Method for protecting key string data in IOS, storage medium, equipment and system
A keychain and data technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as user loss and high security risks, and achieve the effect of protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
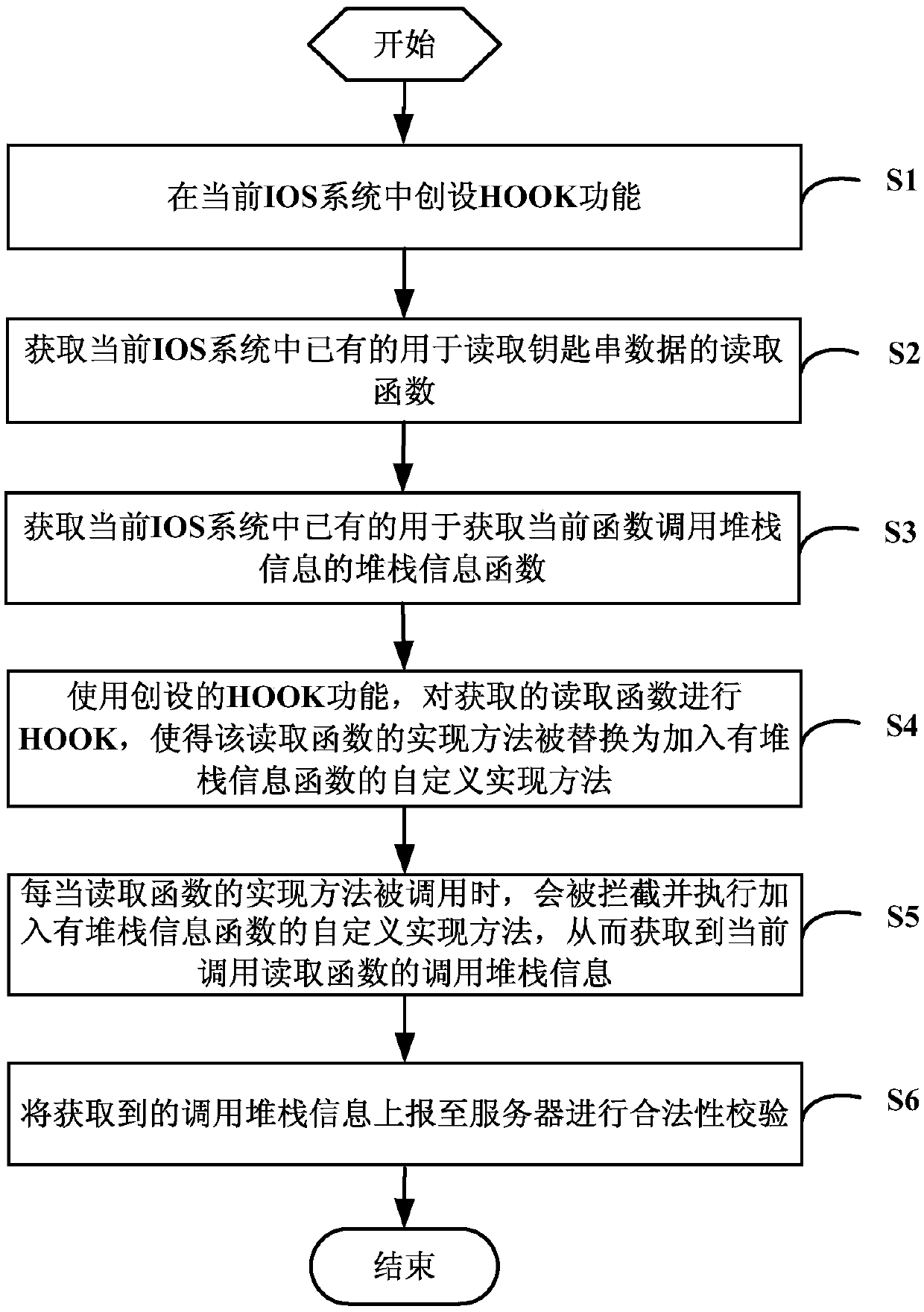
[0035] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
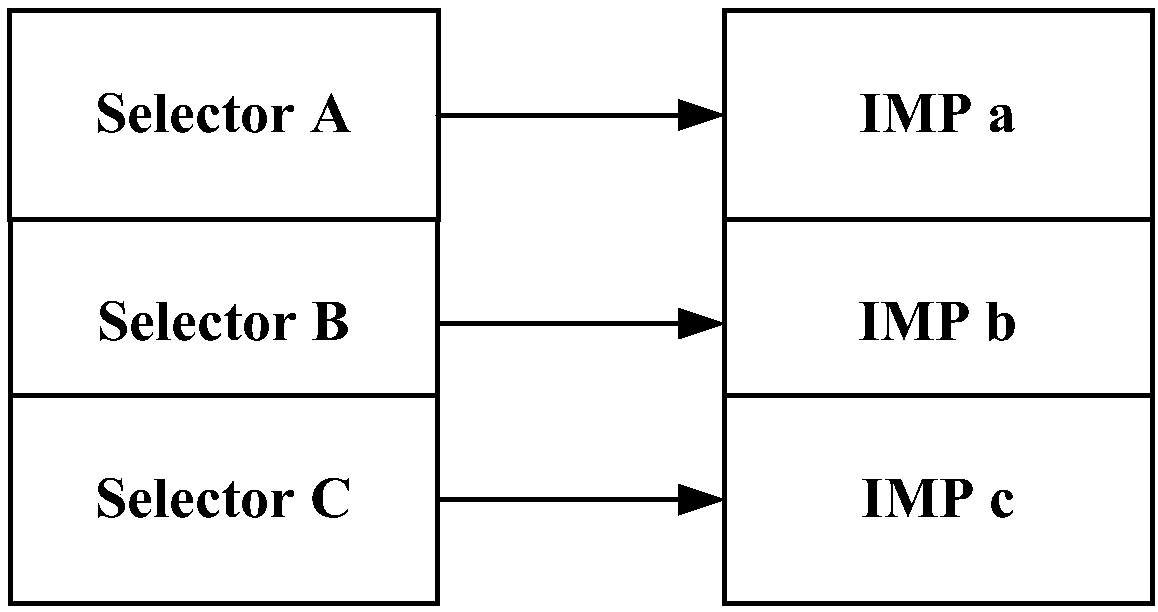
[0036]The design idea of the present invention is: write a HOOK (hook interception) function in advance, this HOOK function can add new method in original function, and through the binding of method, when original function is called, it will be intercepted and execute the added new method. method; then, use the written HOOK function to HOOK the reading function of the system to read the keychain data, and add a function to obtain the current function call stack information in the reading function, so as to obtain all the read keychain data function call stack information; and then report the obtained function call stack information to read the keychain data to the server for legality verification, and block the reading operations that do not meet the legal requirements, so as to effectively prevent hackers from reading The purpose o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com