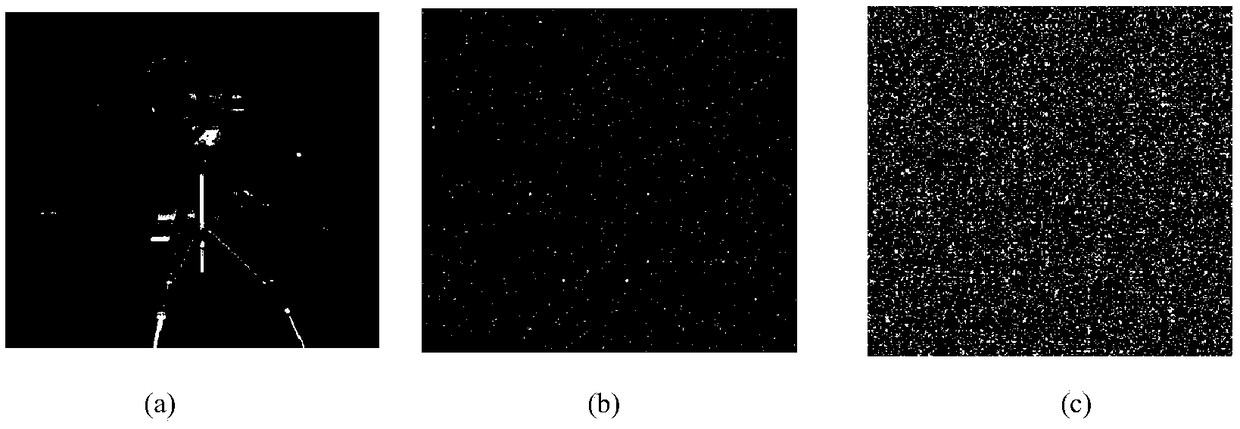
Image encryption method based on chaotic adaptive mechanism
An encryption method and self-adaptive technology, applied in the countermeasures of attacking encryption mechanism, secure communication through chaotic signals, image communication, etc., can solve the problems of increasing the difficulty of key management and infeasibility, and achieve the effect of resisting attacks and reducing difficulty.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0072] (1) Assuming that the plaintext image is an image with 256 gray levels and a size of L=m×n, transform it into a one-dimensional vector P={p(1),p(2),p(3),... ,p(mn)}.
[0073] (2) Given (x(0), y(0), z(0), w(0)) = ((1.98, 1.45, 0.78, 0.8)) as the initial value, use the following chaotic system (1) Generate four chaotic sequences X, Y, Z, W of length L. Among them, X={x(1),x(2),x(3),...,x(L)}; Y={y(1),y(2),y(3),...,y( L)}; Z={z(1),z(2),z(3),...,z(L)}; W={w(1),w(2),w(3),..., w(L)}.
[0074]
[0075] Due to the limitation of computer accuracy, the chaotic sequence may degenerate into a periodic sequence in the iterative process. To overcome this shortcoming, multiple chaotic sequences are subjected to a nonlinear function operation to obtain a longer period sequence.
[0076] Use formula d(i)=cos 2 ((x(i)+y(i)+z(i)) / 3), formula k(i)=cos 2 ((w(i)+x(i)+y(i)) / 3) and t(i)=cos 2 The transformation of ((w(i)+x(i)+z(i)) / 2)(i=1, 2, 3,..., m*n) transforms the chaotic flow X, Y, Z, W int...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap