Resource access method and apparatus, device and storage medium
A resource access and resource technology, applied in the blockchain field, can solve the problems of low accuracy of authorization verification results and insufficient credibility, and achieve the effect of ensuring accuracy, ensuring credibility, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
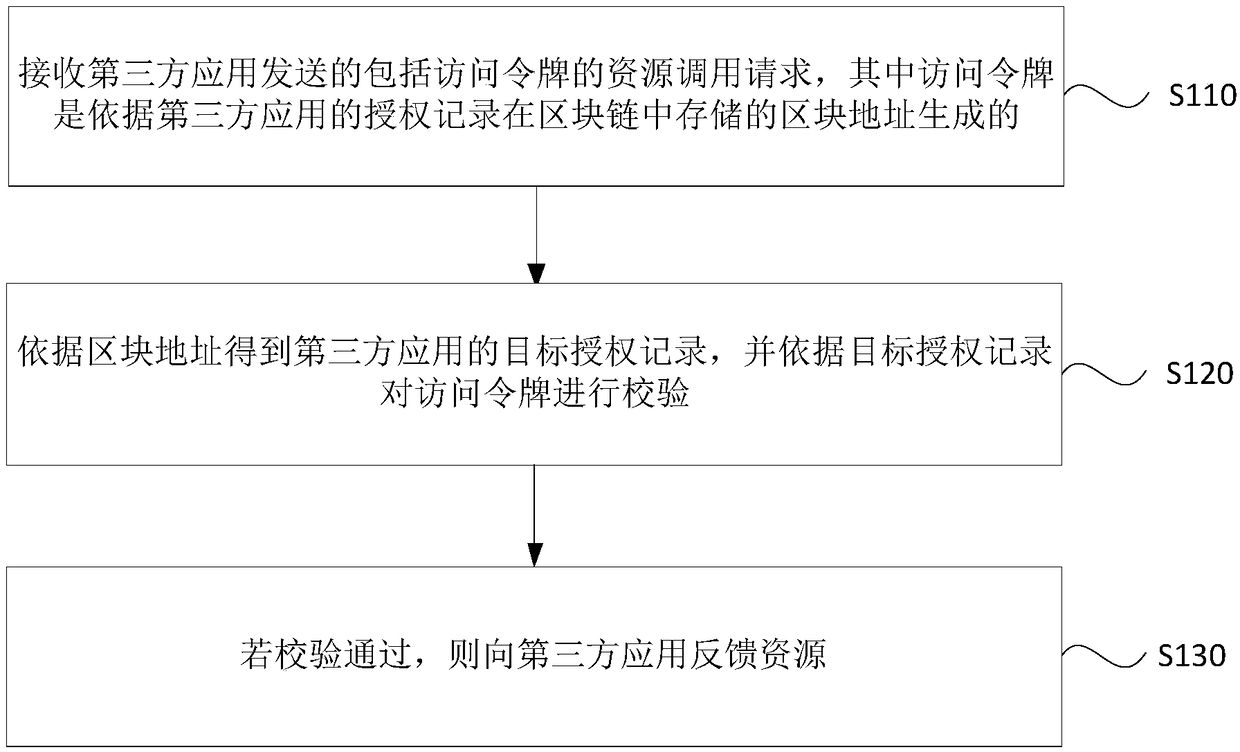
[0039] figure 1 It is a flow chart of a resource access method provided by Embodiment 1 of the present invention. This embodiment is based on the OAuth authorization protocol and applies blockchain technology to resource access scenarios to solve the problem that the authorization record is only stored unilaterally by the authorization server and the validity of the access token is only determined by the existing resource call process. The unilateral verification of the resource server leads to problems such as the accuracy and low credibility of authorization records and access tokens. The applicable blockchain can be a public chain or a consortium chain. The entire set of resource access methods is usually executed in cooperation with resource service nodes, third-party application nodes and authorized service nodes in the blockchain system. Each node independently participates in the operation of the blockchain system. Among them, the third-party application node is conf...
Embodiment 2
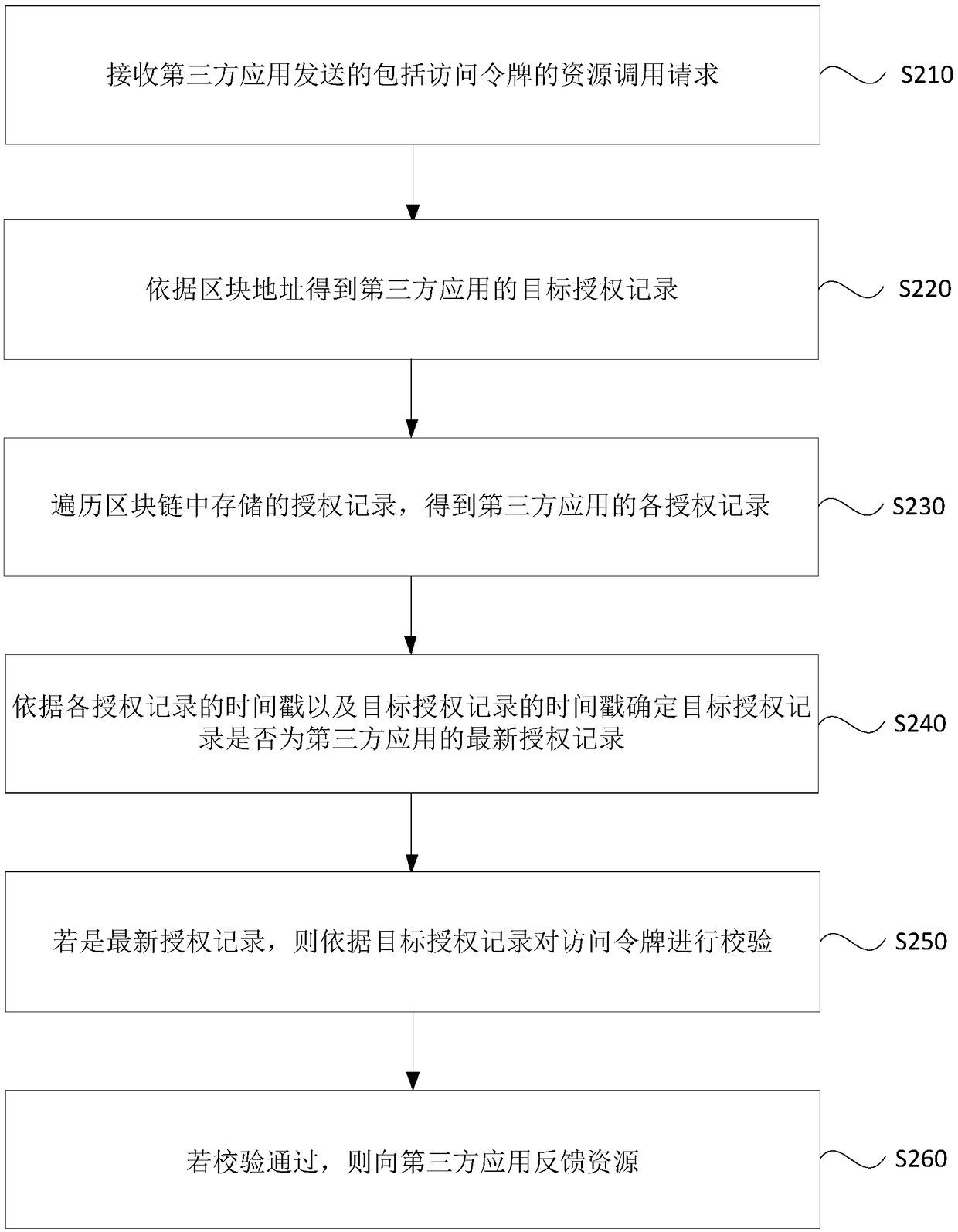
[0059] figure 2 It is a flowchart of a resource access method provided by Embodiment 2 of the present invention. Based on the above embodiments, this embodiment further optimizes the step of verifying the access token according to the target authorization record. see figure 2 , the method specifically includes:
[0060] S210. Receive a resource invocation request including an access token sent by a third-party application.
[0061] S220. Obtain the target authorization record of the third-party application according to the block address.
[0062] S230, traversing the authorization records stored in the blockchain to obtain each authorization record of the third-party application.
[0063] Specifically, the local resource service node can traverse the entire blockchain to find all authorization records of the third-party application according to the identification of the third-party application and / or the identification of the resource owner.
[0064] S240. Determine whe...
Embodiment 3
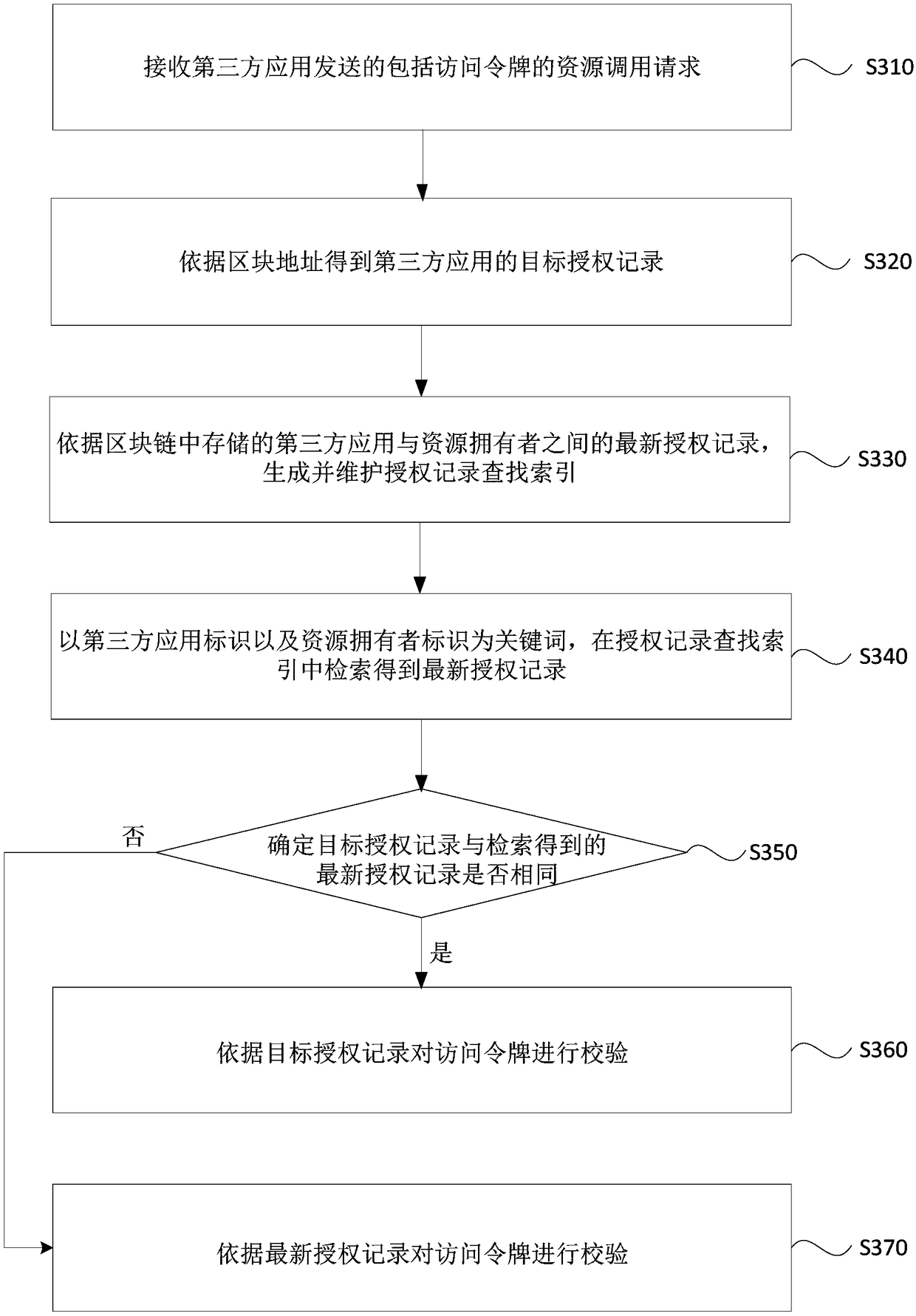
[0072] image 3 It is a flow chart of a resource access method provided by Embodiment 3 of the present invention, and this embodiment is optimized on the basis of the foregoing embodiments. see image 3 , the method specifically includes:
[0073] S310. Receive a resource invocation request including an access token sent by a third-party application.
[0074] S320. Obtain the target authorization record of the third-party application according to the block address.
[0075] S330. Generate and maintain an authorization record search index according to the latest authorization record between the third-party application and the resource owner stored in the blockchain.
[0076] Since the resource service node checks whether the authorization record is up-to-date by traversing the entire blockchain, this process consumes high performance and is inefficient. Therefore, in order to further improve the verification efficiency, the local resource service node, as a node in the bloc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com