Network real name authentication system and method based on certificate chain technology
A real-name authentication and network technology, which is applied in the field of network real-name authentication of certificate chain technology, can solve problems such as low security, threats, and limited use of application scenarios, and achieve the effect of improving security and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
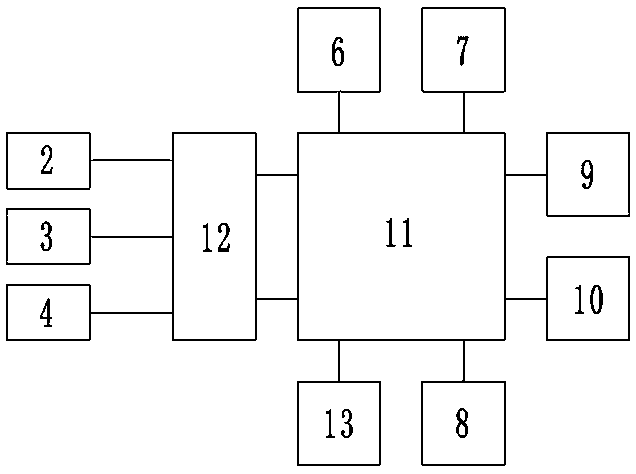
[0039] Such as Figure 1 to Figure 4 As shown, the present invention provides a network real-name authentication system based on certificate chain technology, including: a network real-name authentication terminal 1, a network real-name authentication server 2, an identity verification server 3, and a certificate verification server 4;
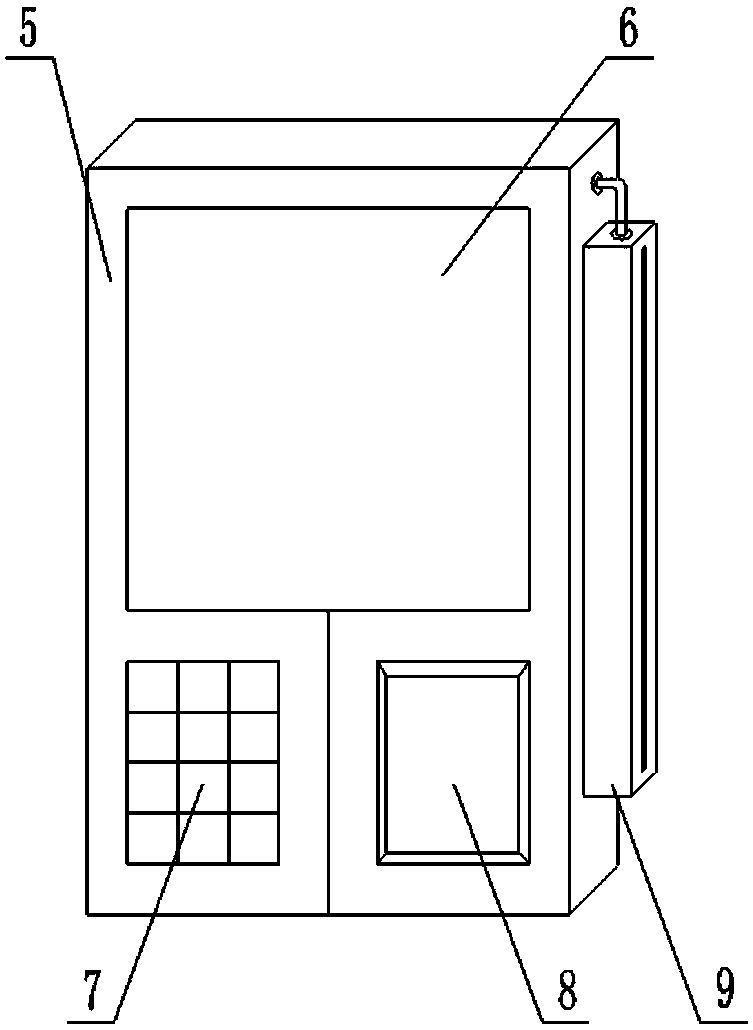
[0040] The network real-name authentication terminal 1 is specifically a hand-held mobile operation terminal, the main body is composed of a housing 5, the front of the housing 5 is provided with an LCD display 6, a keyboard 7 and a camera 8, and the side of the housing 5 is externally mounted. There is a portable scanner 9, and the bottom of the casing 5 is also provided with a port of a printer 10;
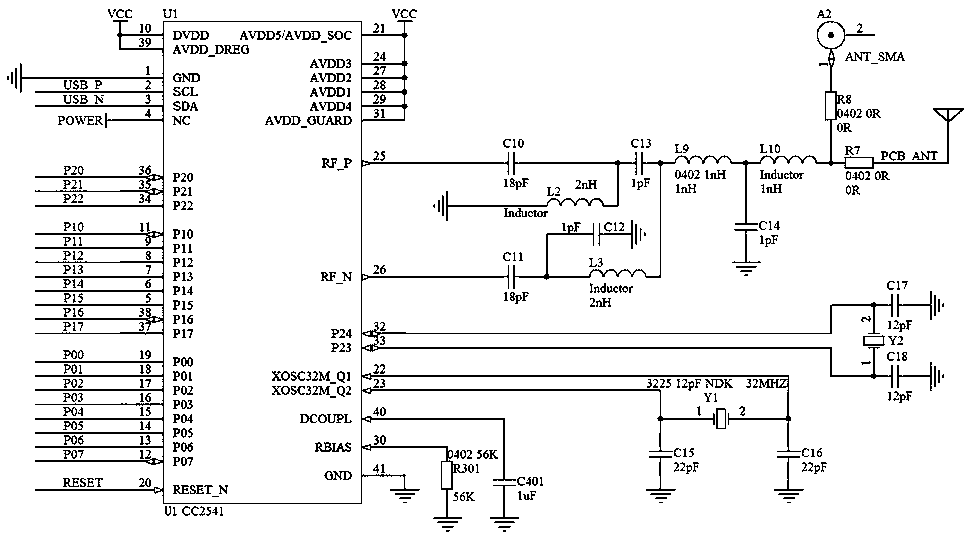
[0041] The inside of the housing 5 is provided with a control circuit board, the control circuit board is integrated with a central controller 11, and the central controller 11 communicates with the LCD display screen 6, the keyboard 7, the came...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com