Deep learning WebShell protection method based on cloud WAF
A deep learning and algorithm technology, applied in electrical components, transmission systems, etc., can solve the problems of high false alarm rate and low WebShell performance, and achieve the effect of low false alarm rate, strong real-time performance, and avoiding occupation of traffic.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
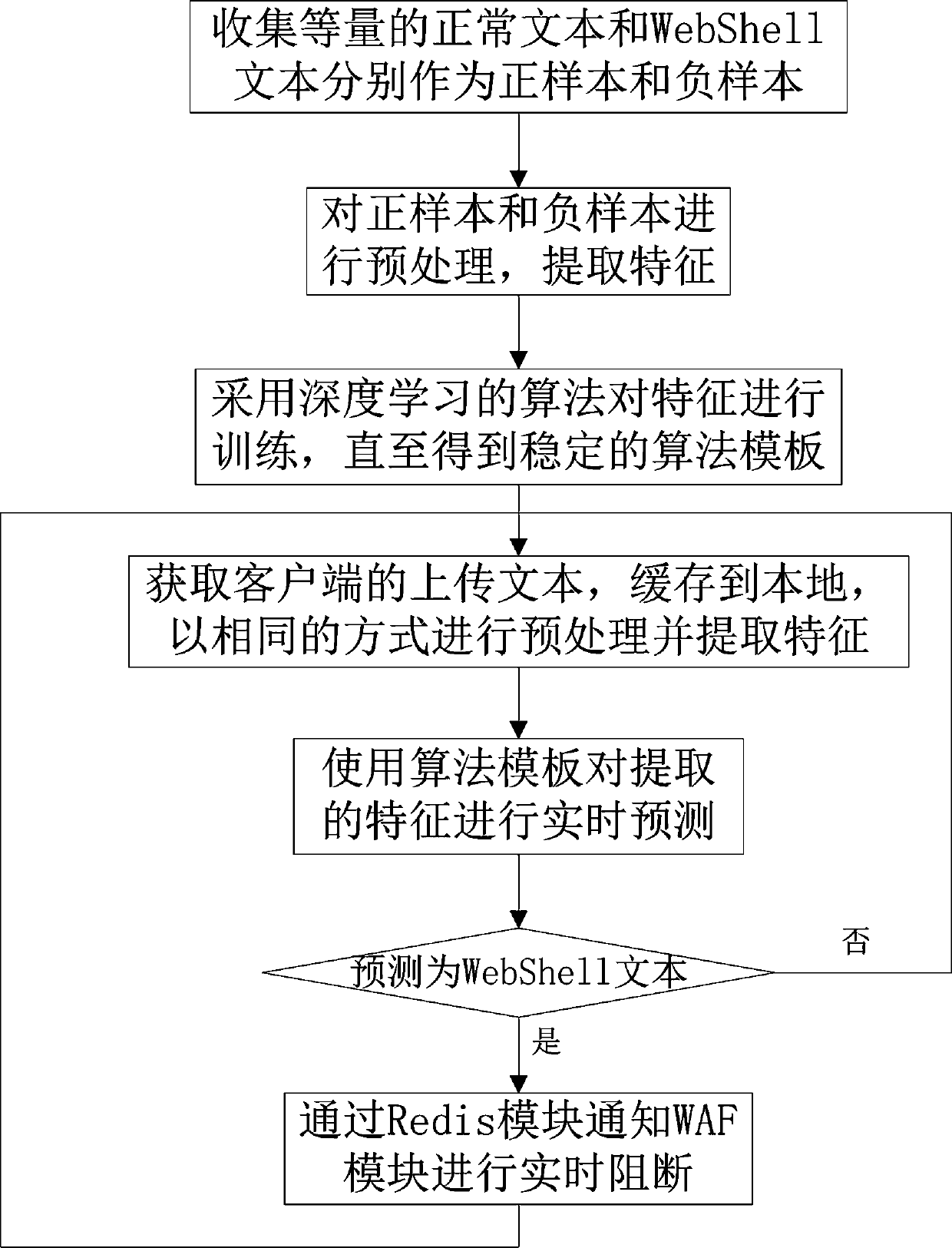
[0024] The invention relates to a cloud WAF-based deep learning WebShell protection method, which is arranged on an nginx analysis server, predicts malicious file upload behaviors in real time according to text content, and simultaneously blocks the behaviors identified as malicious uploaded files in real time.
[0025] The invention mainly includes five parts: data collection, data preprocessing, algorithm template training, real-time prediction and blocking attack source.
[0026] The method includes the following steps.
[0027] Step 1: Collect equal amounts of normal text and WebShell text as positive samples and negative samples, respectively.
[0028] In the present invention, normal text and WebShell text are collected through the GitHub platform and the local WAF production environment.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com