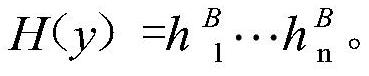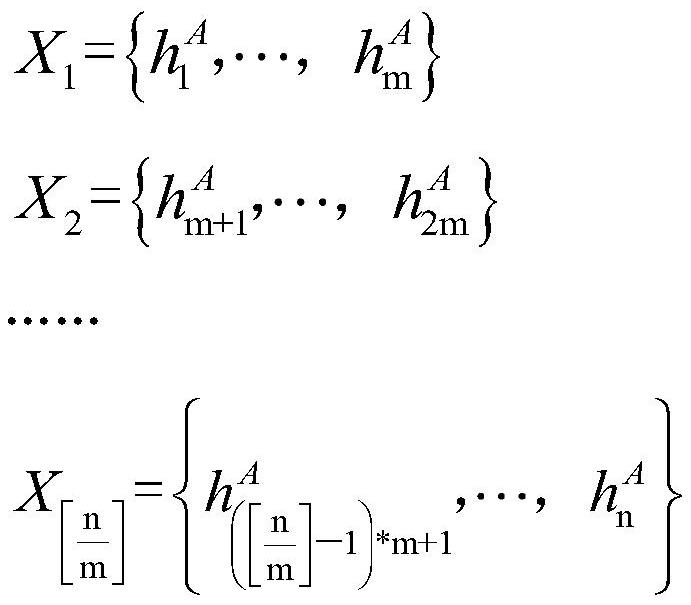A Method for Contrasting Quantum Information of Two Parties Based on Bell Basis
A quantum information and secret information technology, which is applied in the field of quantum information comparison between two parties based on the Bell basis, can solve problems such as reducing efficiency and difficulty in implementing protocols
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The method for comparing two-party quantum information based on the Bell base provided by the present invention is specifically implemented as follows:
[0023] Suppose Alice has a secret information x, and Bob has a secret information y. Alice and Bob compare the secret information according to the following steps:
[0024] The first step: Alice and Bob agree on one-the mapped hash function H: {0,1} n →{0,1} n ; Alice calculates the hash value of her secret information x and gets Bob calculates the hash value of his secret information y and gets
[0025]
[0026] Step 2: Alice divides the hash value H(x) of her secret information x into Groups before There are m elements in each group, and k elements in the last group, m≤n, k≤m; the hash value grouping of Alice's secret information x is as follows:
[0027]
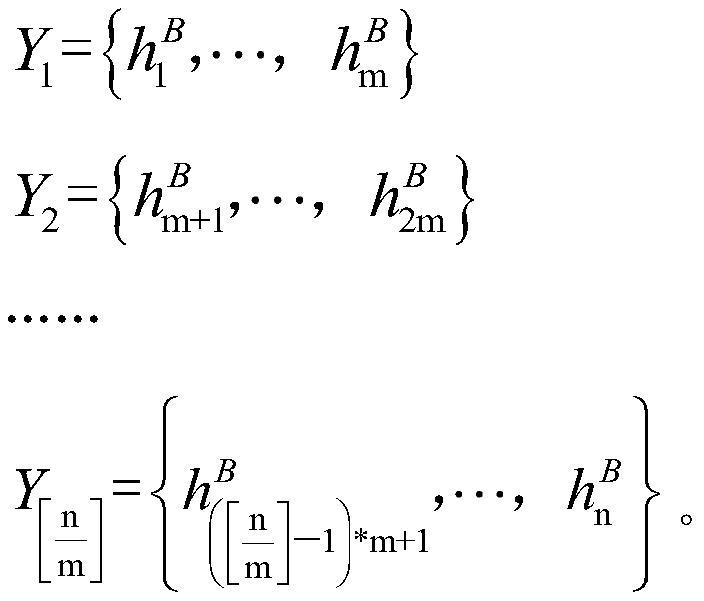
[0028] Bob also divides the hash value H(y) of his secret information y into Groups before There are m elements in each group in the group, and k elements in the las...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com