A method for intelligently identifying and processing network data flow
A technology for intelligently identifying and processing networks, which is applied in the field of network security and can solve problems such as leakage of important data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be specifically introduced below in conjunction with the accompanying drawings and specific embodiments.
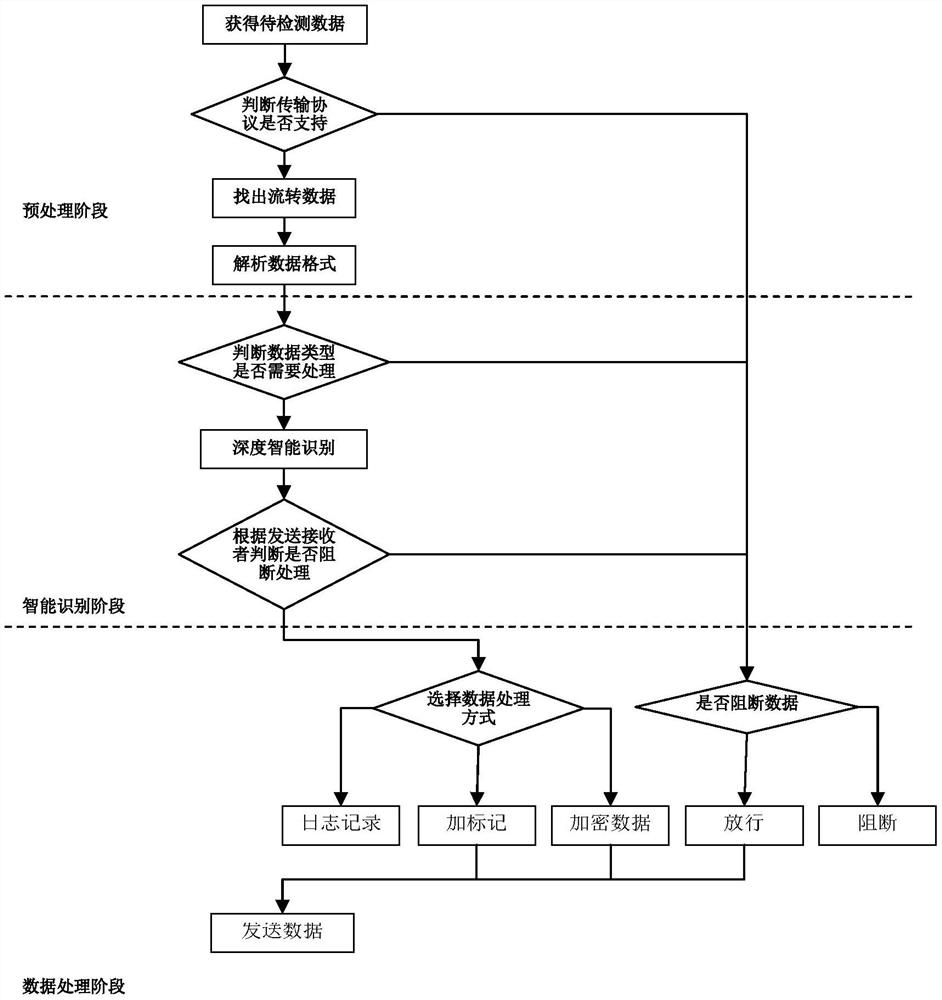
[0034] like figure 1 As shown, a method for intelligently identifying and processing network data flow includes the following steps:
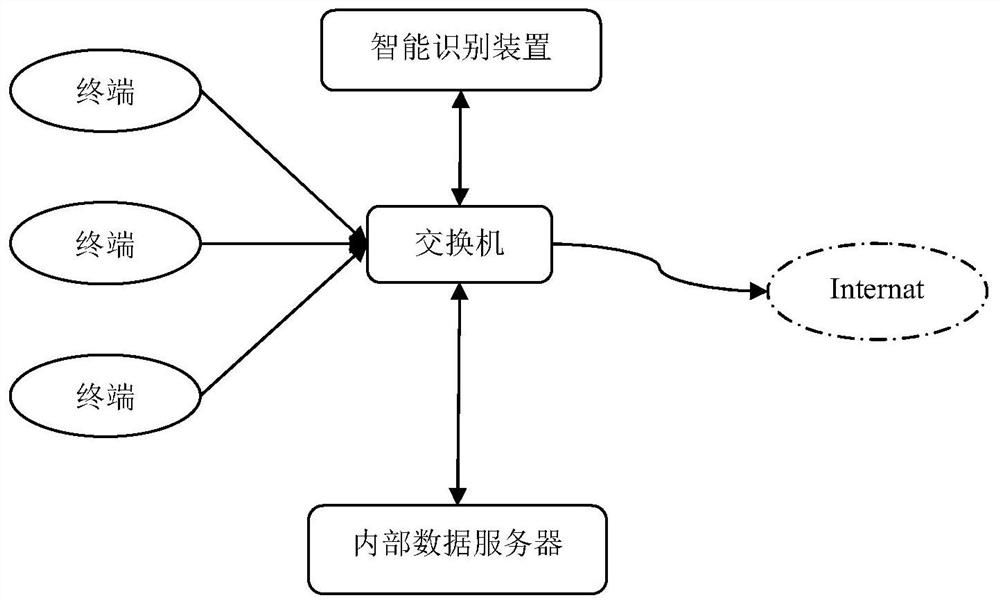
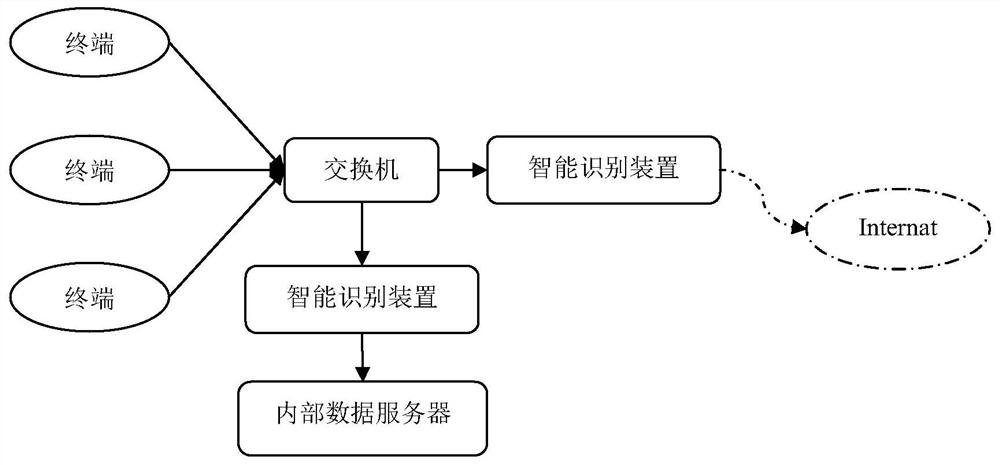
[0035] Step 1: Connect the intelligent identification device, core switch or router to the terminal, internal data server, and public network installation; the identification device forwards the network data stream as an agent, and the device obtains the data to be detected; the data to be detected is the pre-defined target server network data. As an embodiment, the intelligent identification device is a gateway or a proxy server.
[0036] Step 2: Analyze the data to be detected and determine the protocol used for the transmission of the data to be detected. If the protocol used cannot be analyzed, according to the preset network protocol identification rules, directly block or release the data to be det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com