Encrypted file system mounting method and device
An encrypted file system and mounting technology, applied in computer security devices, instruments, electronic digital data processing, etc., can solve problems such as data security, and achieve the effect of reducing operating costs and ensuring data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
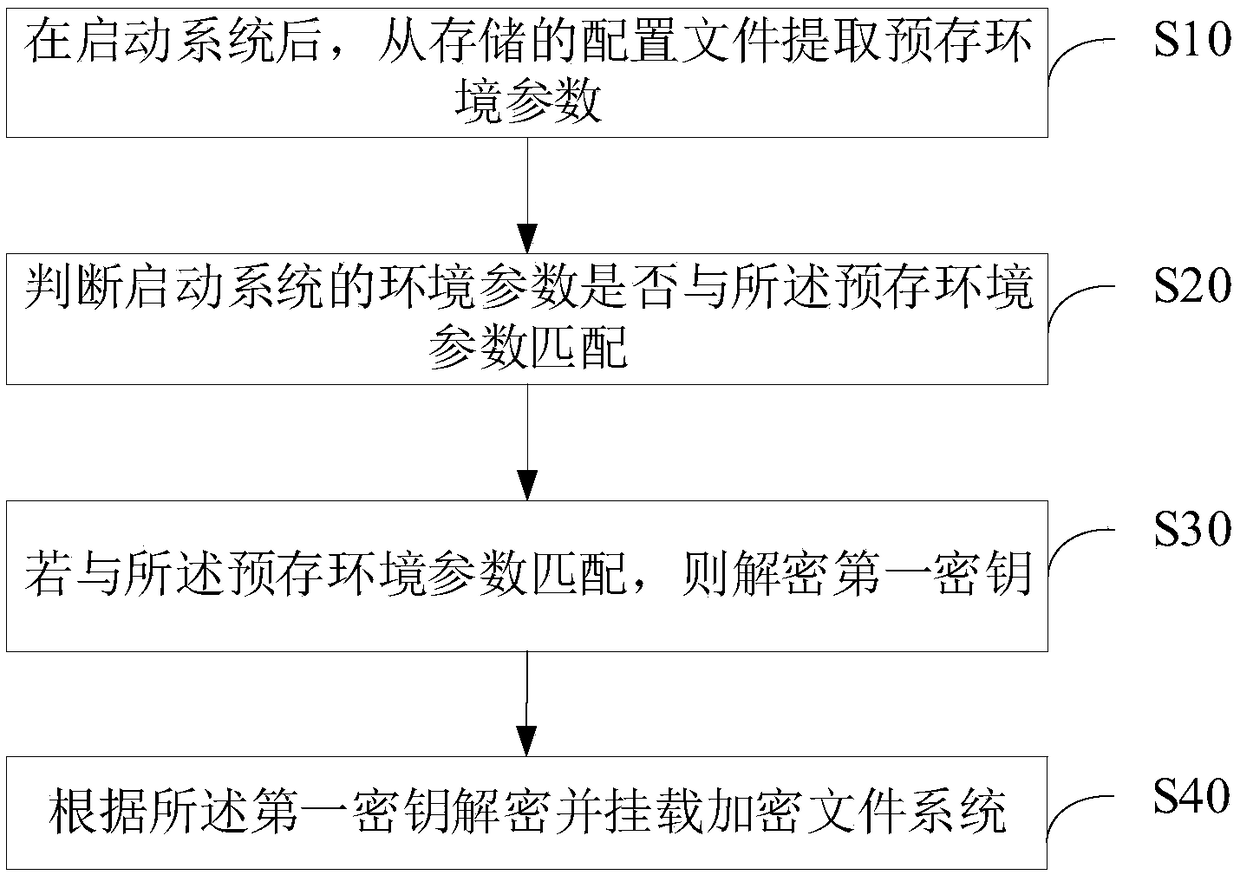
[0029] Please refer to figure 1 , the embodiment of the present application proposes a method for mounting an encrypted file system, including:
[0030] S10. After starting the system, extract the prestored environment parameters from the stored configuration file.
[0031] In this embodiment, the encrypted file system includes encrypted core data and non-encrypted data. Among them, core data includes but not limited to confidential data and core code; non-encrypted data includes configuration files. The above configuration file includes the recorded pre-stored environment parameters and the encrypted first key. The environment parameter refers to a set of verification data generated according to the hardware environment information and / or software environment information acquired by the system. In particular, the set of check data may only contain one check value. The pre-stored environment parameters refer to the verification data generated according to the hardware envi...
Embodiment 2
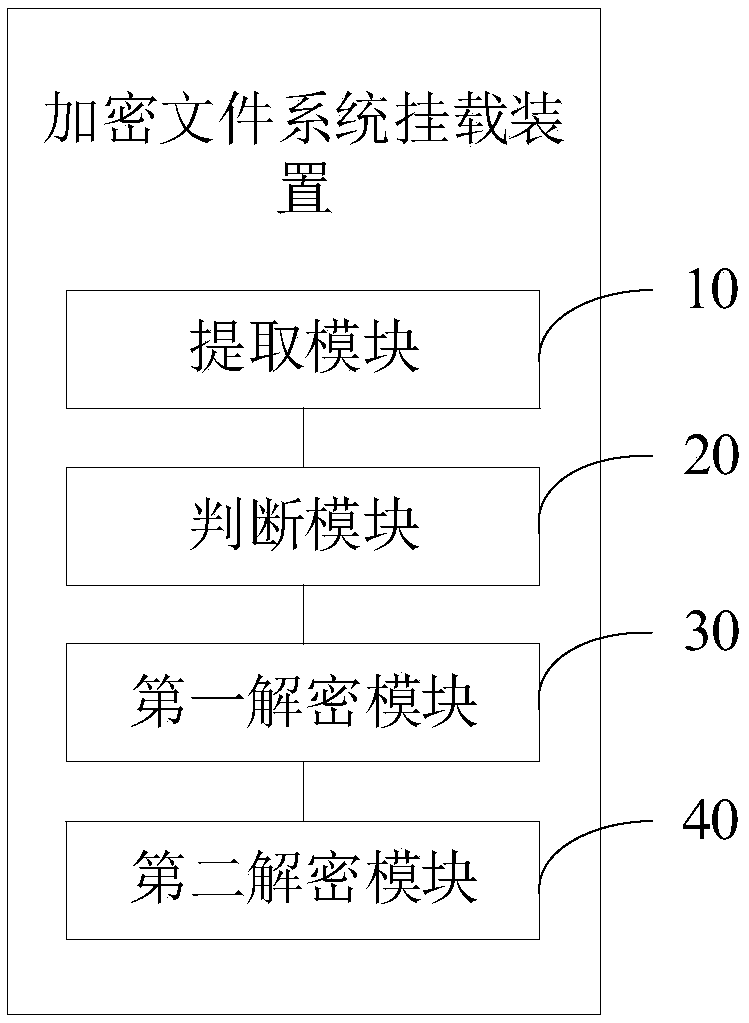
[0083] Please refer to figure 2 , the present invention also proposes an encrypted file system mounting device, comprising:
[0084] An extracting module 10, configured to extract the prestored environmental parameters from the stored configuration file after starting the system;
[0085] A judging module 20, configured to judge whether the environmental parameters for starting the system match the pre-stored environmental parameters;
[0086] The first decryption module 30 is configured to decrypt the first key if it matches the pre-stored environment parameter;
[0087] The second decryption module 40 is configured to decrypt and mount the encrypted file system according to the first key.
[0088] Optionally, the encrypted file system mount device also includes:
[0089] A monitoring module for monitoring real-time equipment operation input;
[0090] an input judging module, configured to judge whether the real-time device operation input matches the preset device opera...
Embodiment 3
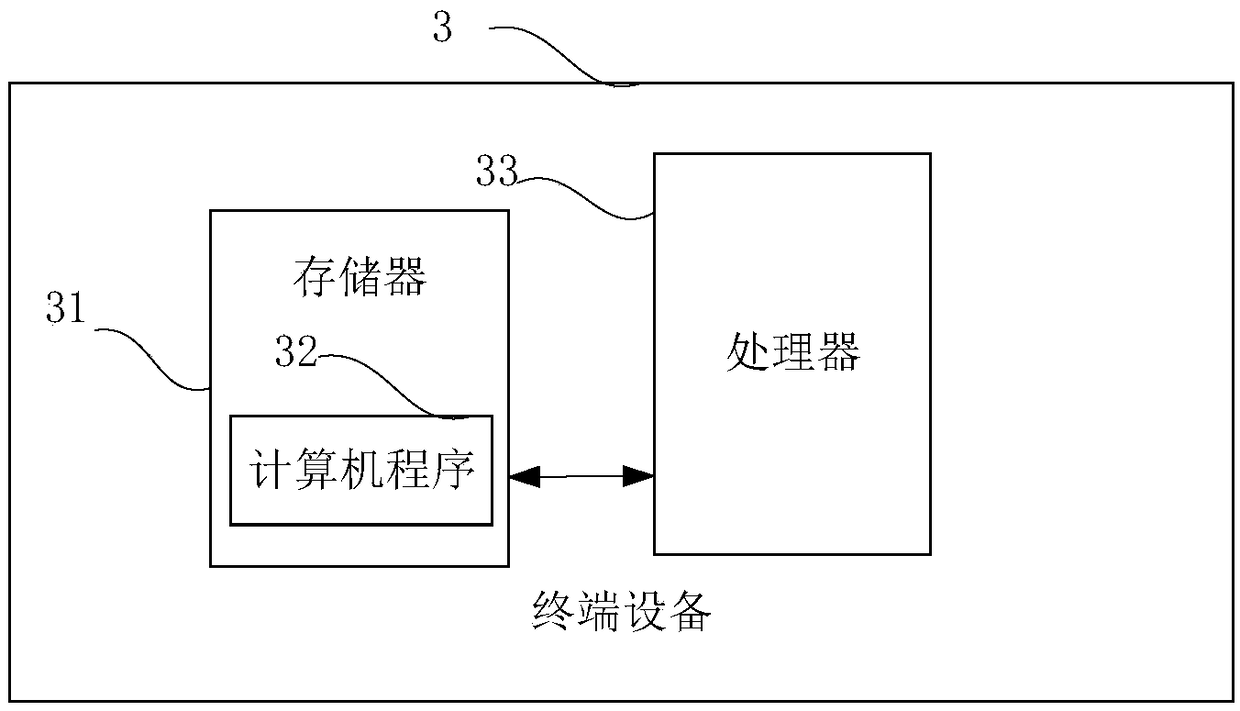
[0115] image 3 It is a schematic diagram of a terminal device provided by an embodiment of the present application. like image 3 As shown, the terminal device 3 of this embodiment includes: a processor 33, a memory 31, and a computer program 32 stored in the memory 31 and operable on the processor 33, such as an encrypted file system mounting program. When the processor 33 executes the computer program 32, the steps in the above-mentioned embodiments of the encrypted file system mounting method are implemented, for example figure 1 Steps S10 to S40 are shown. Alternatively, when the processor 33 executes the computer program 32, it realizes the functions of the modules / units in the above-mentioned device embodiments, for example figure 2 Functions of modules 10 to 40 shown.
[0116] Exemplarily, the computer program 32 can be divided into one or more modules / units, and the one or more modules / units are stored in the memory 31 and executed by the processor 33 to complete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com