A Sample Automatic Calibration Method for Encrypted Traffic Identification
An automatic calibration and traffic identification technology, applied in the field of network security and user privacy, which can solve the problems of correspondence, inapplicability of classifiers, inability to determine the start and end time points of user access, etc., and achieve the effect of accurate user behavior and accurate identification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
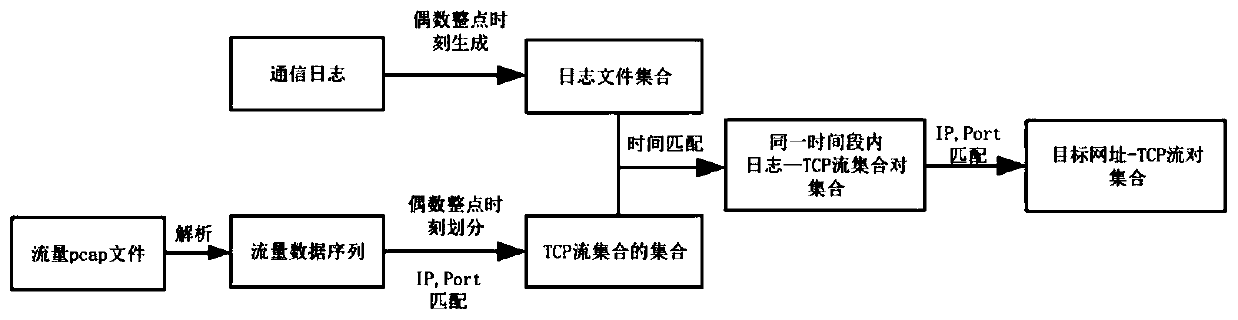
[0031] Step 1: Given a pcap file of traffic data captured continuously for n days, parse it into a data packet sequence in the format of , and require the sequence to be sequenced from small to large by time stamp Sort. Given the communication log generated on the proxy server side, the format of each record is , according to the characteristic that the port of the same IP will not be reused every two hours, it is required The communication log is to generate a file every two hours, that is, every even hour at 0:00, 2:00, 4:00, 6:00, 8:00... and so on to generate a log file, such as 2018 / 4 The communication log from 18:00 to 20:00 of / 20 is recorded as a file at 2018-04-20.18:00.
[0032] Step 2: Timestamp the largest and smallest in the sequence of packets as ts 0 and ts 1 , convert it to the format of [Year-Month-Day.Hour:Minute:Second], recorded as t 0 and t 1 . Calculates less than and closest to t 0 and less than and closest to t 1 The [Year-Month-Day. Even-number...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com