Authentication password for interaction
A password and password matching technology, applied in the field of verification password for interaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
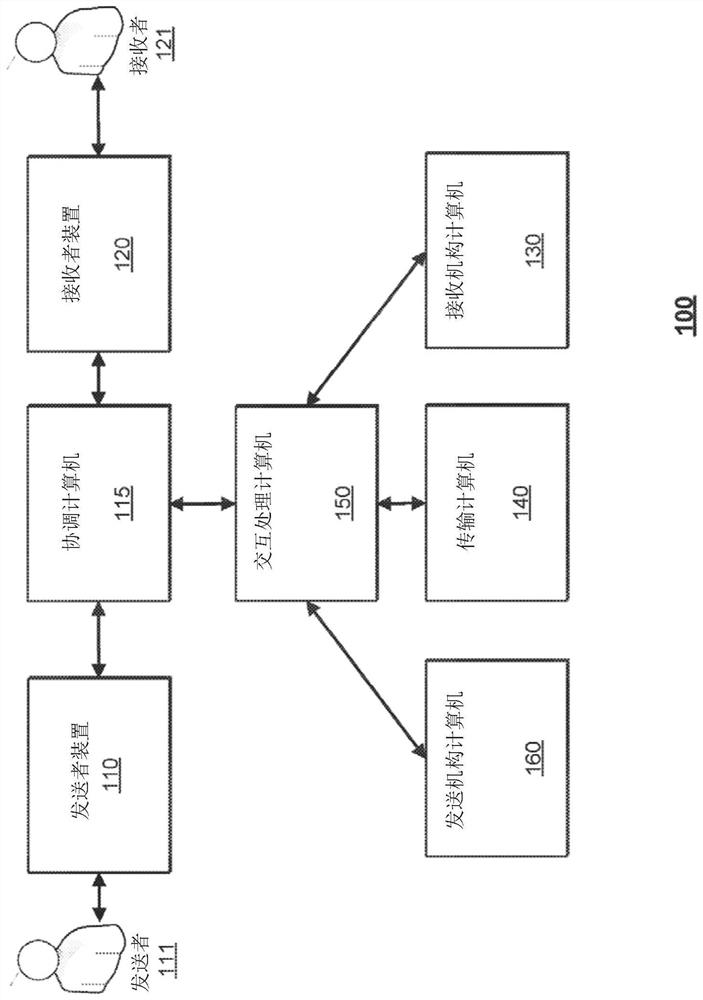
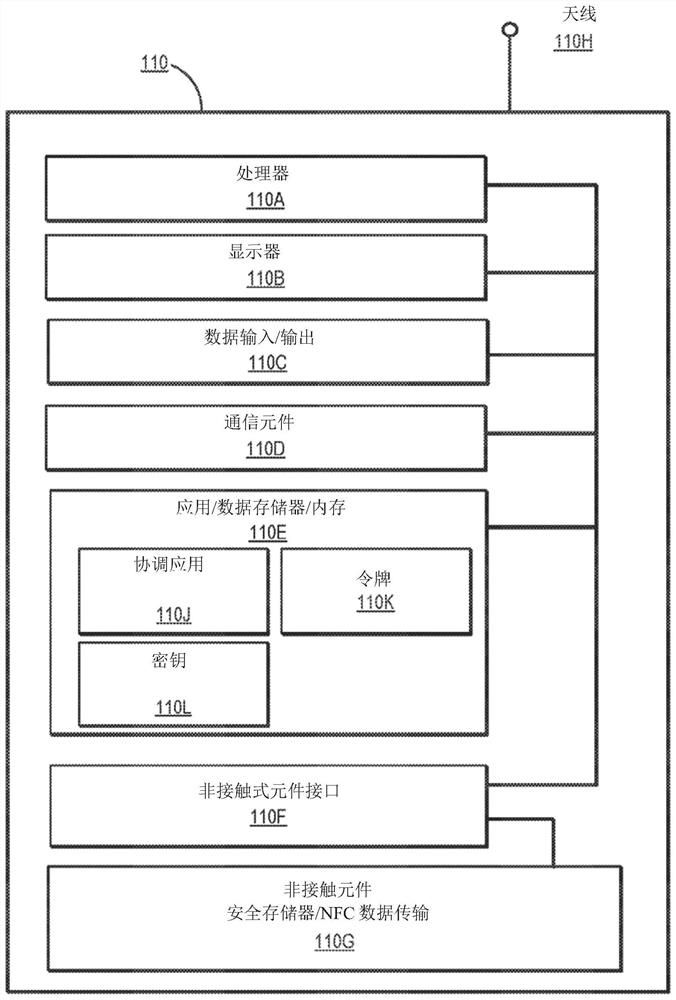
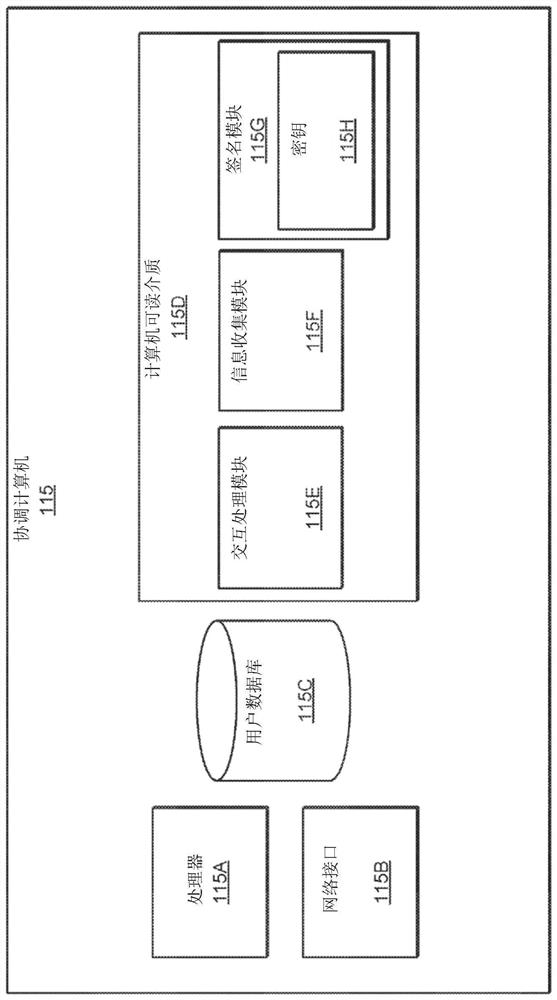
[0021] Embodiments of the present invention relate to preventing man-in-the-middle attacks, replay attacks, and other fraudulent interactions. Embodiments may prevent these fraudulent interactions by verifying the authenticity of the interaction and interaction parameters. A first party (eg, "sender") may initiate an interaction via a first device (eg, "sender device") to send value to a second party (referred to as a "recipient"). The sender can initiate the interaction by selecting the value to send, selecting the account from which to get the value, and by indicating the recipient to receive the value. The sender device may then generate a password for the interaction. The password may be generated using a key associated with the sender, information identifying the sender, and information identifying the recipient.
[0022] When an interaction request is sent to the interaction processing computer, the interaction processing computer may verify that the password is authen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com