Alarm method and system
An alarm system and monitoring server technology, applied in transmission systems, digital transmission systems, electrical components, etc., to ensure operation and improve efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
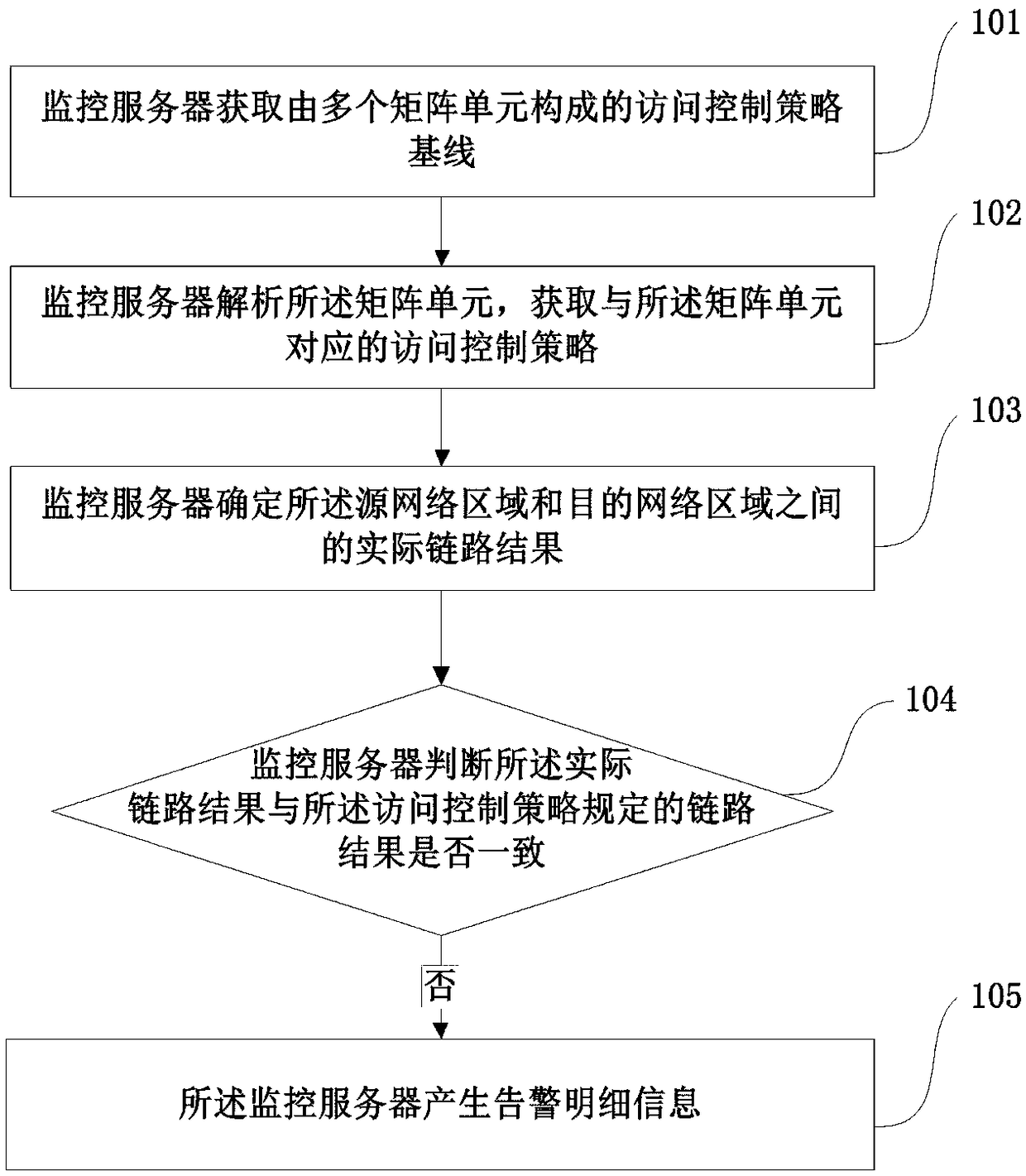
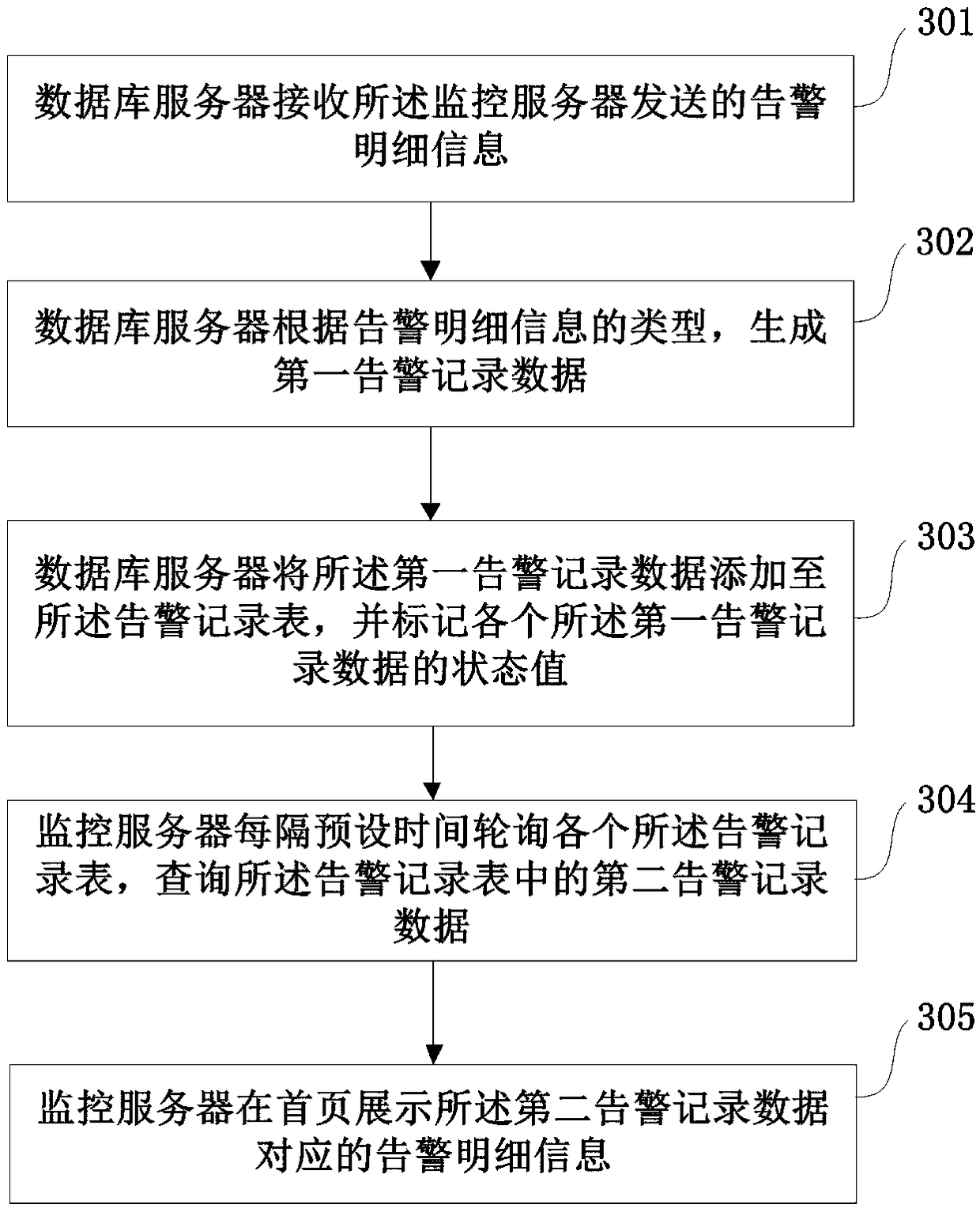
[0062] In order to solve the problem in the prior art that it is often necessary to further process the alarm information in the network system to find out the root cause of abnormal events, the present application provides an alarm method and system through the following embodiments.
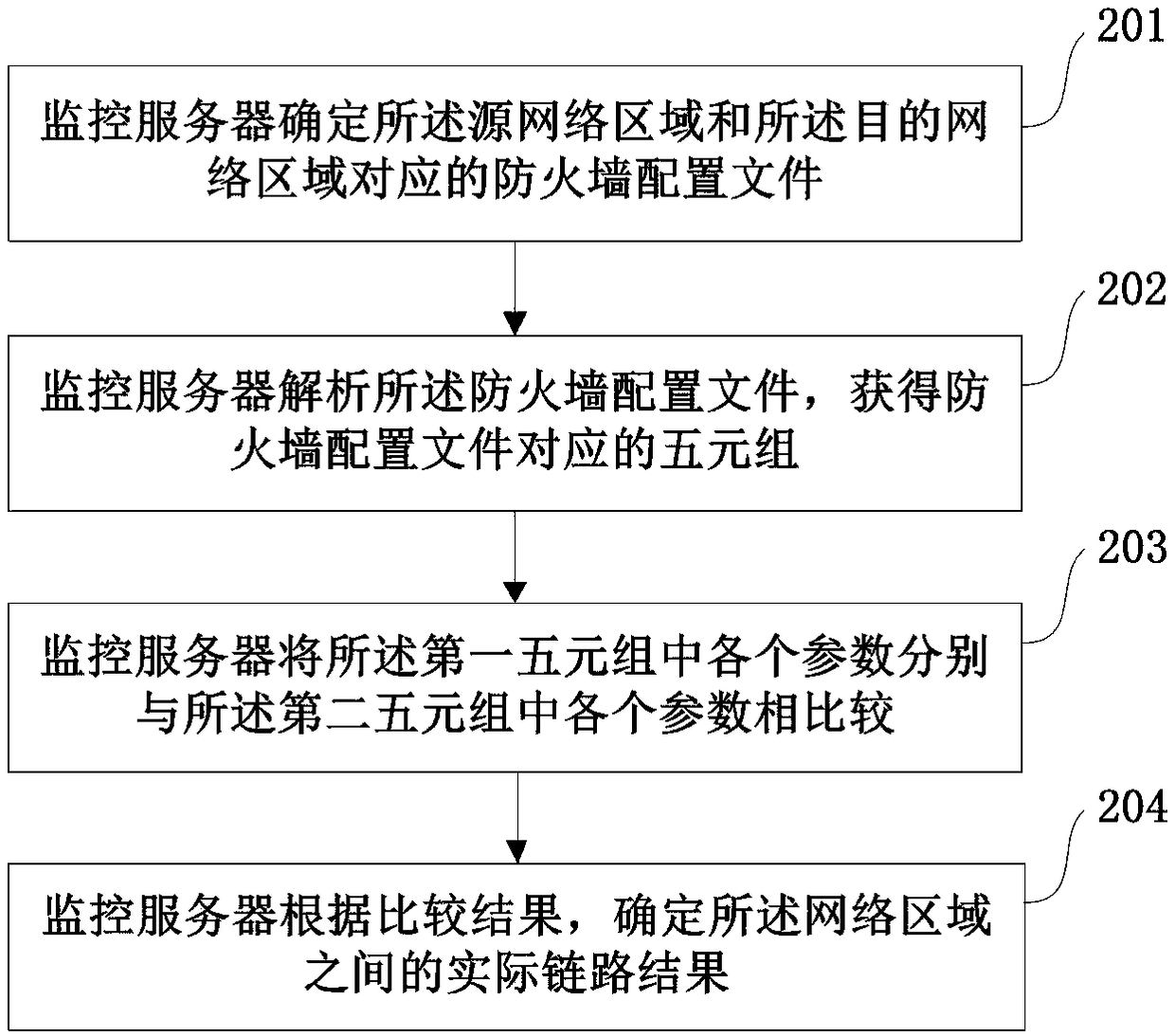
[0063] In the network system, in order to meet the needs of security management, the network system is often divided into multiple security domains, and mutual access between different security domains needs to follow specific rules. In the embodiment of this application, these rules are implemented by means of a firewall. Firewall settings Between each security domain, each firewall has different access control policies, and the access control policies of these firewalls are used to realize the security management of the network system. Inside each security domain, there are often different services, and the mutual access between each service also needs to follow certain rules. Therefore, a fir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com