A method and system for protecting personal privacy
A personal privacy and privacy technology, applied in the field of mobile Internet, can solve the problem of insufficient personal privacy protection, and achieve the effect of strong control and authority binding, good compatibility, and protection of private data.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] In order to make the object, technical solution and advantages of the present invention clearer, the technical solution of the present invention will be further described in detail below in conjunction with specific embodiments. It should be noted that, in the case of no conflict, the embodiments of the present application and the features in the embodiments can be combined with each other arbitrarily.
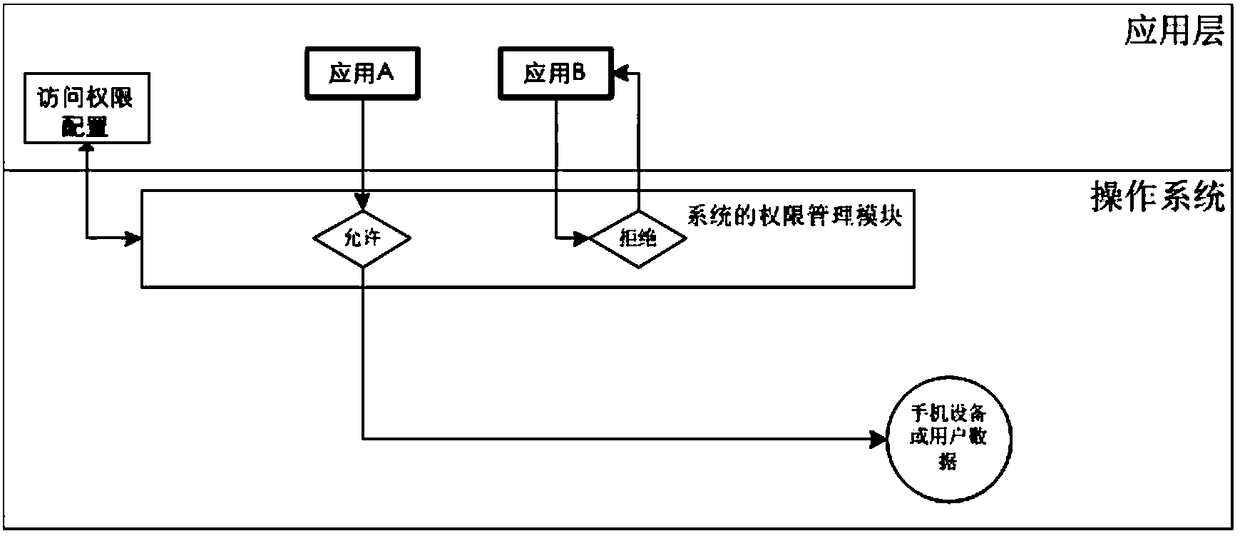
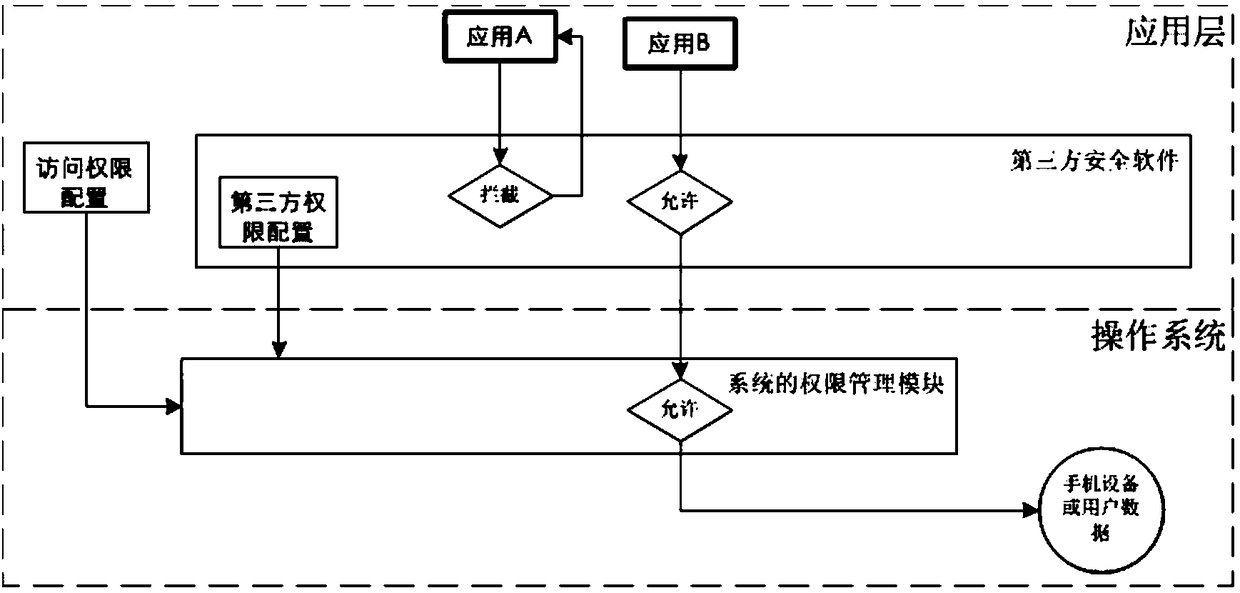
[0065] The inventor of the present application concludes that the rights management system in the related art adopts a black and white rights management method. In addition to denying and allowing access to privacy permissions, the inventor proposes to add "allow access to private data, but access to non-real data or virtual devices", and provide extended configuration so that users can choose how to access non-real data.
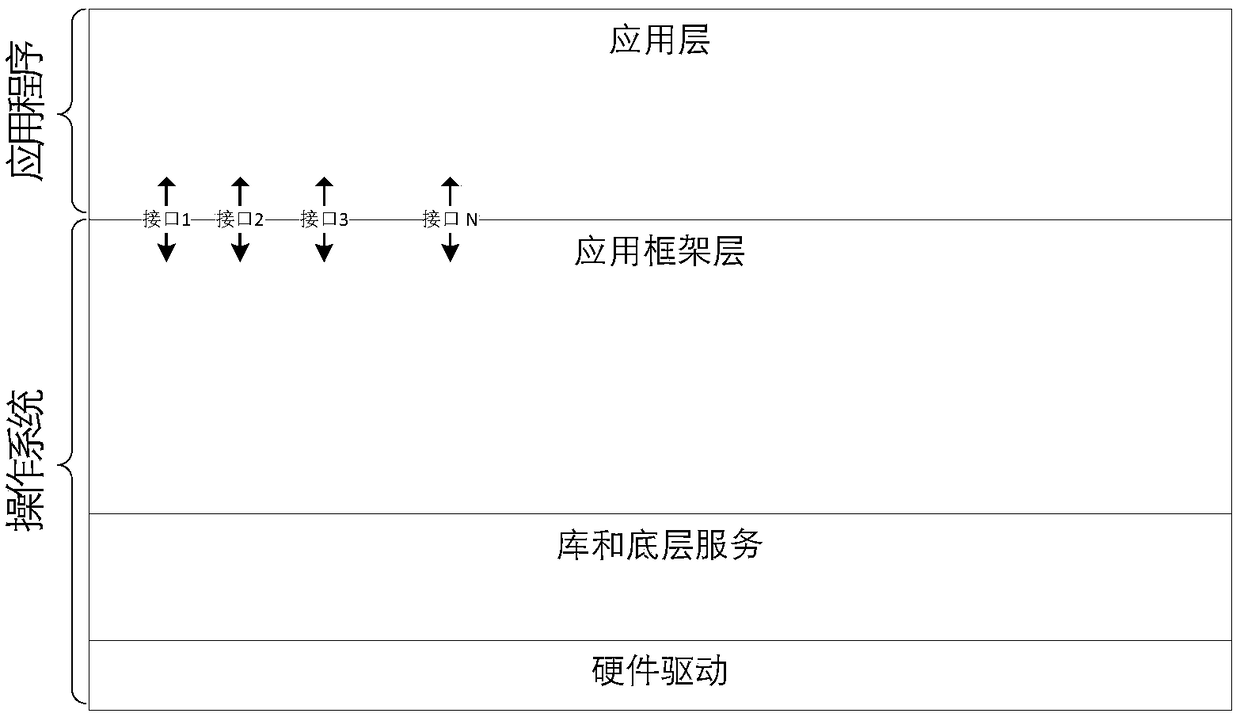
[0066] In addition, the operating systems of mobile terminals currently use a layered architecture, such as image 3 shown. The interface that or...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com