A 6lowpan network intrusion detection method based on improved knn
A technology of network intrusion detection and intrusion detection, applied in network topology, electrical components, security devices, etc., can solve the problems of online detection difficulties, resource consumption, Smurf attacks, etc., and achieve the effect of reducing computational complexity and simplifying calculations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
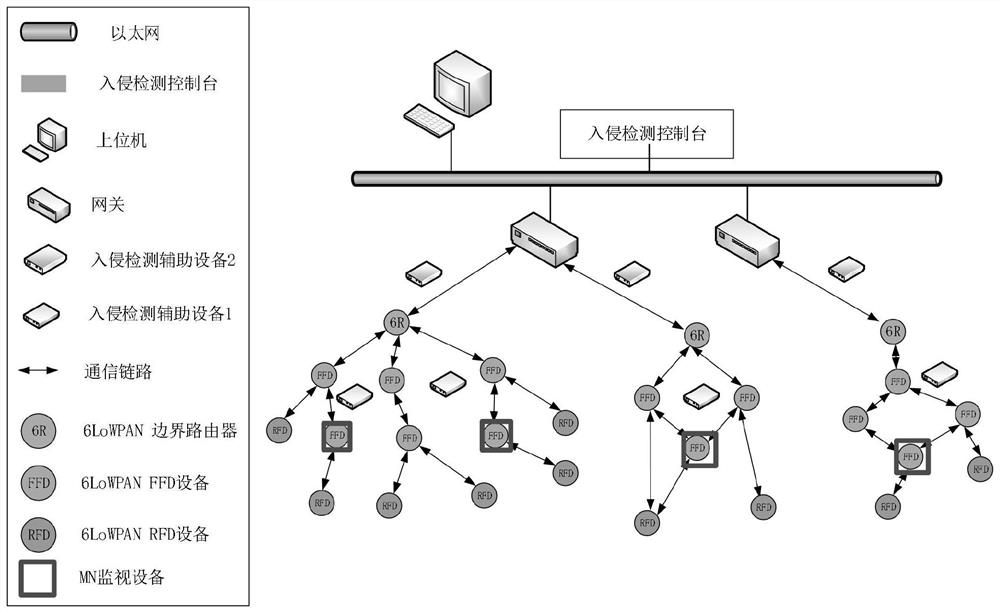
[0306] Attack result: Assume that the attack achieves that node 10 is captured. That is, node 10 is a puppet network element.
[0307] Intrusion Detection Implementation:
[0308] 1) constructing a network element state data table;
[0309] There are a total of 12 network elements in the network. Among them is a 6R network element.
[0310] Therefore, the amount of network element status data is taken as 20.
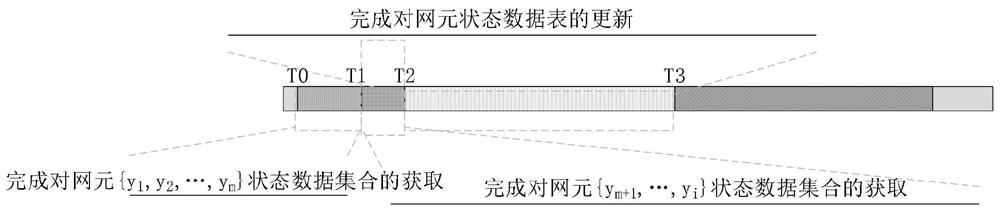
[0311] The network starts from running T 0 →T 1 , T 1 →T 2 Each network element captures data and forms a network element status data table on the console for the first time.
[0312] The algorithm for forming the network element status data table for the first time is as follows:
[0313]
[0314]
[0315] 2) Detection process: construct feature space and establish normal contour.
[0316]
[0317] Intrusion detection results:
[0318] It is easy to see that the parameter k=1 / 12*20≈2
[0319] The intrusion detection process calculates that the data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com