Network token generation method and device, terminal equipment and storage medium
A token and network technology, applied in the field of network token generation, can solve the problems of inability to store user sensitive data, low security of technical specifications, and achieve the effect of enhancing authenticity and uniqueness, ensuring security and exclusivity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
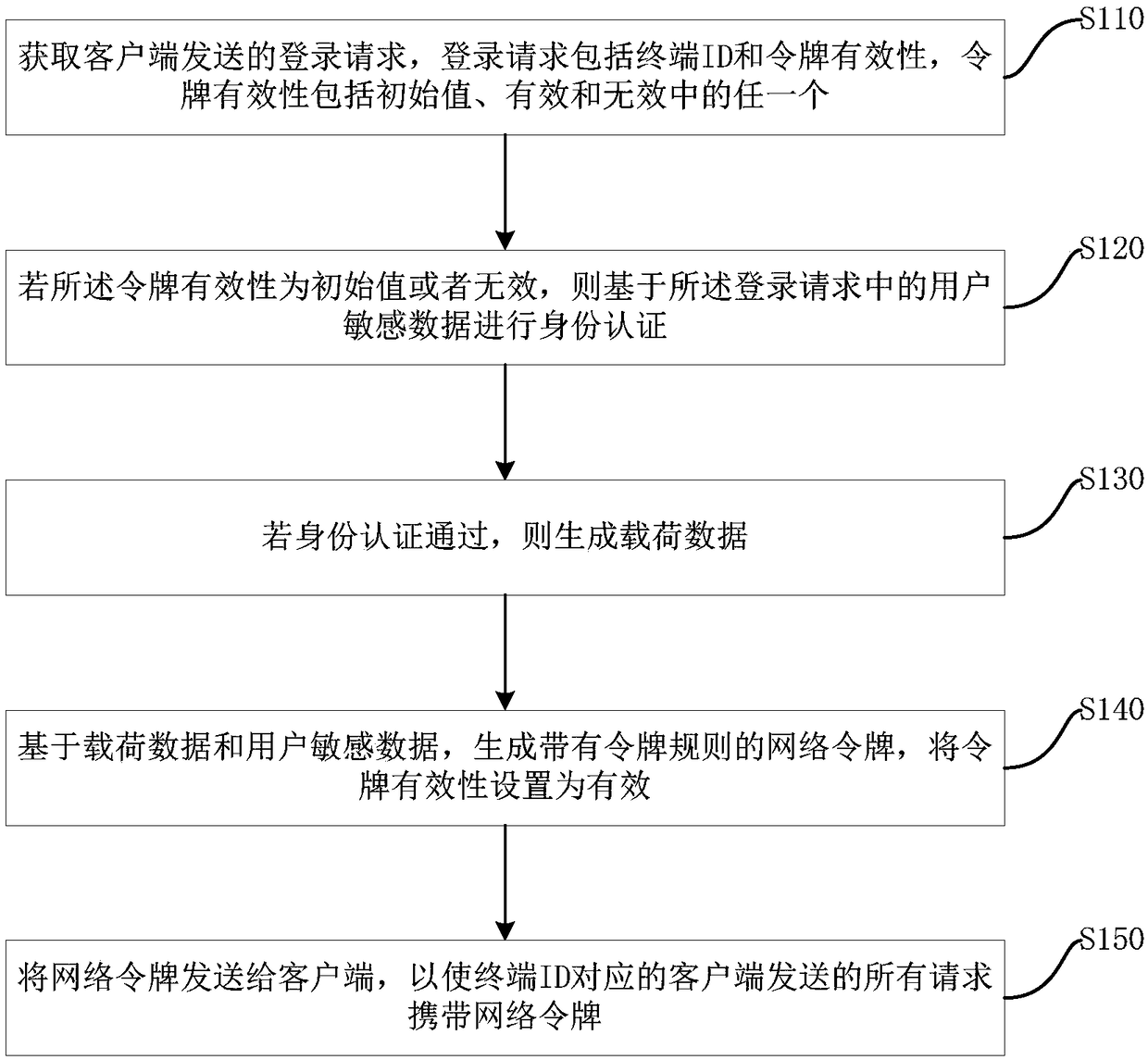
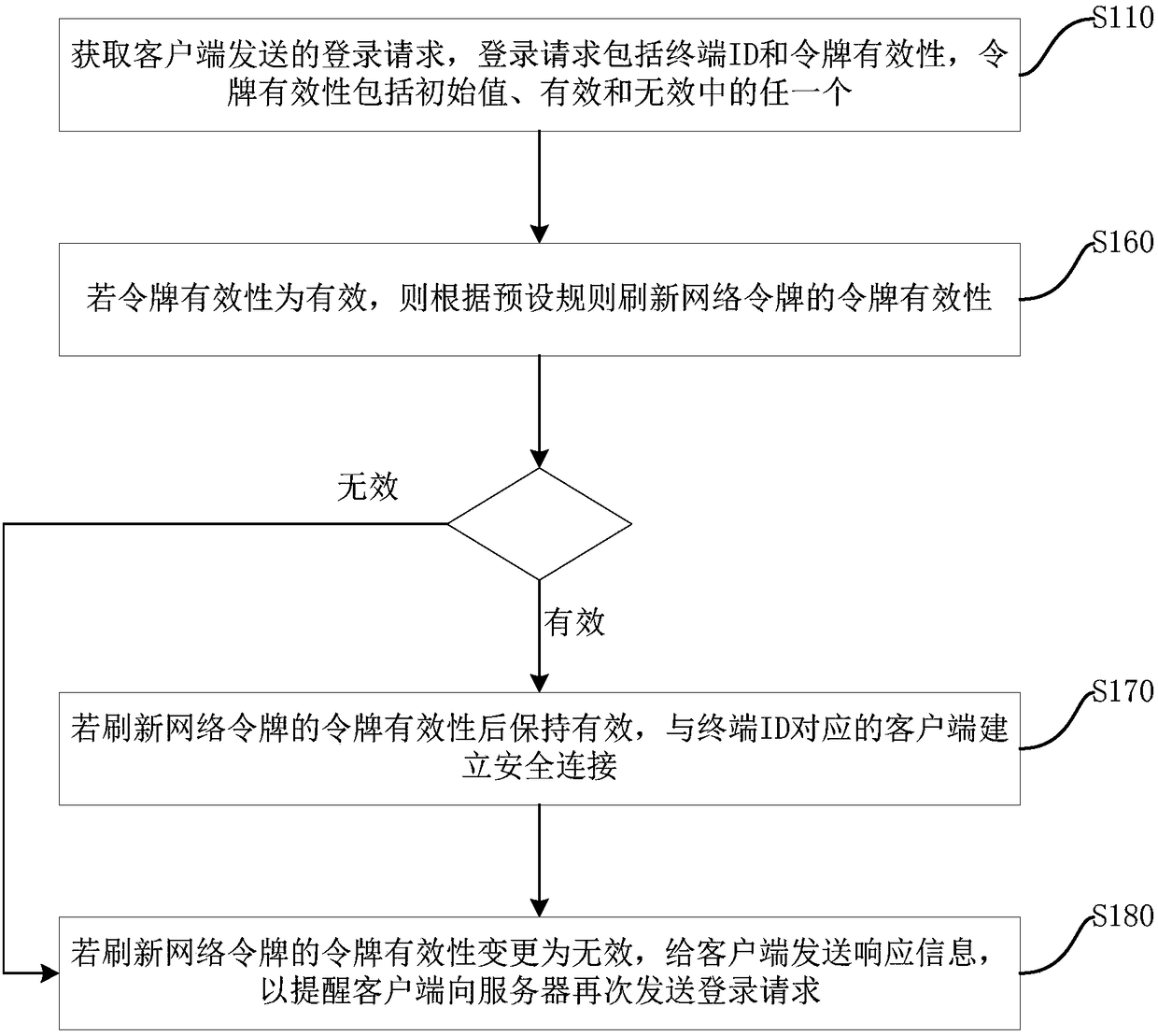
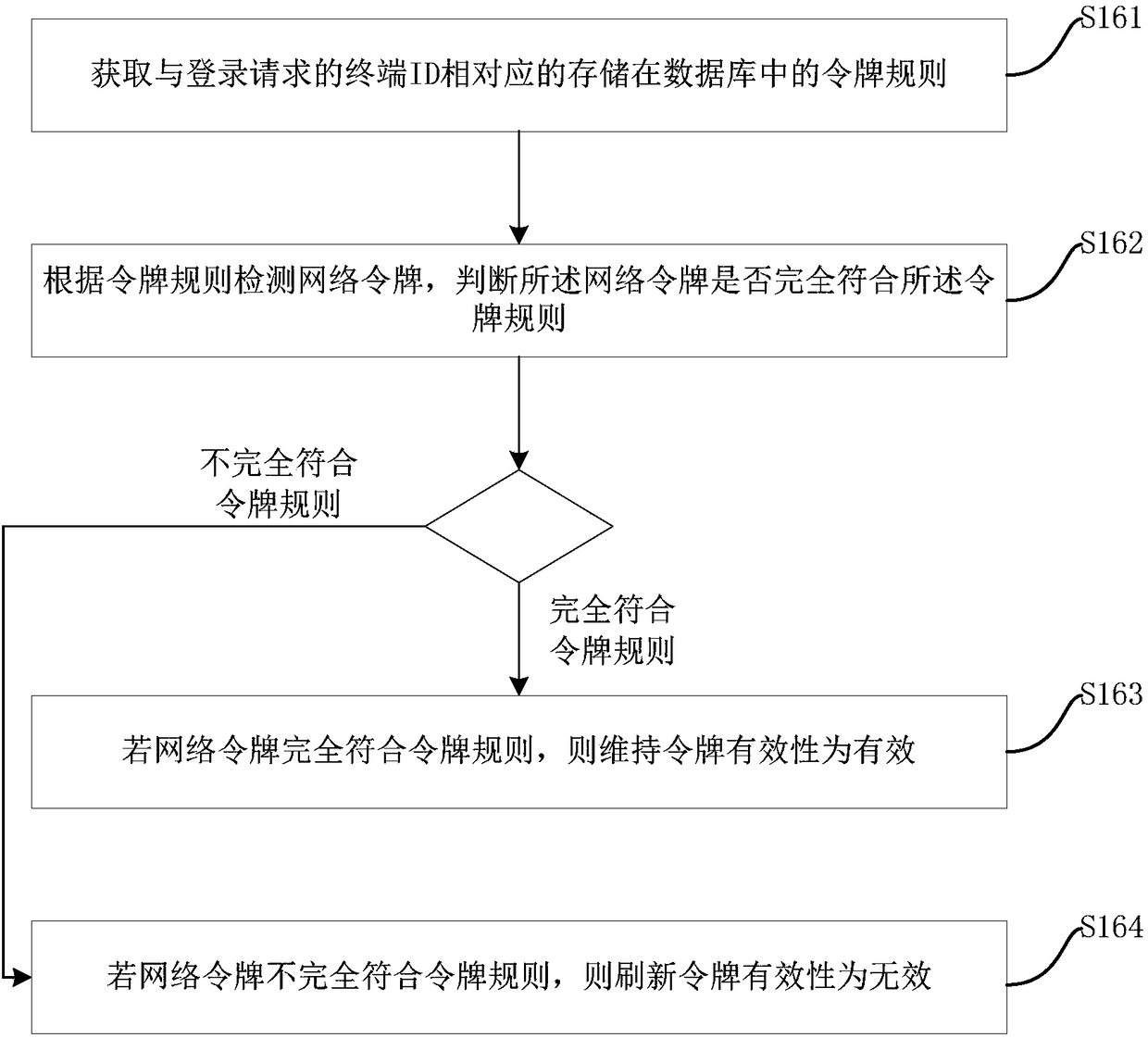
[0031] figure 1 A flowchart showing the method for generating a network token in this embodiment. Web Tokens are a compact, URL-safe specification of representational claims for passing security information between clients and servers. The method for network token generation is applied on the server. Such as figure 1 As shown, the method for generating a network token includes the following steps:
[0032] S110. Obtain a login request sent by the client, where the login request includes a terminal ID and token validity, and the token validity includes any one of an initial value, valid and invalid.
[0033] Specifically, the login request is a request sent by the client when connecting to the server through a browser or a third-party interface.
[0034] The terminal ID is used to uniquely identify the client that sends the login request. The terminal ID can be the login IP used by the client to connect to the server or the hardware MAC address of the client, depending on t...
Embodiment 2
[0143] Figure 7 A functional block diagram of a device for generating a network token corresponding to the method for generating a network token in Embodiment 1 is shown. A Web Token is a concise, URL-safe representation specification for passing security information between a client and a server. The device for generating the network token is applied on the server. Such as Figure 7 As shown, the device for generating a network token includes an acquisition login request module 110 , an identity authentication module 120 , a payload data generation module 130 , a network token generation module 140 , and a network token sending module 150 . Wherein, the realization functions of the obtaining login request module 110, performing the identity authentication module 120, generating the load data module 130, generating the network token module 140 and sending the network token module 150 correspond to the steps of the method for generating the network token in Embodiment 1 One...
Embodiment 3
[0174] This embodiment provides a computer-readable storage medium, and a computer program is stored on the computer-readable storage medium. When the computer program is executed by a processor, the method for generating a network token in Embodiment 1 is implemented. To avoid repetition, it is not repeated here repeat. Alternatively, when the computer program is executed by the processor, the functions of the modules / units in the device for generating network tokens in Embodiment 2 are implemented. To avoid repetition, details are not repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com