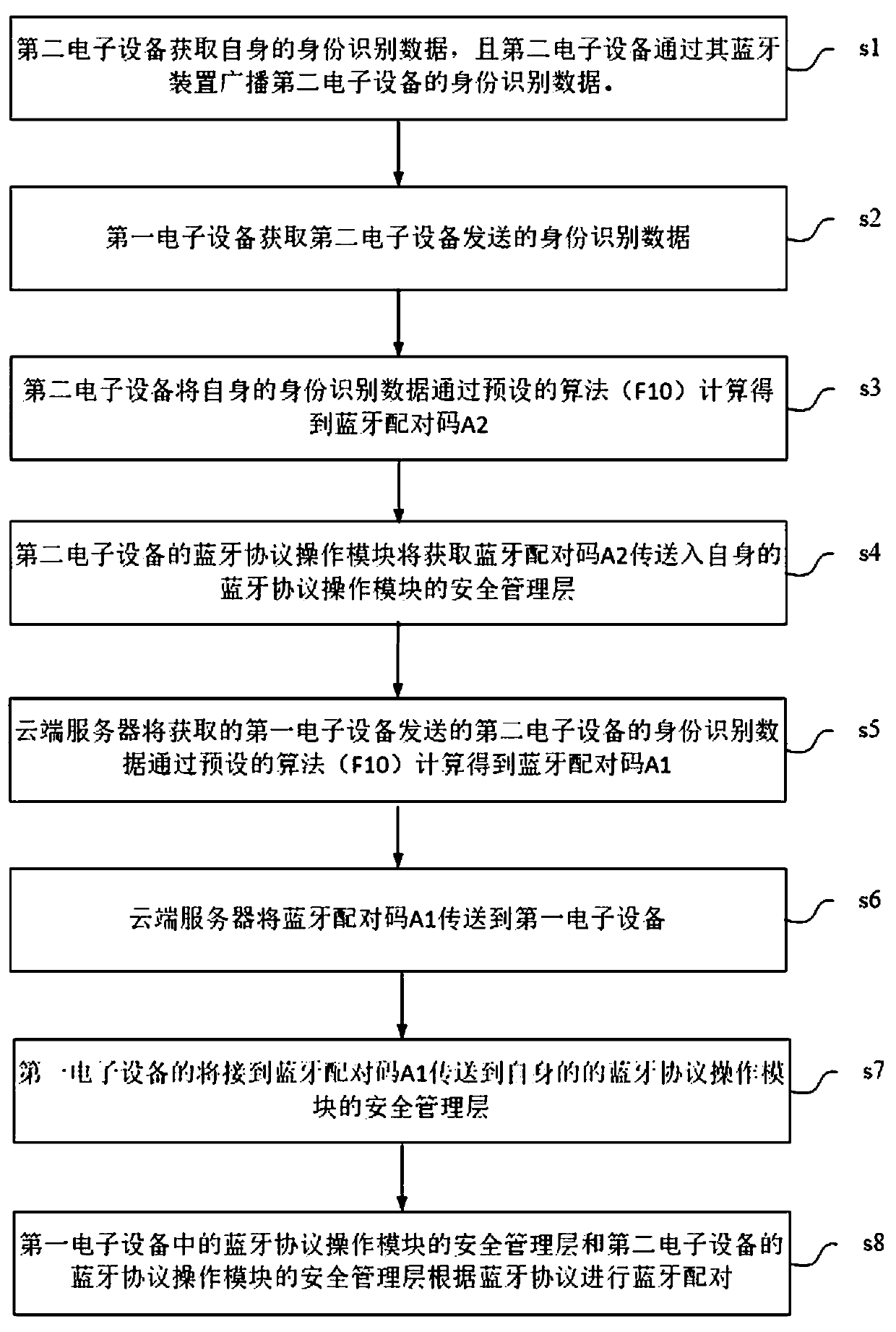
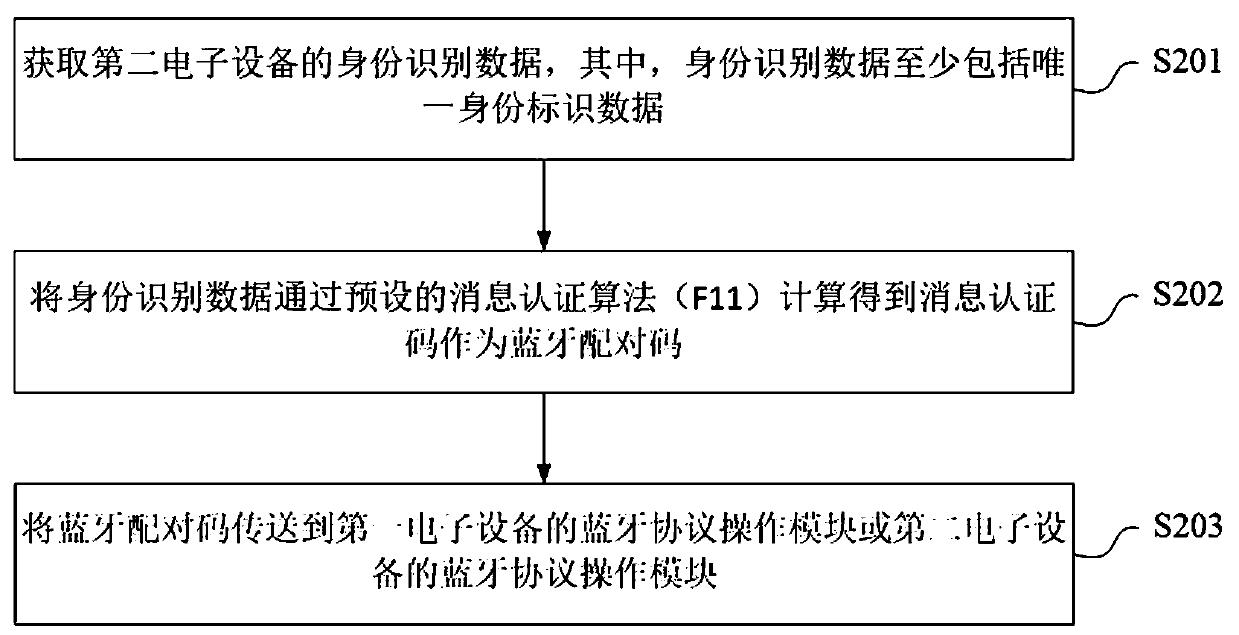
[0071] Implemented using one-way hash functions such as SHA-1, MD5, and HMAC, a message digest is obtained as a message authentication code.
[0072] In the specific implementation process, for example: HMAC calculates an example of message authentication code MAC1: MAC1 = HMAC(K1,IN); HMAC is a key-related hash operation, which takes a key and a message as input and generates a message digest as output. K1 is a message authentication key here. In the one-way hash function, the message authentication key is only used to input the parameters involved in the calculation, not as a real key. The final output message authentication code MAC1 is discrete Factor, which can be passed IN as the ID code is an input message.
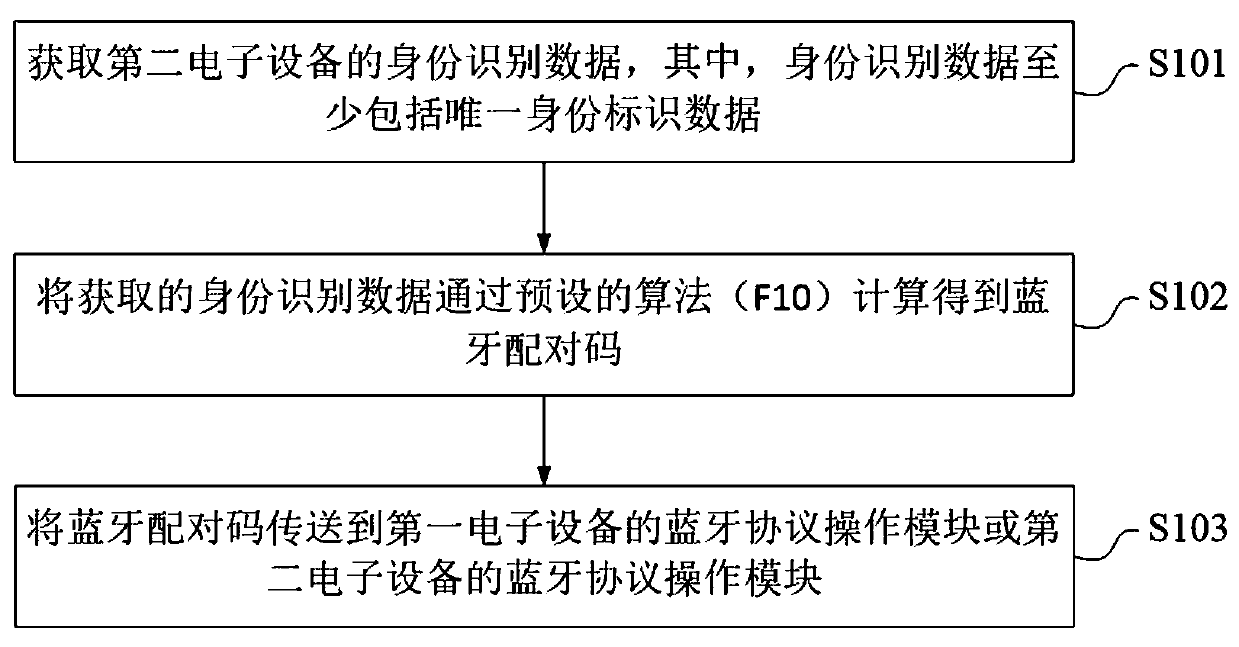
[0073] S203: Send the Bluetooth pairing code to the Bluetooth protocol operation module of the first electronic device or the Bluetooth protocol operation module of the second electronic device.
[0074] Preferably, step S202 further includes:
[0075] Obtain a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com