Service request processing method and service request processing device
A technology of business requests and processing methods, applied in electrical components, transmission systems, etc., can solve problems such as stolen network accounts and high property, and achieve the effect of preventing theft or being cheated and increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
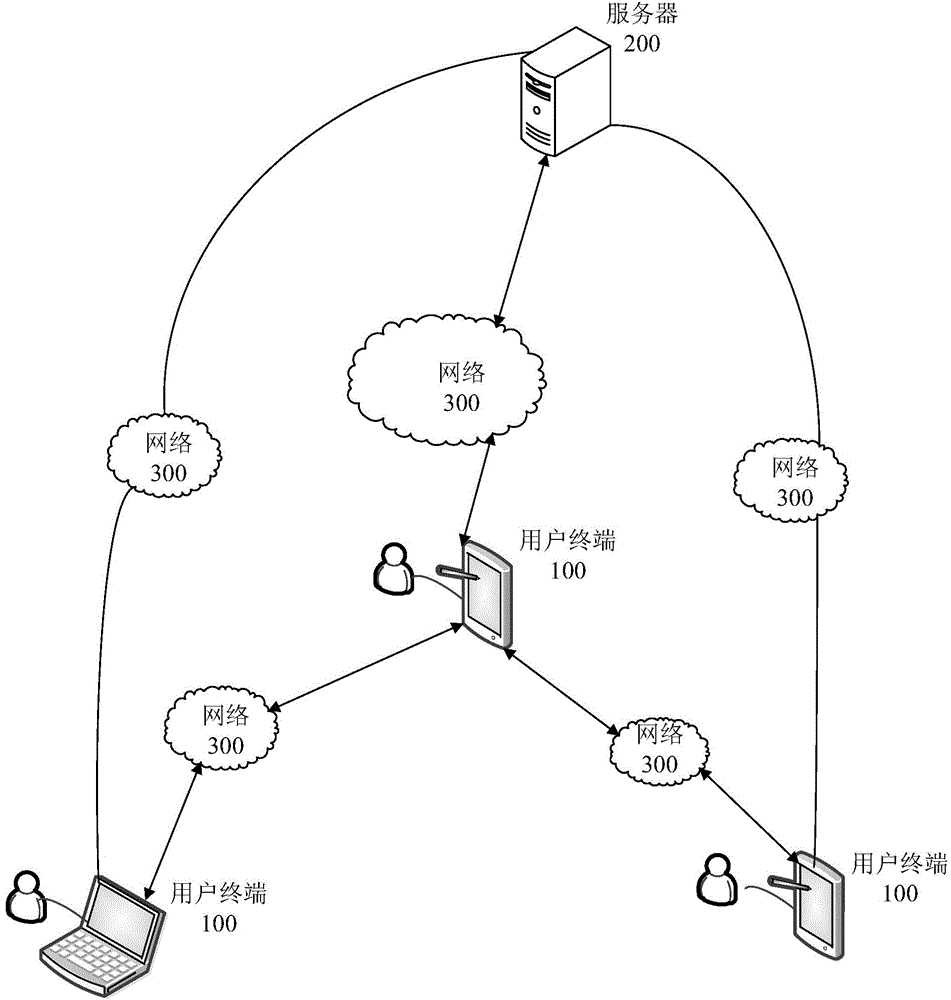
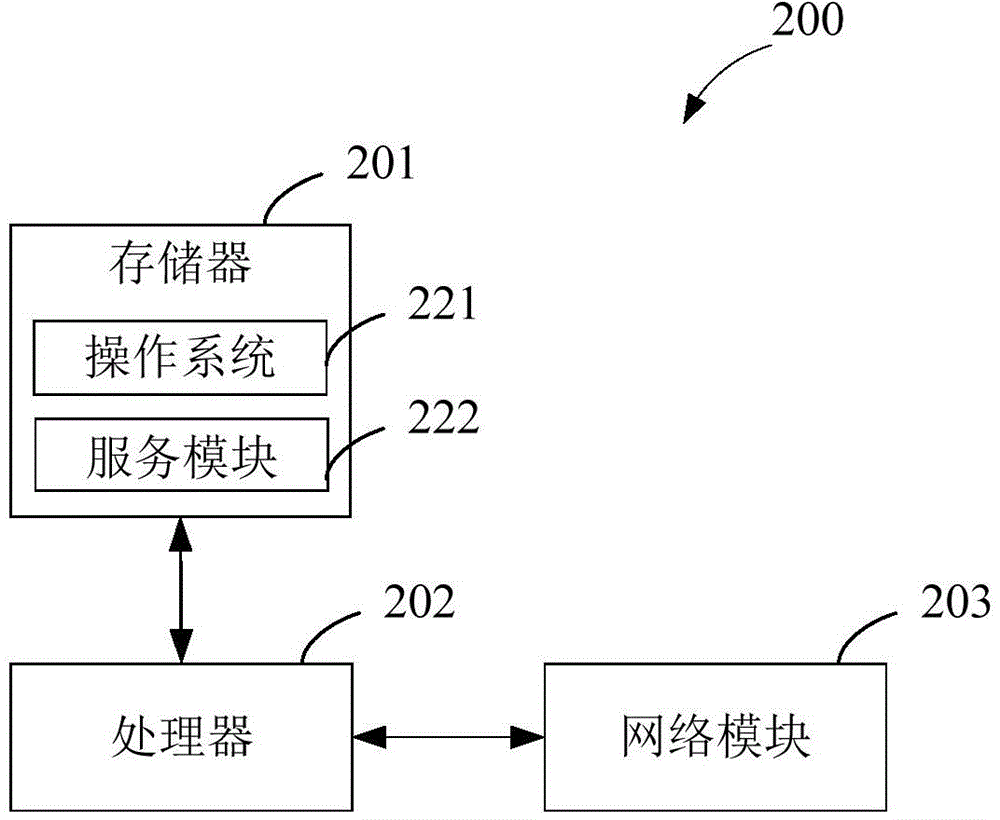
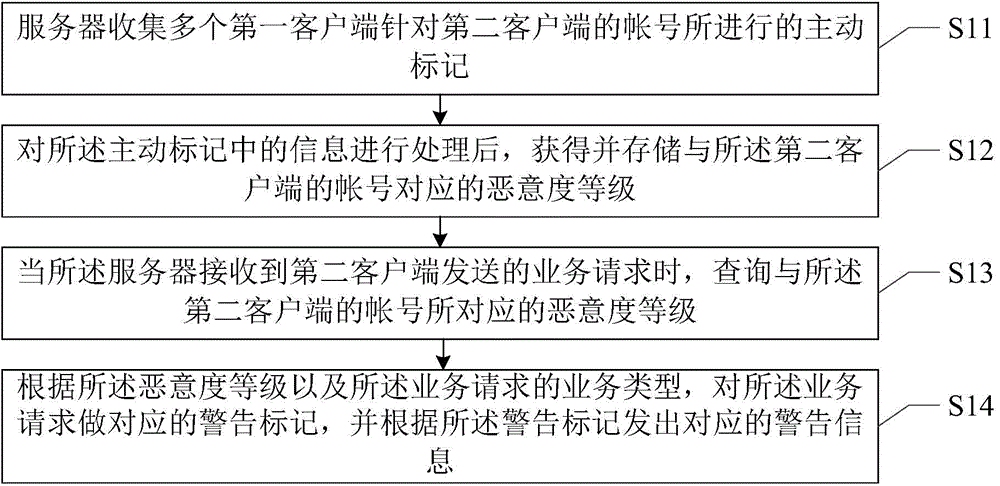
[0034] image 3 It is a flow chart of the service request processing method provided by the first embodiment of the present invention. combine figure 1 , this embodiment describes the processing flow of the server, and the service request processing method provided by this embodiment includes the following steps:
[0035] In step S11, the server collects active markings performed by a plurality of first clients on the accounts of the second clients.
[0036] The server 200 may collect the active marking performed by the user of the client (first client) installed on the user terminal 100 for the account of the second client. The user of the first client can actively mark the messages and accounts published in scenarios such as social networking, instant messaging, purchase, proxy payment, and payment, and submit them to the server.
[0037] In different application scenarios, active marking can take different forms.
[0038] For example, in an instant messaging application (...
no. 2 example
[0057] Figure 5 It is a flow chart of the service request processing method provided by the second embodiment of the present invention. combine figure 1 , this embodiment describes the processing flow of the server. In this embodiment, assuming that the business type processed by the server is a single business type, the method for processing a business request provided by this embodiment includes the following steps:
[0058] In step S201, the server collects active markings performed by a plurality of first clients on accounts of second clients.
[0059] Step S202, after processing the information in the active tag, obtain and store the malicious degree level corresponding to the account number of the second client.
[0060] Step S203, when the server receives the service request sent by the second client, query the malicious degree level corresponding to the account of the second client.
[0061] Step S204, judging whether the malicious degree level is smaller than a fi...
no. 3 example
[0066] Image 6 It is a flow chart of the service request processing method provided by the third embodiment of the present invention. combine figure 1 , this embodiment describes the processing flow of the server. In this embodiment, assuming that the server handles two or more business types, the method for processing a service request provided by this embodiment includes the following steps:
[0067] In step S301, the server collects active markings performed by a plurality of first clients on accounts of second clients.
[0068] Step S302, after processing the information in the active tag, obtain and store the malicious degree level corresponding to the account number of the second client.
[0069] Step S303, when the server receives the service request sent by the second client, query the malicious degree level corresponding to the account of the second client.
[0070] Step S304, judging whether the malicious degree level is smaller than a first threshold.
[0071] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com