Intelligent anti-lost method based on user entering and exiting gate
An anti-lost, gate technology, applied in the direction of a single input/output port register, instruments, alarms, etc., can solve the hidden danger of mobile intelligent terminal volume and easy loss, mobile intelligent terminal legacy, and mobile intelligent terminal economic loss information Leakage and other problems to achieve the effect of preventing loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
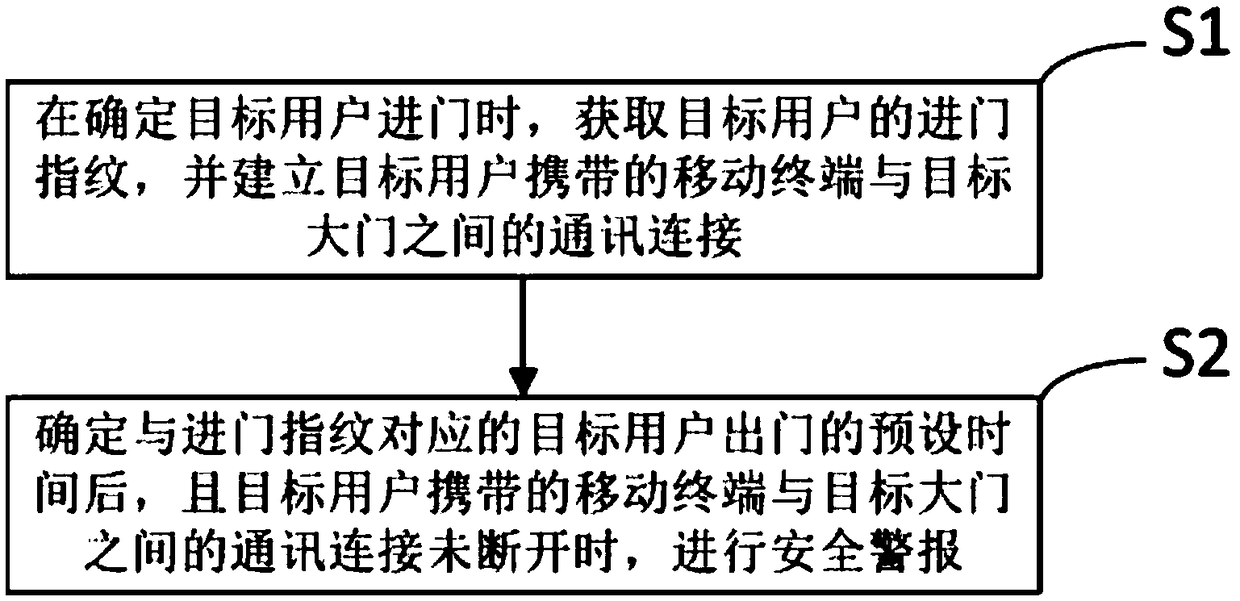
[0018] refer to figure 1 , a kind of intelligent anti-lost method based on the user entering and exiting the door proposed by the present invention, comprising:
[0019] Step S1, when it is determined that the target user enters the door, obtain the entry fingerprint of the target user, and establish a communication connection between the mobile terminal carried by the target user and the target gate, specifically including: acquiring The real-time pressure of the target user is determined to enter the door; the fingerprint of the target user is obtained according to the fingerprint collection device preset on the outside handle of the target door; the mobile terminal carried by the target user is connected to the same local area network as the target door to establish a connection between the mobile terminal and the target door. communication link between.
[0020] In the specific scheme, the real-time pressure acquired by the preset pressure sensor on the outside handle of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com