Privacy-protected vehicle 3D positioning method based on v2r or v2v communication in vehicle network
A technology of privacy protection and positioning method, which is applied to the field of 3D positioning technology and key exchange protocol, which can solve impractical problems and achieve the effect of low delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
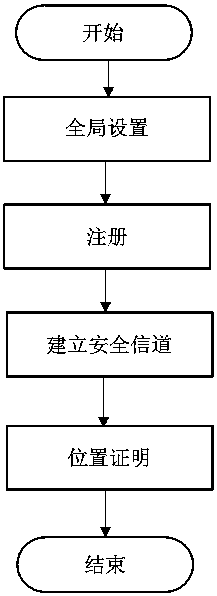
[0032] A privacy-protected vehicle 3D positioning method based on V2R communication in a vehicle network, comprising the following entities: a trusted authority (TA) that generates and issues system parameters, a vehicle, and a roadside unit (RSU), specifically including the following steps:
[0033] Step 1: Global Settings
[0034] Input a security parameter λ, TA performs the following operations:
[0035] 1) Select a cyclic multiplicative group with order q pick a generator
[0036] 2) Generate a system master key s and the corresponding master public key g 0 . TA uses s to issue certificates for vehicles and RSUs. g 0 is used to verify the validity of the certificate;
[0037] 3) Choose a symmetric encryption scheme and a MAC scheme Symmetric key K in symmetric encryption scheme 1 and the symmetric key K in the MAC scheme 2 have the same length;
[0038] 4) Select a hash function H: {0, 1} * - → {0, 1} l , l is and The bit length of the key used in ; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com