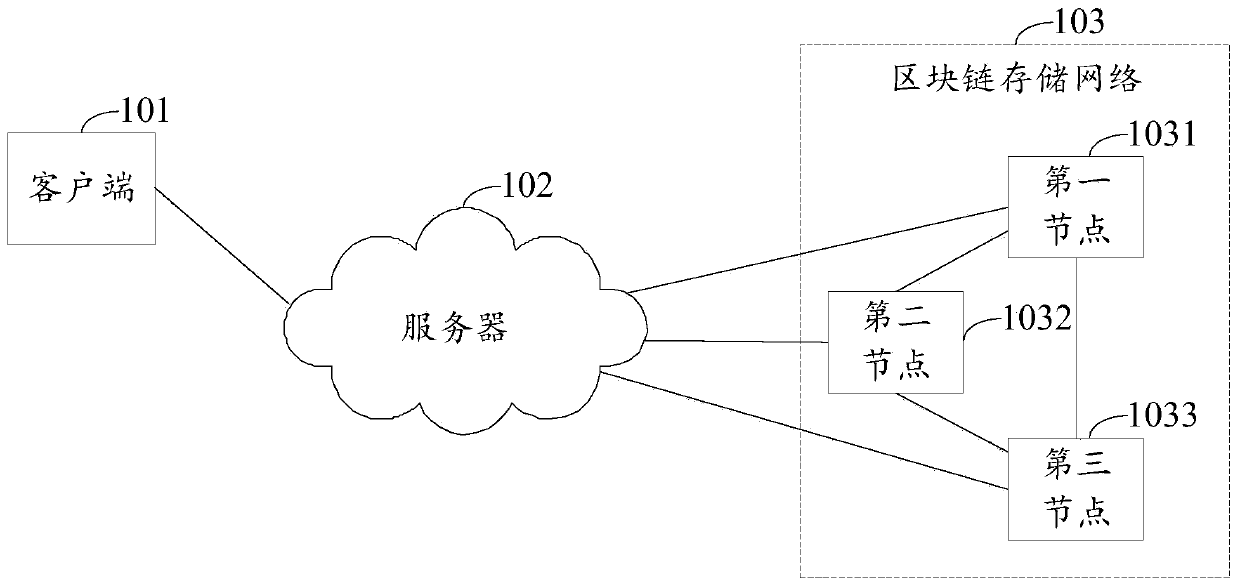
Real object information storage method and device and real object information searching method and device
A technology for information storage and physical objects, applied in the Internet field, can solve problems such as damage to consumers' rights and interests, and achieve the effect of achieving integrity, safeguarding rights and interests, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
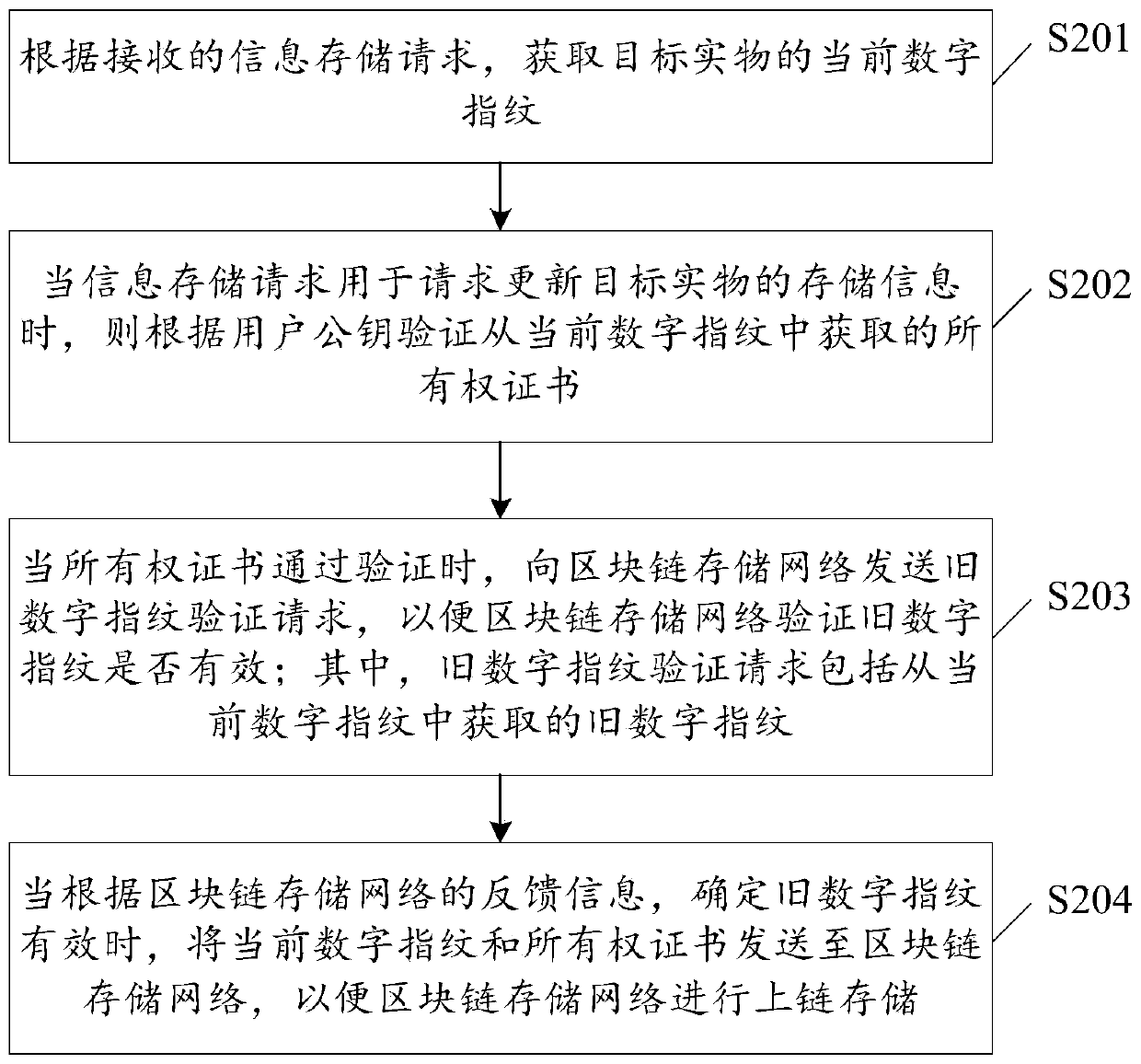
[0078] see figure 2 , which is a flow chart of the physical object information storage method provided by the first method embodiment of the present application.
[0079] The physical information storage method provided in the embodiment of the present application includes:
[0080] S201: Obtain the current digital fingerprint of the target object according to the received information storage request.
[0081] The specific implementation of this step will be described in detail below.
[0082] S202: When the information storage request is used to request to update the stored information of the target object, verify the ownership certificate obtained from the current digital fingerprint according to the user public key.
[0083] The specific implementation of this step will be described in detail below.
[0084] S203: When the ownership certificate passes the verification, send the old digital fingerprint verification request to the blockchain storage network, so that the b...
Embodiment approach
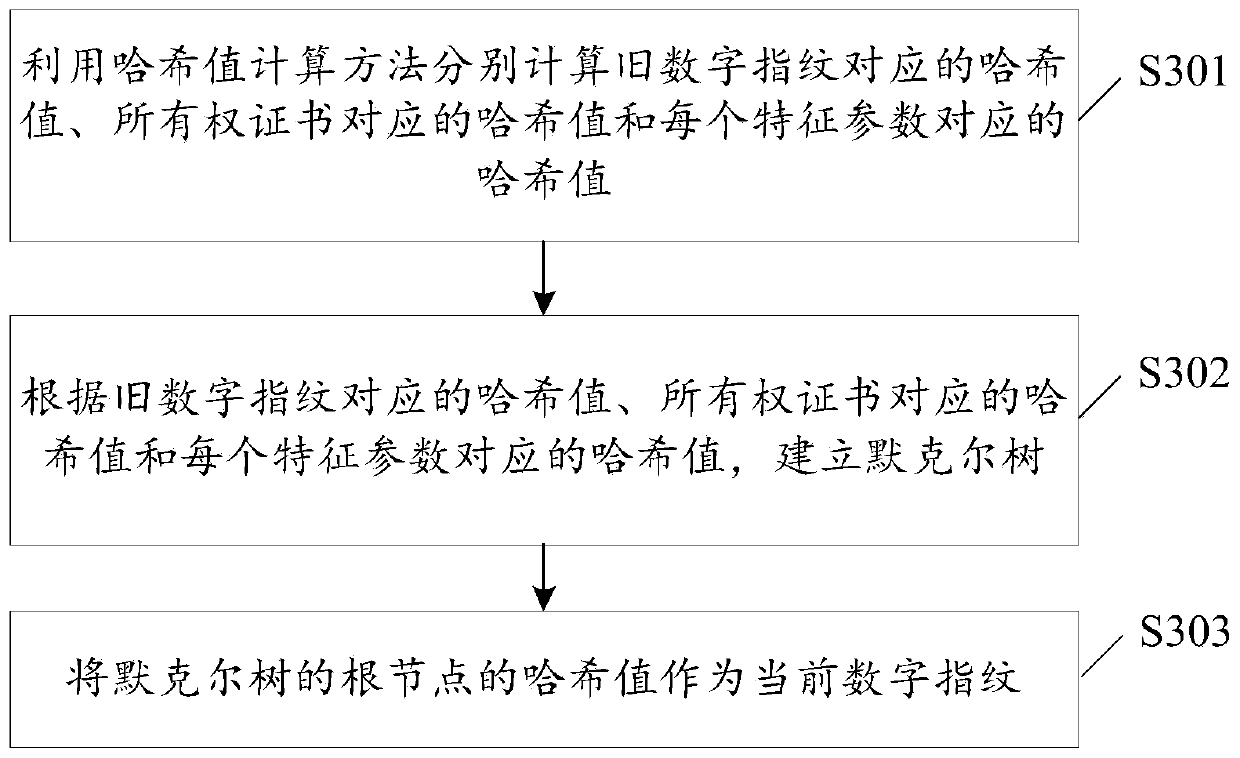
[0102] As an implementation manner, S302 may specifically be:
[0103] S302A1: Use the hash value corresponding to the old digital fingerprint, the hash value corresponding to the ownership certificate, and the hash value corresponding to each characteristic parameter as the hash value of a leaf node of the Merkle tree.
[0104] As an implementation, such as Figure 4 As shown, when the hash value corresponding to the old digital fingerprint is the old fingerprint hash value H 1 , the hash value corresponding to the ownership certificate is the ownership hash value H 2 , The hash value corresponding to the feature parameter is the first feature hash value H 3 To the Nth feature hash value H N+2 When, S302A1 can specifically be: the old fingerprint hash value H 1 , ownership hash value H 2 , the first feature hash value H 3 To the Nth feature hash value H N+2 They are respectively used as the hash values of the 1st leaf node to the N+2th leaf node of the Merkle tree. ...
specific Embodiment approach
[0133] As a specific implementation manner, S202 may specifically be:
[0134] S2021: When the information storage request is used to request to update the stored information of the target object, obtain the ownership certificate according to the current digital fingerprint.
[0135] S2022: Obtain target characteristic parameters according to the ownership certificate and the user public key.
[0136] S2023: Determine whether the target feature parameter matches the feature parameter obtained from the current digital fingerprint, if yes, execute S2024; if not, execute S2025.
[0137] S2024: Determine that the ownership certificate passes the verification of the user public key.
[0138] S2025: Determine that the ownership certificate has not passed the verification of the user public key.
[0139] The above is the specific implementation of S202 provided by the embodiment of this application. In this implementation, first obtain the target characteristic parameters according...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com