Database transparent encryption method and device, electronic device and storage medium
A transparent encryption and database technology, applied in digital data protection, electronic digital data processing, special data processing applications, etc., can solve problems such as difficult to develop databases, and achieve the effect of reducing development difficulty and development costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
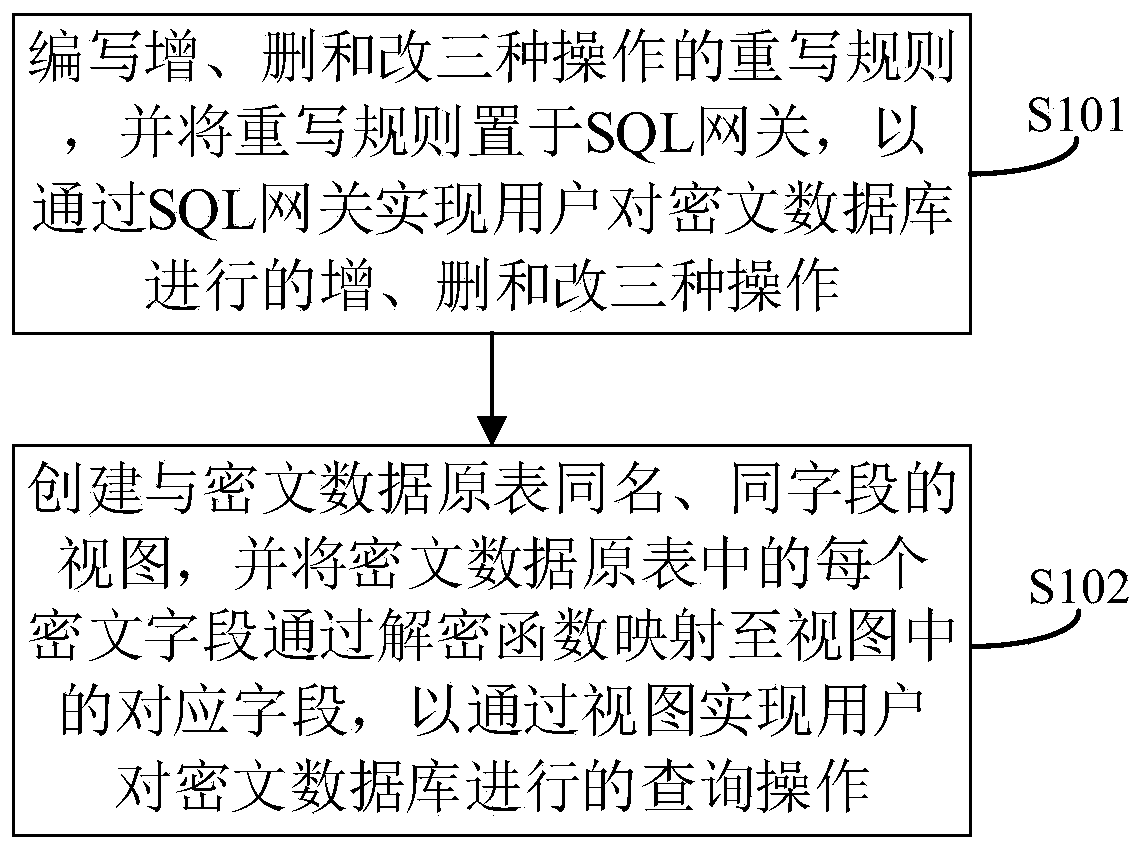
[0055] See figure 1 , figure 1 A flow chart of a database transparent encryption method provided by an embodiment of the present disclosure, which includes the following steps:
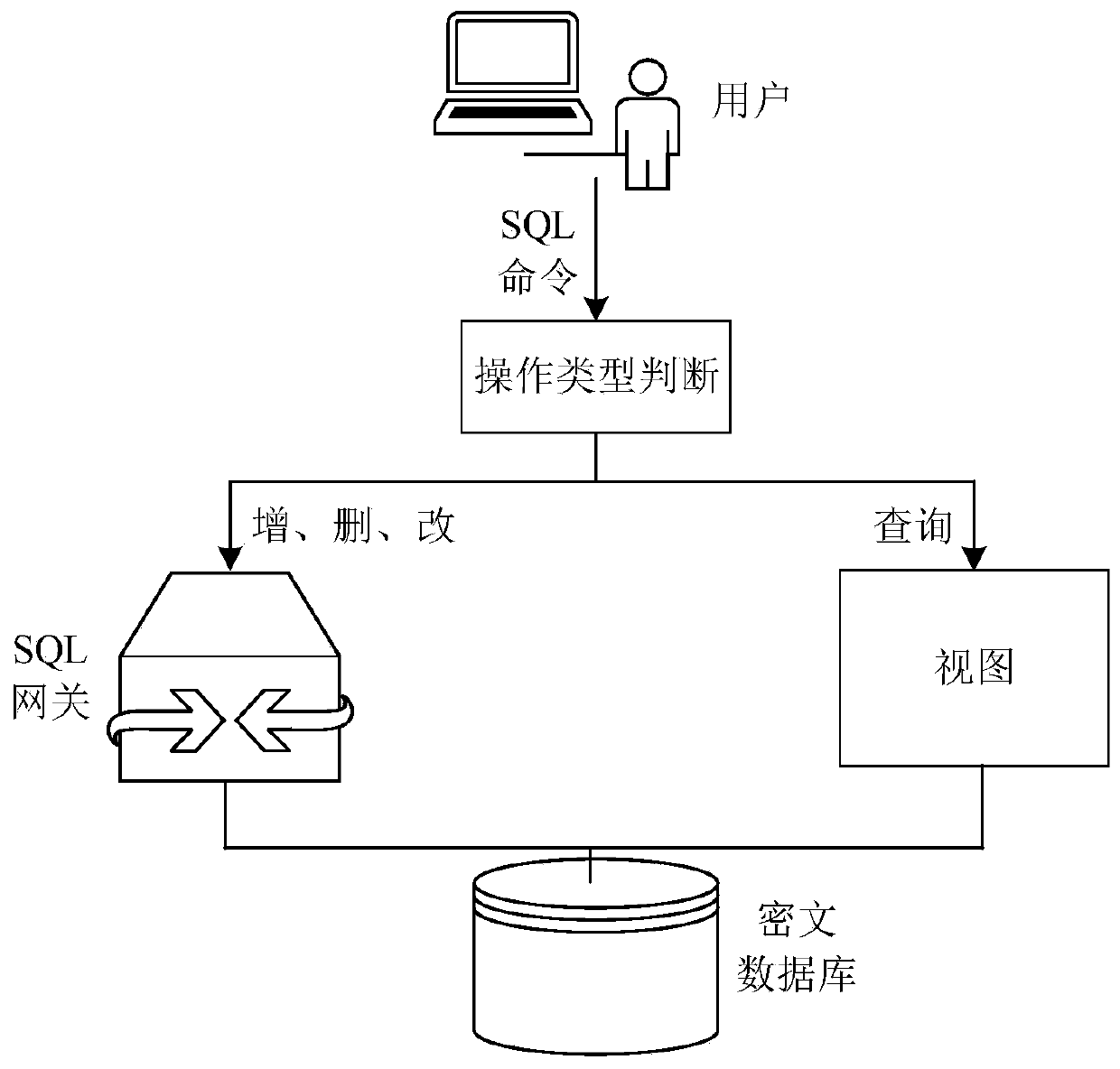
[0056] S101: Write rewriting rules for three operations of adding, deleting and modifying, and place the rewriting rules in the SQL gateway, so as to realize the three operations of adding, deleting and modifying the ciphertext database by the user through the SQL gateway;
[0057] Different from the existing technology that needs to write the four rewriting rules of adding, deleting, modifying and checking, this application only needs to write the three rewriting rules of adding, deleting and modifying which are less difficult to develop, less time-consuming and less costly rules, and put them into the SQL gateway on the upper layer of the ciphertext database, so that through the built-in rewriting rules in the SQL gateway, the common SQL commands of the three types of addition, deletion, and modifi...
Embodiment 2
[0077] See Figure 4 , Figure 4 It is a flowchart of a method for determining the operation type of an SQL command based on a keyword in the database transparent encryption method provided by the embodiment of the present disclosure. On the basis of Embodiment 1, this embodiment provides a method for determining the SQL command based on a keyword The method of the operation type includes the following steps:
[0078] S301: Using keywords of different access types to match the character strings contained in the SQL command to obtain matching keywords;
[0079] S302: Use the access type to which the matching keyword belongs as the operation type of the SQL command.
[0080]This embodiment aims to use keywords of different access types to actively match the character strings contained in the SQL command, wherein the various types of keywords used for active matching can also form a corresponding keyword set, each type of keyword Combining the access type strings corresponding...
Embodiment 3
[0087] See Figure 5 , Figure 5 A structural block diagram of a database transparent encryption device provided by an embodiment of the present disclosure, the device may include:
[0088] The addition, deletion and modification operation processing unit 100 is used to write the rewrite rules for the three operations of addition, deletion and modification, and place the rewrite rules in the SQL gateway, so as to realize the addition, deletion and modification of the ciphertext database by the user through the SQL gateway three operations;
[0089] The query operation processing unit 200 is configured to create a view with the same name and fields as the original table of ciphertext data, and map each ciphertext field in the original table of ciphertext data to a corresponding field in the view through a decryption function, so as to pass the view Realize the query operation performed by the user on the ciphertext database.
[0090] Further, the database transparent encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com