A zero-copy full mirroring system and method for large data static database desensitization
A data desensitization and database technology, applied in digital data protection, electronic digital data processing, computer security devices, etc., can solve the problems of spending a lot of time configuring desensitization rules, occupying database resources, and time-consuming, etc., to ensure consistency Sex and business relevance, meet the scene requirements, and ensure the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0107] For better understanding of the present invention, the present invention is described in detail below with reference to the accompanying drawings.
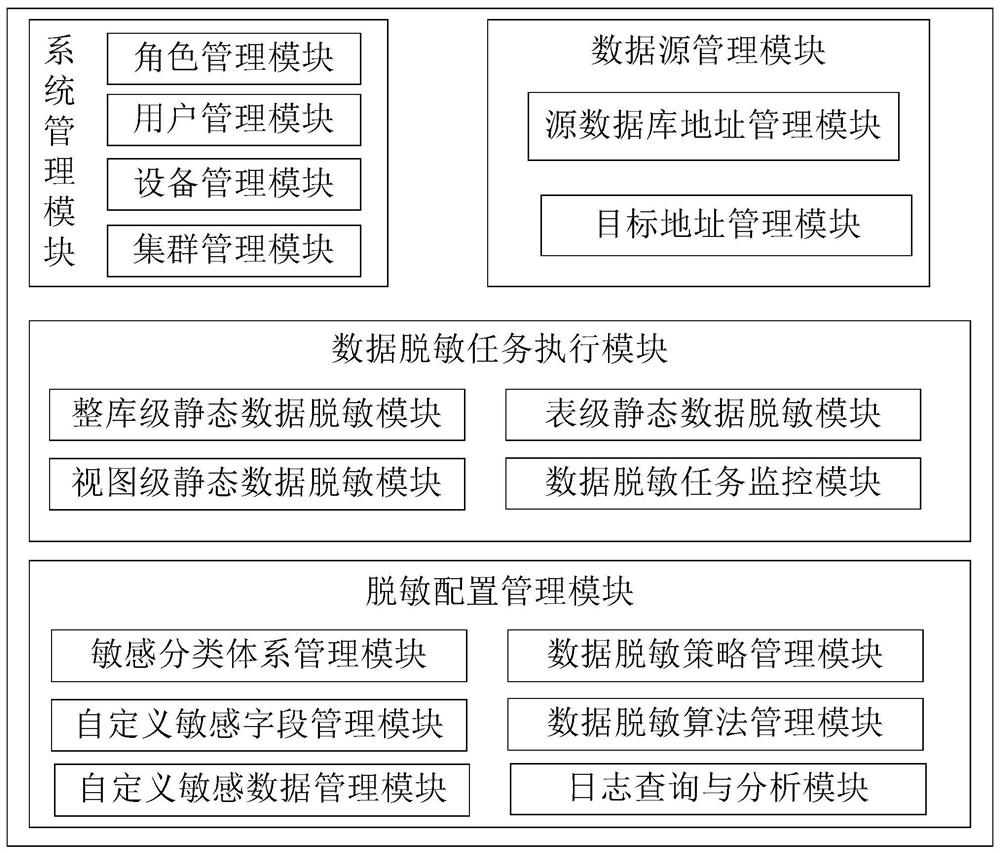
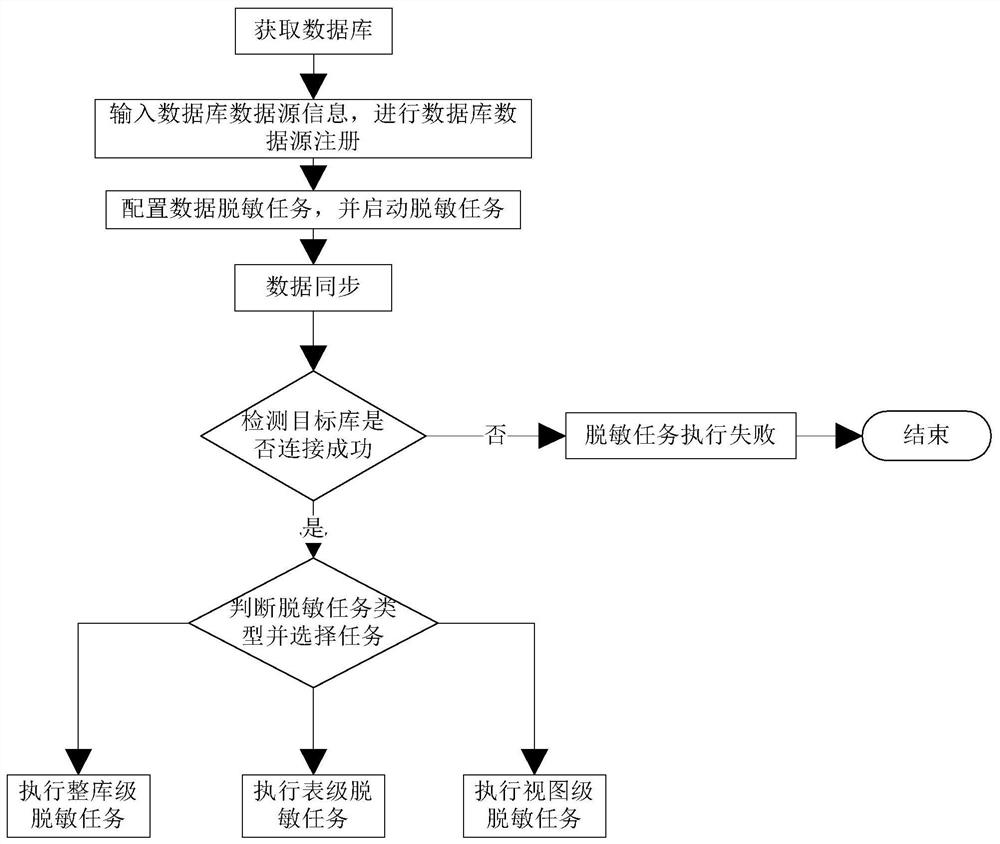
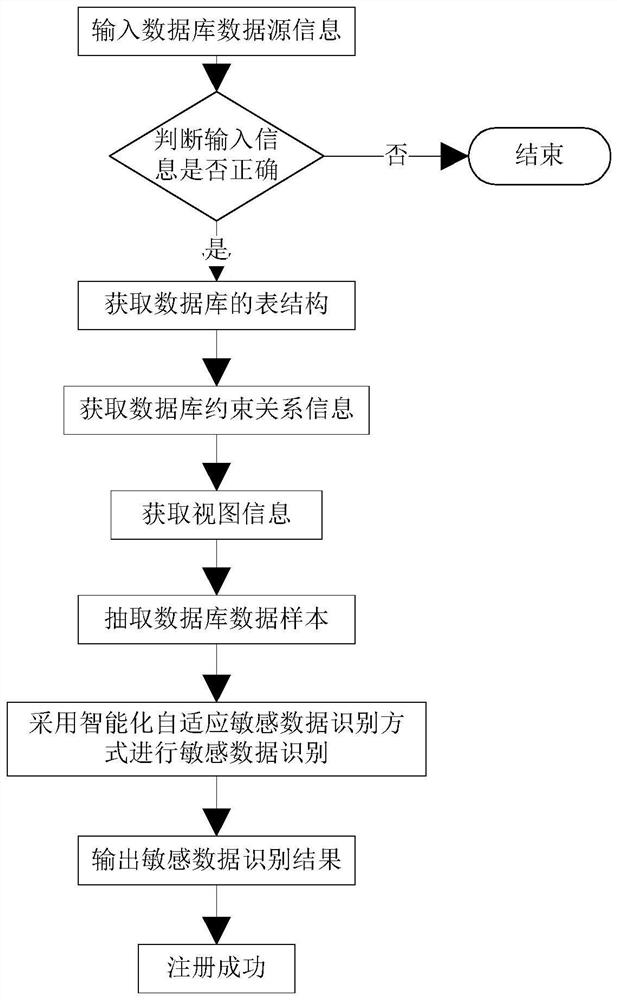
[0108] A zero-copy full mirror big data static database desensitization system mainly includes four modules: system management module, data source management module, data desensitization task execution module and desensitization configuration management module, wherein the data desensitization task execution module is the whole system. the core of the system. like figure 1 As shown in the figure, a zero-copy full-mirror big data static database desensitization system of the present invention includes a system management module that manages the basic functions of the system, a data source management module that manages the source database address and target address of the system, It realizes the configuration and execution of the desensitization task and the monitoring data desensitization task execution module, and the des...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com