Data processing method and device
A data processing and data technology, applied in the computer field, can solve problems such as poor data update effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
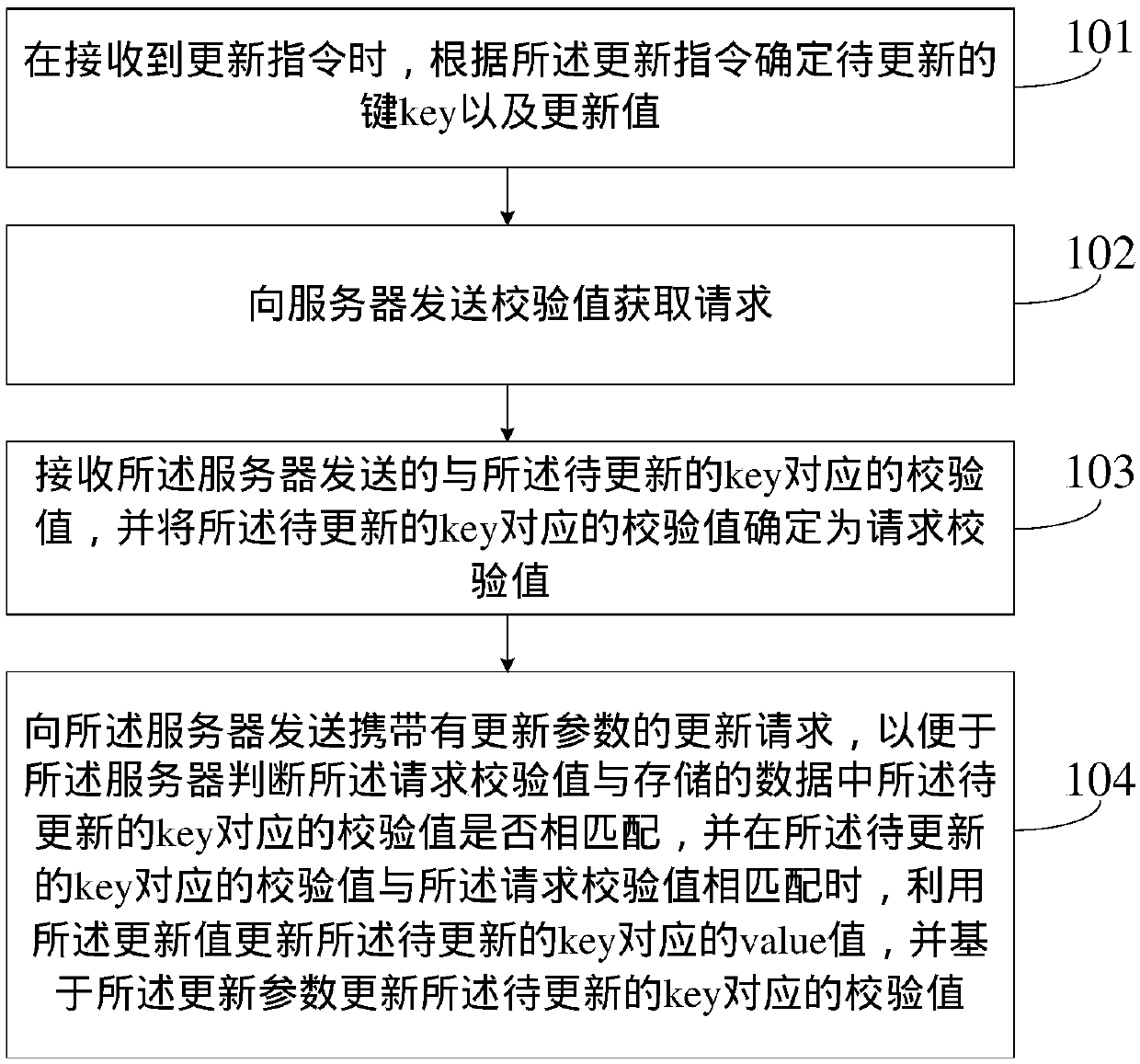
[0069] figure 1 It is a flow chart of the steps of a data processing method provided in Embodiment 1 of the present invention, which is applied to a terminal, such as figure 1 As shown, the method may include:
[0070] Step 101. When an update instruction is received, determine a key to be updated and an update value according to the update instruction.
[0071] In the embodiment of the present invention, the key to be updated is the key that the user needs to update. For example, assuming that the user needs to operate on the key whose content is "map", then "map" is the key to be updated. In the actual application scenario, when the user updates the key, he will first read the current value corresponding to the key, and then combine the needs to be realized and the current value corresponding to the key to determine to update the value corresponding to the key to How much, that is, determines the update value. For example, assuming that the user "Zhang San" reads the curr...
Embodiment 2
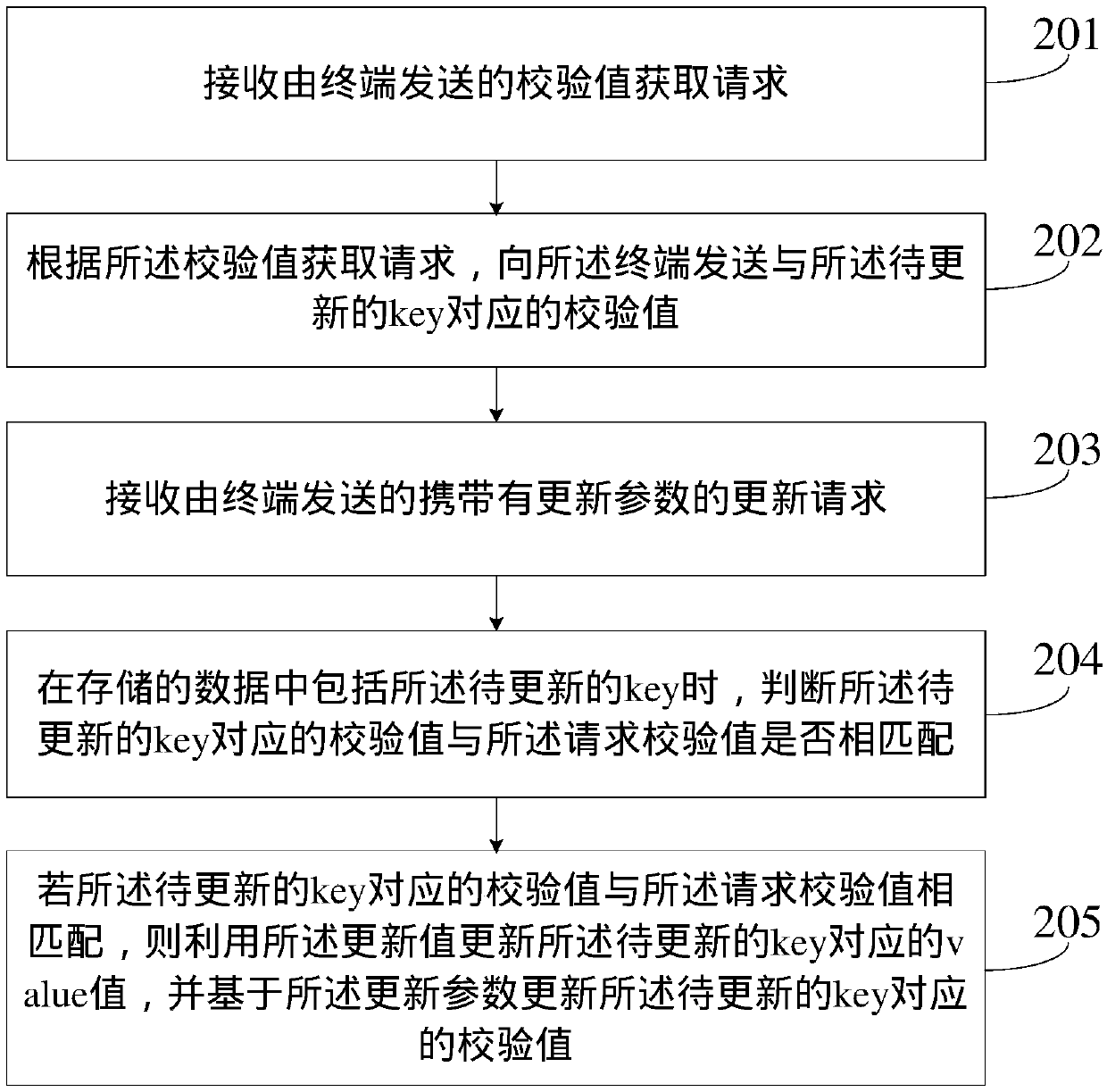
[0082] figure 2 It is a flow chart of the steps of a data processing method provided in Embodiment 2 of the present invention, which is applied to a server, such as figure 2 As shown, the method may include:
[0083] Step 201. Receive a verification value acquisition request sent by a terminal.
[0084] In the embodiment of the present invention, the verification value acquisition request may carry the key to be updated.
[0085] Step 202: Send the verification value corresponding to the key to be updated to the terminal according to the verification value acquisition request.
[0086] In the embodiment of the present invention, after receiving the verification value acquisition request, the server may first extract the key to be updated in the verification value acquisition request, and then search the stored data for the verification key corresponding to the key to be updated. value, and then send the obtained verification value to the terminal. Specifically, the check v...
Embodiment 3
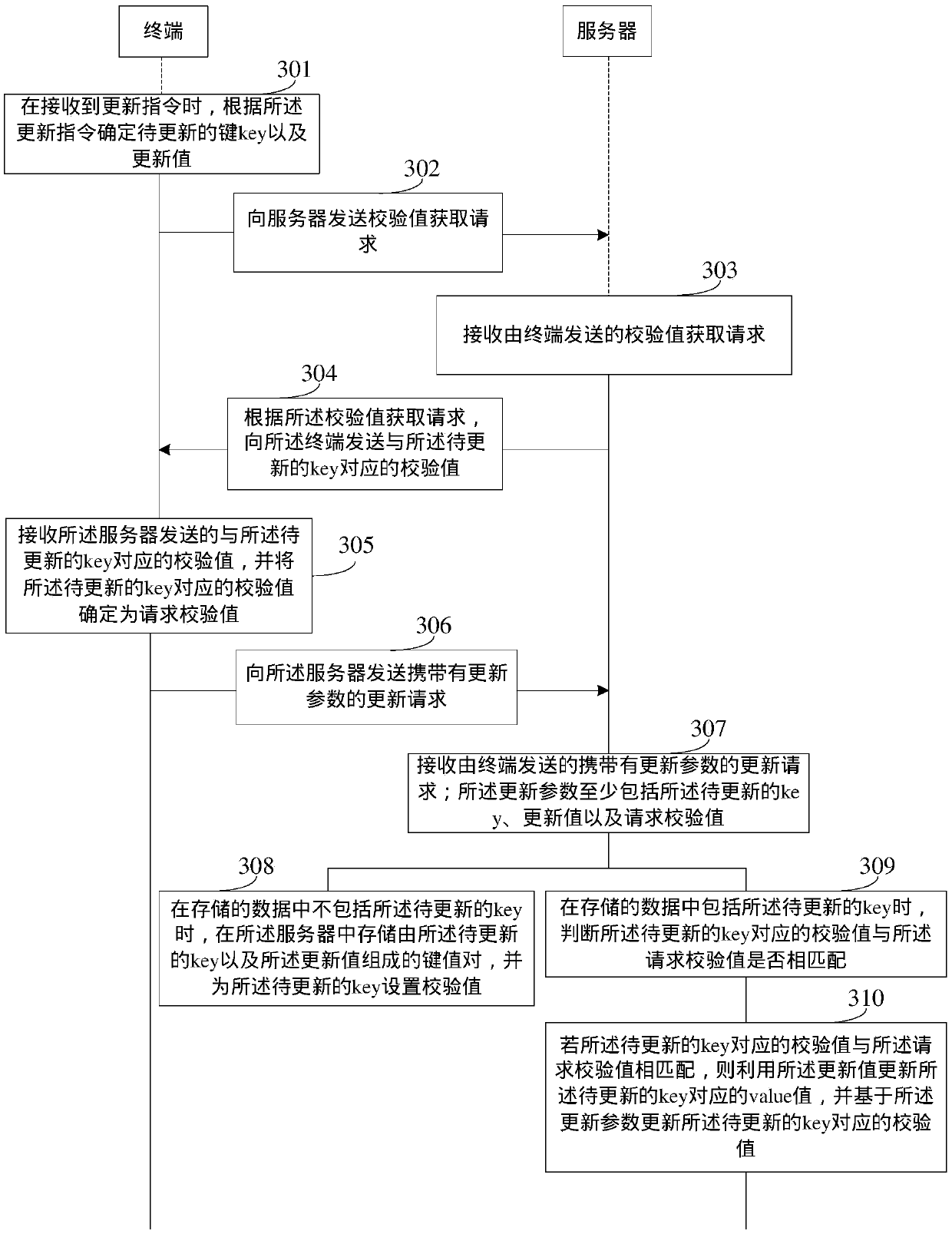
[0095] image 3 It is a flow chart of the steps of a data processing method provided in Embodiment 3 of the present invention, such as image 3 As shown, the method may include:
[0096] Step 301. When receiving an update instruction, the terminal determines the key to be updated and the update value according to the update instruction.
[0097] Specifically, for the implementation manner of this step, reference may be made to the foregoing step 101, which will not be described in detail here in this embodiment of the present invention.
[0098] Step 302, the terminal sends a verification value acquisition request to the server; the verification value acquisition request carries the key to be updated.
[0099] Specifically, for the implementation manner of this step, reference may be made to the above-mentioned step 102, and details are not described here in this embodiment of the present invention.
[0100] Step 303, the server receives the verification value acquisition r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com