Authentication certificate generation method based on block chain
A certificate generation and blockchain technology, applied in user identity/authority verification, digital transmission systems, electrical components, etc., can solve problems such as malicious attacks, attacks, and man-in-the-middle attacks, to ensure consistency, improve stability, and verify Effect of increased speed and communication speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
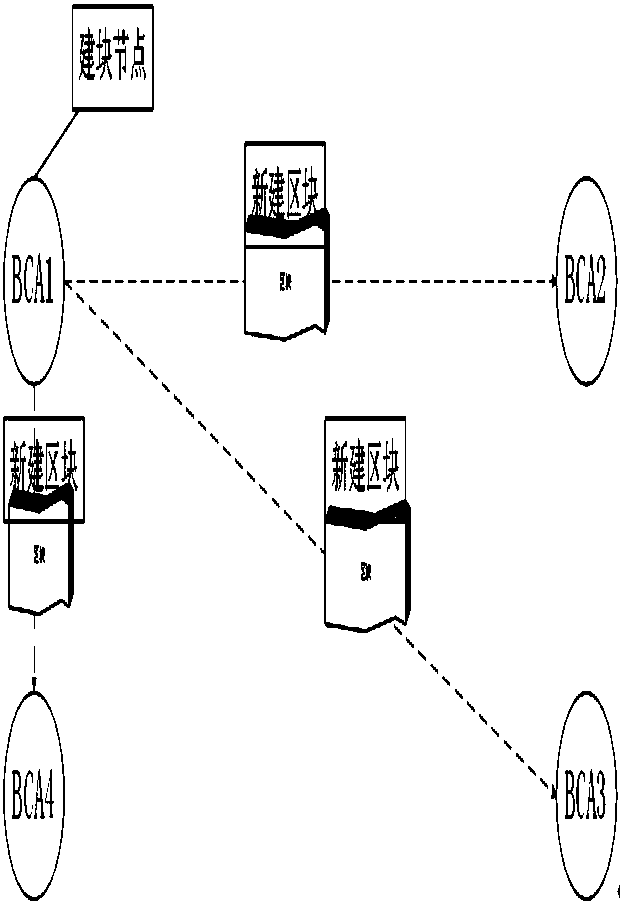
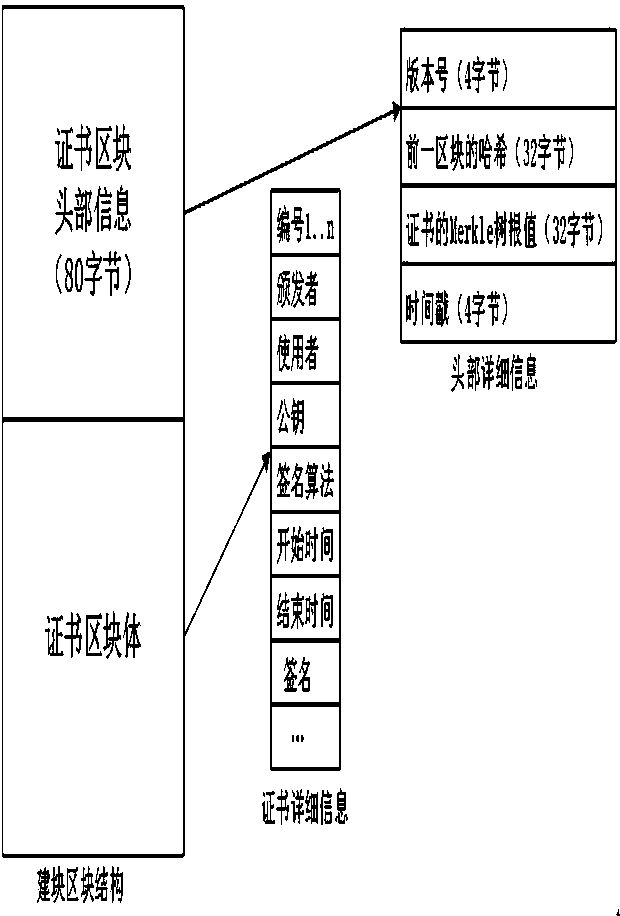
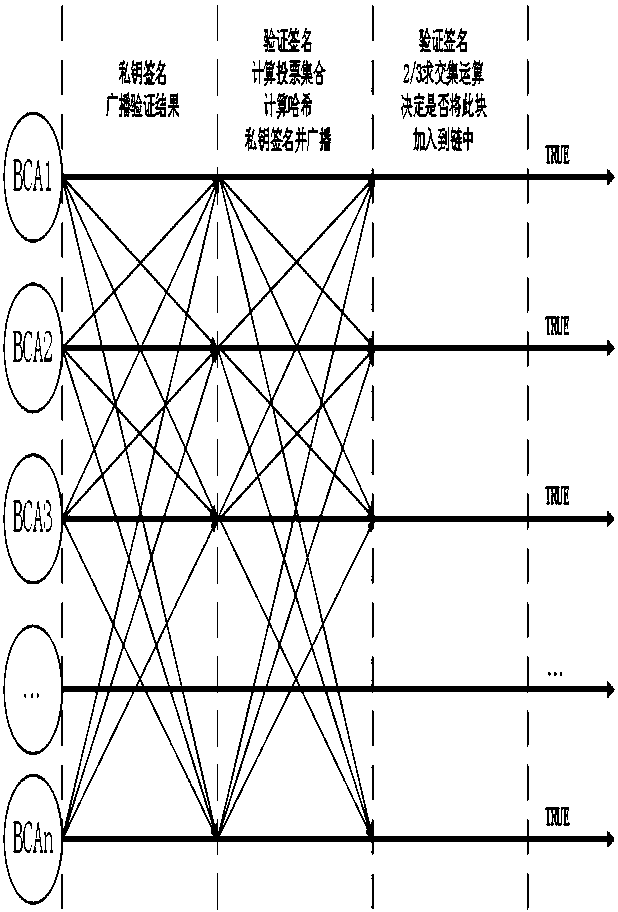
[0037] According to the Byzantine fault tolerance mechanism, in the certificate blockchain system, if F certificate nodes are attacked or fail, at least 3F+1 certificate nodes must exist in the system to ensure the certificate blockchain system normal operation; that is to say, in the authentication certificate blockchain system, at least four nodes must exist to form a complete authentication certificate blockchain. If any authentication certificate node is attacked or fails, as long as the number is less than two-thirds of all nodes in the system, the normal operation of the authentication certificate blockchain system can be guaranteed according to the Byzantine fault tolerance mechanism. After the abnormal node returns to normal, according to the synchronization mechanism of the authentication certificate system, a synchronization request will be made to the remaining authentication certificate nodes to obtain a complete authentication certificate blockchain. This ensures ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap