System and method for implementing DNS attack resistance based on network processor
A network processor and attack packet technology, applied in the field of network security, can solve problems such as failure to work properly, secondary servers cannot obtain valid traffic, etc., and achieve the effect of ensuring normal work and line bandwidth.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] This embodiment provides a network processor-based anti-DNS attack system, including:
[0040] The configuration management module is used to configure the filter field mask that needs attention, including source IP address, destination IP address and transport layer payload length; at the same time, it is used to configure the forwarding threshold for DNS special traffic and the selection of cycle aging time;
[0041] The message analysis module is used to analyze the DNS message to obtain the source IP address, the destination IP address and the length of the transport layer load, and then perform an 'AND' operation with the filter field mask to obtain the final filter field that needs attention;
[0042] Decision-making module, used to determine whether the DNS message is an attack message, use the final filter field to search the DNS flow table, if a certain entry is matched, then obtain the total number of statistics in the entry, if it exceeds the forwarding thres...
Embodiment 2
[0045] Corresponding to the above-mentioned embodiment of the system for realizing anti-DNS attack based on the network processor, the second embodiment provides a method for realizing anti-DNS attack based on the network processor, including the following steps:
[0046](1) Configure the filter field mask that needs attention, including source IP address, destination IP address and transport layer payload length; at the same time, it is used to configure the forwarding threshold for DNS special traffic and the selection of cycle aging time;
[0047] (2), flow analysis DNS message, to obtain source IP address, destination IP address and transport layer load length, then carry out 'AND' operation with filter field mask, obtain the final filter field that needs attention;
[0048] (3), judge whether the DNS message is an attack message, use the final filter field to search the DNS flow table, if a certain entry is matched, then obtain the total number of statistics in the entry, ...
Embodiment 3
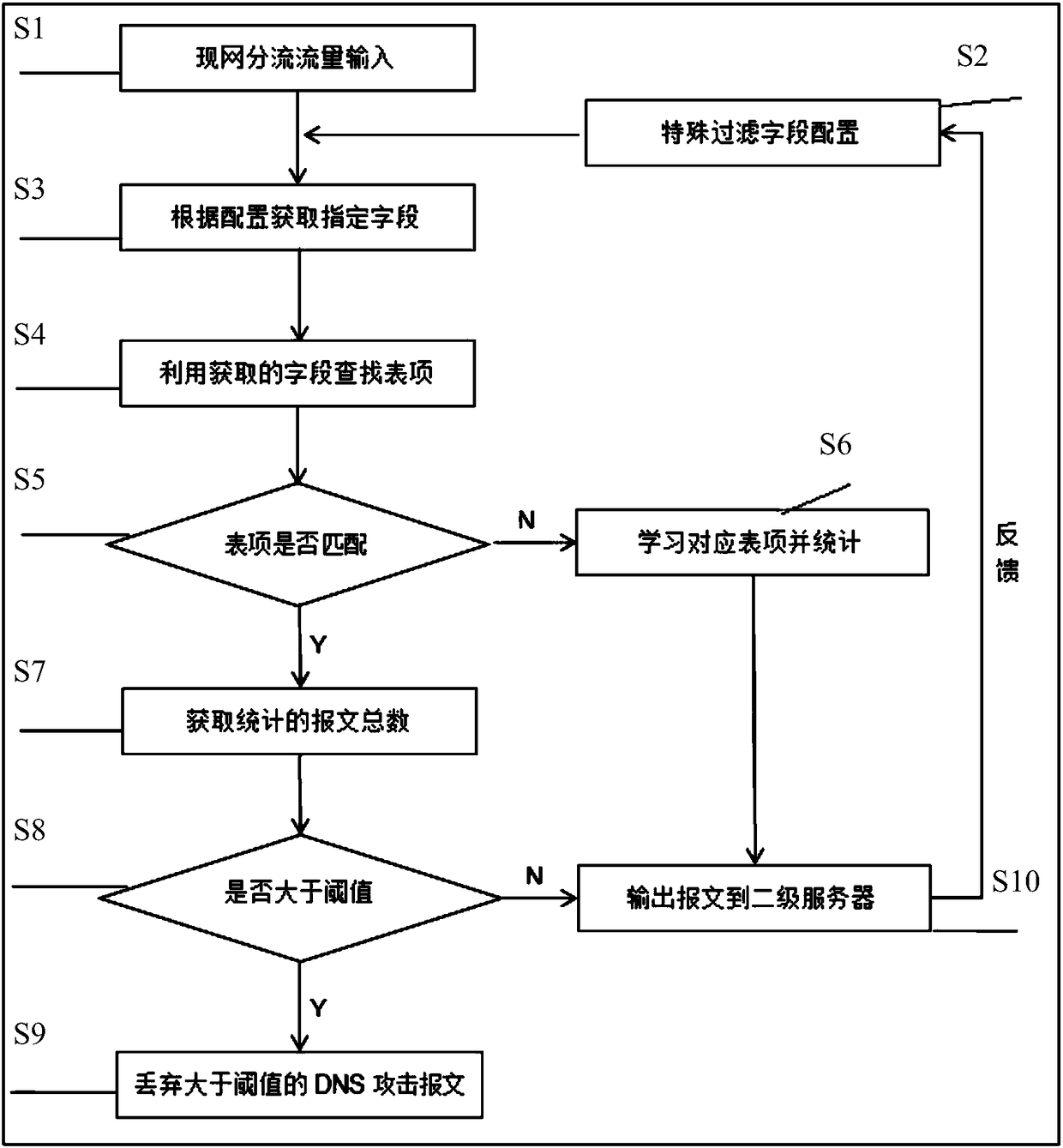
[0051] Please combine figure 1 As shown, this embodiment provides a specific method for implementing anti-DNS attack based on a network processor, including the following steps:
[0052] Step S1, various traffic of the live network enters the first-level distribution device;
[0053] Step S2, through the management configuration interface, configure the mask of the special field that needs to be filtered, and then send it to the first-level distribution device. At the same time, it can be modified according to the feedback information from the second-level server. The filter field includes source ID address and destination IP address. , IP length field, and cycle aging time;
[0054] Step S3, the first-level device parses the message, and extracts the corresponding field in the message whose UDP destination port is 53 according to the mask of the configured filter field, including the source IP address, the destination IP address and the length of the transport layer payload;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com