Message verification code attack protection method, server and computer readable storage medium
A technology of SMS verification code and storage medium, applied in the field of SMS verification code attack protection method, server and computer-readable storage medium, can solve problems such as inability to solve short-message bombs, etc., and achieve the effect of preventing attack behavior and reducing spam text messages
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
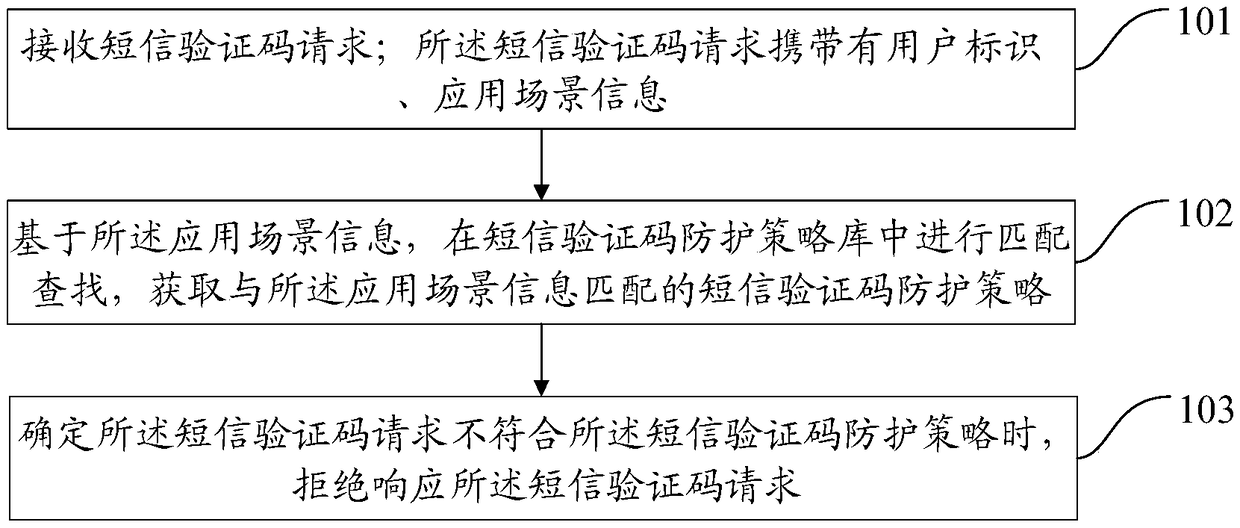
[0030] figure 1 It is a schematic diagram of the implementation flow of a short message verification code attack protection method according to an embodiment of the present invention. The method includes the following steps:
[0031] Step 101: Receive a SMS verification code request; the SMS verification code request carries user identification and application scenario information;
[0032] Specifically, the SMS verification code management system such as the server and the background management platform or the SMS verification code management device receives the SMS verification code request; wherein, the SMS verification code request carries at least user identification and application scenario information.
[0033] Here, the SMS verification code request may be generated by triggering an application program in the terminal, or may be generated by triggering a background interface, an application program interface, etc.; the SMS verification code request includes a SMS verif...
Embodiment 2
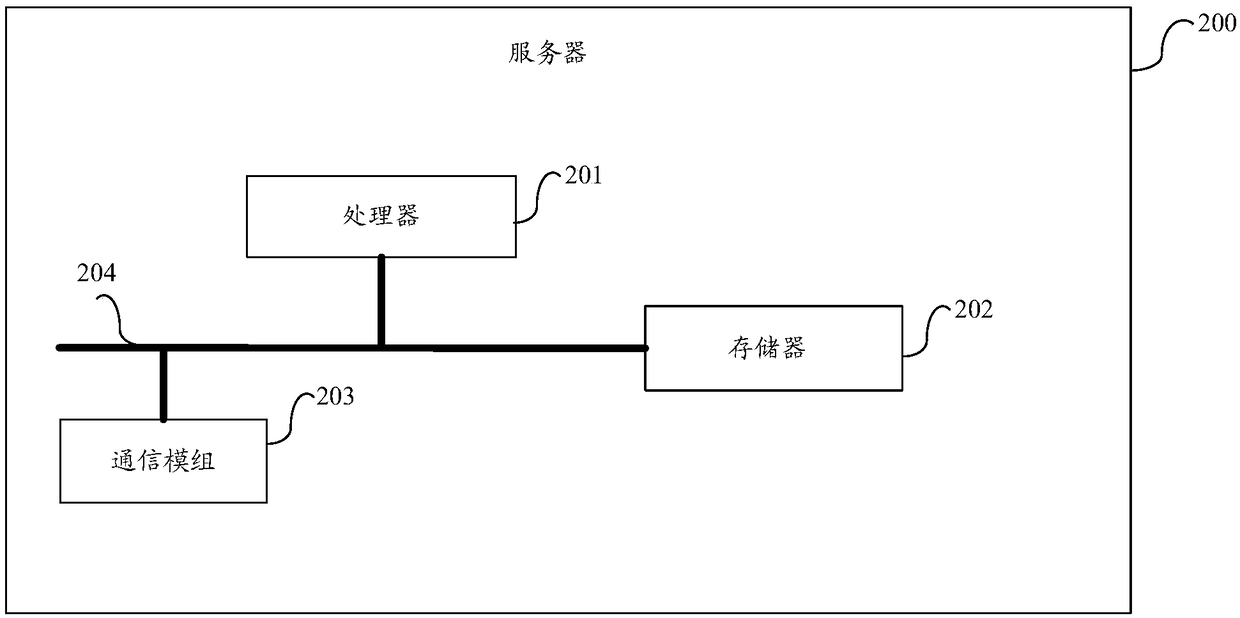
[0110] An embodiment of the present invention provides a server, image 3 It is a schematic diagram of the composition and structure of the server in the embodiment of the present invention, the server 200 includes: one or more processors 201, memory 202, and one or more modules; wherein, image 3 The processor 201 shown in the figure is not used to indicate that the number of processors is one, but only used to indicate the positional relationship of the processor relative to other devices. In practical applications, the number of processors can be one or more a; similarly, image 3 The memory 202 shown in FIG. 2 also has the same meaning, that is, it is only used to refer to the positional relationship of the memory relative to other devices. In practical applications, the number of the memory may be one or more.
[0111] The one or more modules are stored in the memory 202 and configured to be executed by the one or more processors 201, the one or more modules are used to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com