Method, device and equipment for generating data obfuscation rules
A technology of data generation and generation equipment, which is applied in the computer field, can solve problems such as malicious user attacks, omissions and errors, and incomprehension, and achieve the effects of increasing the risk of leakage, making it less prone to errors or omissions, and improving generation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
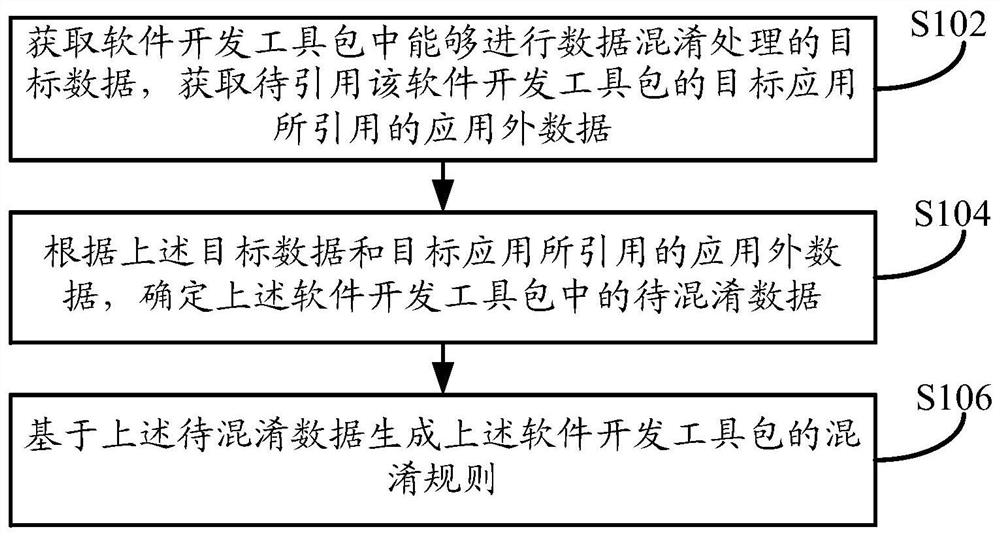
[0056] like figure 1 As shown, the embodiment of this specification provides a method for generating a data obfuscation rule, and the execution body of the method may be a terminal device or a server, where the terminal device may be a personal computer or the like. The server can be an independent server, or a server cluster composed of multiple servers, and the server can be a background server of a certain business (such as the development and upgrade of a certain application, etc.), or a website ( Such as the background server of an online shopping website or a payment application, etc.). The method can be used in processing such as generating a rule that can rewrite certain data to generate new data that is not readable by users or technicians but does not affect the original logic of the data. The method specifically may include the following steps:
[0057] In step S102, the target data capable of data obfuscation processing in the software development kit is obtained...
Embodiment 2
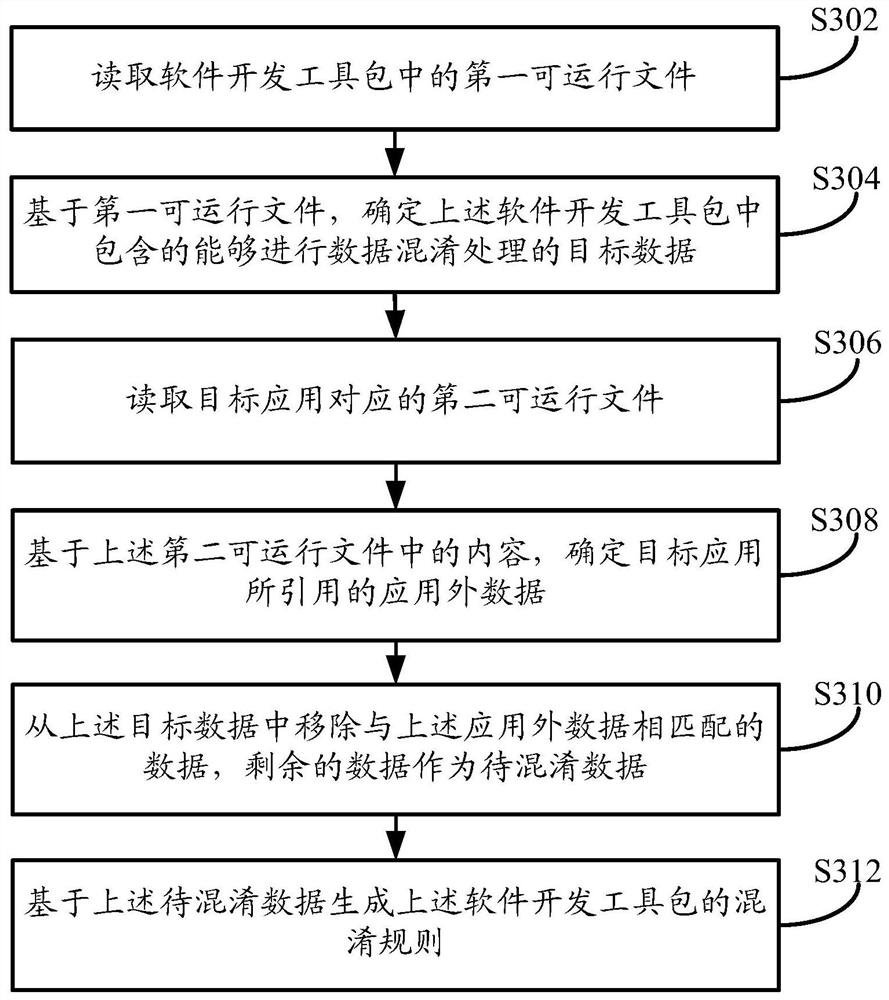
[0072] like image 3 As shown, the embodiment of this specification provides a method for generating a data obfuscation rule, and the execution body of the method may be a terminal device or a server, where the terminal device may be a personal computer or the like. The server can be an independent server, or a server cluster composed of multiple servers, and the server can be a background server of a certain business (such as the development and upgrade of a certain application, etc.), or a website ( Such as the background server of an online shopping website or a payment application, etc.). The method can be used in processing such as generating a rule that can rewrite certain data to generate new data that is not readable by users or technicians but does not affect the original logic of the data. The method specifically may include the following steps:
[0073] In step S302, the first executable file in the software development kit is read.
[0074] Wherein, the first exec...
Embodiment 3
[0091] like Figure 4 As shown, the embodiment of this specification provides a method for generating a data obfuscation rule, and the execution body of the method may be a terminal device or a server, where the terminal device may be a personal computer or the like. The server can be an independent server, or a server cluster composed of multiple servers, and the server can be a background server of a certain business (such as the development and upgrade of a certain application, etc.), or a website ( Such as the background server of an online shopping website or a payment application, etc.). The method can be used in processing such as generating a rule that can rewrite certain data to generate new data that is not readable by users or technicians but does not affect the original logic of the data. The method specifically may include the following steps:
[0092] In step S402, read the first dex file and the mapping file in the software development kit.
[0093] Wherein, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com