A security verification method and device for a message into a label
A technology for entering tags and messages, applied to electrical components, transmission systems, etc., can solve problems such as the inability to prevent equipment impacts, and the inability of LSR to identify the legitimacy of tags, so as to achieve simple configuration, prevent network attacks, and achieve simple effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
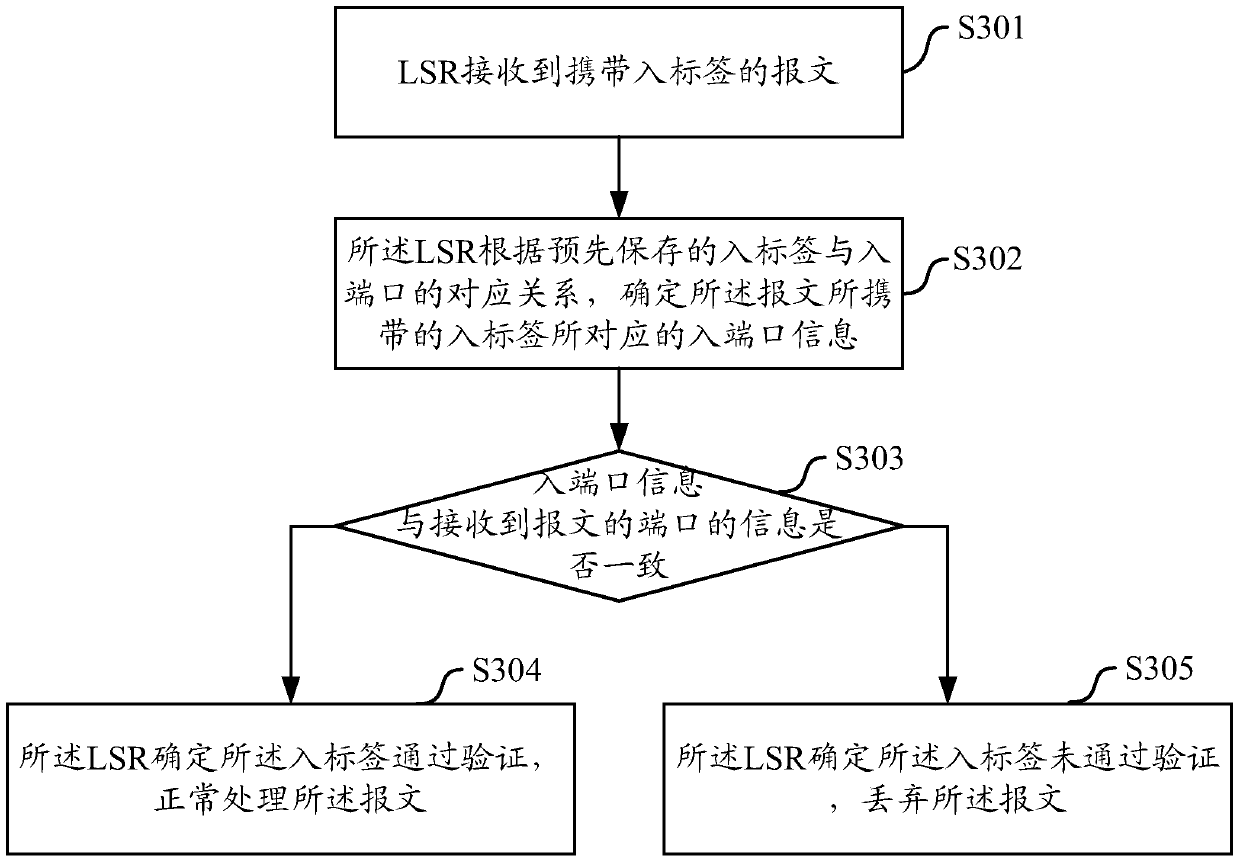
[0031] In order to solve the problem in the prior art solution that the LSR cannot identify the validity of the label and prevent malicious attack packets from impacting the equipment, this application proposes a security verification method for packets entering labels.
[0032] Such as image 3 As shown, it is a schematic flow diagram of a security verification method for a message into a label proposed in the embodiment of the present application. The method is applied in an MPLS network and specifically includes the following steps:
[0033] In step S301, the LSR receives a message carrying an incoming label.
[0034] When this step occurs, depending on whether the source validity check function of the incoming label is enabled on the LSR, there will be the following two situations:
[0035] Case 1: the LSR has currently enabled the source validity checking function of the incoming label, and then performs the subsequent step S302.
[0036] It should be noted that the spe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com