Network request method, network authentication method, terminal equipment and server
A network request and network authentication technology, applied in the field of communication, can solve the problems of terminal device system incompatibility, high development cost, and difficulty in development for developers, so as to avoid incompatibility, reduce development difficulty and development cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
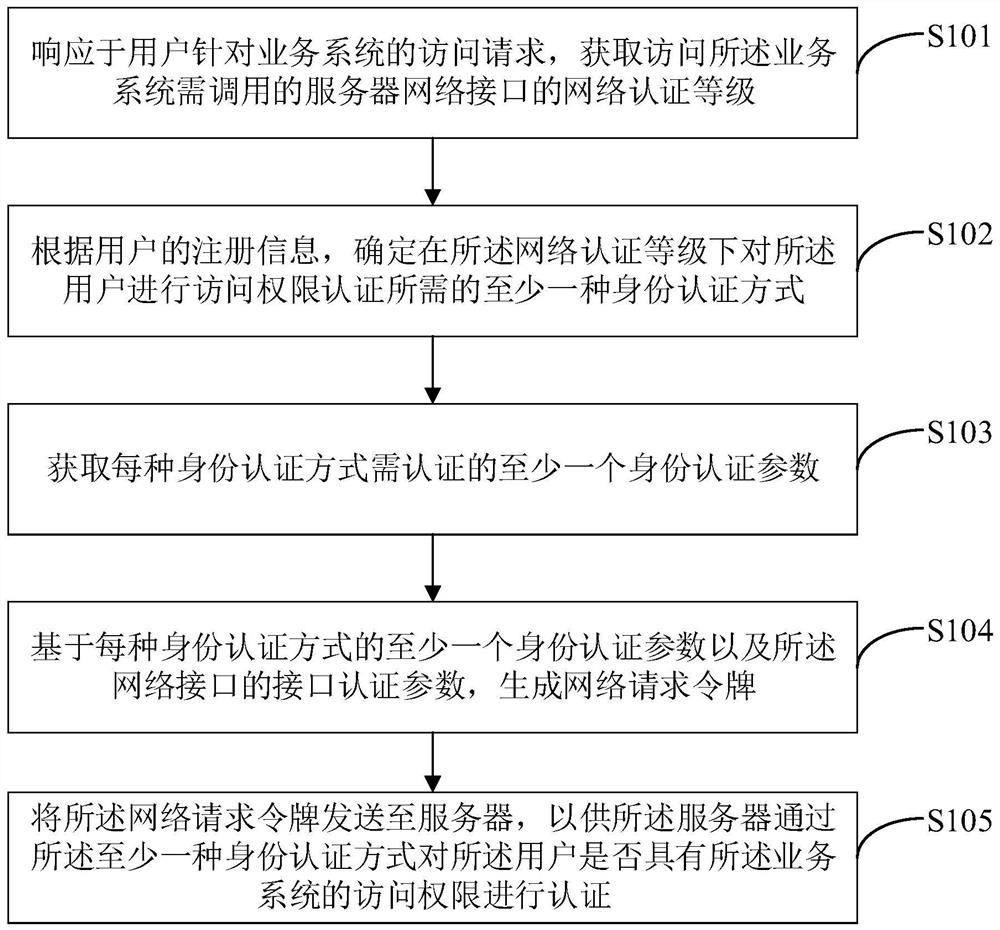
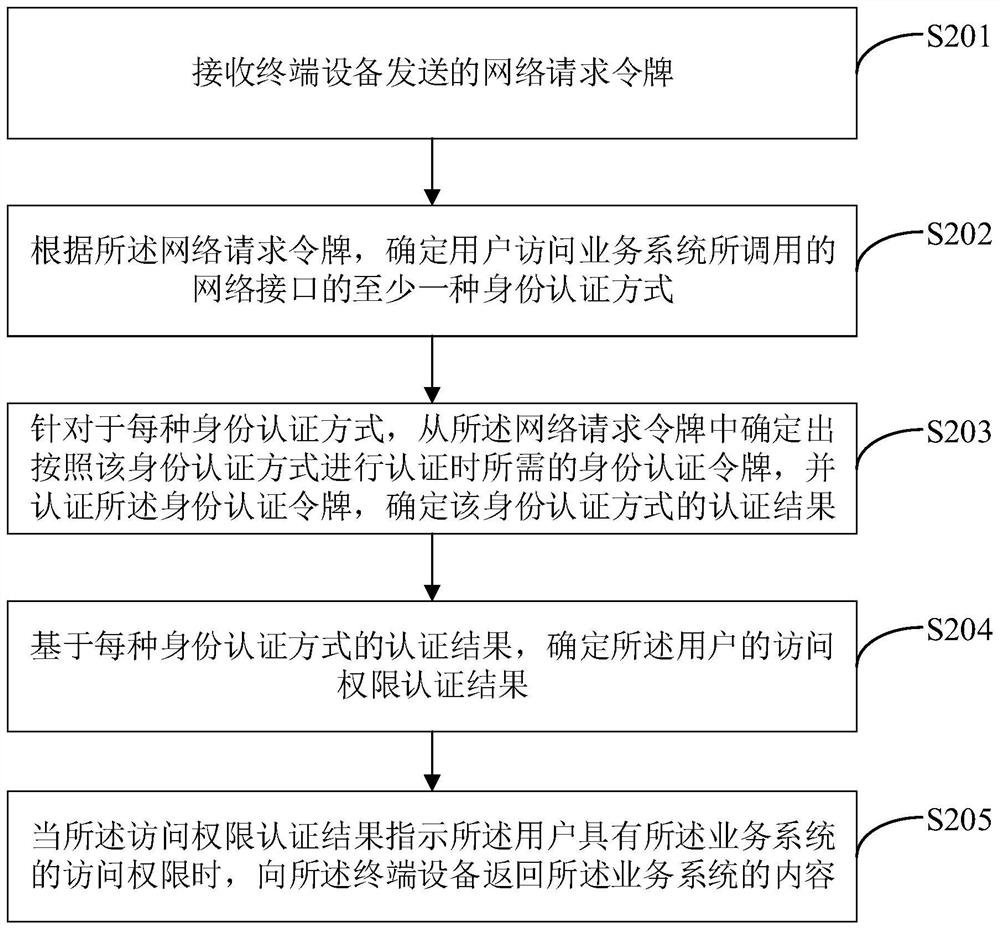
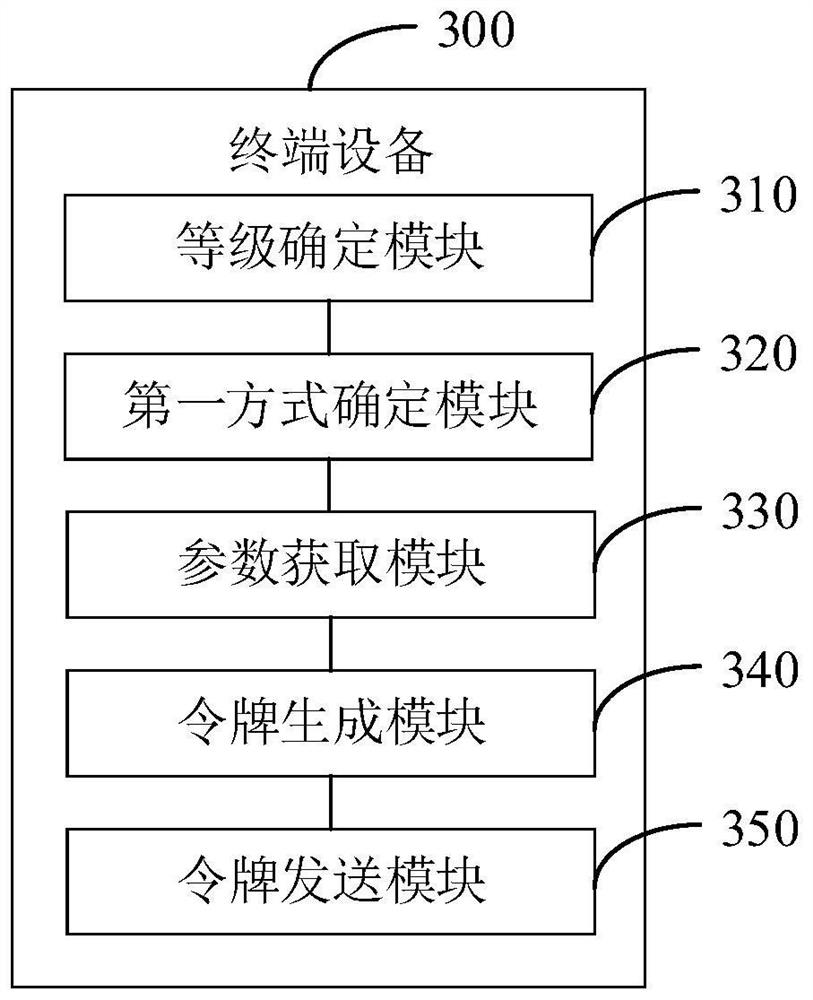
[0087] Below in conjunction with the accompanying drawings in Example embodiments of the present application, technical solutions in the embodiments of the present application will be clearly and completely described.
[0088] Below in conjunction with embodiments illustrated in the drawings of the present application, the technical solutions in the embodiments of the present application will be clearly and completely described, obviously, the described embodiments are merely part of embodiments of the present application, rather than all embodiments. Components of the present application embodiments described and illustrated in the drawings herein can be arranged and designed in a variety of different configurations. Thus, the following detailed description of the embodiments of the present application provided in the drawings is not intended to limit the scope of the present application claimed, but only the selected embodiments of the present application. Based on the embodimen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com