Asymmetric image encryption based on ECC and chaos
An encryption method and asymmetric technology, applied in image communication, electrical components, etc., can solve problems such as low encryption efficiency and weak security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The implementation process of the present invention will be further described in detail below in conjunction with specific drawings and examples.
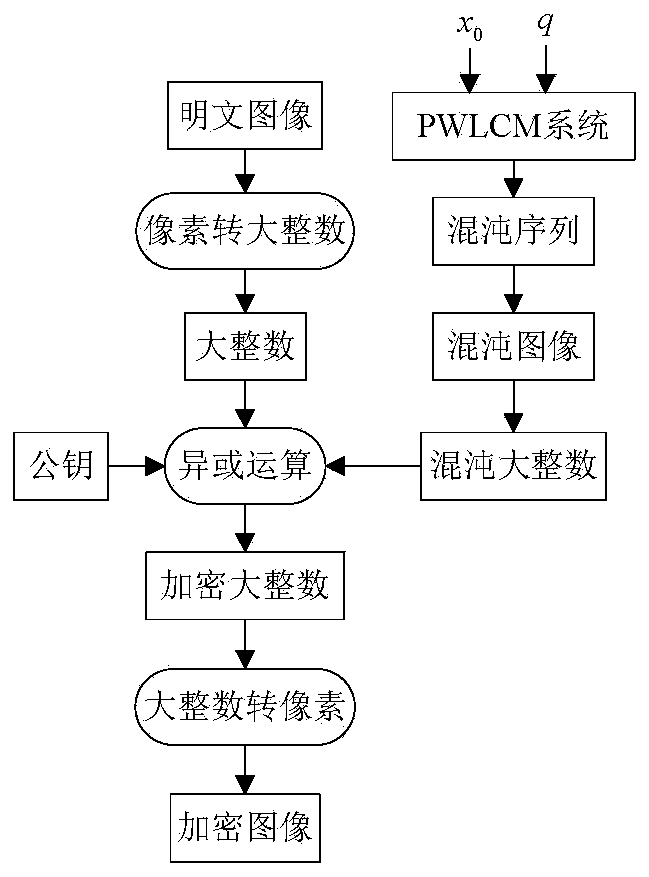
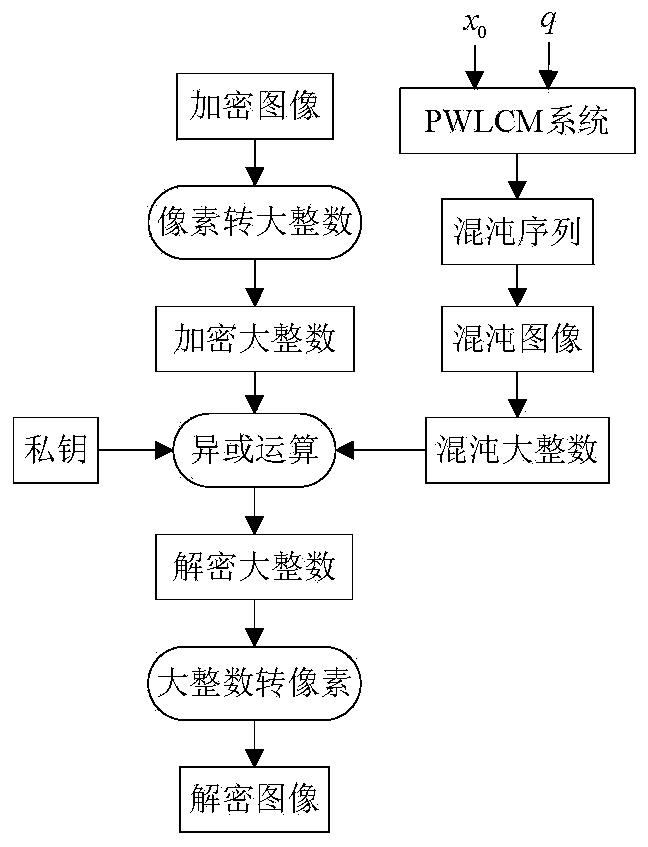
[0045] figure 1 is the encryption flowchart of this method, figure 2 is the decryption flowchart of the method.
[0046] The programming software used is MyEclipse 2015 CI, select image 3 A Lena image of size 512×512 is shown as the original interaction image. Using this method, Bob’s key generation steps are as follows:
[0047] Step K1: Select a key length of l =512-bit elliptic curve whose parameters are a =62948605579730632276664 21306476379324074715770622746227136910445450301914281276098027990968407983962691151853678563877834221834027439718238065725844264138, b =3245789008328967059274849 584342077916531909009637501918328323668736179176583263496463525128488282611559800773506973771797764811498834995234341530862286627和 p =89489622076502325516566028 151591534221626096440983545113445971872000570104135524399179343...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com