Authentication method and system, storage medium, and electronic device based on digital certificate
A technology of digital certificates and authentication methods, applied in digital transmission systems, transmission systems, electrical components, etc., can solve problems such as insufficient security enhancement methods, security key leakage, and insufficient security protection strength, and achieve the effect of ensuring data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
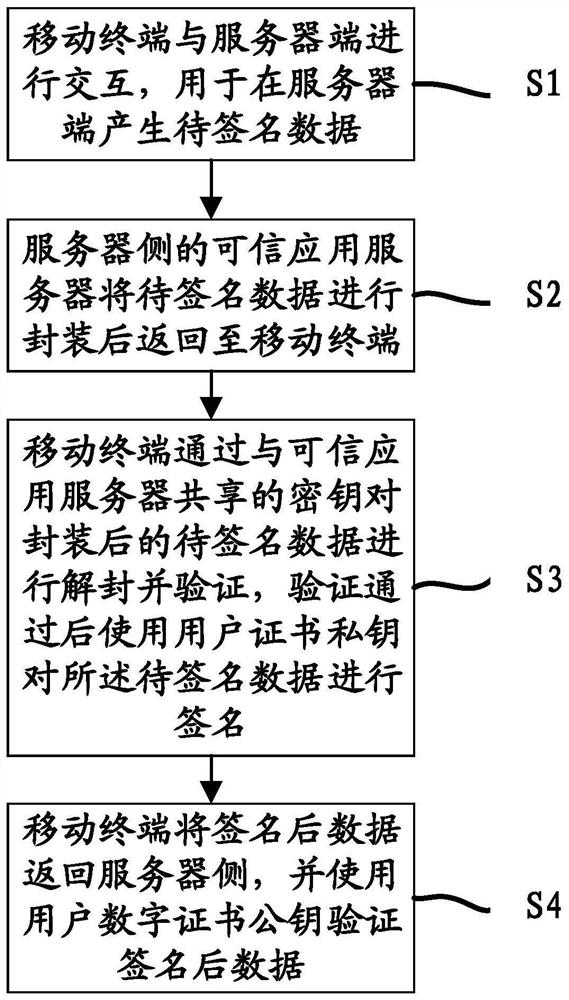
[0059] Embodiment 1, the authentication method based on digital certificate such as figure 2 As shown, it should be understood that the premise of the process described in this embodiment is that the digital certificate has been initialized and issued, and this embodiment is configured as an application example of a digital certificate, including the following steps:
[0060] S11. The mobile terminal interacts with the mobile application server; wherein, the user has applied for and installed a digital certificate application in the security unit of the mobile terminal, and the mobile application server has also retained the user's public key certificate; the user interacts with the server through the mobile application , to generate the data to be signed that needs to be signed by the user's digital certificate. For example, the user can trigger a third-party service to call the call interface module in the mobile terminal to obtain the device information and digital certifi...
Embodiment 2
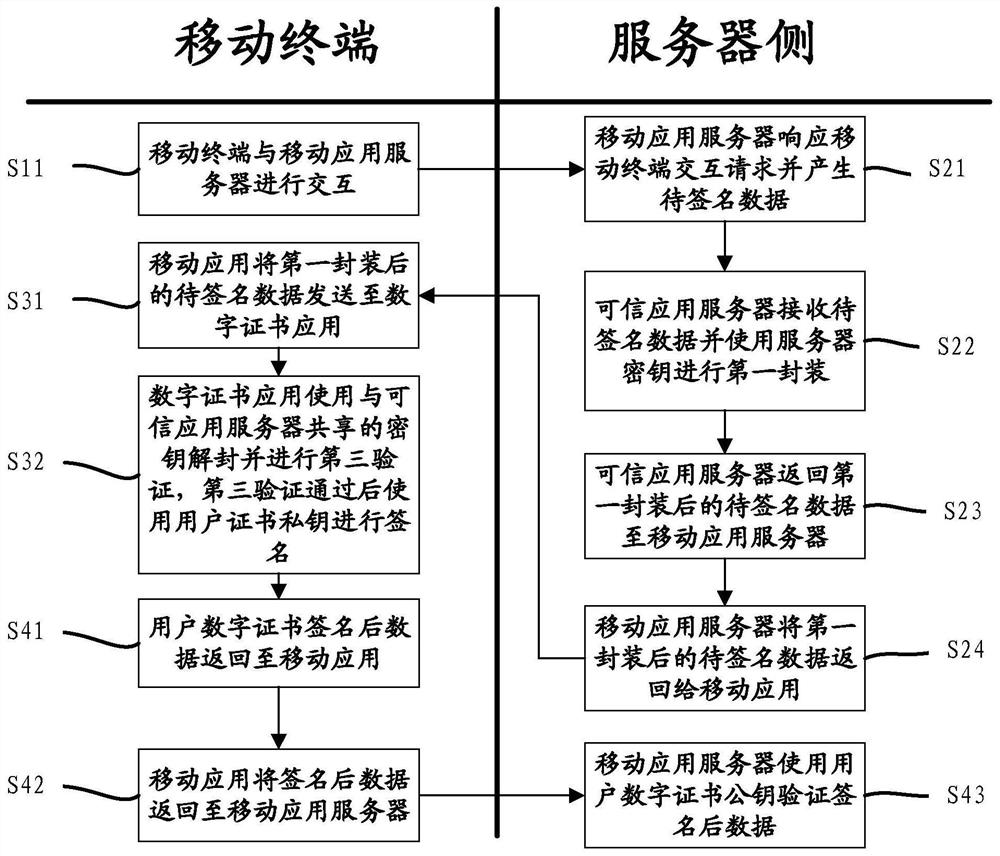
[0070] Embodiment 2, the authentication method based on digital certificate such as Figure 4 As shown, it should be understood that the premise of the process described in this embodiment is that the digital certificate has been initialized and issued. This embodiment is configured as an application example of a digital certificate, including the following steps:
[0071]S11. The mobile terminal interacts with the mobile application server; wherein, the user has applied for and installed a digital certificate application in the security unit of the mobile terminal, and the mobile application server has also retained the user's public key certificate; the user interacts with the server through the mobile application , to generate the data to be signed that needs to be signed by the user's digital certificate. For example, the user can trigger a third-party service to call the call interface module in the mobile terminal to obtain the device information and digital certificate ...
Embodiment 3
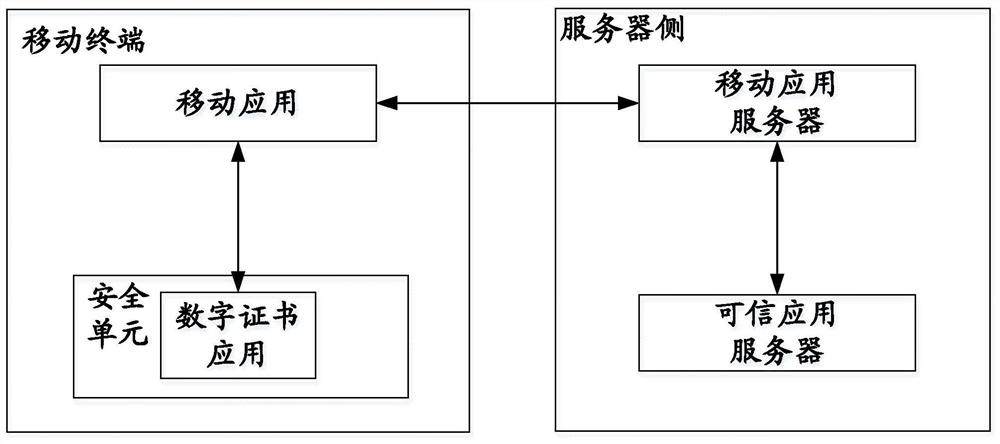
[0084] Example 3, such as image 3 As shown, the authentication system based on digital certificates includes a security unit built in a mobile terminal, a mobile application server, and a trusted application server; the mobile application server has a user digital certificate public key built in, and a digital certificate is installed in the security unit Application; Among them, the digital certificate application is a string of numbers that marks the identity information of the communication parties in the network communication, and provides a way to verify the identity of the communication entity on the Internet. In this embodiment, it is issued to the user by a legal authority, and the user's certificate corresponding private key is stored in the digital certificate application in the security unit of the mobile terminal, and the user's public key certificate can be obtained by the mobile application server from the legal authority and used for Subsequent verification of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com