Patents
Literature
50results about How to "Prevent being cheated" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
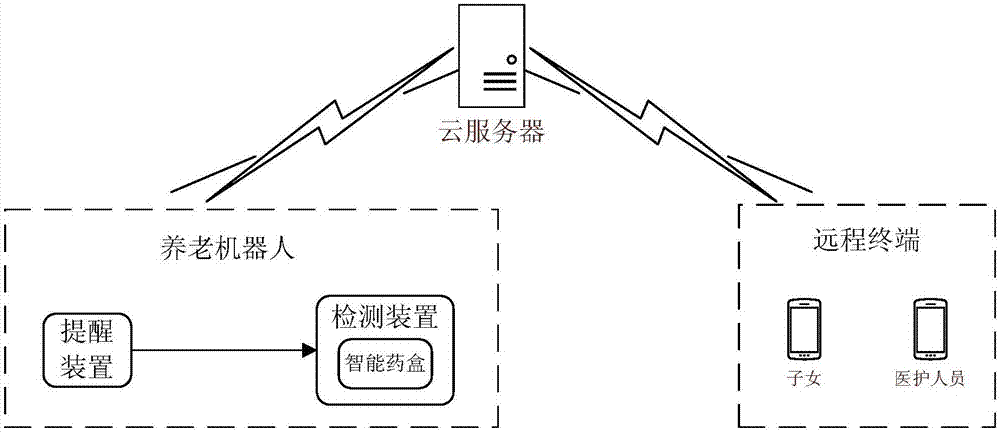
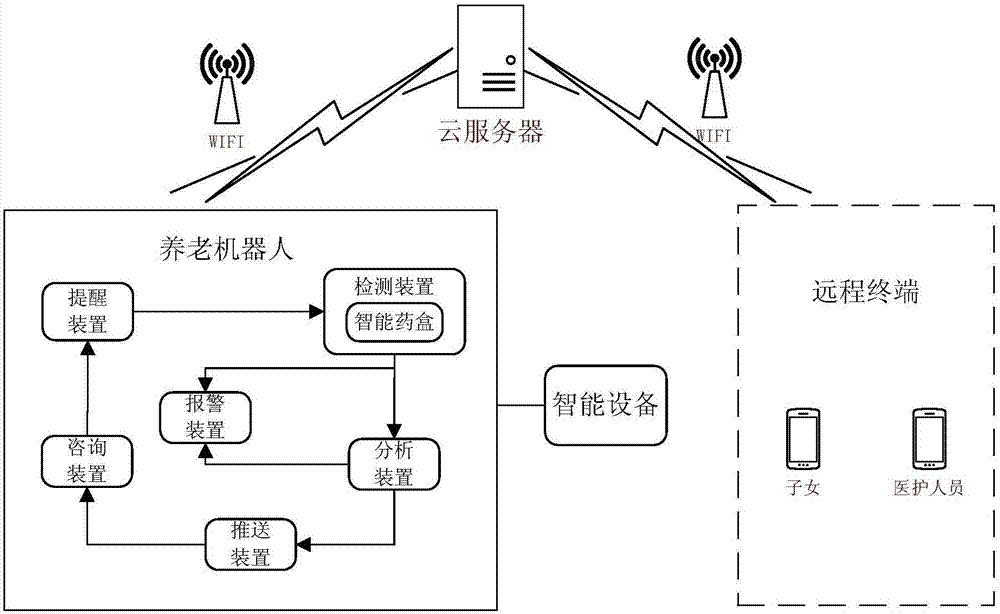
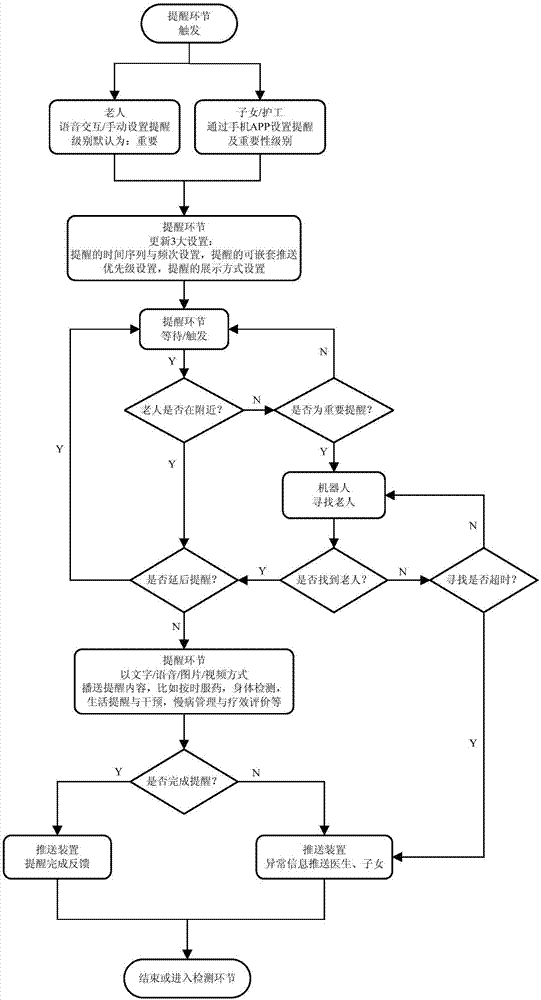
Intelligent health management system based on elder-caring robot
InactiveCN107480851AMeet the needs of daily physical examinationEasy to integrateOral administration deviceDiagnostic recording/measuringDiseaseSound sources
The invention provides an intelligent health management system based on an elder-caring robot; the system comprises an elder-caring robot, a remote terminal and a cloud server; the elder-caring robot comprises a reminder and a detector mutually connected; the reminder starts path planning and mobile functions according to a preset medical solution, searches the elder according to a face recognition technology and a sound source positioning technology, communicates with the elder through a voice interaction technology, and broadcasts prompt contents; the detector monitors an intelligent medicine box opening state on the elder-caring robot, detects the elder complete conditions on the prompt contents through the image identification technology and the voice interaction technology, and synchronizes the detection result onto the cloud server; the cloud server sends the information to the remote terminal, thus returning feedbacks to children or medical personnel. The intelligent health management system can provide complete, professional, intelligent and safe one-stop intelligent health management services, so children can remotely monitor, track and detect elder living conditions in a long term, thus realizing disease types and risk predictions.
Owner:北京小豆儿机器人科技有限公司
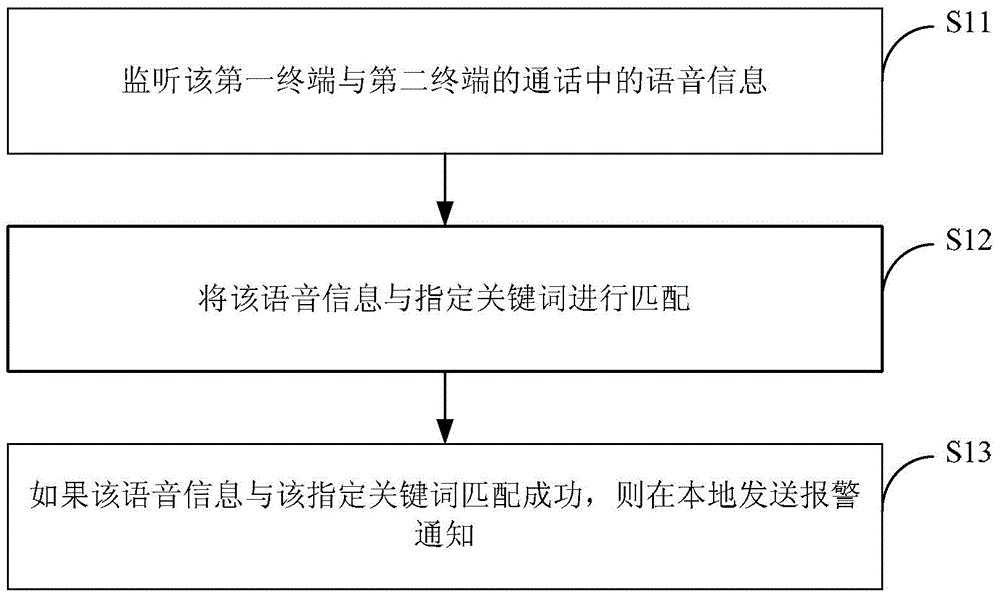
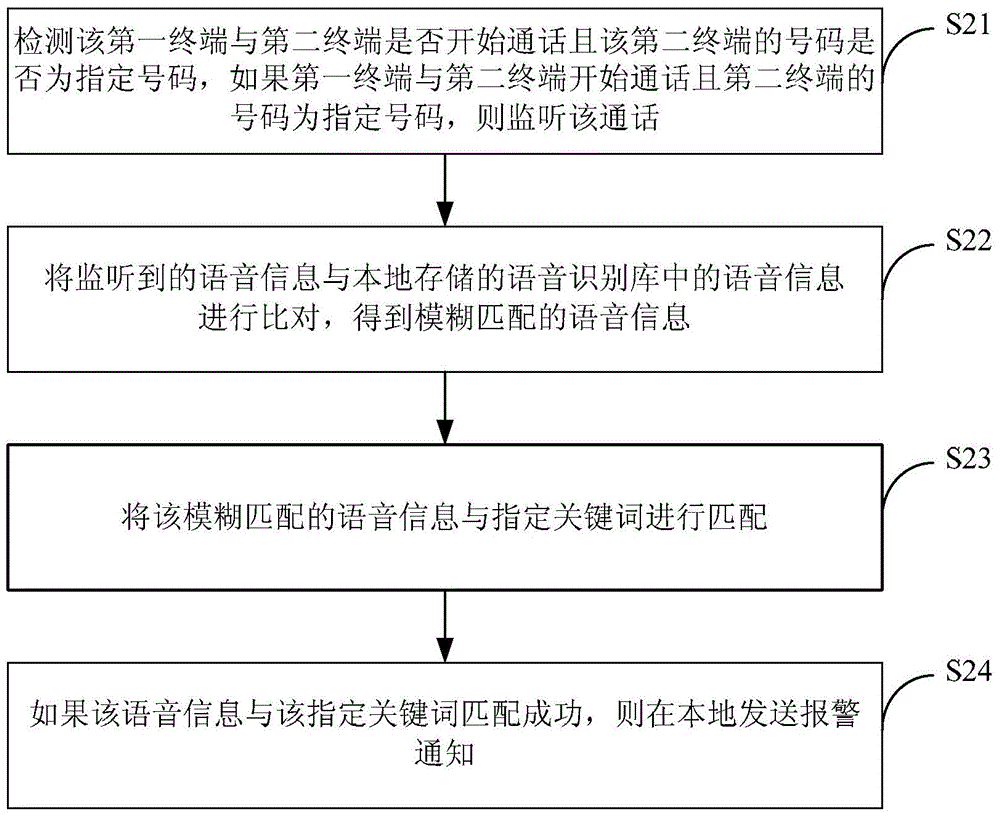
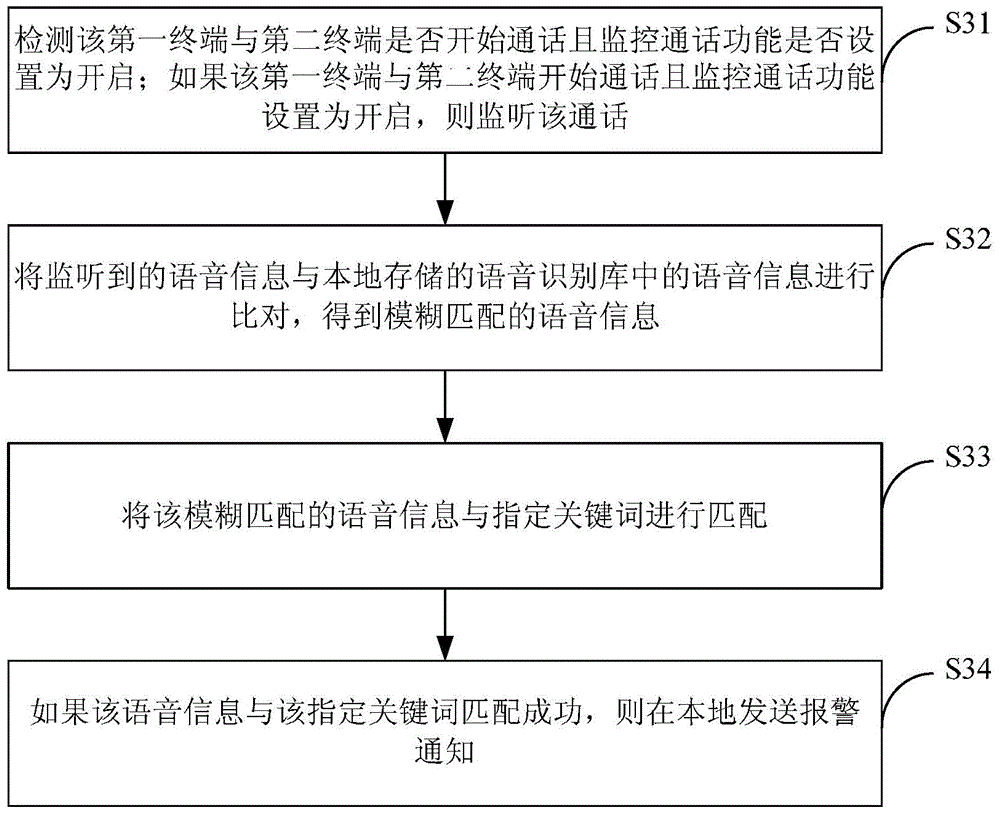
Method and device for monitoring calls
InactiveCN104065836ABe vigilantStay away from phone scamsSupervisory/monitoring/testing arrangementsSpeech recognitionMonitoring callComputer terminal
The invention provides a method and a device for monitoring calls and belongs to the communication fields. The method is applied to a first terminal and comprises the steps of monitoring voice information in a call between the first terminal and a second terminal, matching the voice information with a specified keyword, and locally sending out an alarm notice if the voice information is successfully matched with the specified keyword. The device comprises a monitoring module, a matching module and a notification module. The method and the device are capable of helping a user with raising own vigilance and reducing the risk of dupery, and thus effectively helping the user to keep away from voice phishing and preventing dupery.
Owner:XIAOMI INC
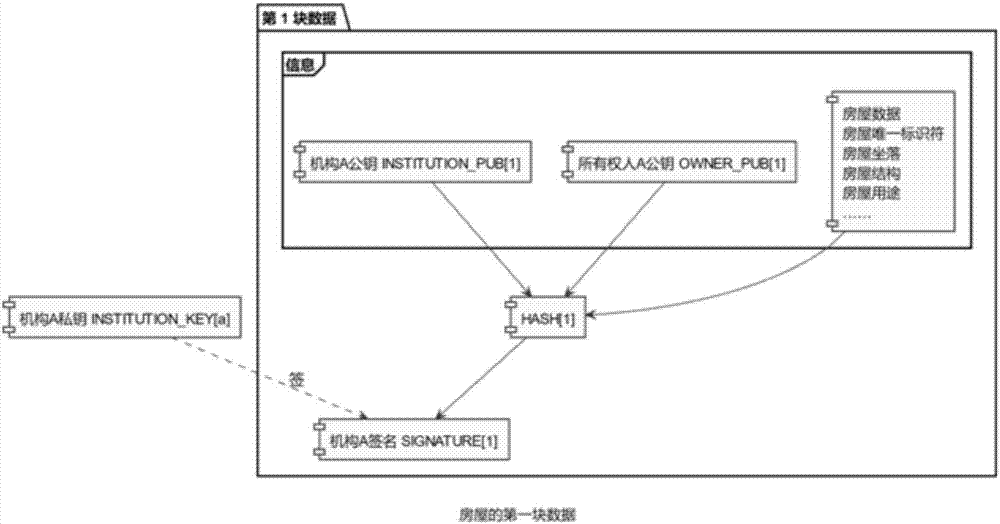
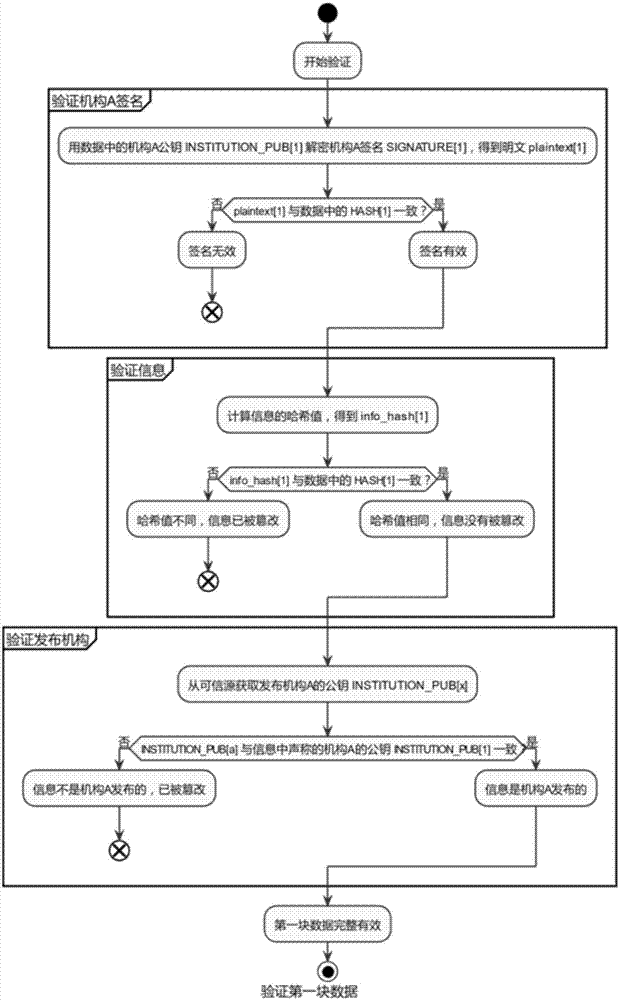
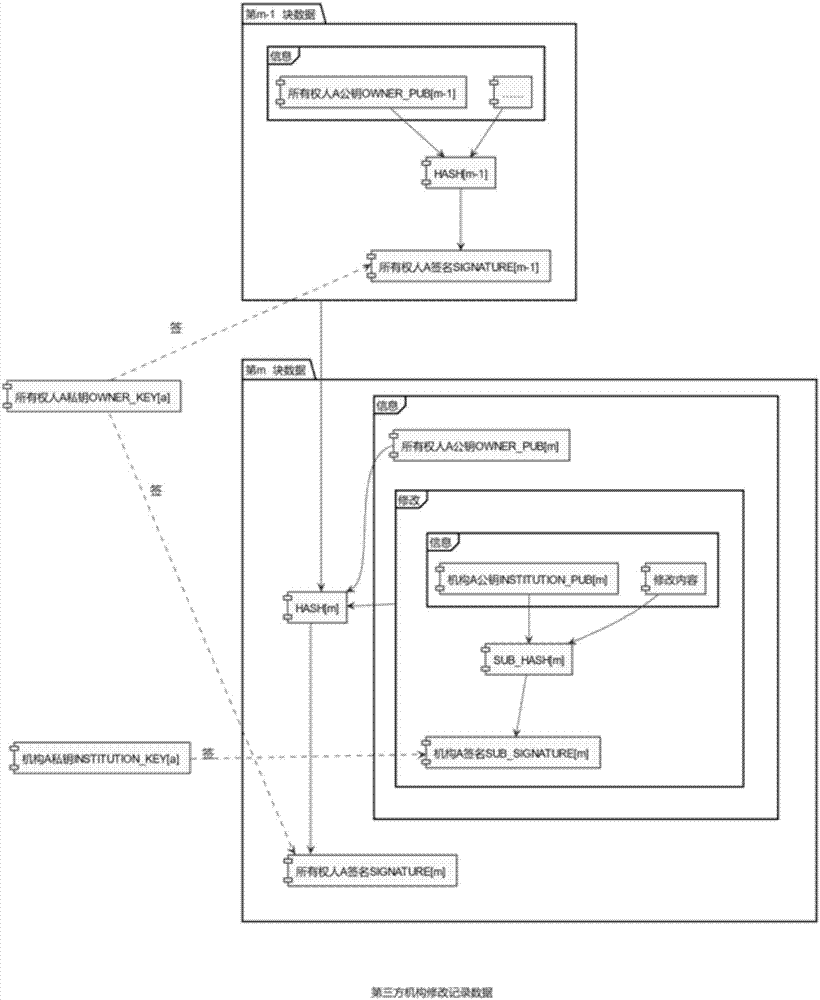
Block chain-based house history generation method
ActiveCN107506661ANon-tamperableOpenData processing applicationsDatabase distribution/replicationTamper resistanceComputer hardware
The invention relates to the field of real estates, and discloses a block chain-based house history generation method. The method comprises the following steps of: firstly filling information, carrying out operation by a block chain, generating first block data of a house, verifying validity of the first block data, and storing the first block data in the whole block chain; when the house state changes, for example, data updating or owner alternation is carried out, obtaining data of the last block from the whole block chain, filling modification content or alternation content, carrying out operation by the block chain, generating the current block data, verifying effectiveness of a signature of the current block data and integrity of the modification content or the alternation content, and storing the current block data in the whole block chain. According to the method, uniform house history is formed, and the disclosed information cannot be tampered, so that the correctness and tamper-resistance of the house information are ensured.
Owner:HENAN ZHENER INTERNET TECH
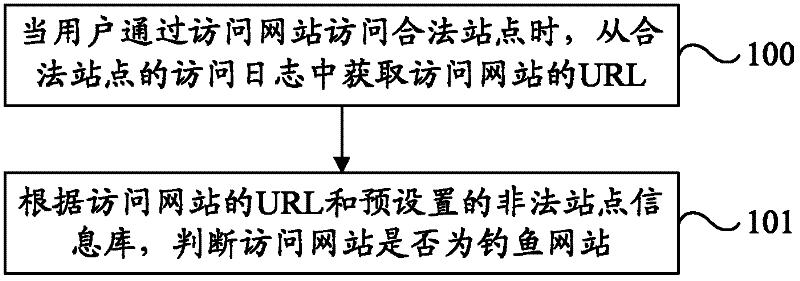
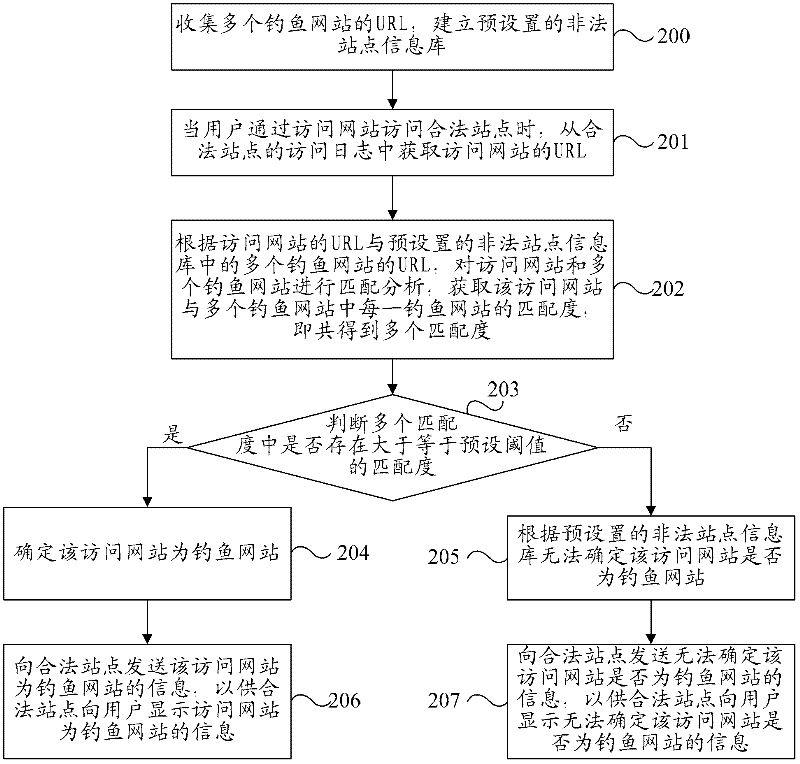
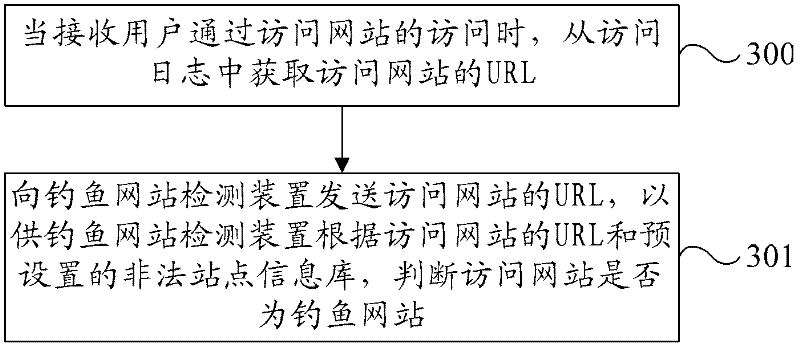
Method, device, system and website for detecting fishing website
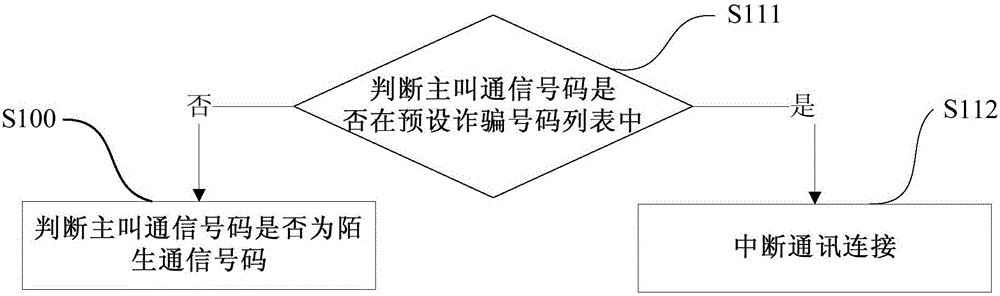
InactiveCN102546618APrevent being cheatedEffective Security GuaranteeTransmissionSpecial data processing applicationsInformation repositoryLogbook
The invention provides a method, a device, a system and a website for detecting a fishing website. The method includes that when users access legal websites through an access website, uniform resource locator of the access website is obtained in an access log of the legal website; whether the access website is a fishing website or not is judged according to the uniform resource locator of the access website and a preset illegal website data base; and the uniform resource locators of a plurality of fishing websites are stored in the illegal data base of a preset value. By means of the technical scheme, when the users access the legal websites through the access website and when the access website is the fishing website, the fishing website can be detected, certain prompt can be given to the users in the following operation, the users can be prevented from being cheated so as to lose sensitive information, and safety guarantee can be provided for the users effectively.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD
Management system for automobile leasing and renting information
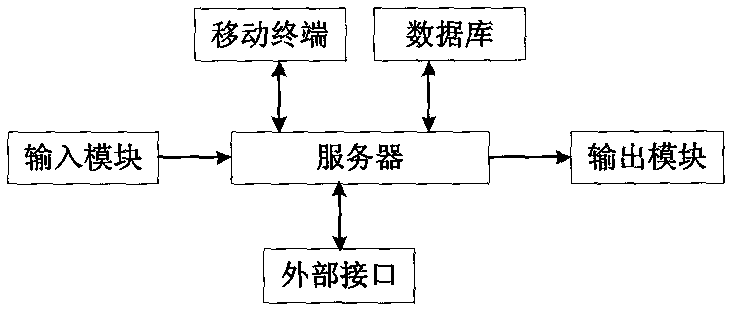
The invention relates to a management system for automobile leasing and renting information. The management system comprises a server and further comprises a mobile terminal, a database, an external interface, an input module and an output module which are connected with the server, wherein the server is used for receiving and processing various instructions; the mobile terminal is arranged on an automobile terminal and is used for sending automobile state information and instruction to the server; the database is used for storing various information in the management system for the automobile leasing and renting information; the external interface is in communication connection with other databases; and the input module is used for receiving an input information instruction of a user, and the output module is used for outputting a processing result of the server. When the management system is used, the identity information of the user is identified by the input module, and then the identity information is compared with the information in the database through the server, so that a leasing company can judge whether the automobile is rented or not. Meanwhile, the management system also has the functions of blacklist warning, one-certificate multi-renting, resource sharing, and the like.
Owner:QUANZHOU HAOJIE INFORMATION TECH DEV
Information processing method, information processing device and terminal
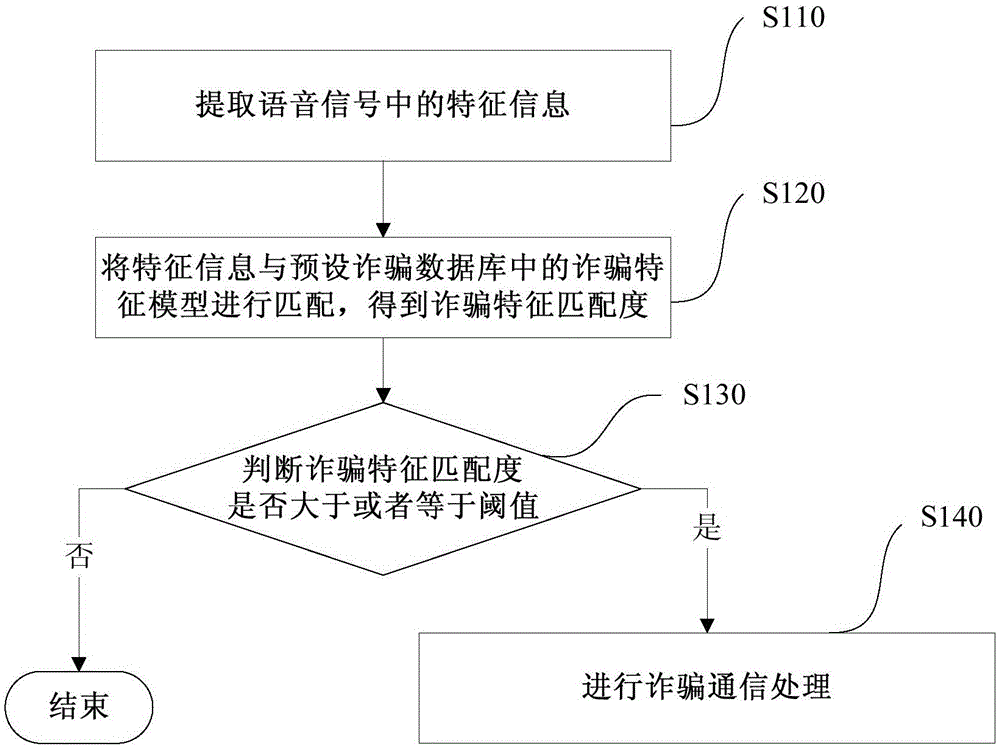
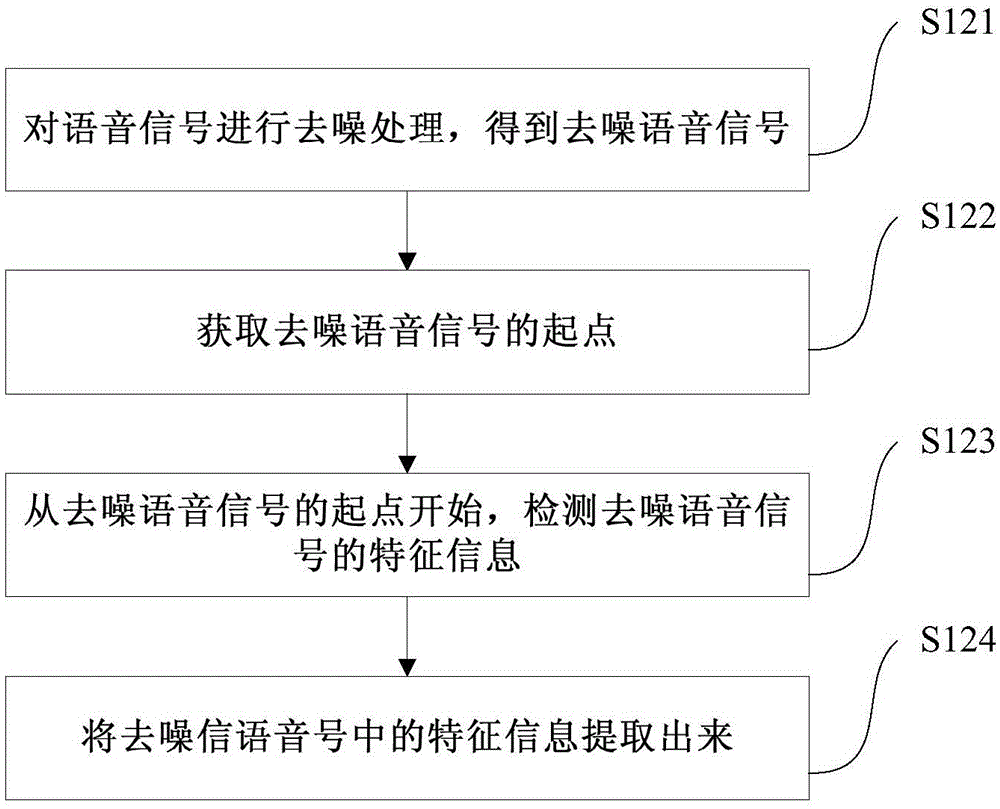
InactiveCN105100363ATimely processingAvoid being scammedUnauthorised/fraudulent call preventionInformation processingComputer terminal
The invention discloses an information processing method, an information processing device and a terminal. The information processing method comprises the steps of: extracting characteristic information in a voice signal; matching the characteristic information with a fraud characteristic model in a preset fraud database to obtain a fraud characteristic matching degree; judging if the fraud matching degree is greater than or equal to a threshold; when the fraud matching degree is greater than or equal to a threshold, carrying out a fraud communication treatment. By monitoring communication content of the terminal in real time as well as detecting and judging the communication content, the fraud communication treatment can be carried out in time to prevent a user from being tricked when the communication is regarded as fraud communication.
Owner:XIAOMI INC
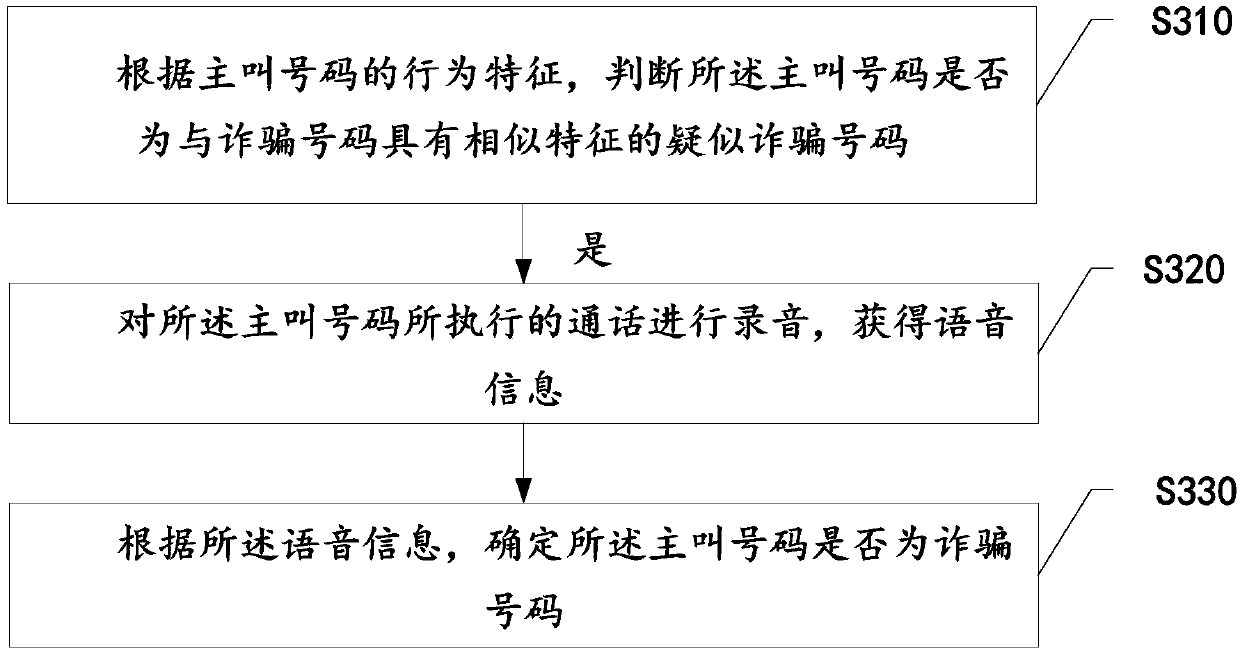
Fraudulent number identification method and device
InactiveCN107734128AImprove accuracyImprove securitySubstation equipmentSpeech recognitionIdentification deviceComputer terminal
The invention discloses a fraudulent number identification method, which is applied to a mobile terminal. The method comprises the steps of: according to the behavior characteristics of a calling number, determining whether the calling number is a suspected fraudulent number having characteristics similar to a fraudulent number; and if so, recording a call executed by the calling number to obtainvoice information, and determining whether the calling number is a fraudulent number according to the voice information. In addition, the embodiments of the invention further provide a fraudulent number identification device and a computer-readable storage medium. By adopting the method and the device, the accuracy of fraudulent number identification is further improved, users are prevented from being cheated, and users' security is improved.
Owner:NUBIA TECHNOLOGY CO LTD
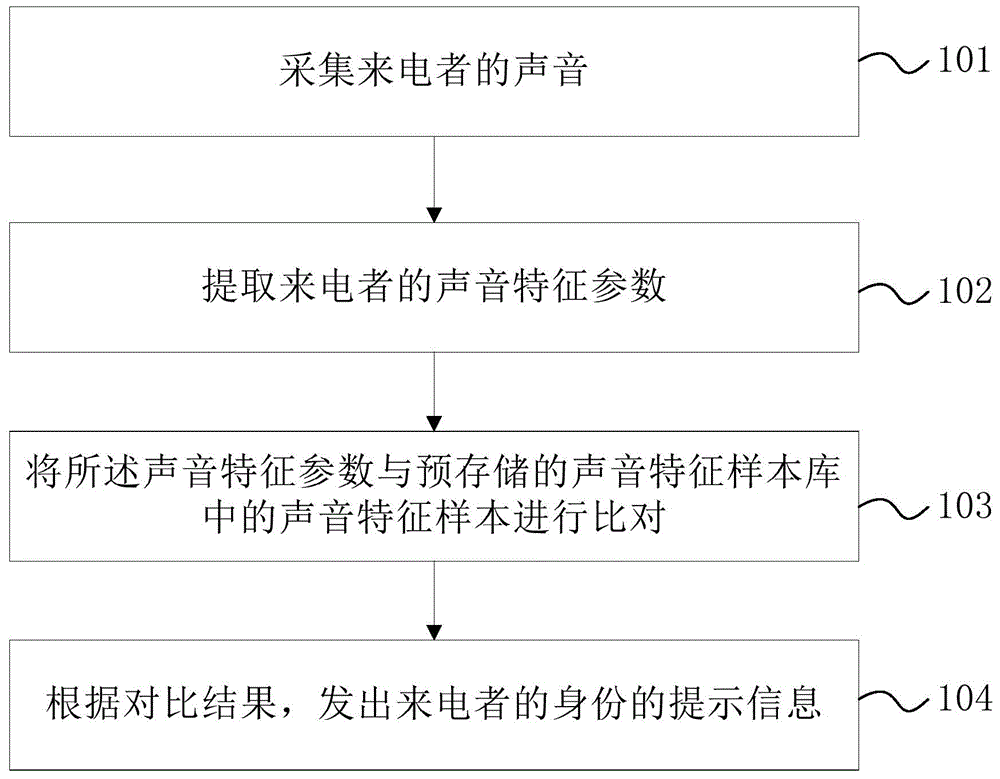
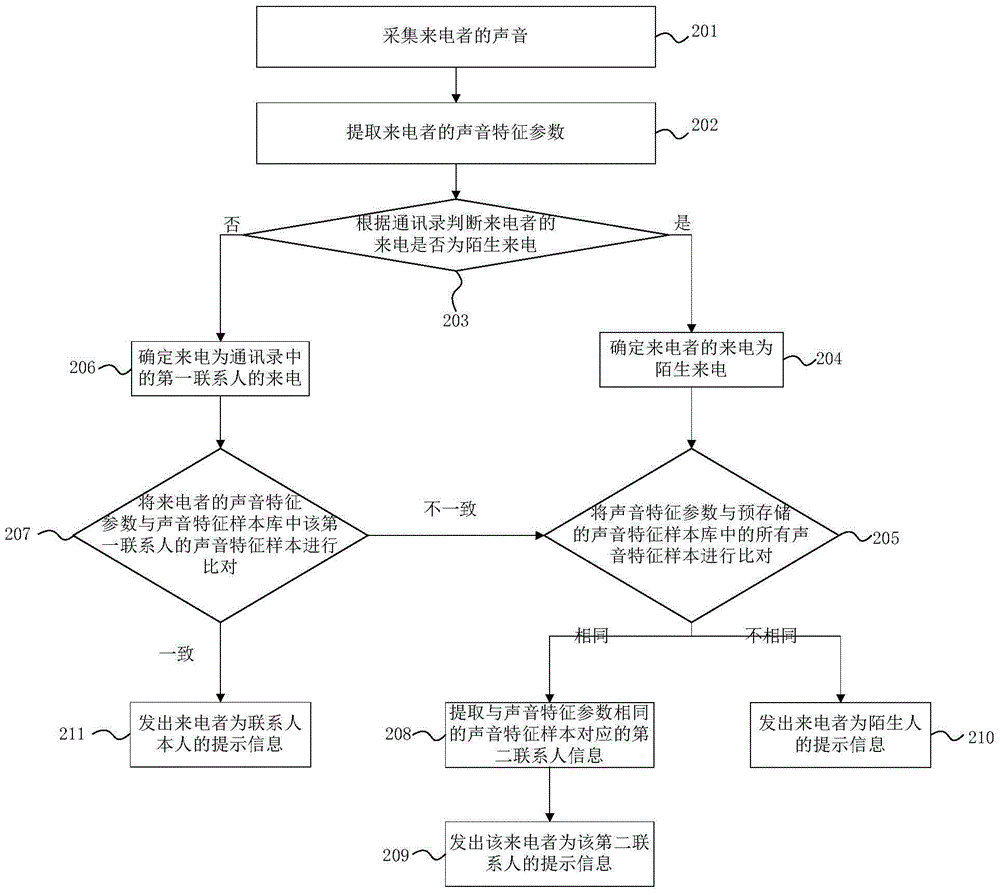
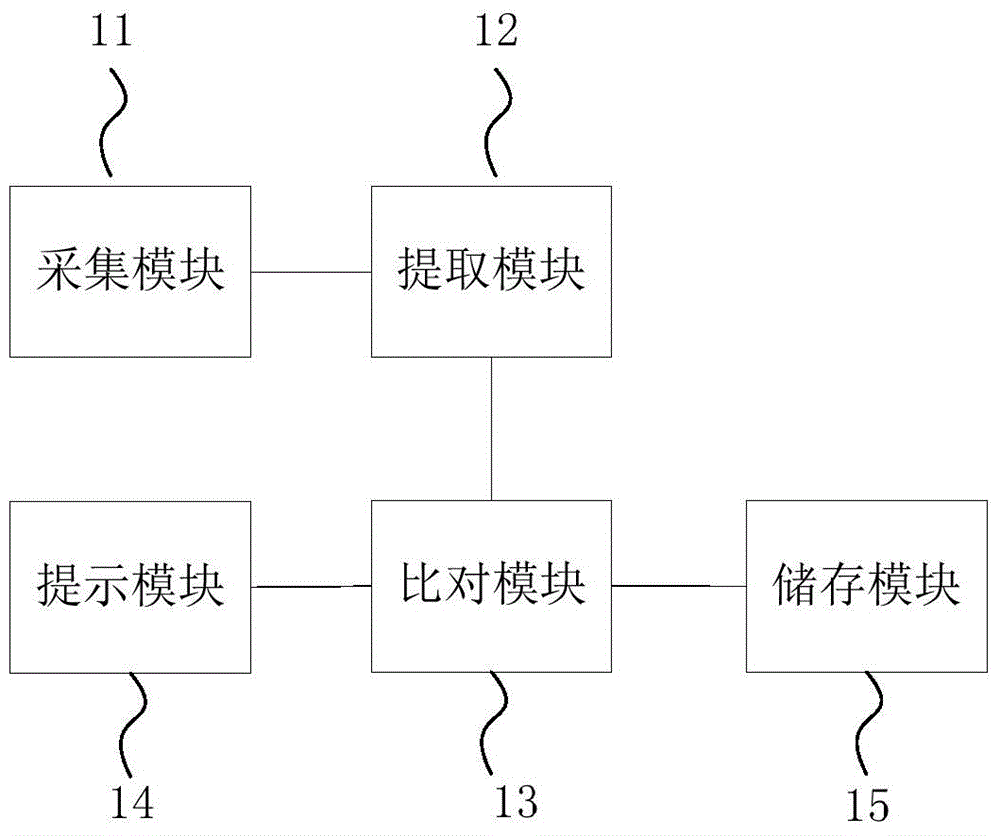
Voice recognition method, voice recognition device and mobile terminal
InactiveCN104954532APrevent being cheatedCheated lessSpeech analysisCalling susbscriber number recording/indicationSpeech identificationComputer terminal
The invention provides a voice recognition method, a voice recognition device and a mobile terminal. The method comprises the following steps: acquiring voice of a caller; extracting voice characteristic parameters of the caller; comparing the voice characteristic parameters with a voice characteristic sample prestored in a voice characteristic sample library; transmitting prompt information about the identity of the caller according to the comparison result. According to the voice recognition method, the voice recognition device and the mobile terminal provided by the invention, whether the voice characteristic sample consistent with the voice characteristic parameters of the caller exists or not is judged by acquiring the voice of the caller, extracting the voice characteristic parameters of the caller and accordingly comparing the voice characteristic parameters with the prestored voice characteristic sample library, so as to prevent a user from being cheated. By the adoption of the technical scheme of the invention, the identity of the caller can be recognized reliably and effectively, and a corresponding prompt is made, so that the possibility that the user is cheated in an incoming call conversation is reduced, and the safety of the incoming call conversation of the user is further improved.
Owner:SHENZHEN TINNO WIRELESS TECH
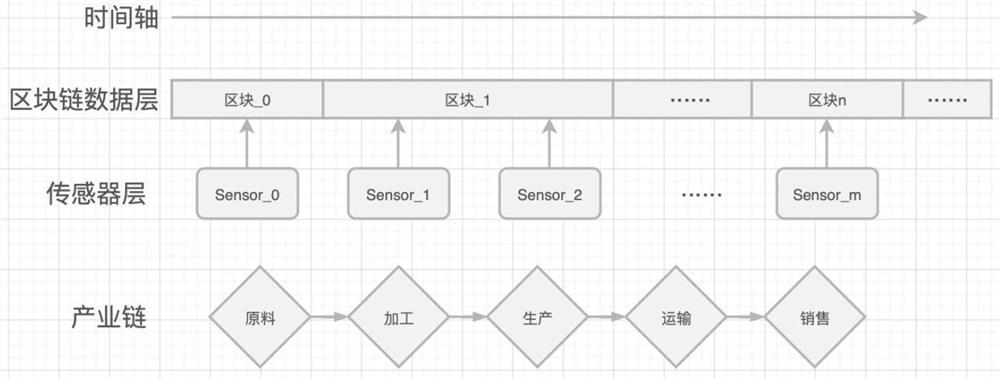
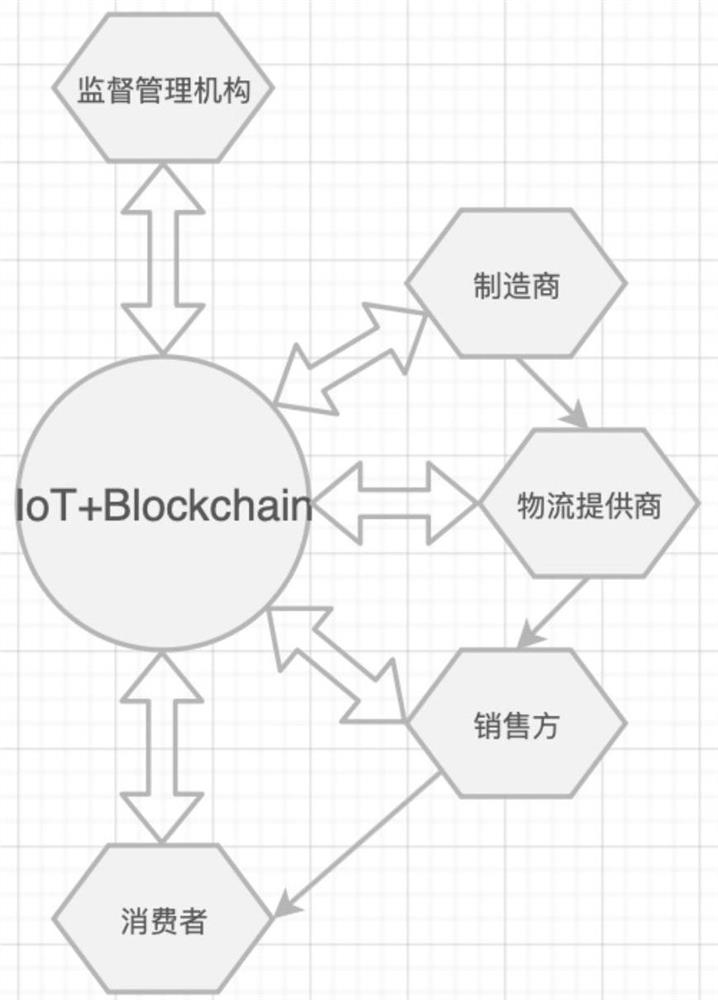
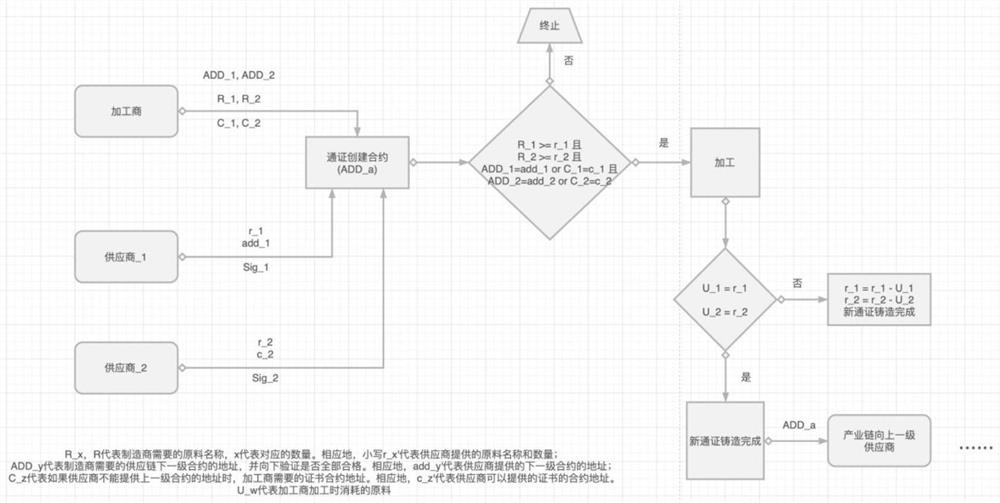
Traceability management system for wine industry supply chain based on block chain
InactiveCN112330345AGuaranteed uptimeAccurate and efficient traceabilityDatabase distribution/replicationDigital data protectionThe InternetGrape wine
The invention discloses a traceability management system for a wine industry supply chain based on a block chain, the traceability management system comprises a system framework and a system composition; the system is applied to wine process design, and the system framework comprises an Internet of Things + block chain, an interaction mechanism and participant roles. The system composition provides a decentralized supply chain management system based on an intelligent contract, which is established on the basis of a block chain technology. According to the invention, the block chain and the Internet of Things are innovatively applied to the red wine industry chain, and one batch of goods is mapped into the non-homogeneous pass, so that the traceability becomes accurate and efficient; eachmanufacturing link of the industrial chain is ingeniously projected into a transaction in a block chain, so that each link of the product must be guaranteed in quality and quantity, cannot be missing,and is traceable and tamper-proof; an external data storage excitation mechanism is designed, participants are excited to participate in network maintenance, and stable operation of the network is kept.
Owner:宁波旺链信息科技有限公司
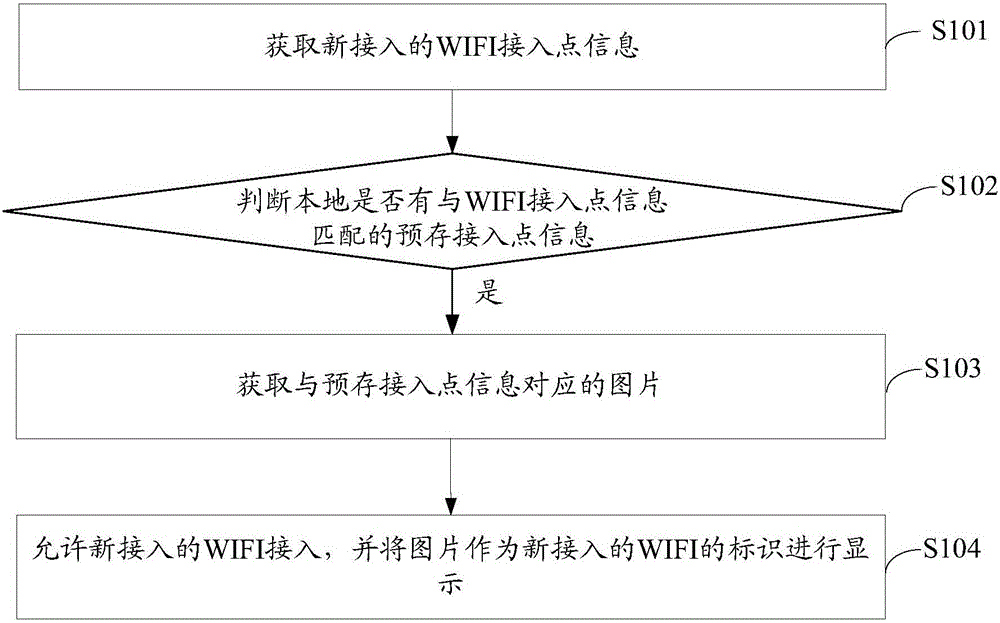
WIFI identification method and intelligent terminal
Owner:TCL COMM TECH NINGBO CO LTD
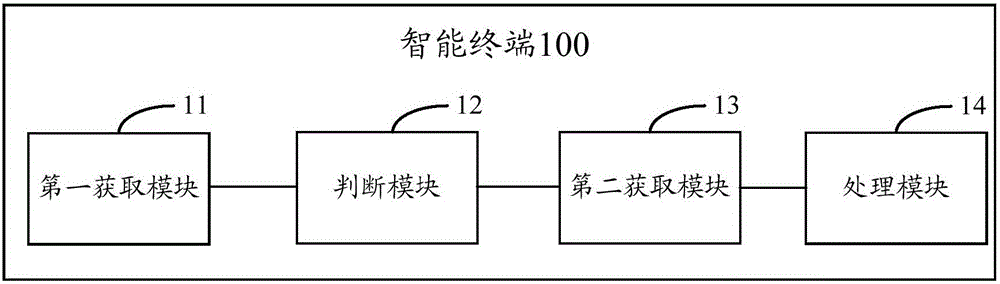
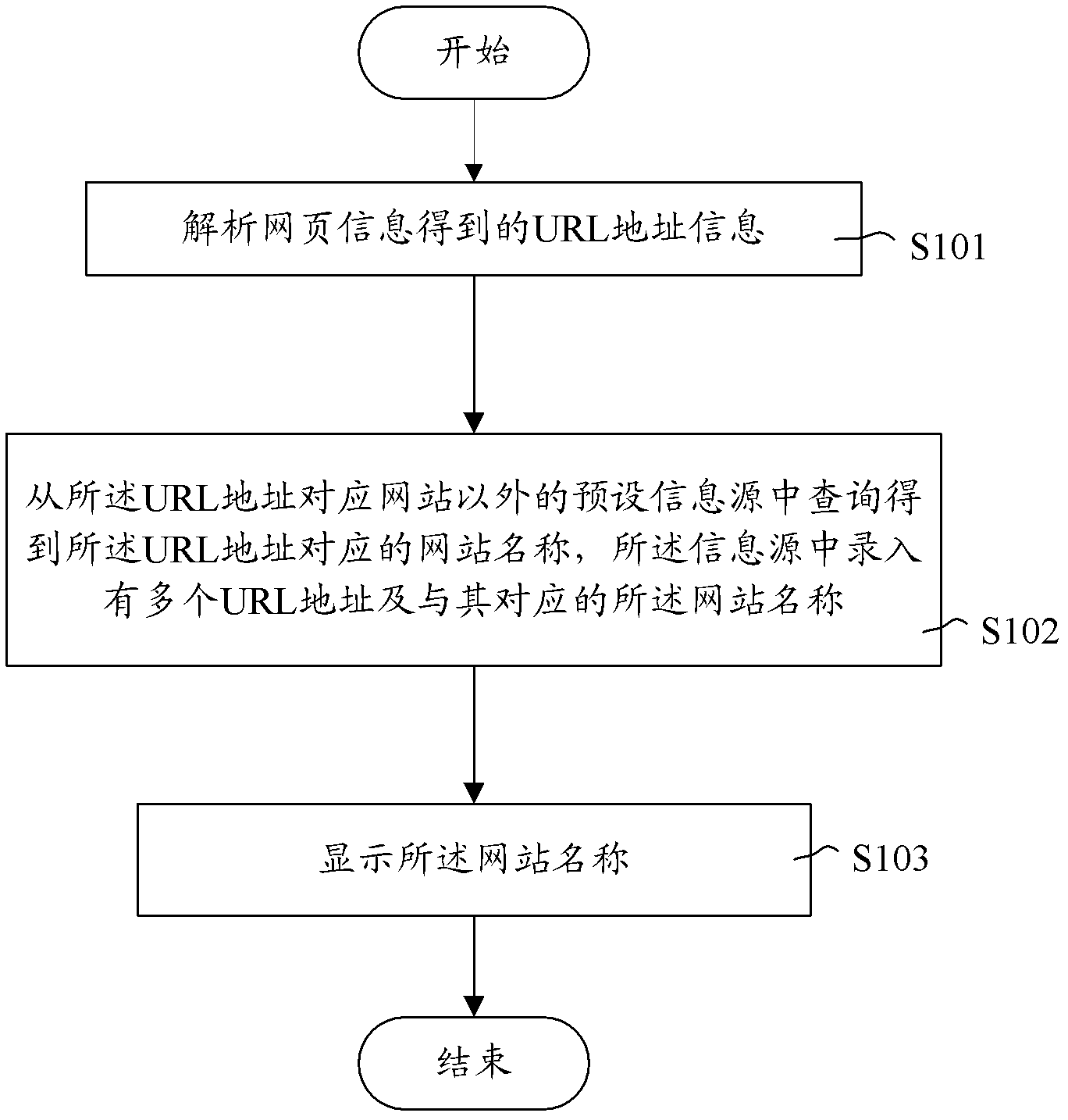
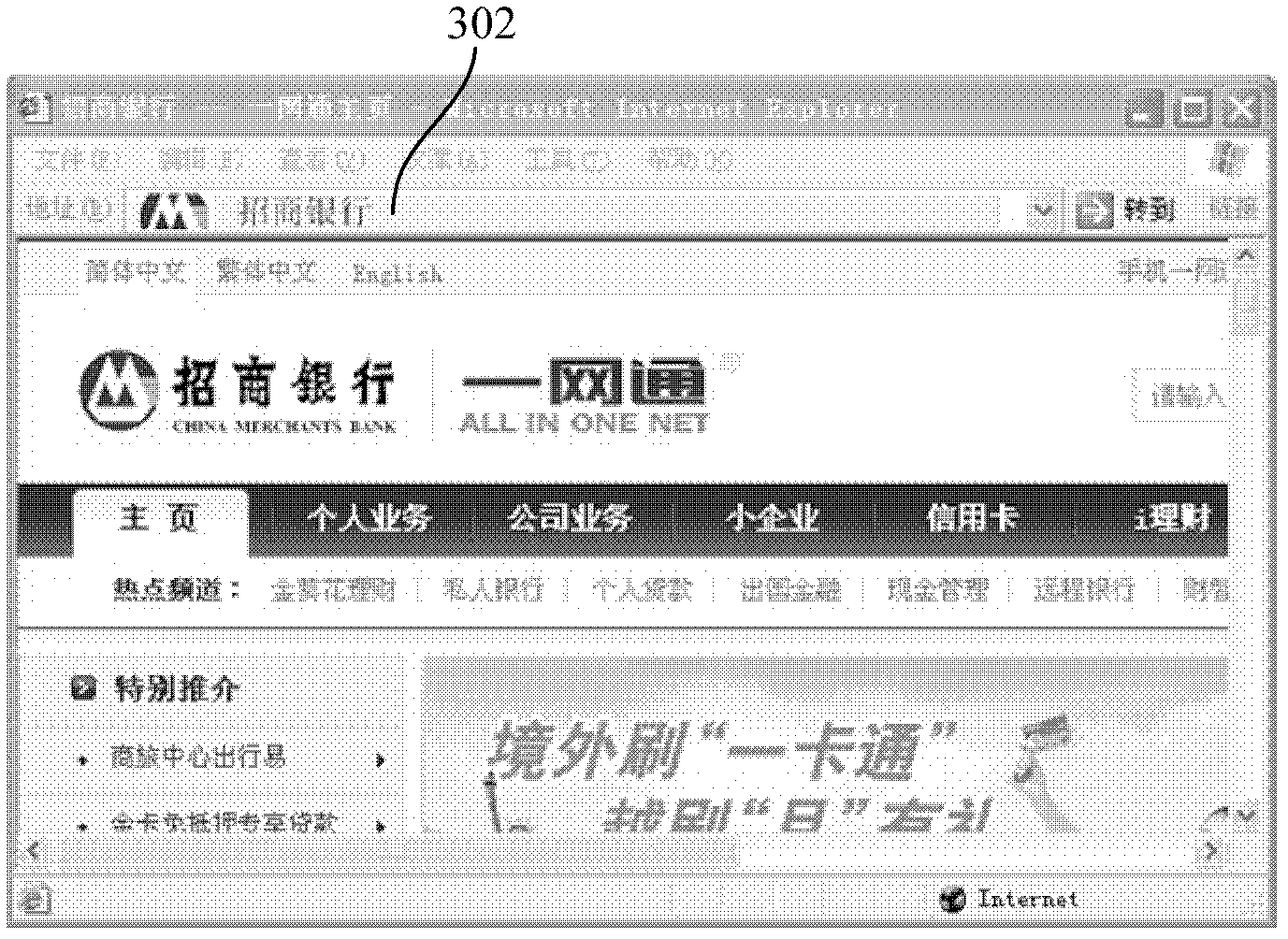
Webpage loading method of browser
InactiveCN103164411ABe vigilantImprove securitySpecial data processing applicationsPhishingUniform resource locator
A webpage loading method of a browser comprises the following steps: analyzing webpage information to obtain uniform resource locator (URL) address information; inquiring from a preset information source except for corresponding websites of URL addresses to obtain the corresponding site names of the URL addresses, wherein a plurality of URL addresses and the corresponding website names are recorded in the information source; and displaying the website names. According to the webpage loading method of the browser, due to the fact that the site names are obtained from the preset information source, at the moment, after a user enters a phishing website, due to the fact that corresponding website names cannot be found in the information source, so that the user can be quickly on the alert and prevent from being cheated.
Owner:SHENZHEN KINGDEE MIDDLEWARE
Cellphone, mobile communication system and verification method of instant messaging software account
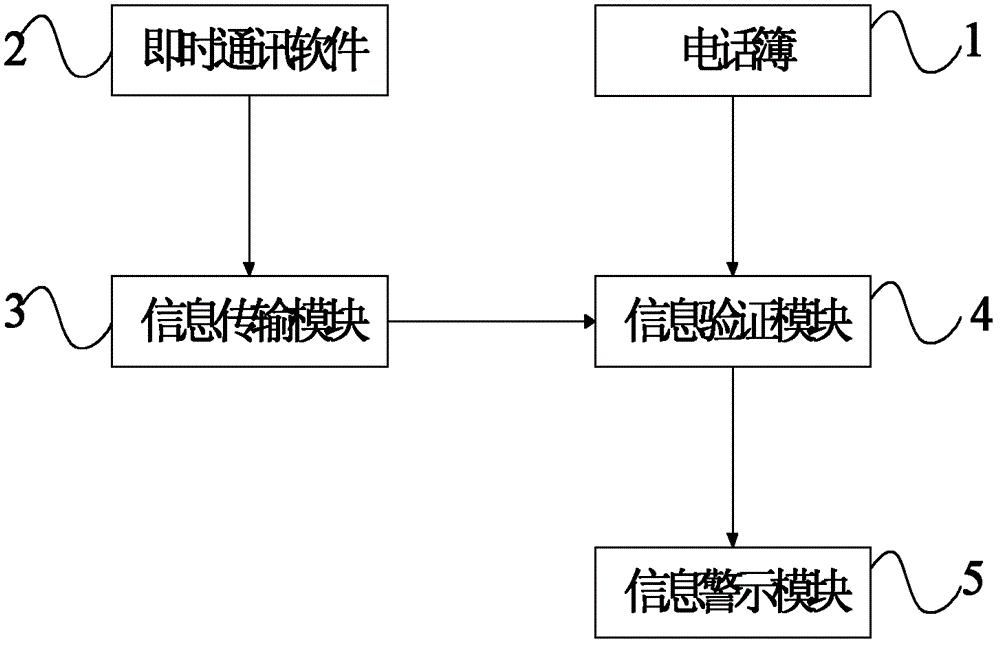
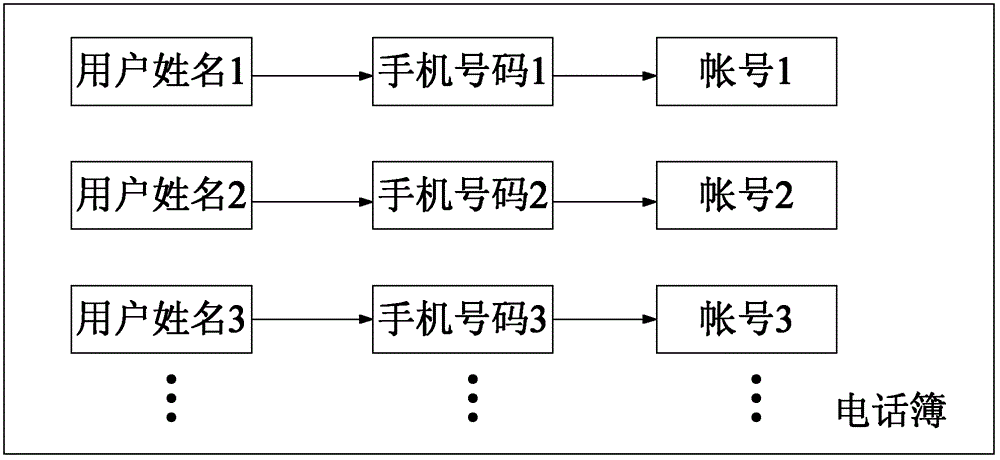
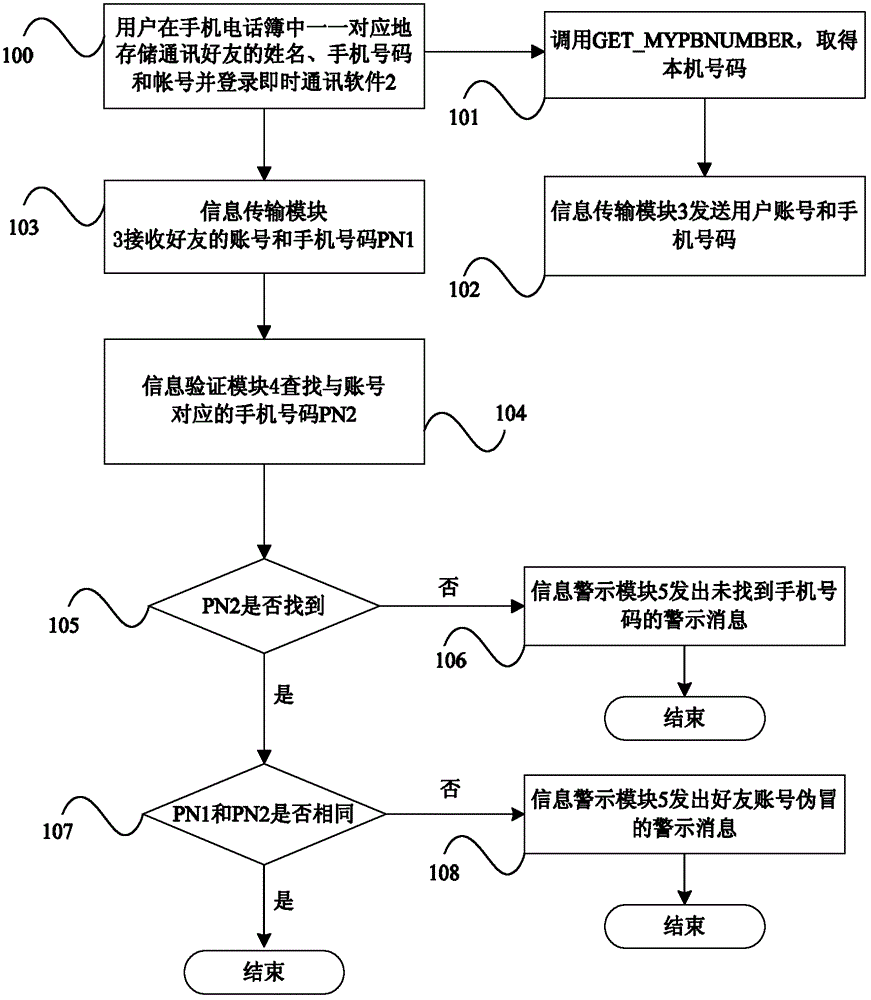
ActiveCN103067882APrevent being cheatedMessaging/mailboxes/announcementsSecurity arrangementMobile Telephone NumberInformation transmission
The invention discloses a cellphone, a mobile communication system and a verification method of an instant messaging software account. The cellphone comprises a telephone book, instant messaging software, an information transmission module, an information authentication module and an information warning module. The instant messaging software comprises a user account and the accounts of the communication friends of the user, and the telephone book is used for respectively storing the names, the cellphone numbers and the accounts of the communication friends one by one. The information transmission module is used for sending and receiving the accounts and the cellphone numbers. The information authentication module is used for verifying the consistency of the cellphone numbers of online communication friends received by the information authentication module. The information warning module is used for warning when the information authentication module fails in verifying. After the user logs in the instant messaging software, the cellphone and the account verification method of the mobile communication system can verify the authenticity of the accounts of the online communication friends and send out warning information, so that the user can pay attention to unusual friend accounts, and being deceived is prevented.
Owner:SHANGHAI YIKE COMM TECH
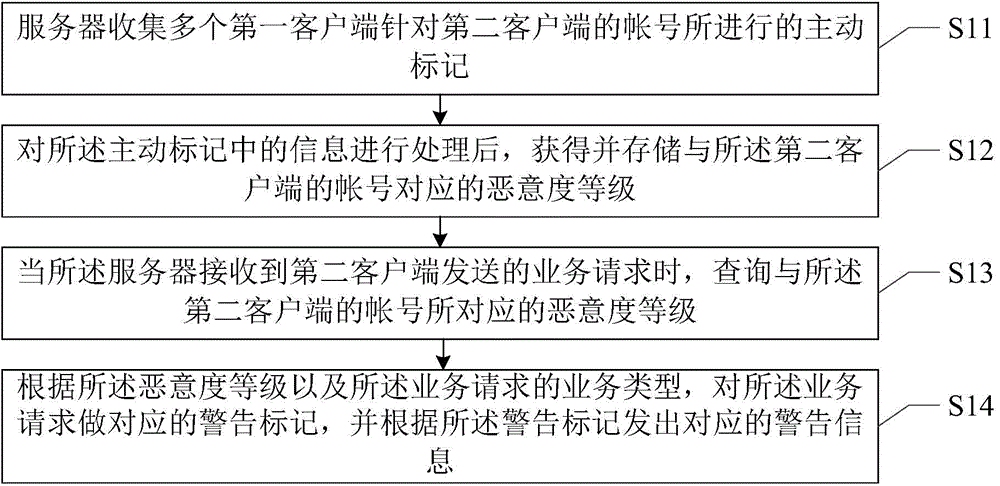
Service request processing method and service request processing device
An embodiment of the invention provides a service request processing method which comprises the steps of collecting active marks of a plurality of first clients to the account number of a second client by a server; after processing information in the active marks, acquiring and storing a malice degree which corresponds with the account number of the second client; when the server receives a service request which is transmitted from the second client, searching a malice degree which corresponds with the account number of the second client; and arranging a corresponding warning mark on the service request according to the malice degree and the service type of the service request, and transmitting corresponding alarm information according to the warning mark. Furthermore the embodiment of the invention further provides a service request processing device. The service request processing method and the service request processing device can effectively prevent theft or cheating of user information or property and furthermore improve safety of Internet information.
Owner:TENCENT TECH (SHENZHEN) CO LTD
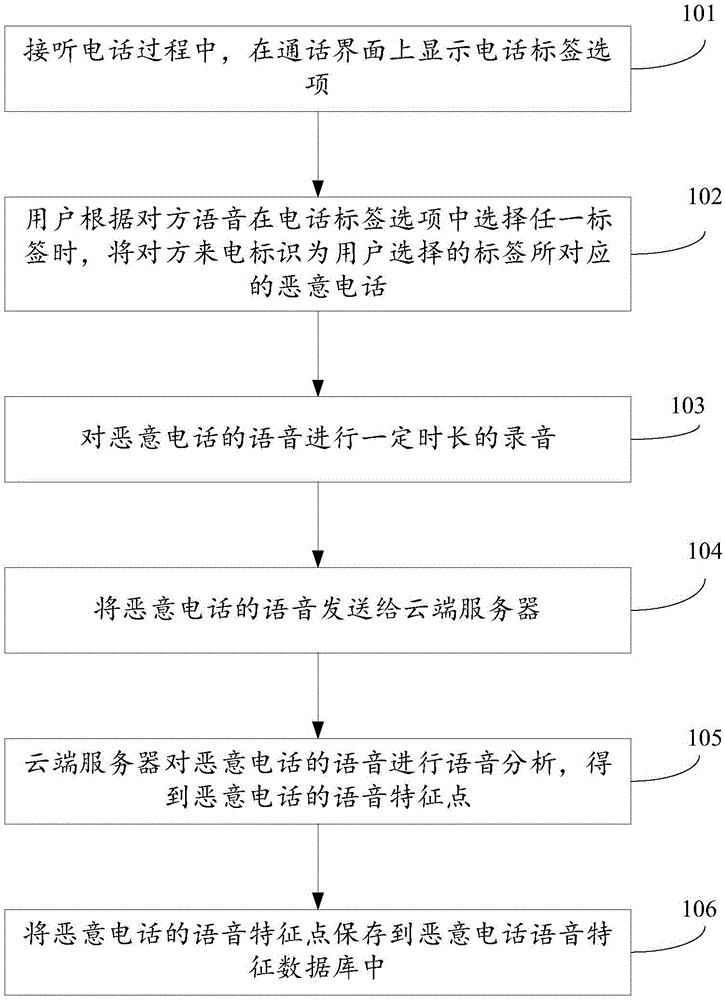
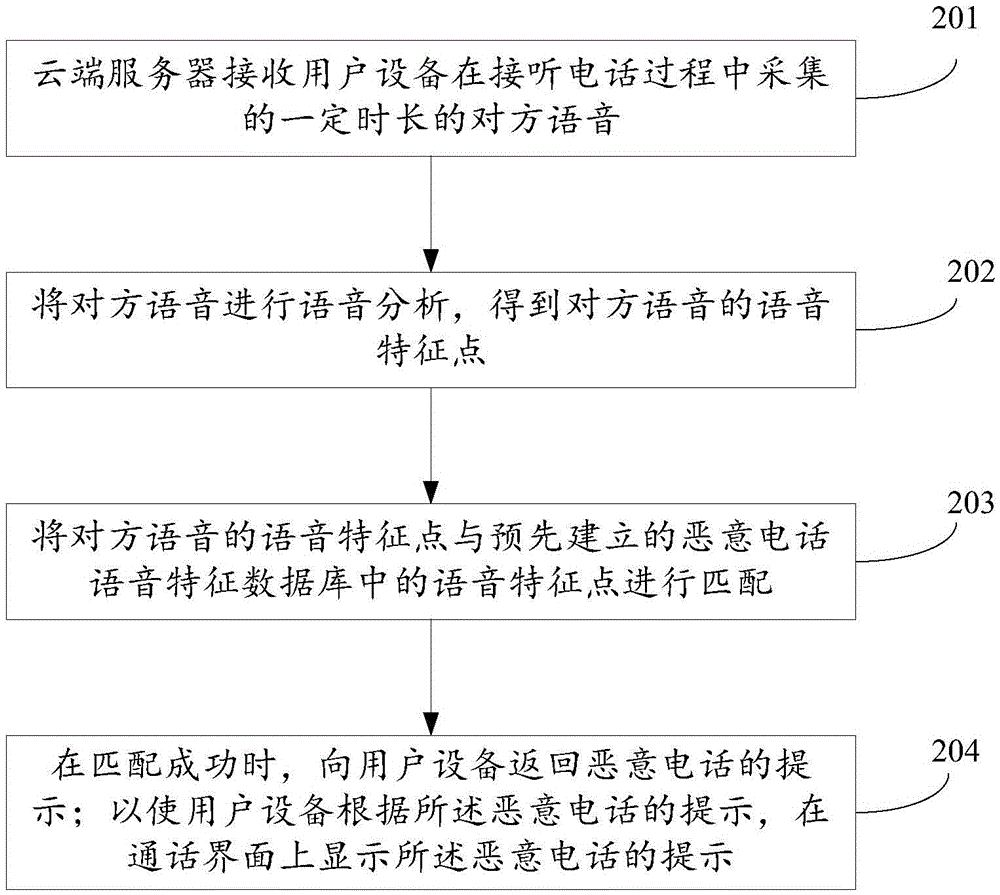
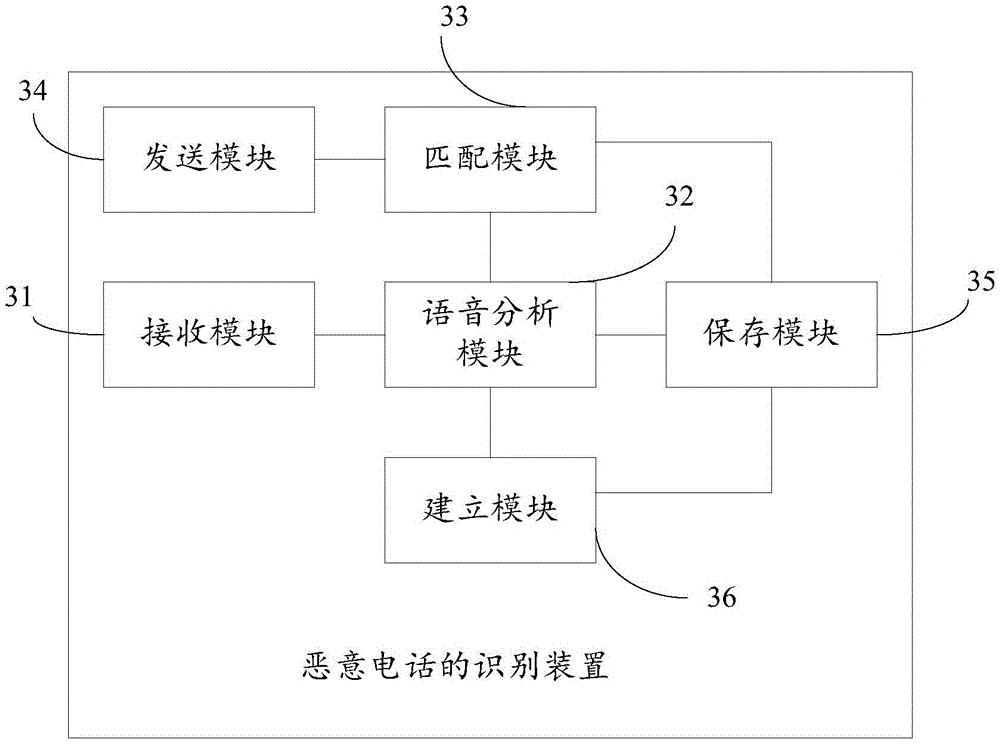
Recognition method and apparatus of malicious call
InactiveCN106790950AImprove securityPrevent being cheatedSubstation equipmentAutomatic exchangesVoice analysisSpeech sound
The invention discloses a recognition method and apparatus of a malicious call. A cloud server receives voice of a certain duration of an opposite side, acquired by user equipment in a call-answering process; a voice analysis of the voice of the opposite side is conducted, and voice characteristic points of the voice of the opposite side are obtained; the voice characteristic points of the voice of the opposite side and voice characteristic points of a pre-established malicious call voice characteristic database are matched; a prompt of the malicious call is returned to the user equipment during successful matching; and the user equipment displays the prompt of the malicious call on a calling interface according to the prompt of the malicious call. According to the method and apparatus, the security of using the telephone by users is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
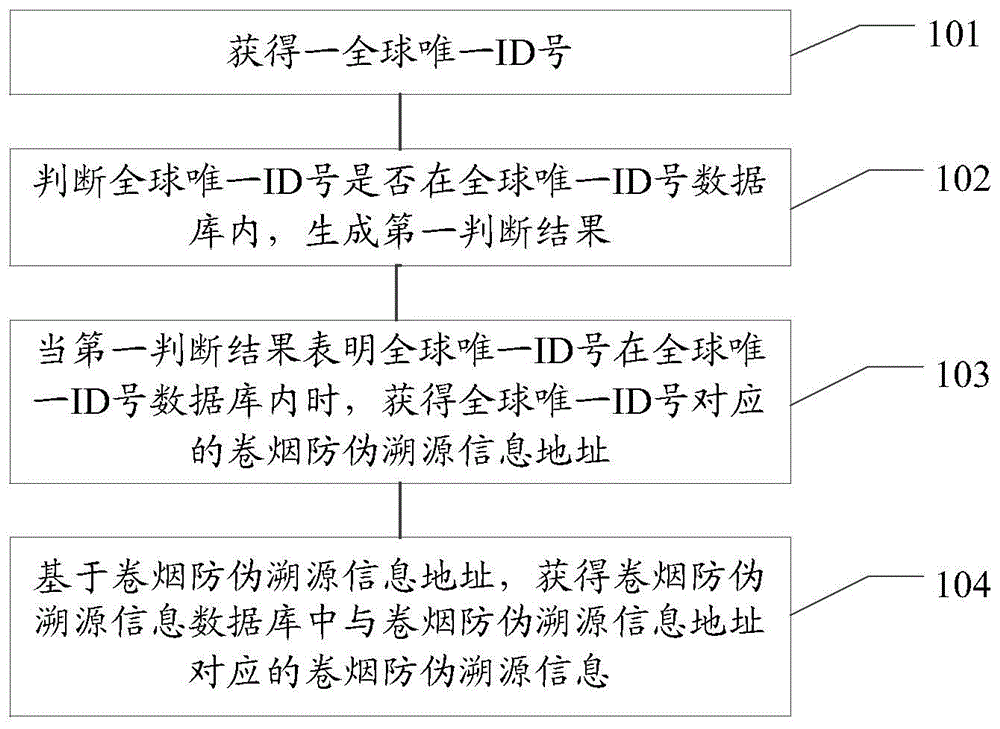
Cigarette fake preventing and source tracing method and system based on Internet of Things
InactiveCN104156762AEffective authenticity judgmentImprove authenticity identification abilityCo-operative working arrangementsRecord carriers used with machinesThe InternetSource tracing
The invention discloses a cigarette fake preventing and source tracing method and system based on the Internet of Things. The method is applied to the cigarette fake preventing and source tracing system which is provided with a globally unique ID number database and a cigarette fake preventing and source tracing information database. The method includes the steps of obtaining a globally unique ID number, judging whether the globally unique ID number exists in the globally unique ID number database or not, generating a first judgment result, obtaining a cigarette fake preventing and source tracing information address corresponding to the globally unique ID number when the first judgment result shows that the globally unique ID number exists in the globally unique ID number database, and obtaining cigarette fake preventing and source tracing information, corresponding to the cigarette fake preventing and source tracing information address, in the cigarette fake preventing and source tracing information database on the basis of the cigarette fake preventing and source tracing information address. By means of the method, the recognition capability for cigarette fake preventing and source tracing can be improved, and the safety of the cigarette fake preventing and source tracing information is enhanced.
Owner:YUNNAN SINOTECH IOT TECH
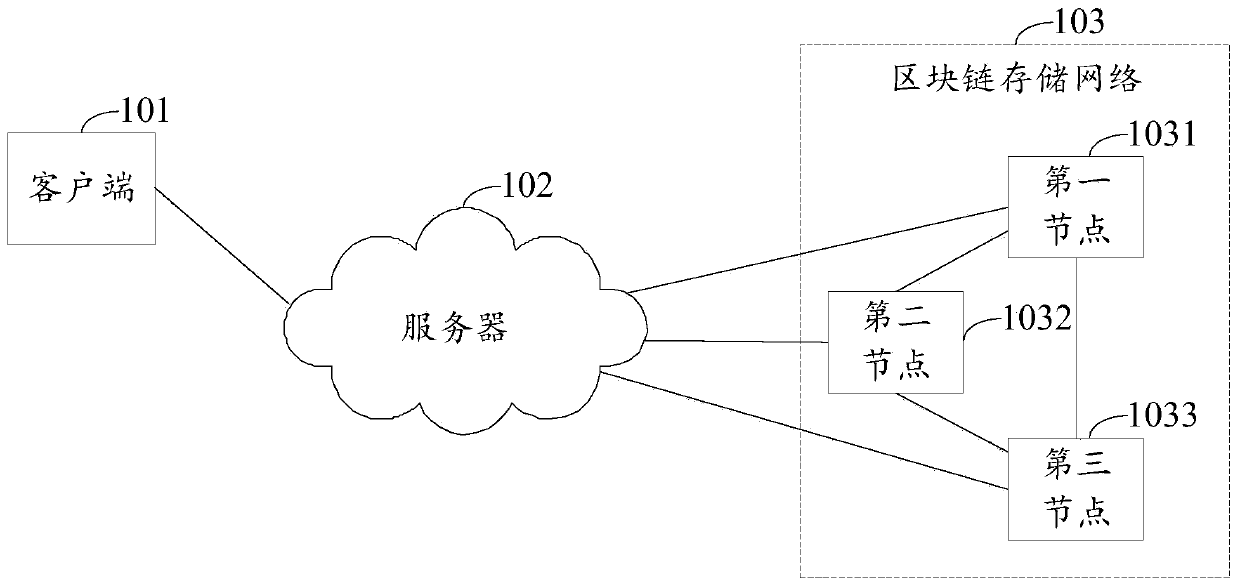
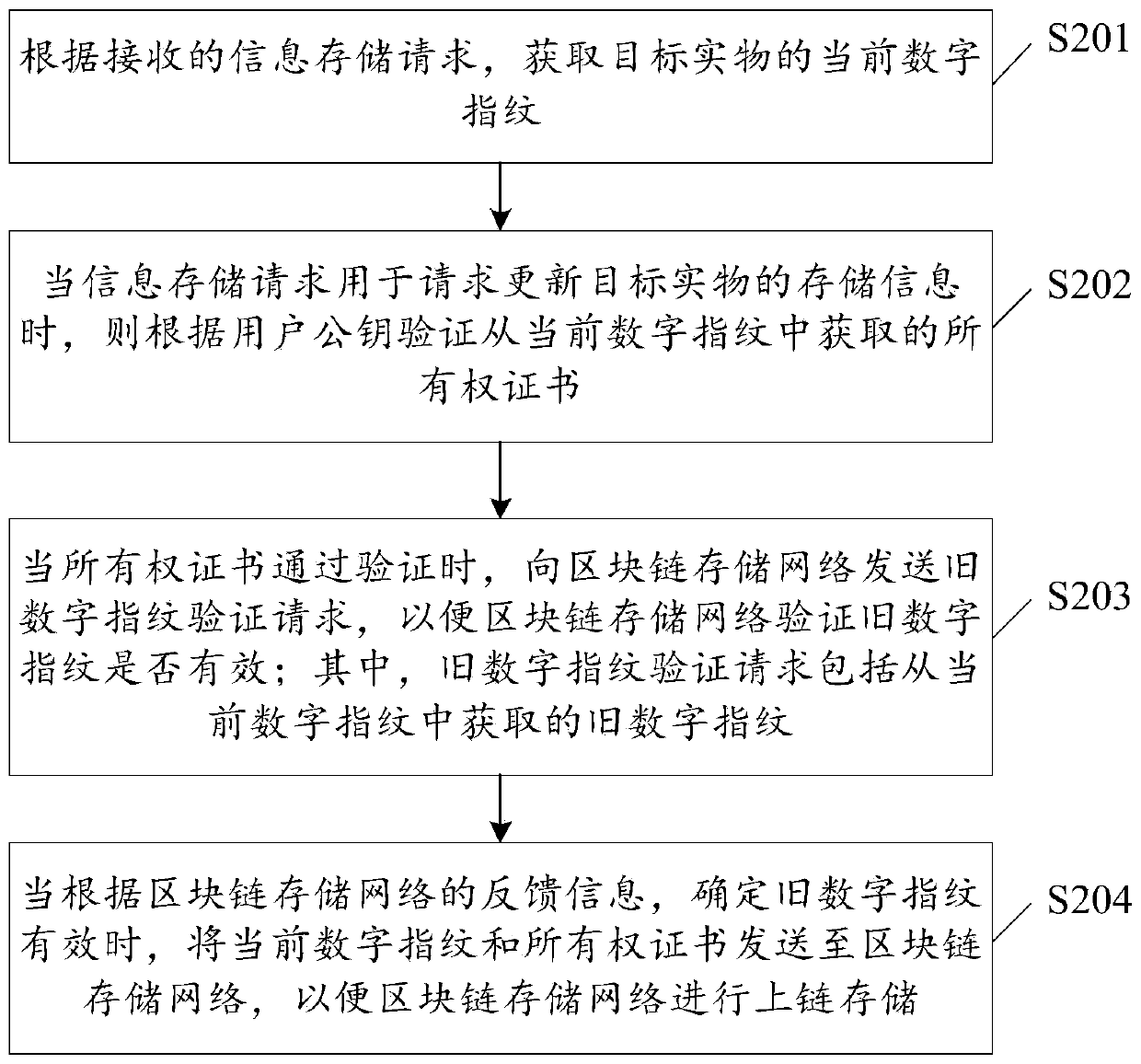
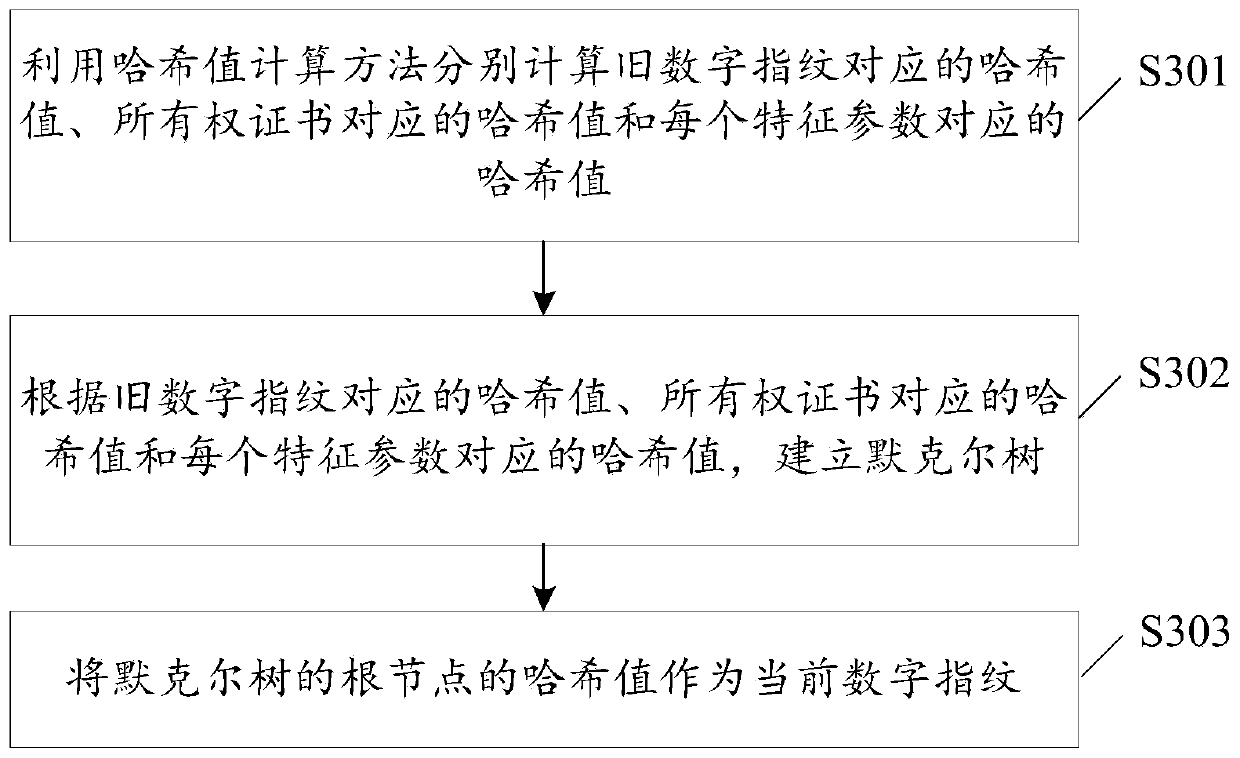
Real object information storage method and device and real object information searching method and device
ActiveCN109918874AImplement storageAccurate storageDigital data protectionDigital data authenticationRelevant informationInformation searching
The invention discloses a real object information storage method and device and a real object information searching method and device, and the method comprises the steps of storing a current digital fingerprint which passes the verification of a user public key and the validity verification of a block chain storage network into the block chain storage network, and achieving the information storageof a target real object. The current digital fingerprint comprises the old digital fingerprint used for recording the historical information of the target object; Therefore, when the stored information in the block chain storage network is used for verifying whether the old digital fingerprint is valid or not; whether the current information change occurs on the stored information of the target object or not can be confirmed. Therefore, no information omission exists between the current digital fingerprint stored in the block chain storage network and the stored old digital fingerprint. Therefore, omission of change information of the target object is avoided, integrity of information storage of the target object is achieved, so that a subsequent user can accurately find all historical information of the target object, the user is prevented from being cheated due to the fact that the user does not know relevant information of the target object, and rights and interests of the user aremaintained.
Owner:度小满科技(北京)有限公司
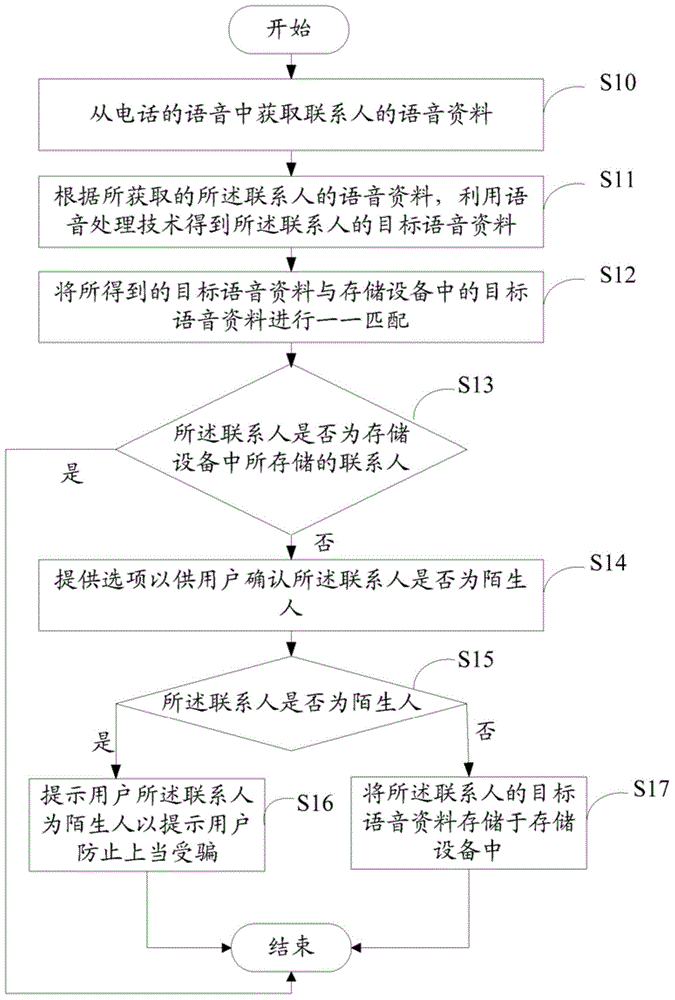
Phone fraud prevention system and method
The invention relates to a phone fraud prevention system and a method. The method comprises the steps of acquiring voice information of a contact when an electronic device and a communicator of the contact are in communication; according to the voice information of the contact, acquiring target voice information of the contact through a voice processing technology; matching the acquired target voice information with each piece of target voice information stored in a storage device in advance so as to obtain matching ratio of the target voice information of the contact to each piece of target voice information stored in the storage device; judging whether the contact is among the contacts stored in the storage device according to all the matching ratios; if the contact is not among the contacts stored in the storage device, offering options for a user to confirm whether the contact is a stranger; and if the contact is not a stranger, storing the target voice information of the contact in the storage device of the electronic device. Through adoption of the method, the user can be warned timely so as not to be deceived by phone fraud.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Security protection method, mobile terminal and device having storage function
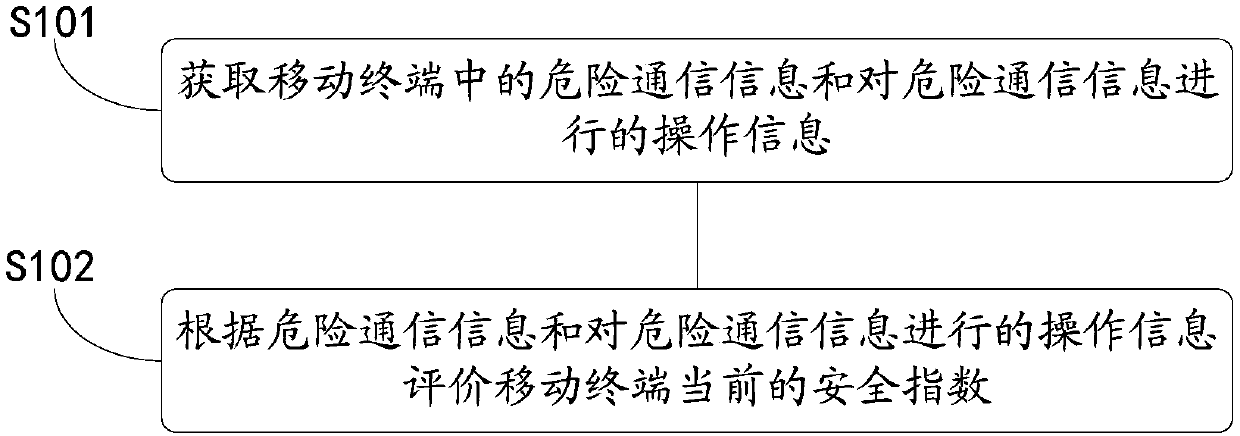
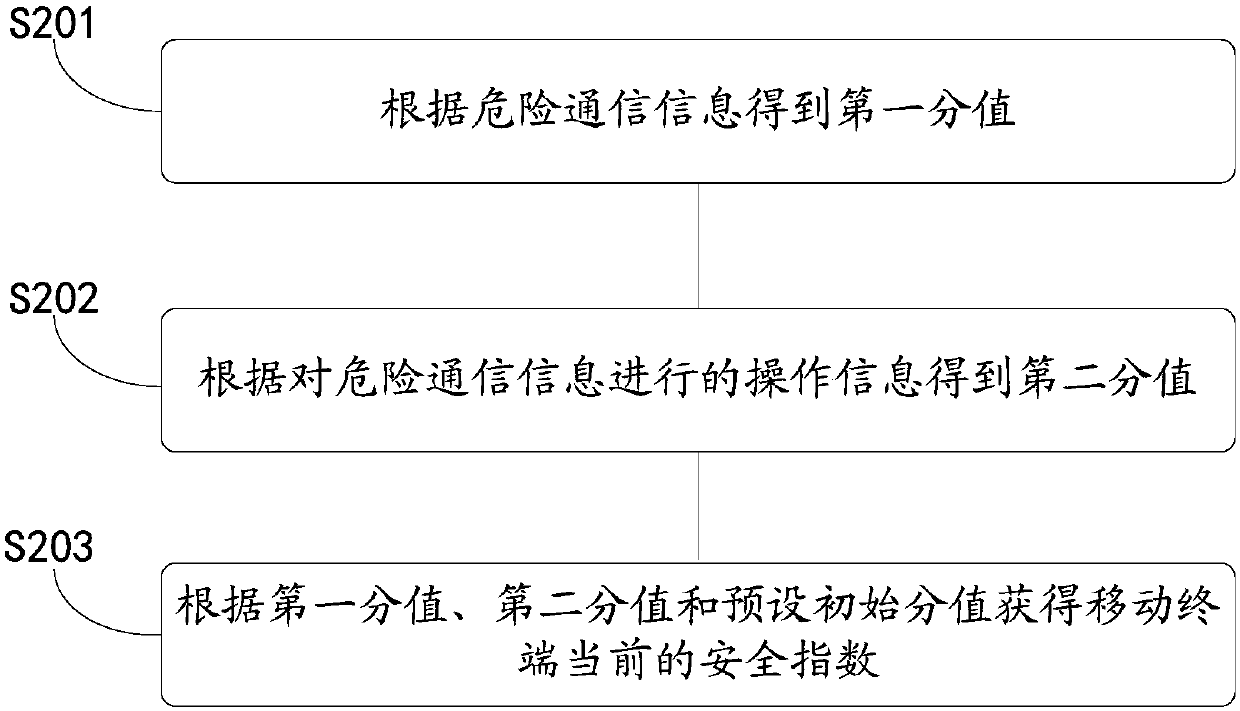
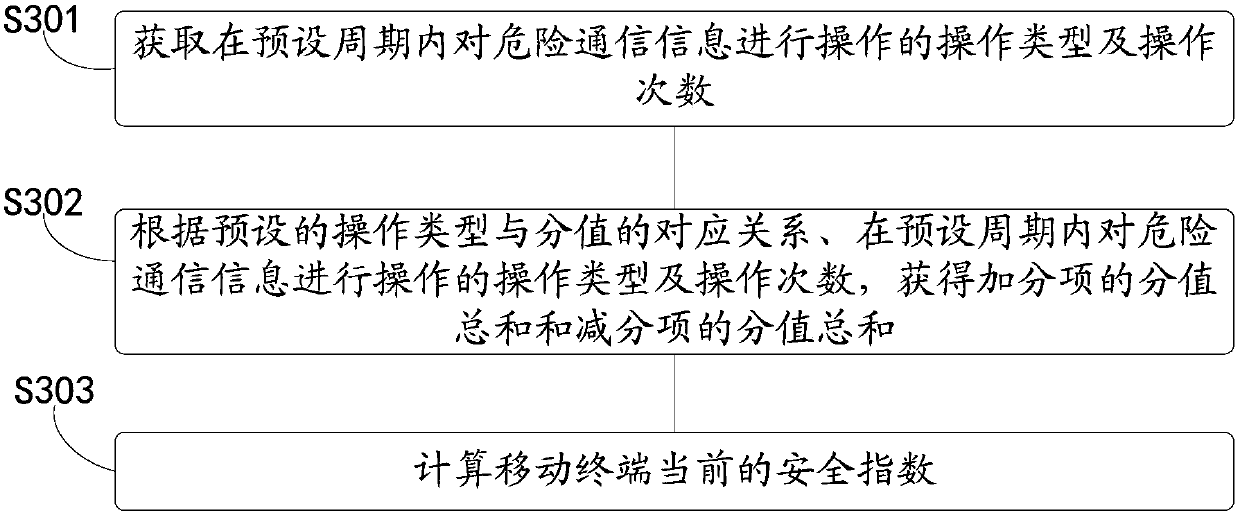
InactiveCN107623915APrevent being cheatedProtection securityMessaging/mailboxes/announcementsSecurity arrangementSecurity indexHazard communication
The invention discloses a security protection method, a mobile terminal and a device having the storage function. The method comprises the steps that hazard communication information in the mobile terminal and operation information performed on the hazard communication information are acquired; and the current security index of the mobile terminal is evaluated according to the hazard communicationinformation and the operation information performed on the hazard communication information. With application of the mode, the protection effect of the fraud prevention technology can be enhanced bythe method.
Owner:BEIJING ZHUMU LANGMA MOBILE COMM CO LTD
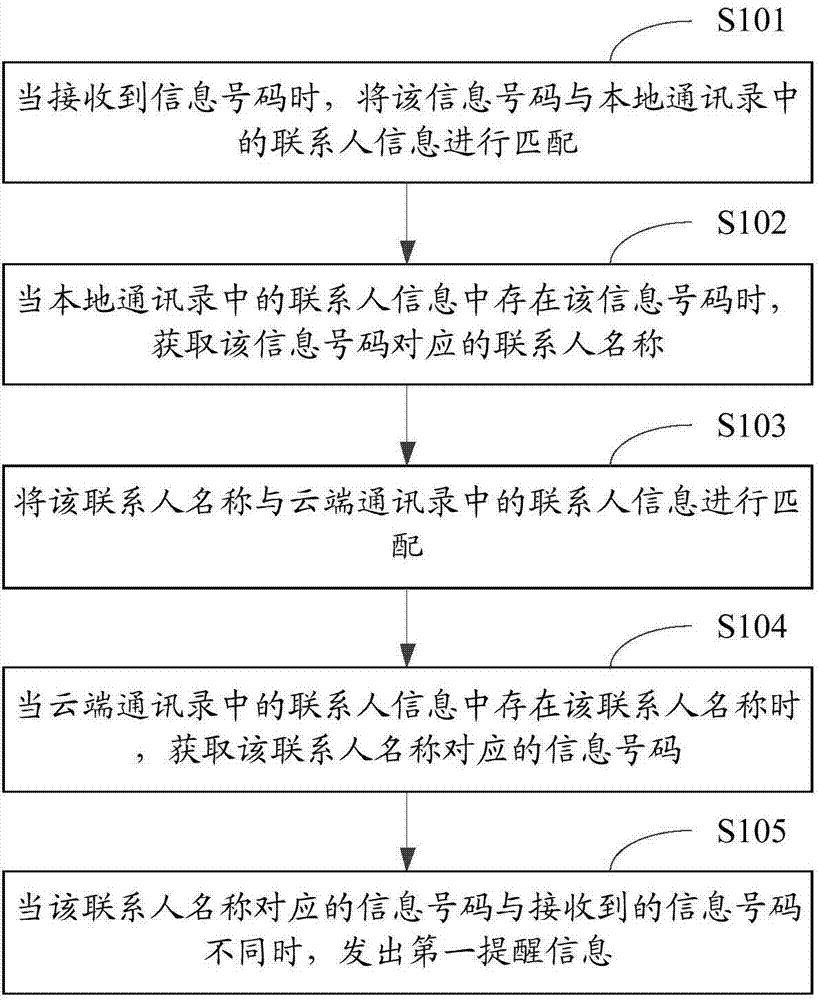
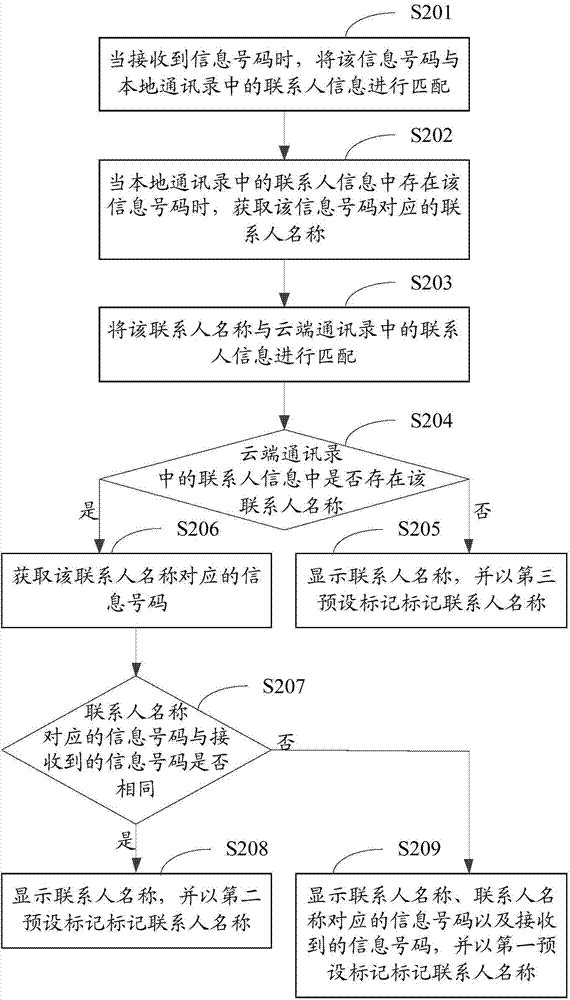
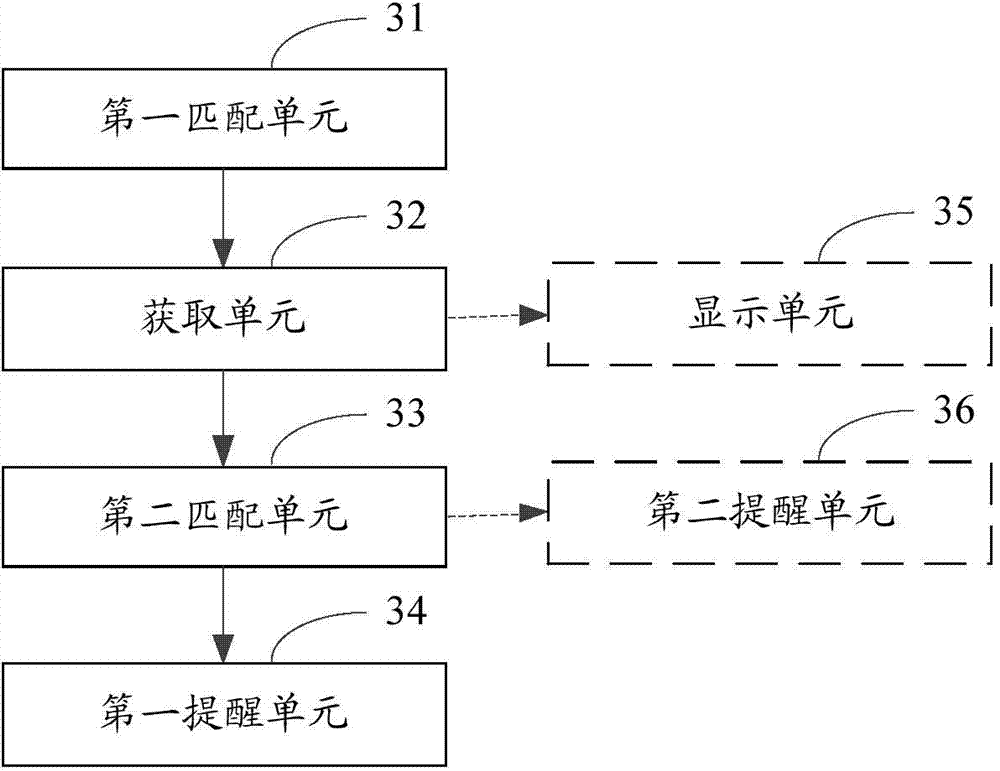
Message number recognition method and device
ActiveCN104754104ABe vigilantPrevent being cheatedSubstation equipmentContact NameComputer engineering
The invention is suitable for the technical field of communication and provides a message number recognition method and device. The message number recognition method includes: when a message number is received, matching the message number with contact information in a local address list; when the contact information in the local address list contains the information number, acquiring contact name corresponding to the information number; matching the contact name with contact information in a cloud address list; when the contact information in the cloud address list contains the contact name, acquiring message number corresponding to the contact name; when the message number corresponding to the contact name is different from the received information number, sending out a first prompting message. By recognizing vicious communication initiators, a user is enabled to raise his or her vigilance, so that the user is effectively prevented from being deceived.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
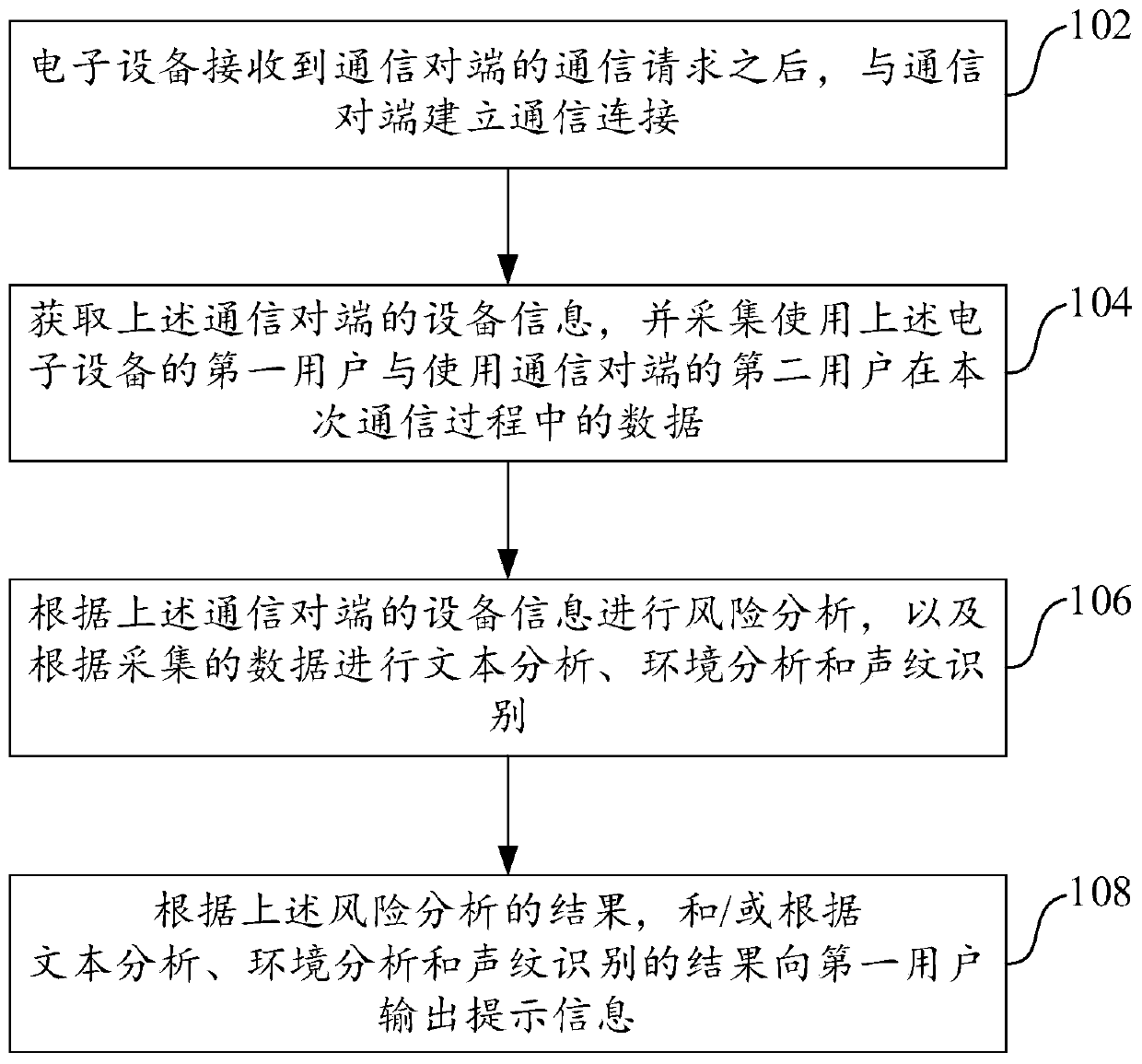
Communication network fraud identification method and apparatus, and electronic device
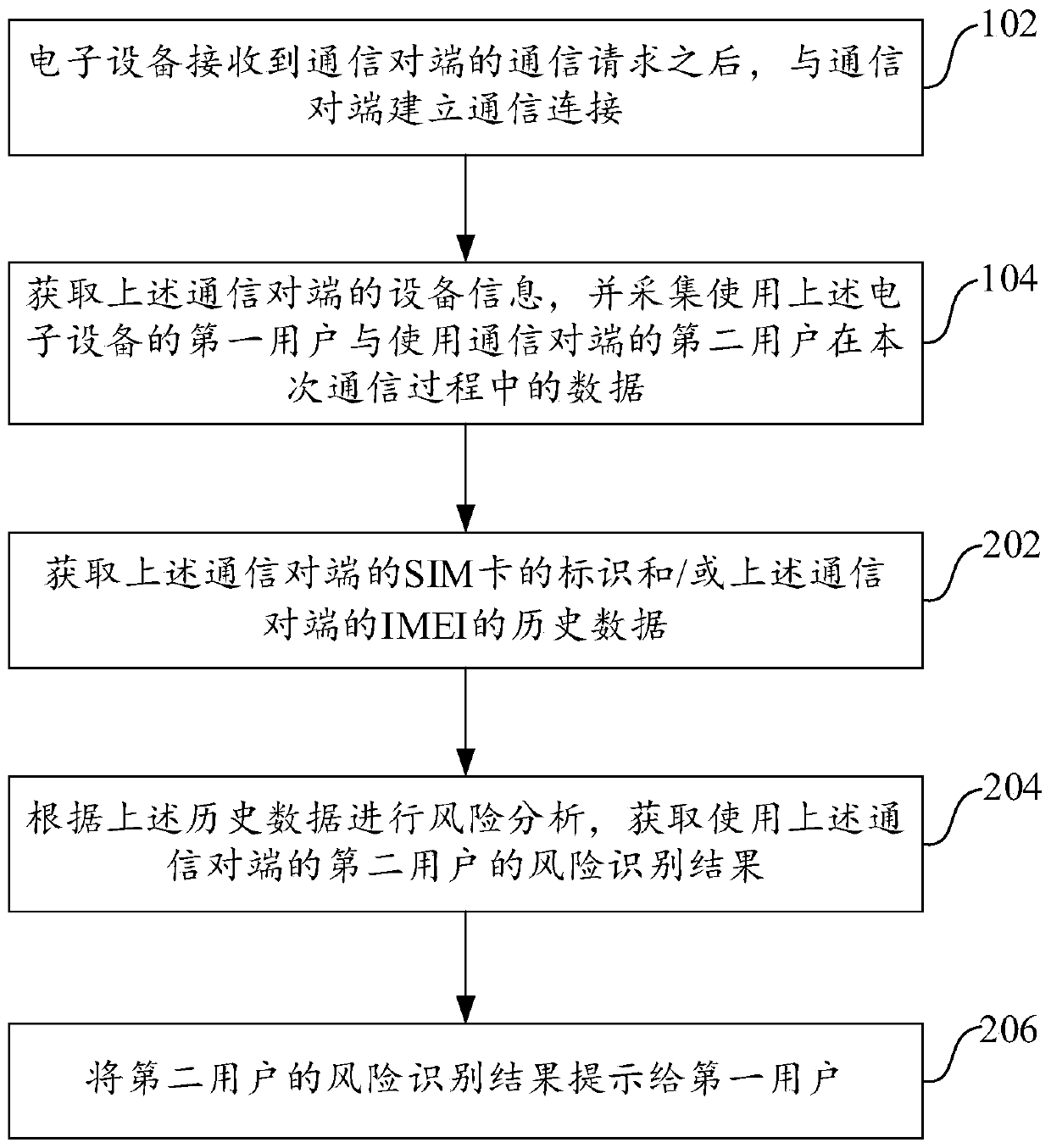
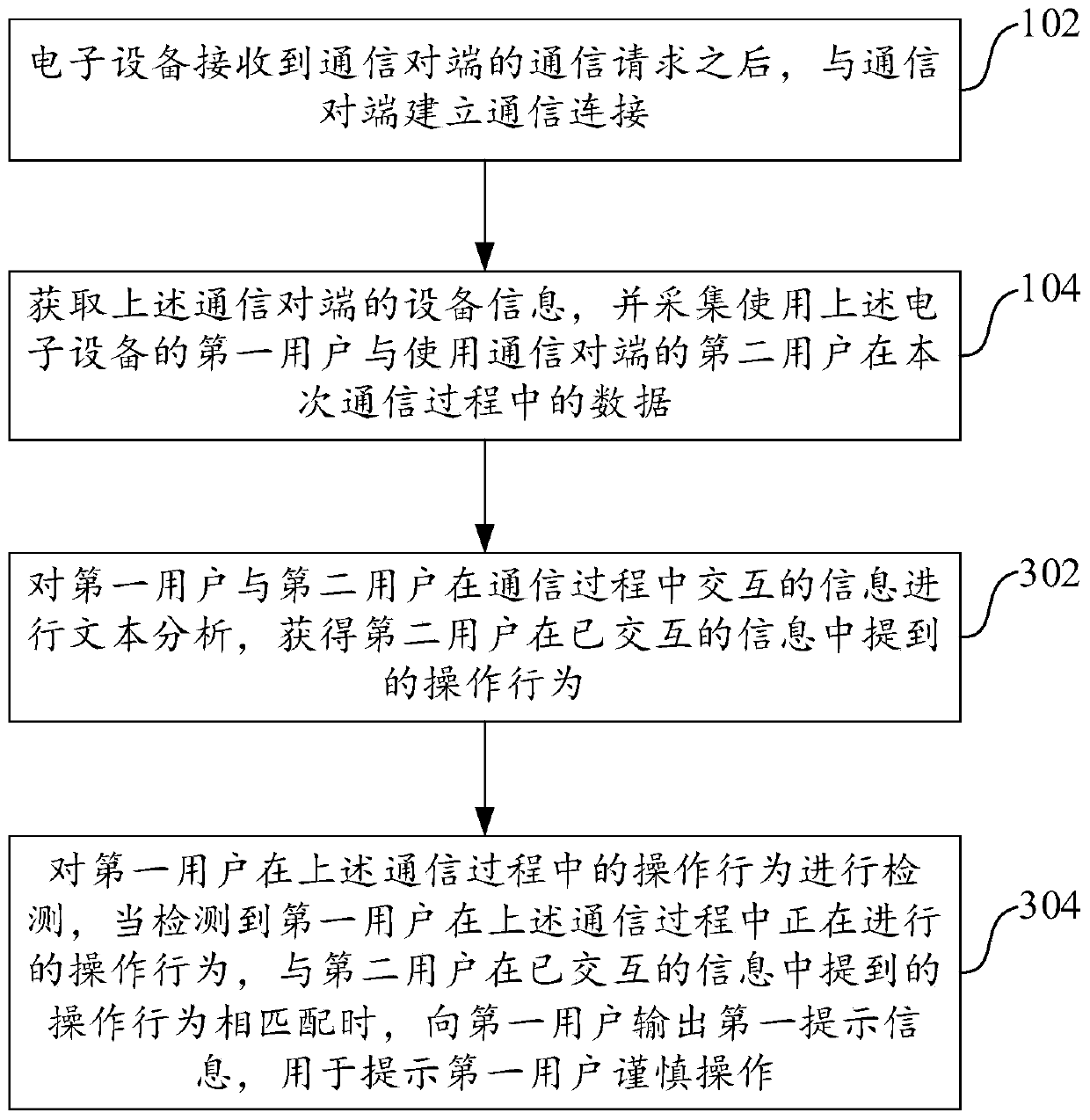
ActiveCN111601000APrevent being cheatedRealize risk management and controlSupervisory/monitoring/testing arrangementsComputer networkInternet fraud
Embodiments of the invention provide a communication network fraud identification method and apparatus, and an electronic device. The invention discloses a communication network fraud identification method. The electronic devicereceives a communication request of a communication opposite terminal, and then establishes communication connection with a communication opposite terminal; then, the electronic deviceacquires equipment information of the communication opposite terminal; thedata of a first user is acquired by using the electronic device and a second user using the communication opposite terminal in the communication process; risk analysis is carried out according to the equipment information of the opposite communication terminal; text analysis, environment analysis and voiceprintrecognition are carried out according to the collected data; and finally, according to a risk analysis result, a and / or the prompt information is output to the first user according to the results of the text analysis, the environment analysis and the voiceprint recognition, so that the information output by the communication opposite terminal in the communication process can be recognized and prompted at the first time when the two communication parties begin to communicate, and accompanying risk management and control are realized.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Device specially used for cleaning city small-advertisements
InactiveCN109092725AProtect the appearance of the cityImprove aestheticsCleaning using toolsHuman environmentEngineering
The invention belongs to the technical field of environmental protection, and provides a device specially used for cleaning city small-advertisements. The device specially used for cleaning the city small-advertisements comprises a shell assembly and a heating assembly. The shell assembly comprises a handle, a fan shell, a protective shell, a shovel blade and a blade piece. The fan shell is fixedly connected with the handle. The fan shell is positioned on the outer surface of the handle, the protective shell is fixedly connected with the fan shell, and the protective shell is positioned on theouter surface of the fan shell. An electric heating wire generates heat in a heating chamber so as to heat the air in the whole heating chamber; an electric fan blows out the hot air in the heating chamber to heat the small-advertisements on the roadside, so that the small-advertisements lose stickiness; then, one corners or the side faces of the small advertisements are shoved up by the blade piece; and then, the small advertisements on the roadside are removed, so that the appearance of a city is protected, the beauty of the city is improved, and the human environment of the city is protected.
Owner:芜湖品源装饰工程有限责任公司
Manual carving and machine carving automatic distinguishing device
InactiveCN112577963APrevent being cheatedAvoid manual detection errorsOptically investigating flaws/contaminationBilateral symmetryIndustrial engineering
The invention discloses a manual carving and machine carving automatic distinguishing device which comprises a machine body and a detection cavity formed in the machine body. Entrances and exits communicating with the outside are symmetrically formed in the left wall and the right wall of the detection cavity, a first electric sliding rail is arranged on the bottom wall of the detection cavity, afirst sliding block is arranged on the first electric sliding rail in a sliding mode, an electric rotating shaft is rotationally arranged at the upper end of the first sliding block, a bottom plate isfixedly arranged on the electric rotating shaft, a second electric sliding rail is arranged at the upper end of the bottom plate, and clamping blocks are arranged on the second electric sliding railin a bilateral symmetry sliding mode. The radian of the convex part on the carving image can be automatically detected. If the radian of the convex part is more smooth, the work is carved by a machine, so that manual detection is not needed, errors caused by manual detection are avoided, meanwhile, whether the lower end of the convex part of the image sinks inwards or not can be detected, whetherthe work is carved manually or not is judged, the detection accuracy is improved, and a purchaser is prevented from being cheated easily.
Owner:广州钇普科技有限公司
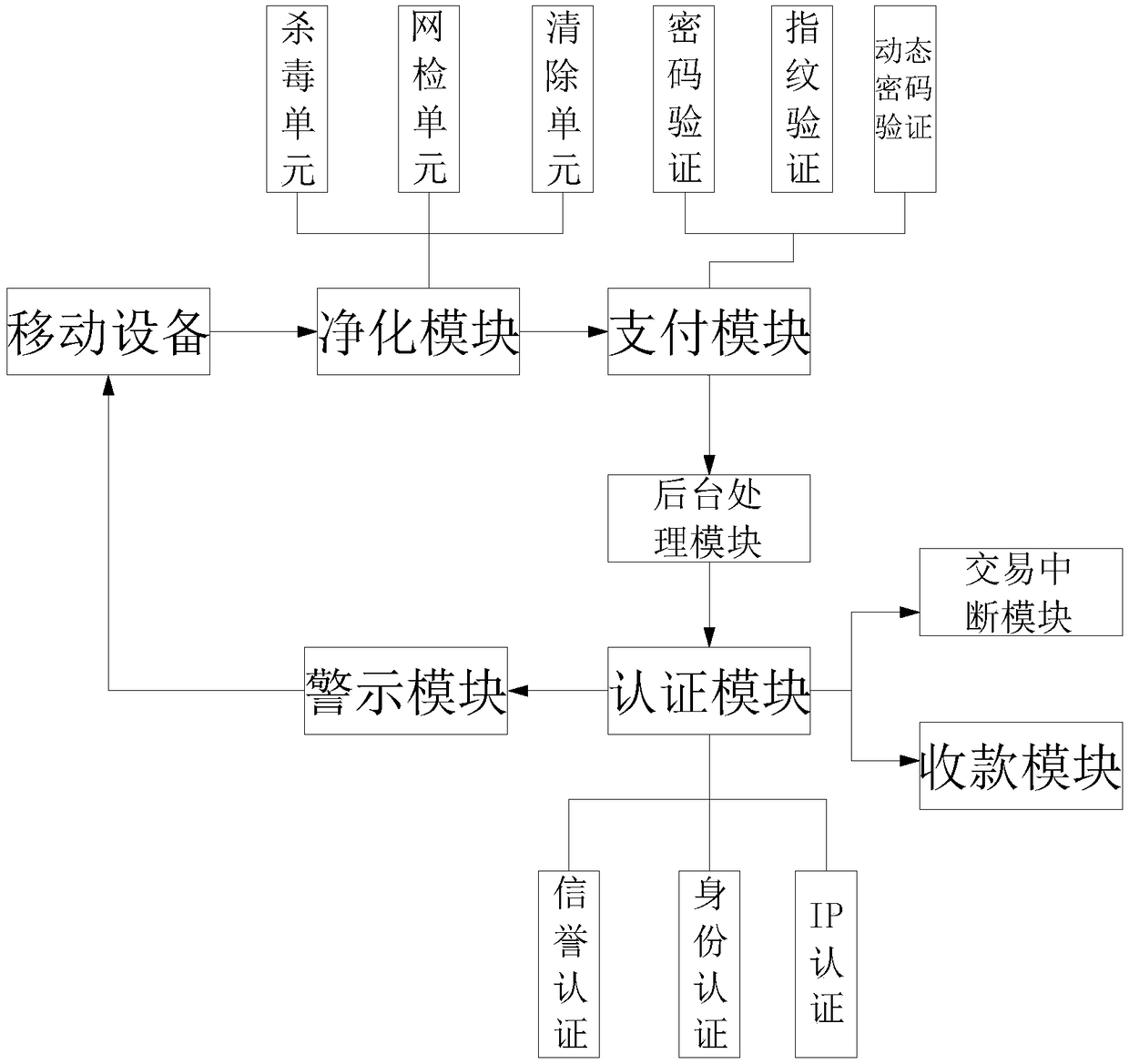
Mobile Internet payment risk control method and system
InactiveCN108520418AImprove securitySecurity ConfirmationTransmissionProtocol authorisationBackground processWireless network
The invention discloses a mobile Internet payment risk control method and system. The method includes steps: S1, a mobile device submits an order and enters a payment page, a purification module is started at the moment, an antivirus unit scans a mobile phone and automatically cleans viruses, and when the mobile device is connected with a wireless network, a network check unit is started to confirm the security of the wireless network; meanwhile, a cleaning unit in the purification module forcedly closes all operating third party background software, and when the purification module is safelypassed, a payment module is entered; S2, after the payment module is entered, firstly verification is passed through a payment password and a fingerprint password, and when the payment amount exceedsa specific amount, the mobile device receives a dynamic password, and the payment is completed through second verification of input of the dynamic password; and S3, the payment fund enters a background processing module for saving. According to the method and system, the security is high, dual safety protection can be realized before and after payment of the mobile device, and payment risks are greatly avoided.
Owner:WUHU LERUISI INFORMATION CONSULTING
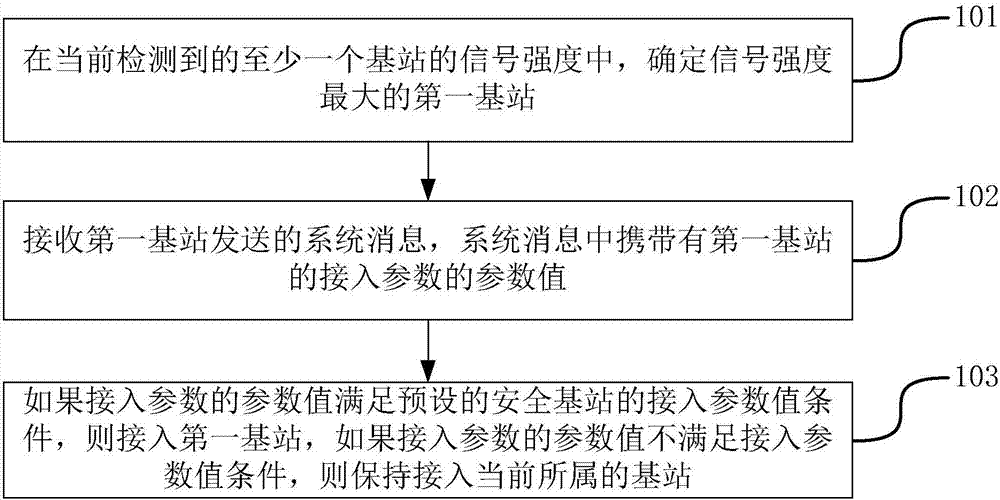
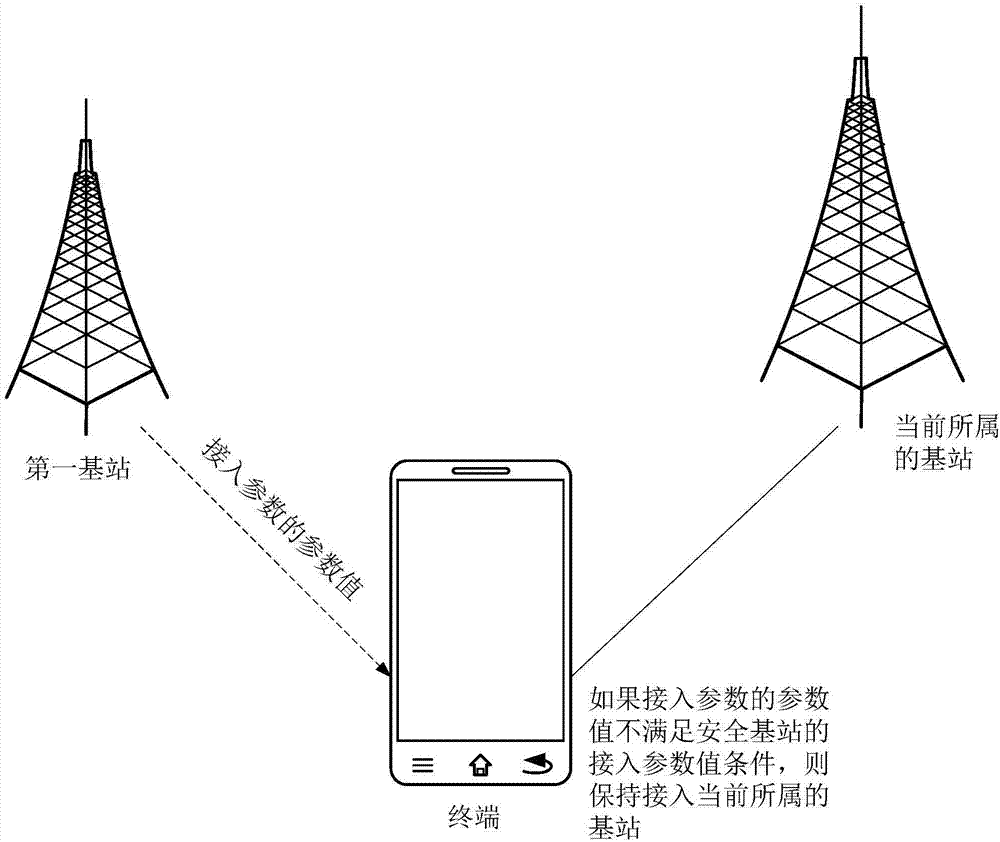
Base station access method and device
ActiveCN107404723APrevent being cheatedAvoid Scam Text MessagesAssess restrictionTransmission monitoringHigh signal intensityAccess method
The invention relates to a base station access method and device, and belongs to the technical field of computers. The method comprises the steps that a first base station with the highest signal intensity is determined according to the currently-detected signal intensities of at least one base station; a system message sent by the first base station is received, wherein the system message carries parameter values of access parameters of the first base station; if the parameter values of the access parameters meet the preset access parameter value conditions of a secure base station, a terminal accesses the first base station; and if the parameter values of the access parameters do not meet the access parameter value conditions, the terminal keeps accessing the base station to which the terminal belongs. By adopting the method and device, the condition that the terminal accesses an insecure base station can be avoided, the condition that the terminal receives fraud information is prevented, and therefore a user is prevented from being deceived.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
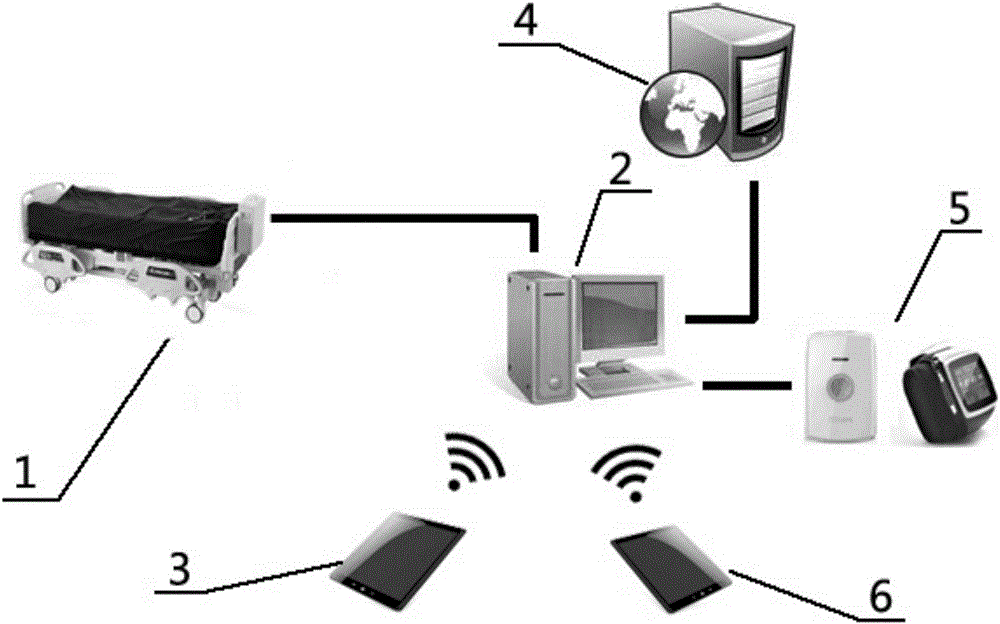
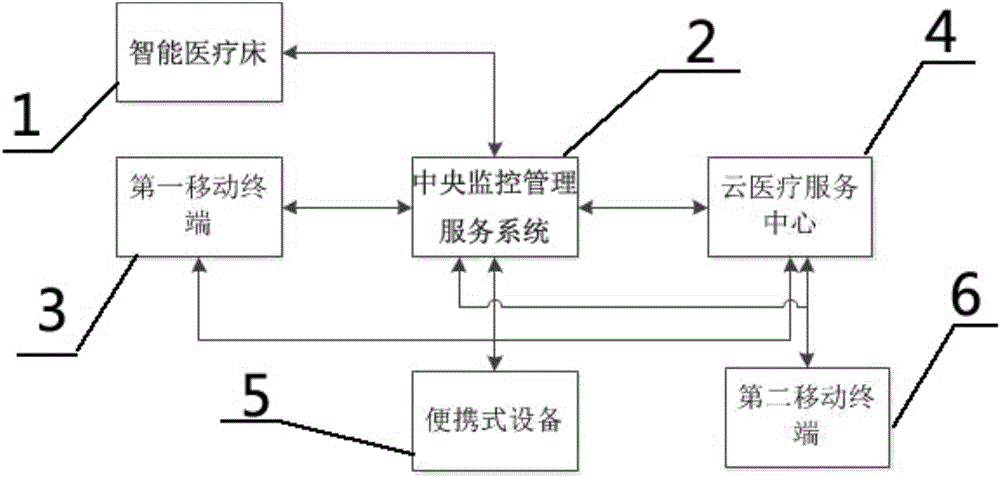
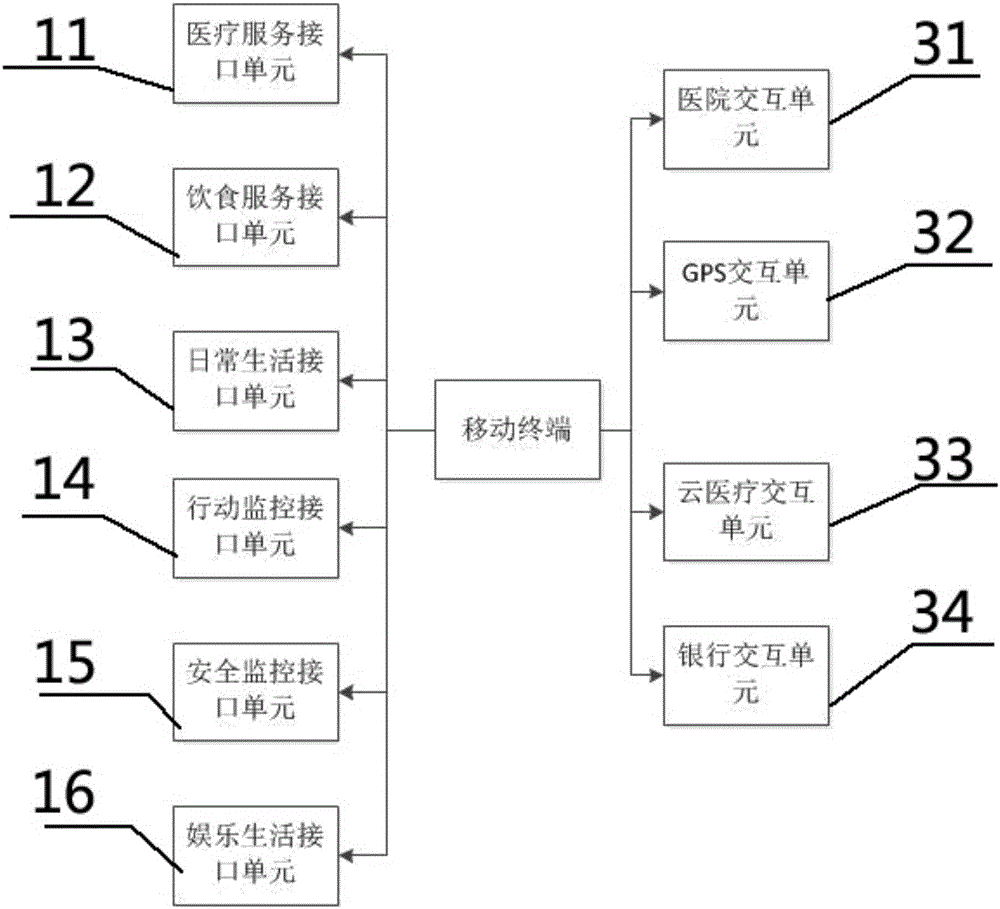
Intelligent cloud medical-care system based on intelligent medical bed
InactiveCN106777869AProtect your healthPrevent being cheatedTelemedicineSpecial data processing applicationsService systemReal-time computing
The invention provides an intelligent cloud medical-care system based on an intelligent medical bed; the intelligent cloud medical-care system comprises the intelligent medical bed, a central monitoring management service system, and a first mobile terminal; the intelligent medical bed and a portable device are in communication connection to the central monitoring management service system, the central monitoring management service system is in communication connection with a cloud medical service center through a network, the cloud medical service center can connect central monitoring management service systems of multiple hospitals, the intelligent medical bed is provided with a plurality of communication ports and external interfaces, and the central monitoring management service system is used for receiving and processing a user's current health parameters sent by the intelligent medical bed, sending an alarm signal to the first mobile terminal according to the user's current health parameters, and providing the user with various medical-care living services. The intelligent cloud medical-care system can meet the medical-care needs of users, can provide 24-hour monitoring for the body of each user, can provide automatic alarming, and provides a brand-new medical-care mode for the user.
Owner:黄劲涛
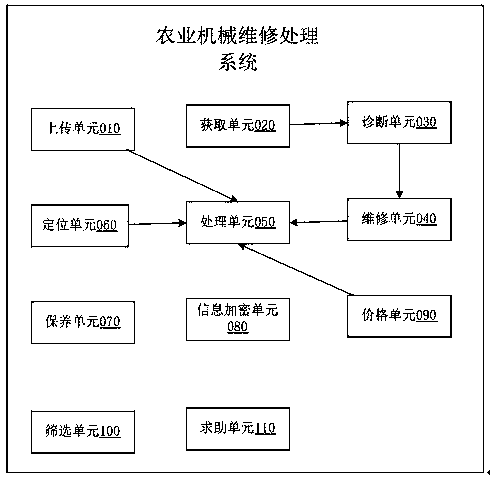
Agricultural mechanical fault processing system based on big data
InactiveCN108564183ATargetedComprehensiveData processing applicationsOriginal dataAgricultural engineering
The invention discloses an agricultural mechanical fault processing system based on big data. The system comprises an uploading unit, an acquisition unit, a diagnosis unit, a repairing unit, a positioning unit and a processing unit, wherein the uploading unit is used for uploading information of an agricultural machine by a user and establishing an original database; the acquisition unit is used for acquiring the information of the agricultural machine; the diagnosis unit is used for storing and collecting agricultural machine damage information, establishing a database, comparing informationtransmitted from the acquisition unit with that in an information library, and judging damage situations of the agricultural machine; the repairing unit is used for storing and collecting agriculturalmachine repairing information, establishing a database, comparing information transmitted from the diagnosis unit with that in the database, and determining a repairing scheme; the positioning unit is used for acquiring specific positions of repairing stores, fitting stores and agricultural machines in present areas; the processing unit is used for carrying out comprehensive processing and recommending appropriate repairing schemes according to the information. Due to the arrangement of the system, repairing information can be effectively recommended to users.
Owner:许谐兴
A method and system for anti-counterfeiting and traceability of watches based on two-dimensional codes
ActiveCN105701673BEasy to identifyPrevent being cheatedCommerceSpecial data processing applicationsLogistics managementDatabase
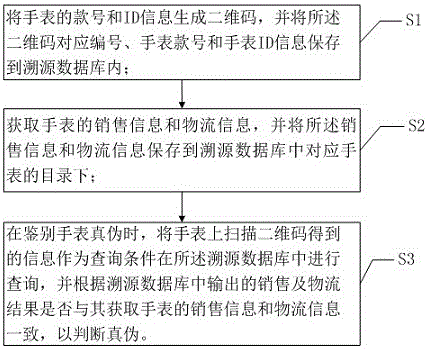
The present invention provides a watch anti-fake traceablility method and system based on two-dimensional codes. The style number and ID information of a watch are generated to be two-dimensional codes, and the two-dimensional codes are stored in a traceablility database; sale information and logistics information are stored in a directory corresponding to the watch in the traceablility database; and when the watch is subjected to true-false distinguishing, the information obtained by scanning the two-dimensional codes on the watch is taken as a query condition to perform query in the traceablility database, and the true and false is distinguished according to whether the sale and logistics results outputted from the traceablility database are consistent to the obtained sale information and logistics information of the watch or not. The watch anti-fake traceablility method and system based on two-dimensional codes are configured to perform laser printing two-dimensional codes and two-dimensional code ID on a watch through the laser two-dimensional codes technology and store the two-dimensional codes information and the sale and logistics information to the traceablility database so as to perform watch anti-fake traceablility through adoption of the traceablility database, facilitate true-false distinguishing of a watch for consumers and prevent the consumers from being deceived.
Owner:依波精品(深圳)有限公司
Intelligent house renting recommendation system based on big data and working method thereof
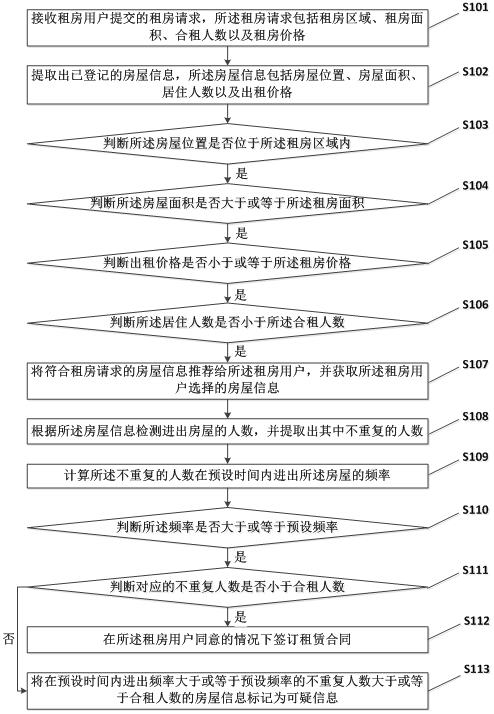
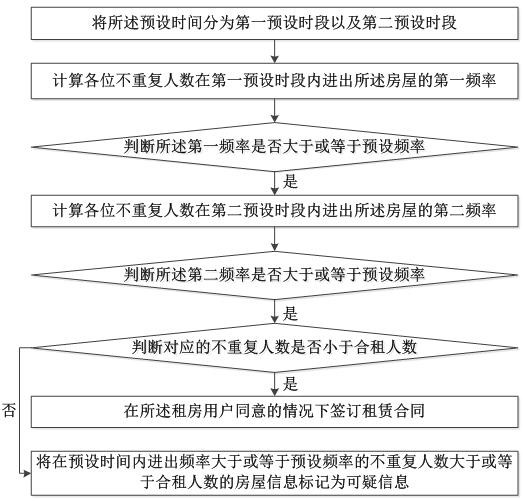
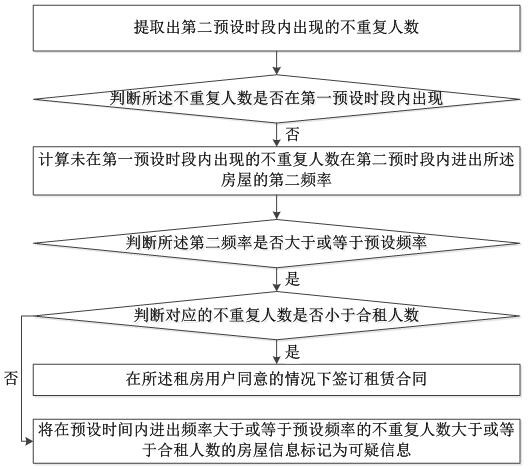
The invention discloses an intelligent house renting recommendation system based on big data and a working method thereof, and the system comprises: a first extraction module which is configured to extract registered house information; a first acquisition module which is configured to acquire house information selected by a house renting user; a personnel detection module which is configured to detect the number of people going in and out of the house; a second extraction module which is configured to extract the number of people who are not repeated; a first calculation module which is configured to calculate the frequency of the non-repetitive people going in and out of the house within a preset time; a fifth judgment module which is configured to judge whether the frequency is greater than or equal to a preset frequency or not; a sixth judgment module which is configured to judge whether the number of non-repetitive people whose in-out frequency is greater than or equal to the preset frequency within the preset time is less than the number of shared renters; and a marking module which is configured to mark the house information of which the in-out frequency is greater than or equal to the preset frequency and the number of non-repetitive people is greater than or equal to the number of joint tenants in the preset time as suspicious information.
Owner:苏州商信宝信息科技有限公司
A method and device for incoming and outgoing calls
ActiveCN106657535BPrevent being cheatedPrevent fraudCalling susbscriber number recording/indicationEngineeringTelephone number
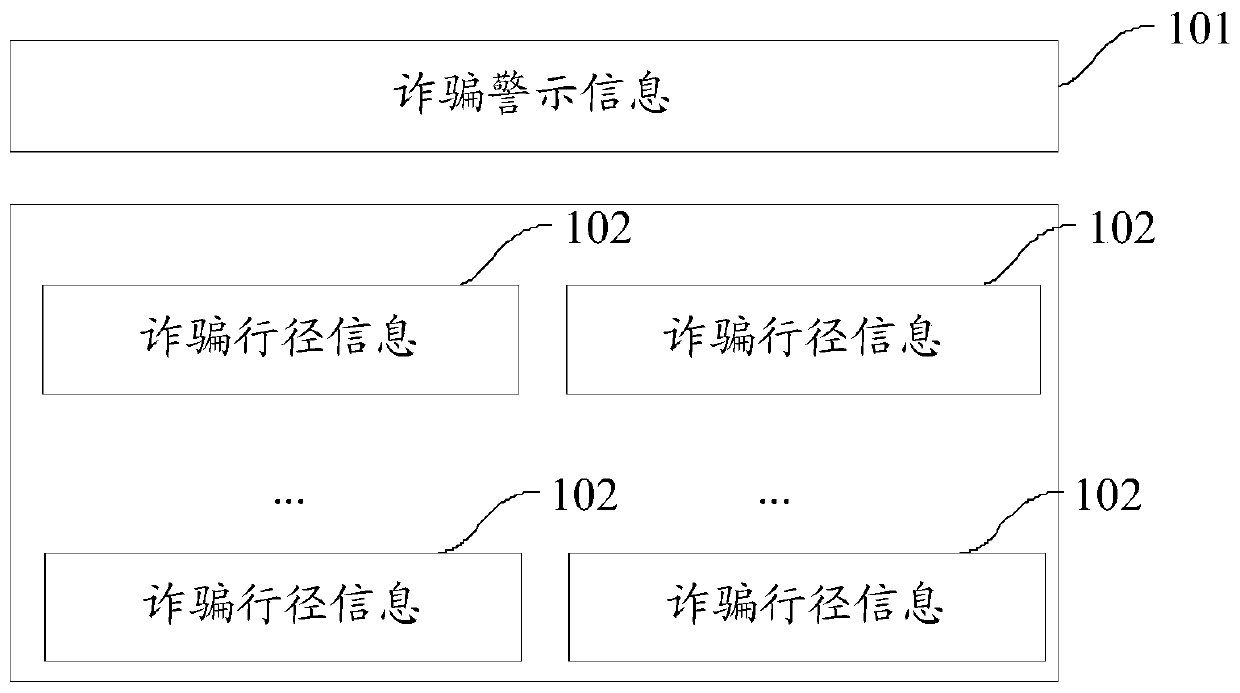
An embodiment of the invention provides an incoming and outgoing call processing method and device. The method specifically comprises the following steps: after incoming and outgoing calls are ended, a fraud prompt window is displayed; the fraud prompt window comprises at least one kind of fraud action information, the displayed fraud action information carries a link, and a user is enabled to jump to a page of the fraud action information by triggering the fraud action information. The fraud action information displayed via the method disclosed in the embodiment of the invention can be used for fulfilling a user fraud alerting function and a user fraud action knowledge education function, a user can be effectively prevented from being cheated by an incoming call which is just answered, and the method disclosed in the embodiment of the invention can be used for effectively preventing fraud behaviors caused by answering a call from a new fraud telephone number.
Owner:BEIJING QIHOO TECH CO LTD
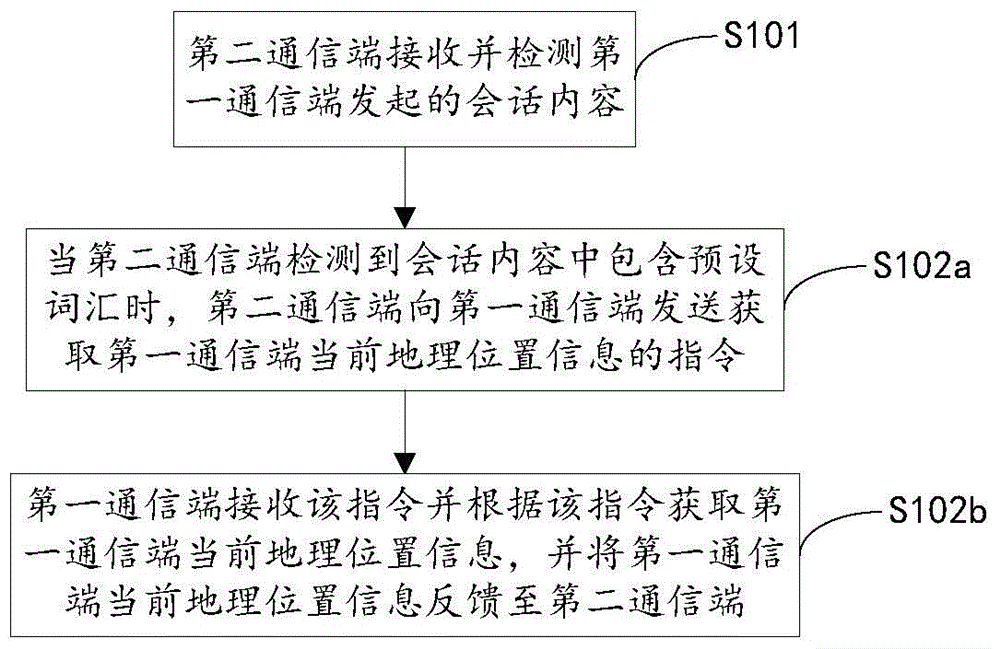
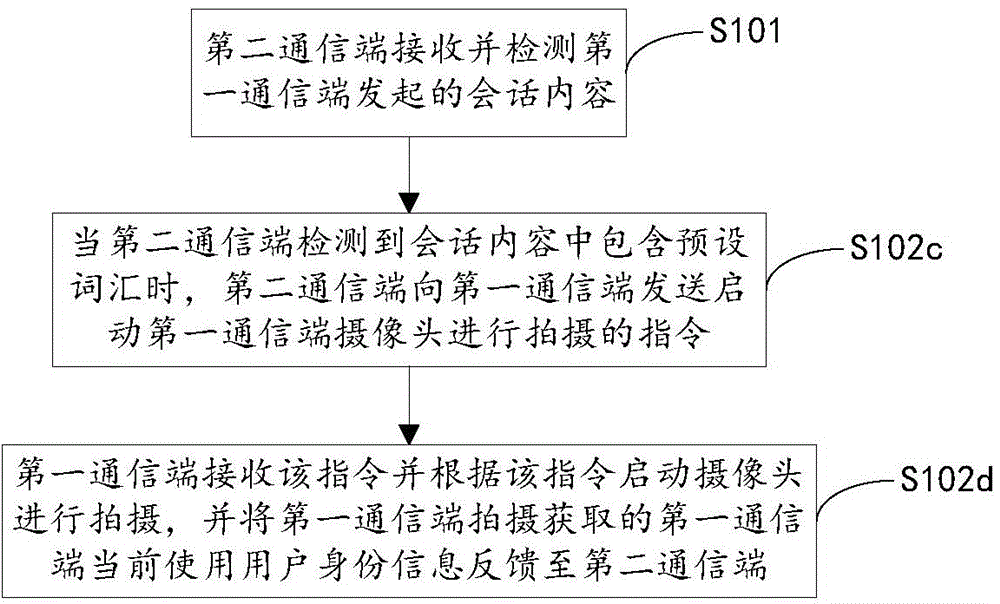
Secure communication method and system and communication terminal
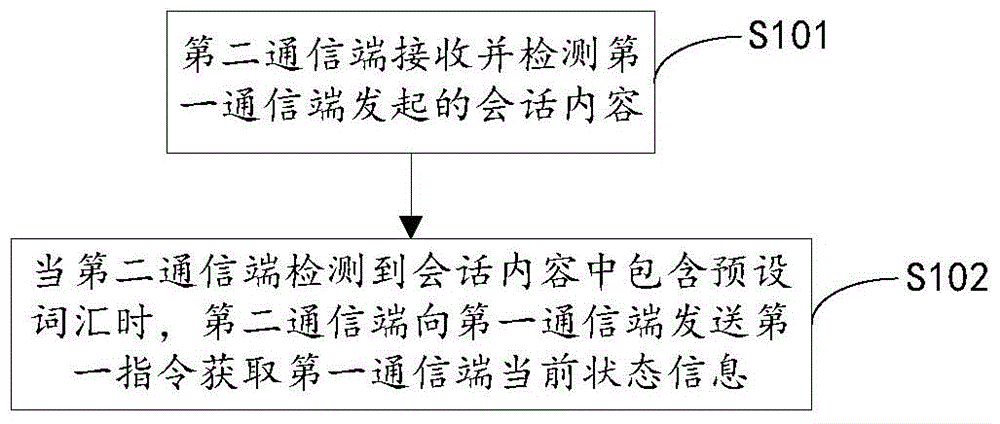
The invention discloses a secure communication method. The method comprises a detection step that a second communication terminal receives and detects session contents initiated by a first communication terminal; and an obtaining step that when the second communication terminal detects preset words contained in the session contents, the second communication terminal sends a first instruction to the first communication terminal, thus obtaining the current state information of the first communication terminal. Through application of the secure communication method provided by the invention, the first communication terminal and the second communication terminal build communication connection and carry out a session; the second communication terminal receives and detects the session contents initiated by the first communication terminal; when it is detected that the session contents sent to the first communication terminal by the second communication terminal have the preset words, the second communication terminal sends the first instruction to the first communication terminal, thus obtaining the current state information of the first communication terminal, a user can judges the reliability of this time session through viewing the current state information of the first communication terminal, and the user is prevented from being cheated.
Owner:BEIJING ERENEBEN INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com