SM2 algorithm signature method applied to CS architecture
An algorithm and response code technology, applied in the field of cryptography, can solve the problems of the lack of a mechanism for the server to actively verify the identity of the client entity, and achieve the effects of improving signature security, less interaction, and low latency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] In order to make the purpose, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
[0058] Parameter Description:
[0059] SM2 curve parameters, the elliptic curve E is an elliptic curve defined on the finite field Fq, and G is the base point of order n on the elliptic curve E.
[0060] [*] means point multiplication operation, that is, to calculate k times points of the base point G of order n on the elliptic curve E;
[0061] Elliptic curve point (x1, y1)=k[*]G, [*] means point multiplication operation, that is, k times points of point G on the elliptic curve are calculated;
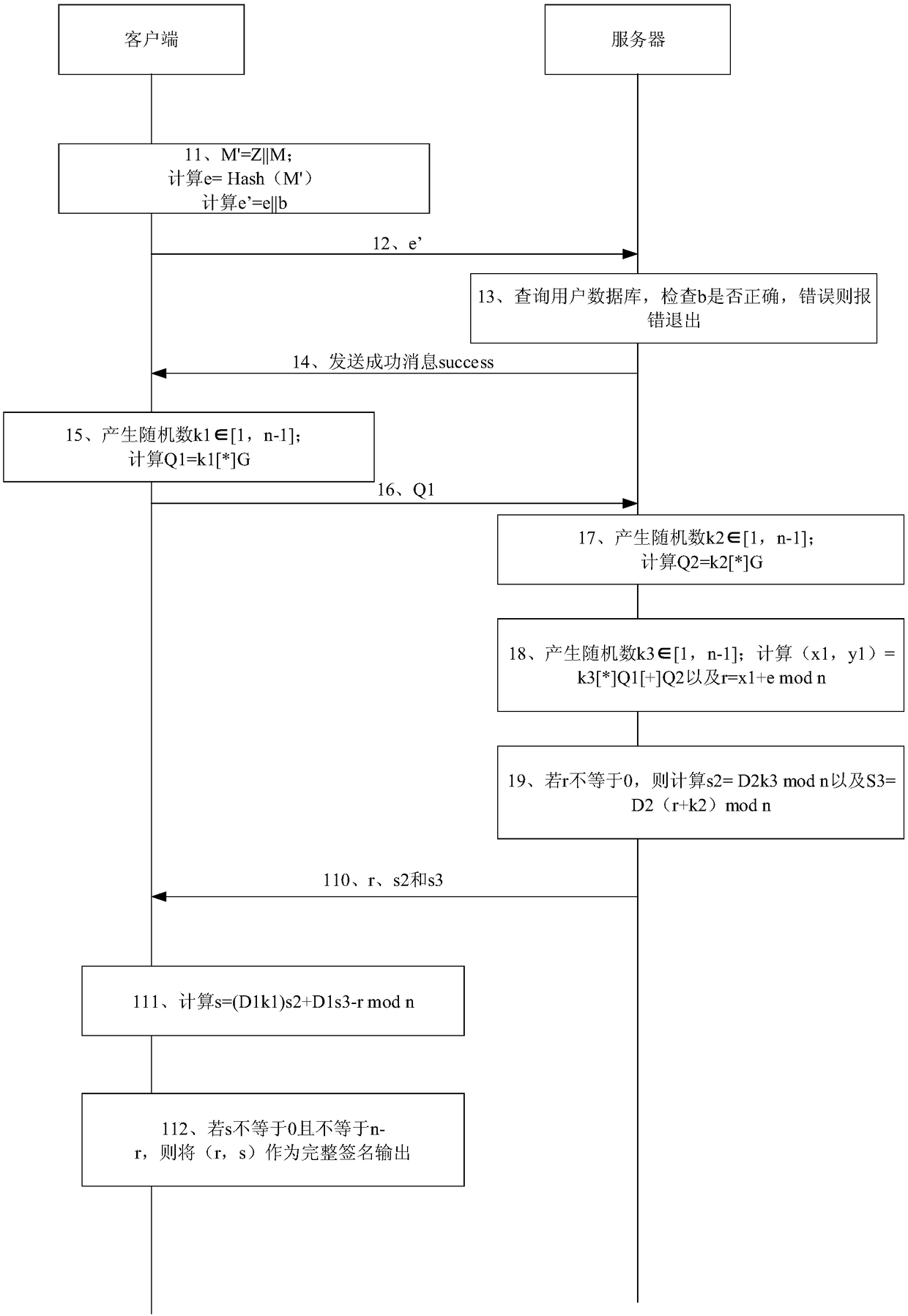
[0062] figure 1 It is a flow chart of an example of the SM2 signature method for unilaterally uploading single-factor authentication in the present invention.
[0063] Step 11: The client concatenates Z, M, to form M', calculates Hash(M'), takes the calc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com