Memory access mode protection method based on data redundancy
A memory access and data redundancy technology, which is applied in electrical digital data processing, memory systems, instruments, etc., can solve the problem that it is difficult for attackers to effectively associate access operations, and achieve the effect of reducing communication overhead and avoiding leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The simulation of the invention class runs in the gem5 simulator environment. The simulator provides a full-fidelity simulation environment that can simulate memory access including CPU and memory modules, which is exactly the operation that the present invention aims to protect. It should be noted that the mathematical symbols in the following text have been agreed in the "Content of the Invention" section and will not be described here.
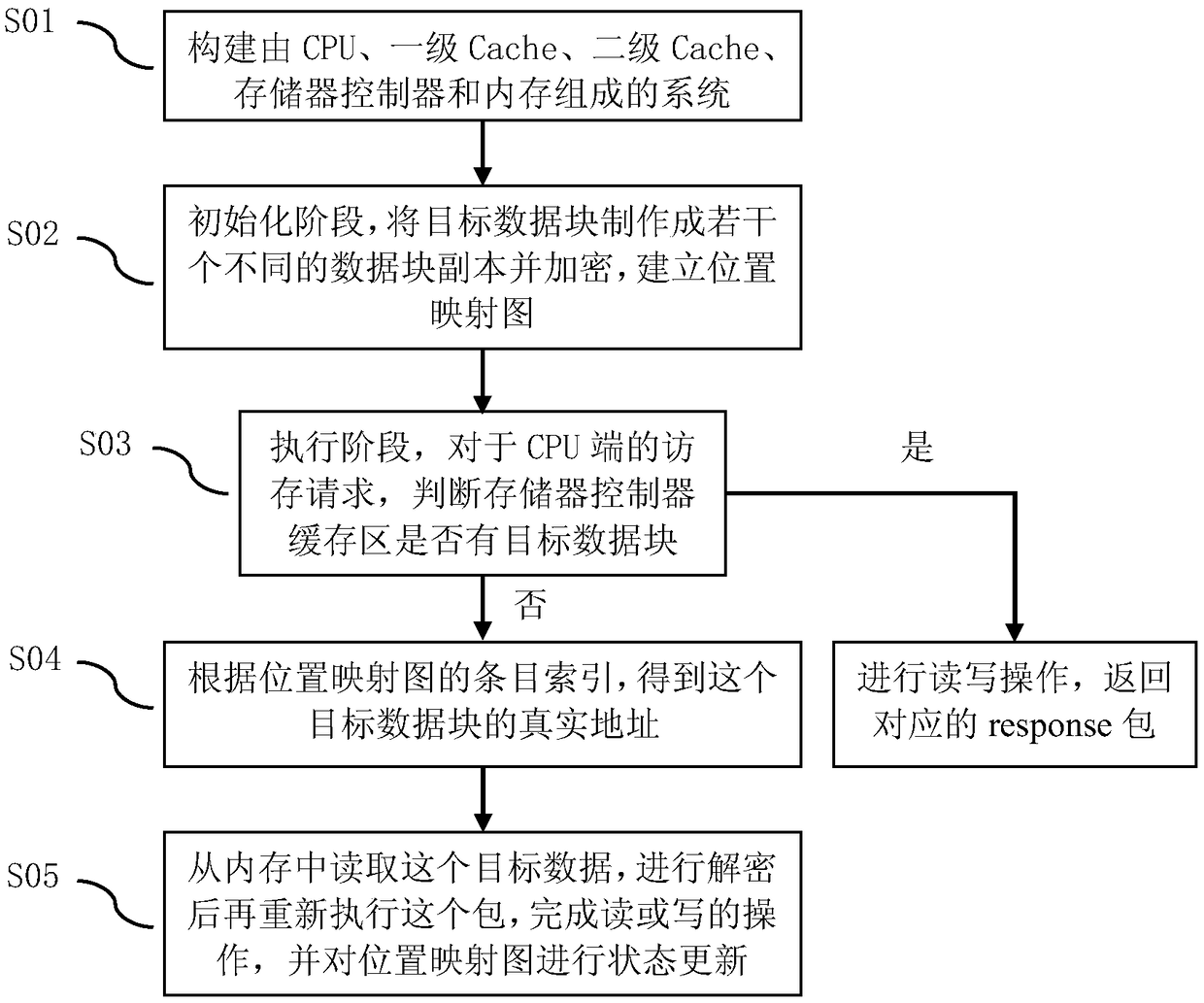
[0042] Such as figure 1 As shown, a data redundancy-based memory access mode protection method specifically includes the following steps:
[0043] S01. First construct a system consisting of a CPU, a first-level cache, a second-level cache, a memory controller (partially inherited from the native cache class) and memory. Wherein the memory controller intercepts the request of the secondary cache between the secondary cache and the memory. At the same time, h hash functions are preset.
[0044] S02. During the initialization proce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com