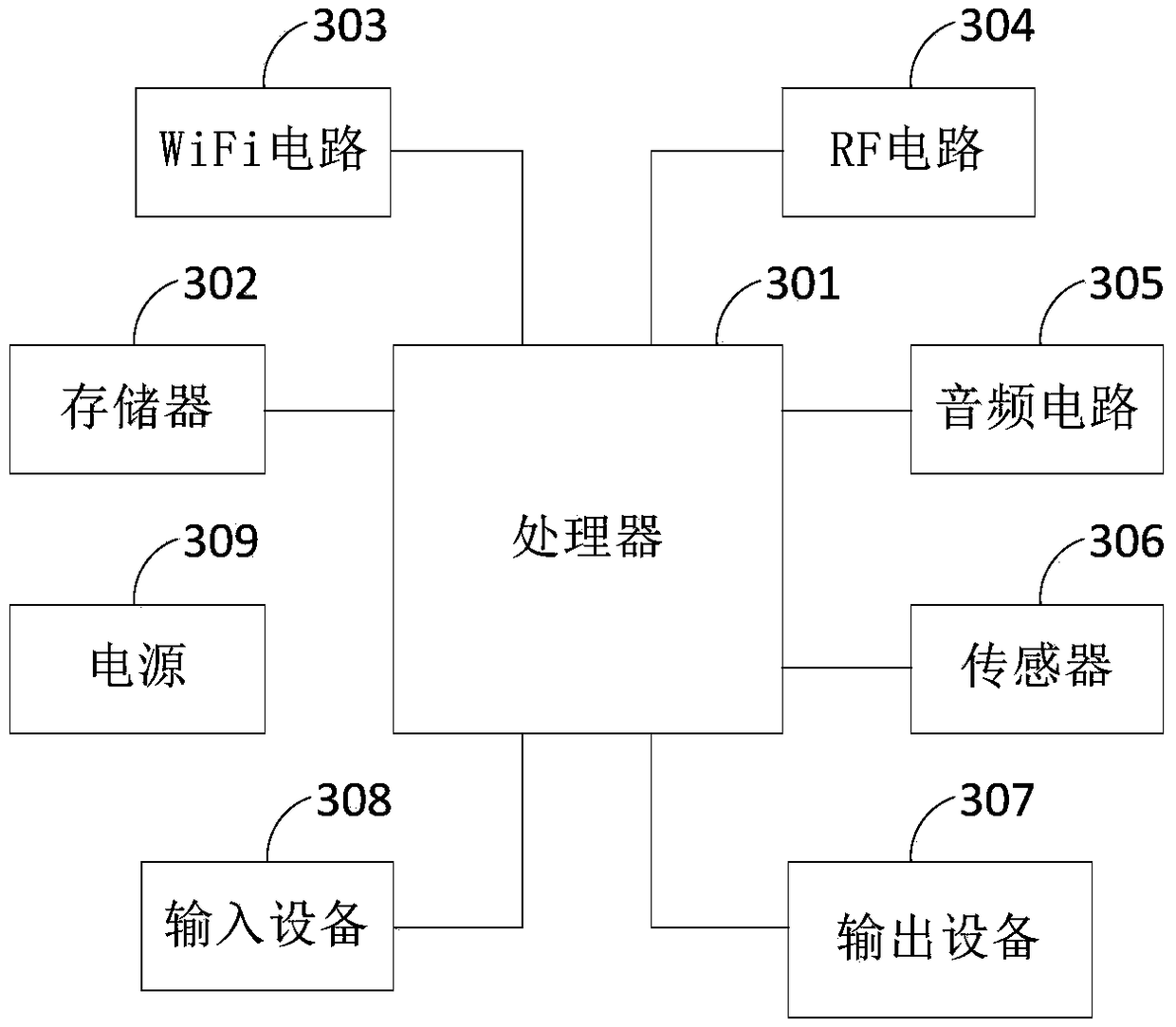
Patents
Literature
40results about How to "Avoid being scammed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
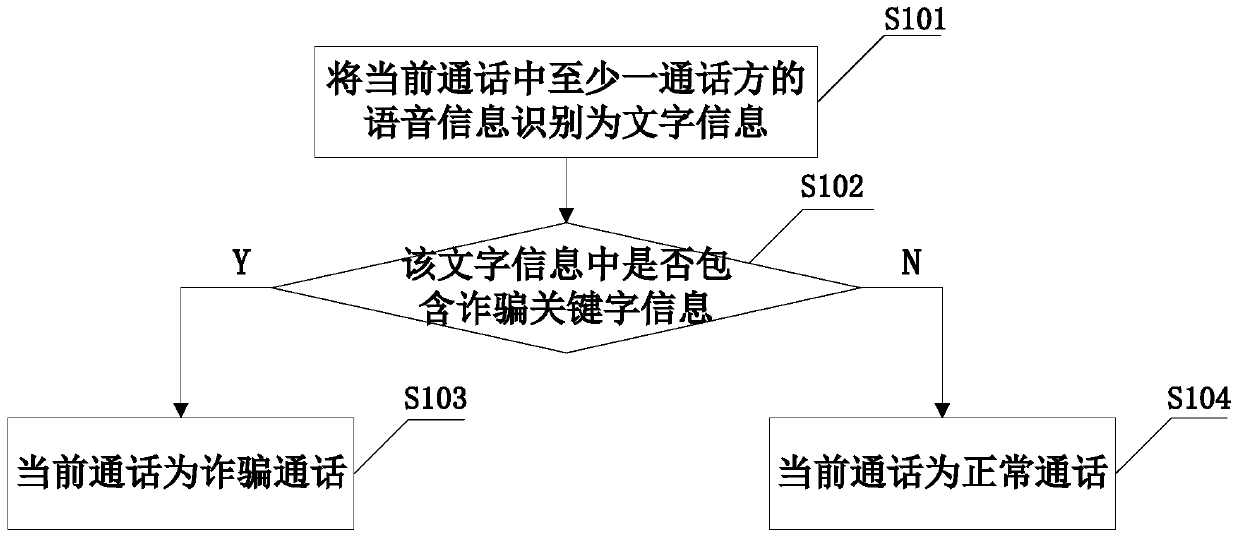
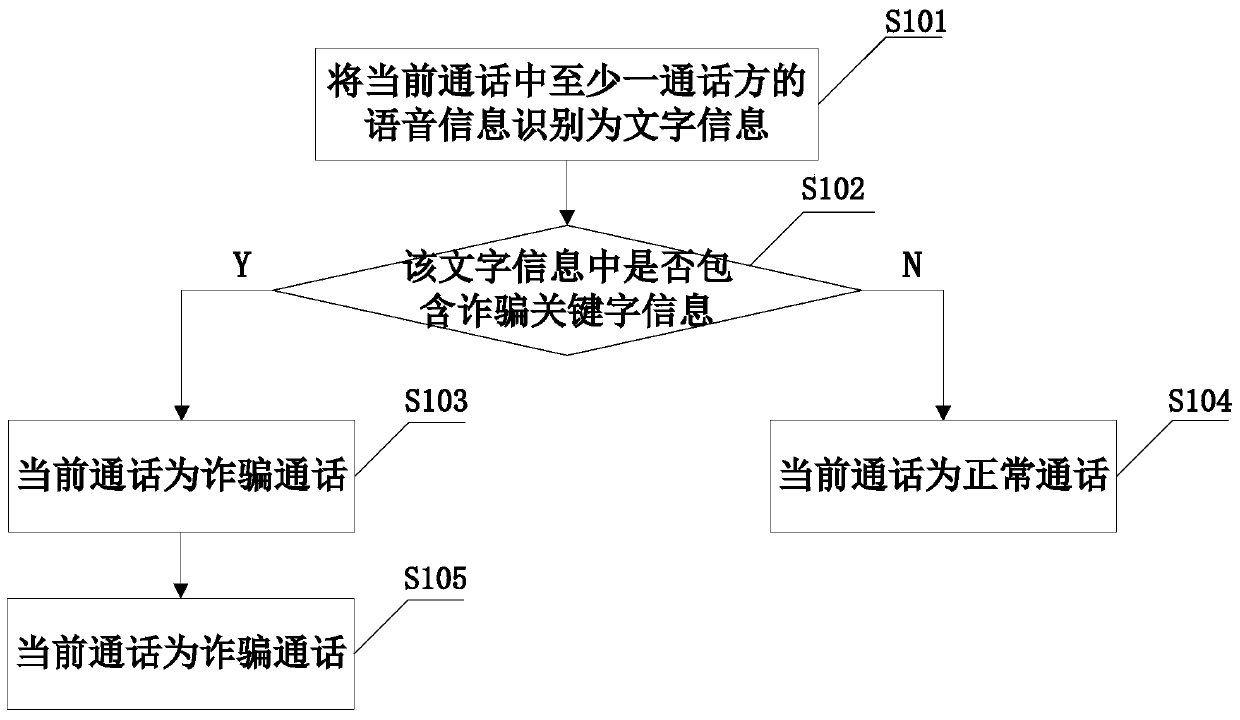
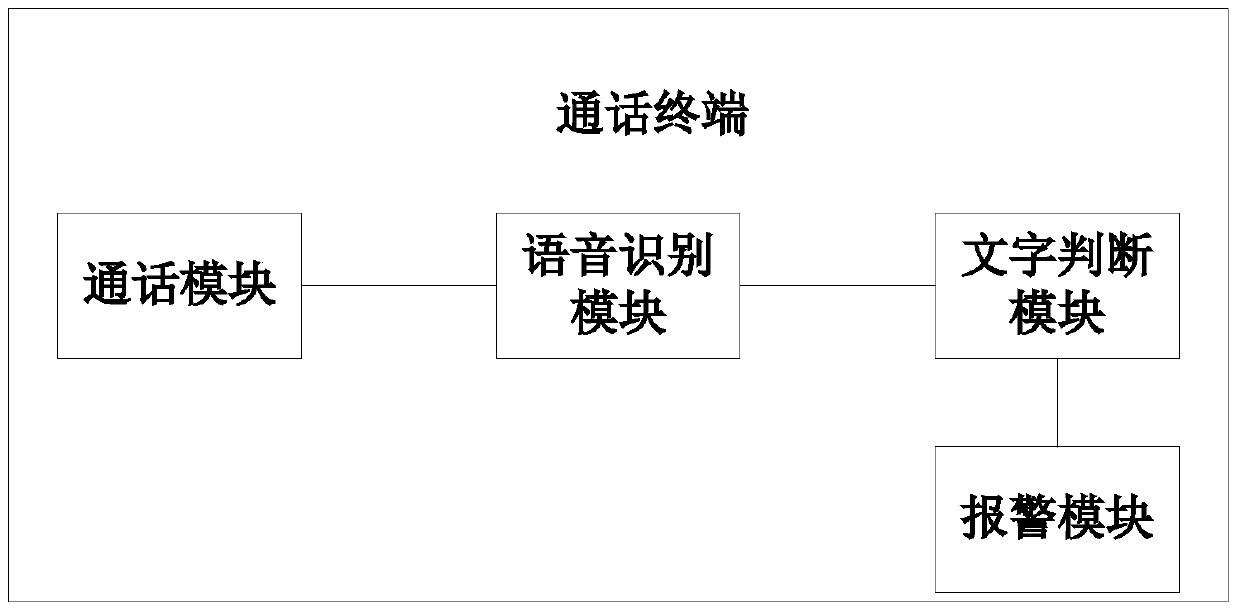
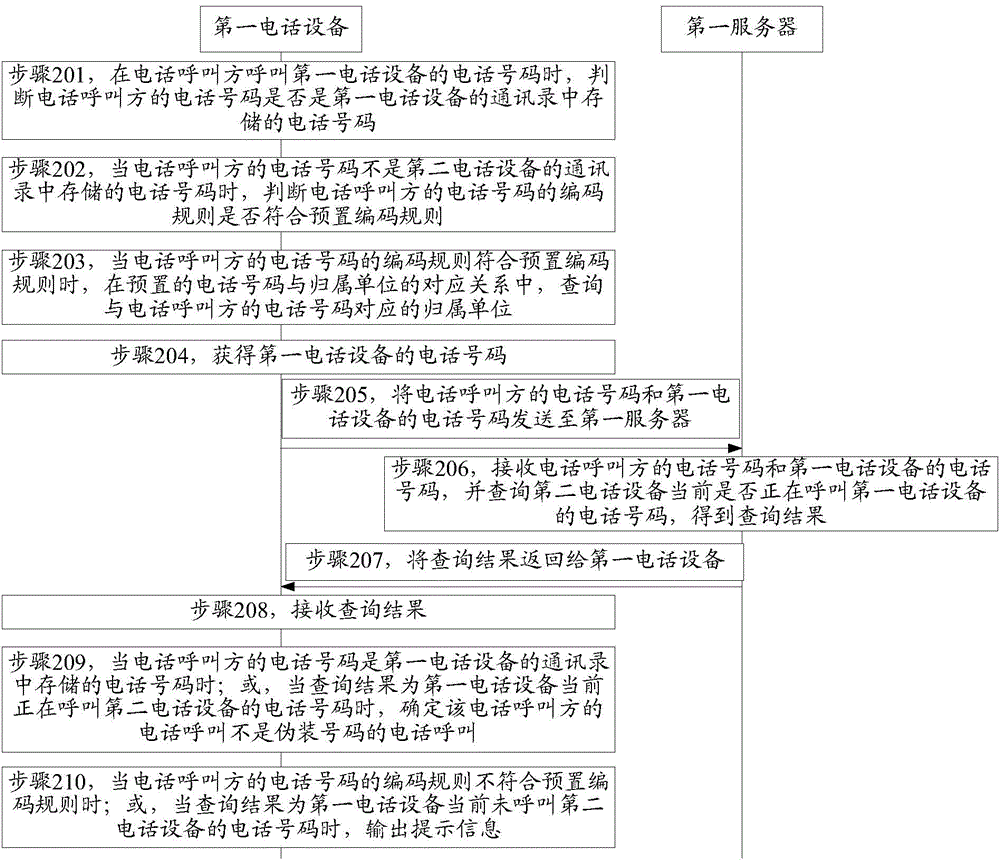
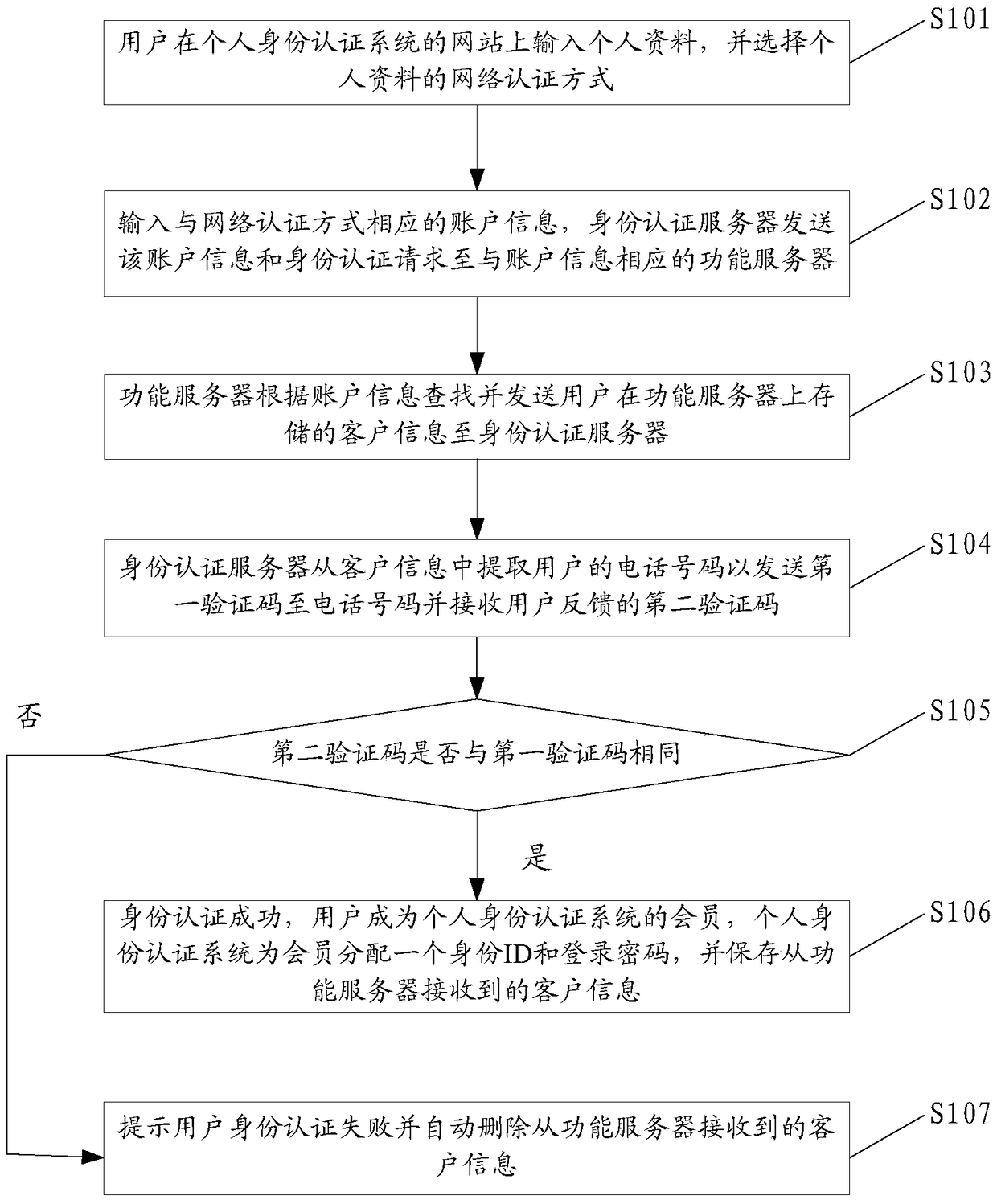
Fraud call identification method, fraud prevention method and call terminal
InactiveCN105100362AAvoid being scammedUnauthorised/fraudulent call preventionSpeech recognitionTelecommunicationsSpeech sound
Owner:ZTE CORP
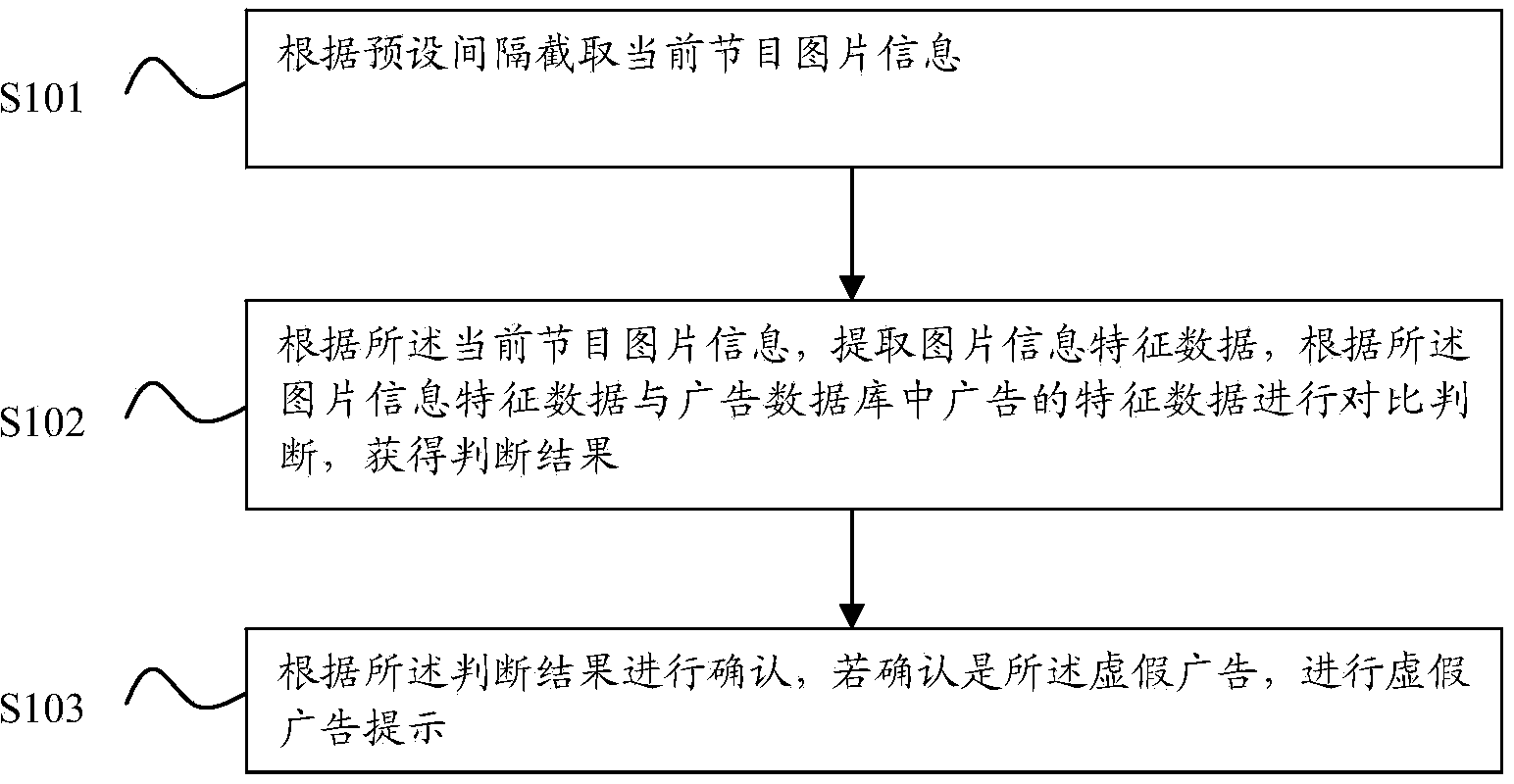
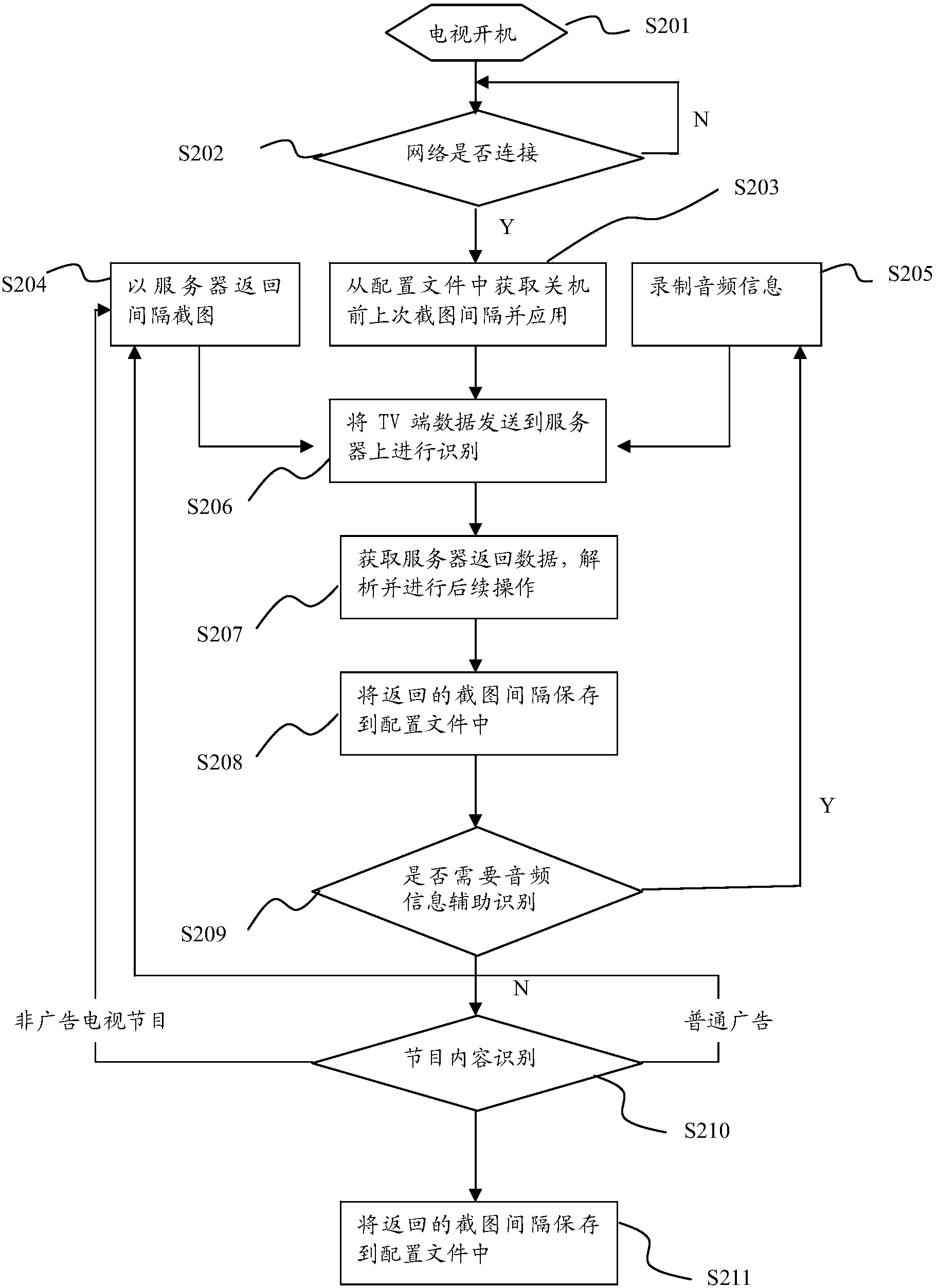
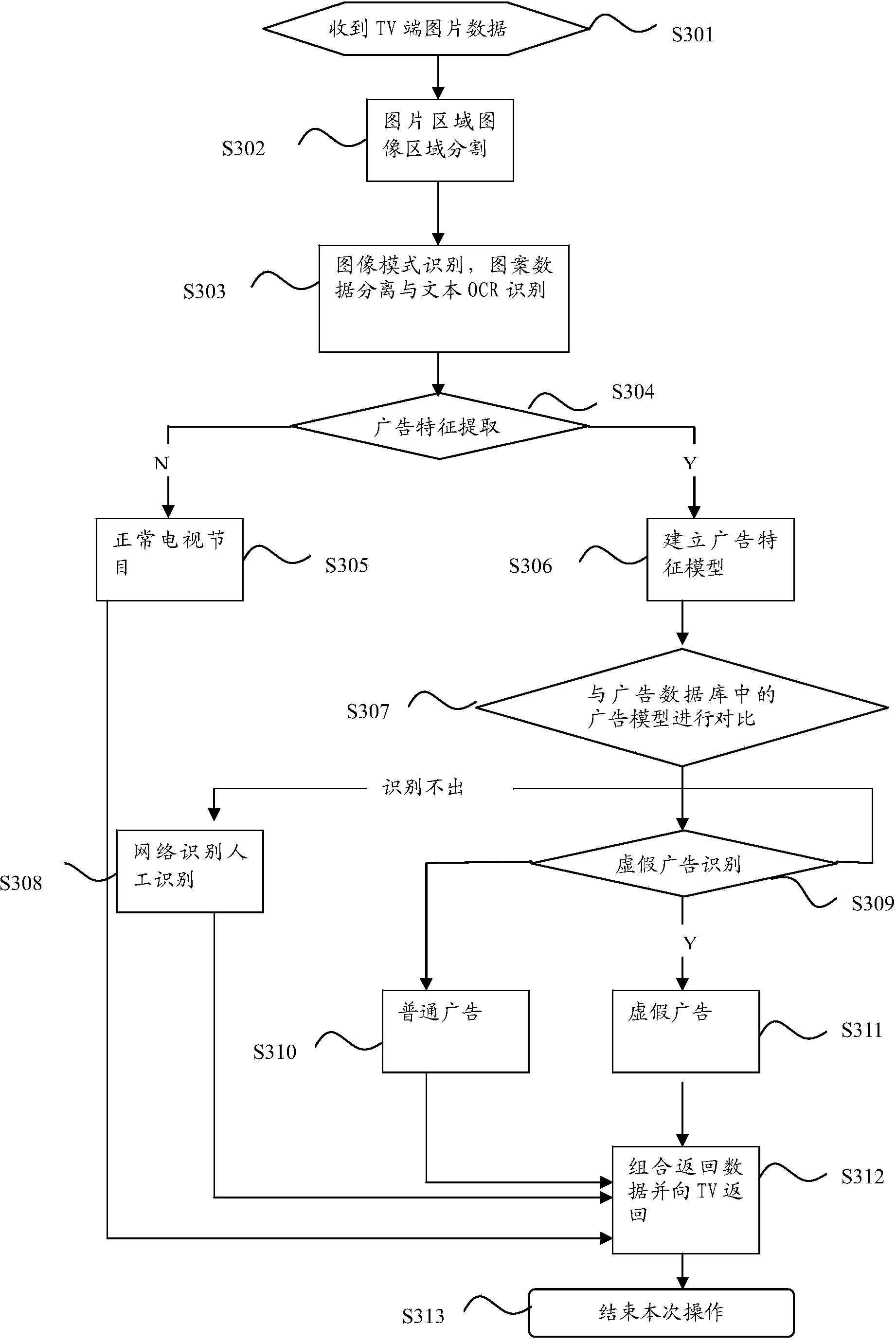
Television false advertisement prompting method and system
InactiveCN103458300AImprove experienceAvoid being scammedSelective content distributionMarketingCable televisionMultimedia
The invention provides a television false advertisement prompting method and system. The television false advertisement prompting method comprises the following steps that current program image information is captured at preset intervals; through capturing of the current program image information, image information characteristic data are extracted, and through comparison between characteristic data and advertisement characteristic data of an advertisement data base, false advertisement judgment is conducted; after a false advertisement is confirmed, a false advertisement prompt is given. By the adoption of the television false advertisement prompting method and system, a user can visually recognize the false advertisement and avoid being tricked, so that a television really brings happiness to people, and the experience degree of use of the television by the user is greatly improved.
Owner:TIANJIN SAMSUNG ELECTRONICS CO LTD +1
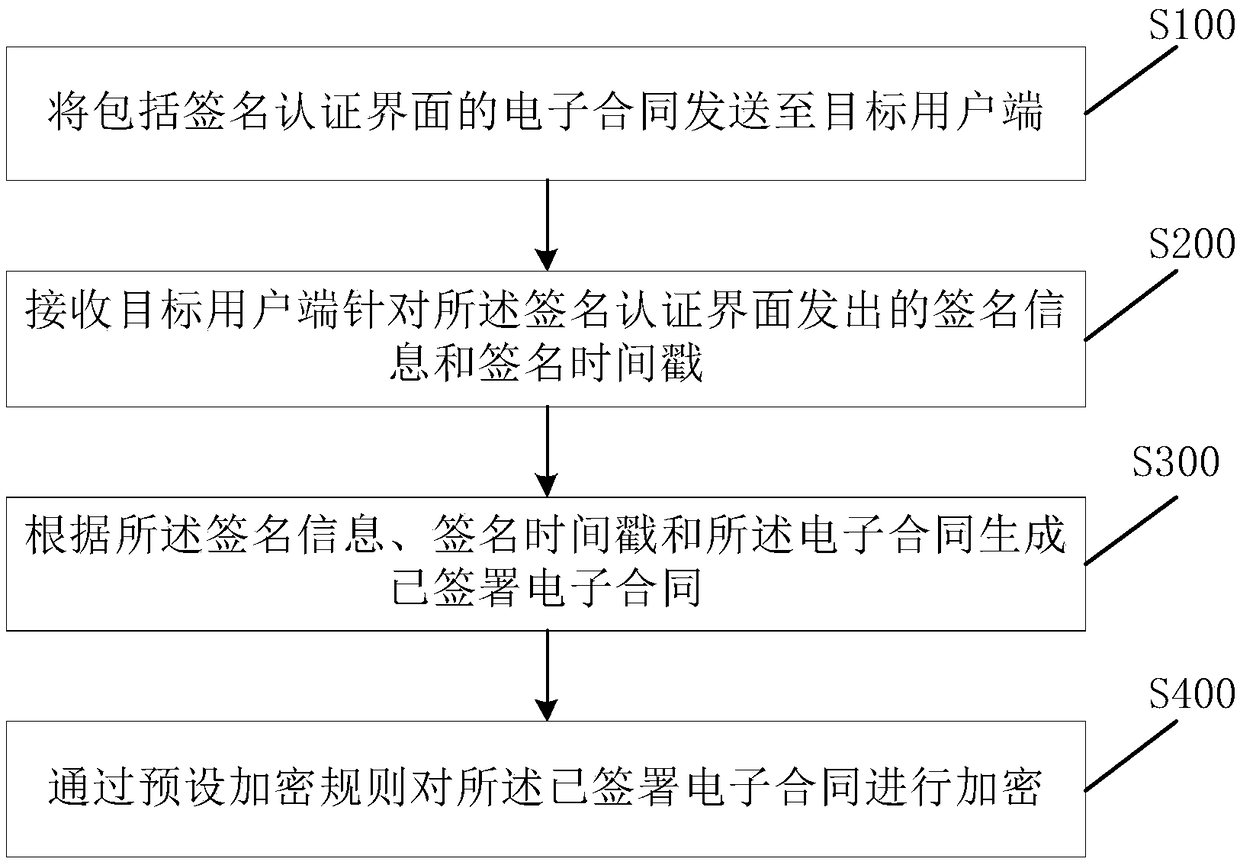
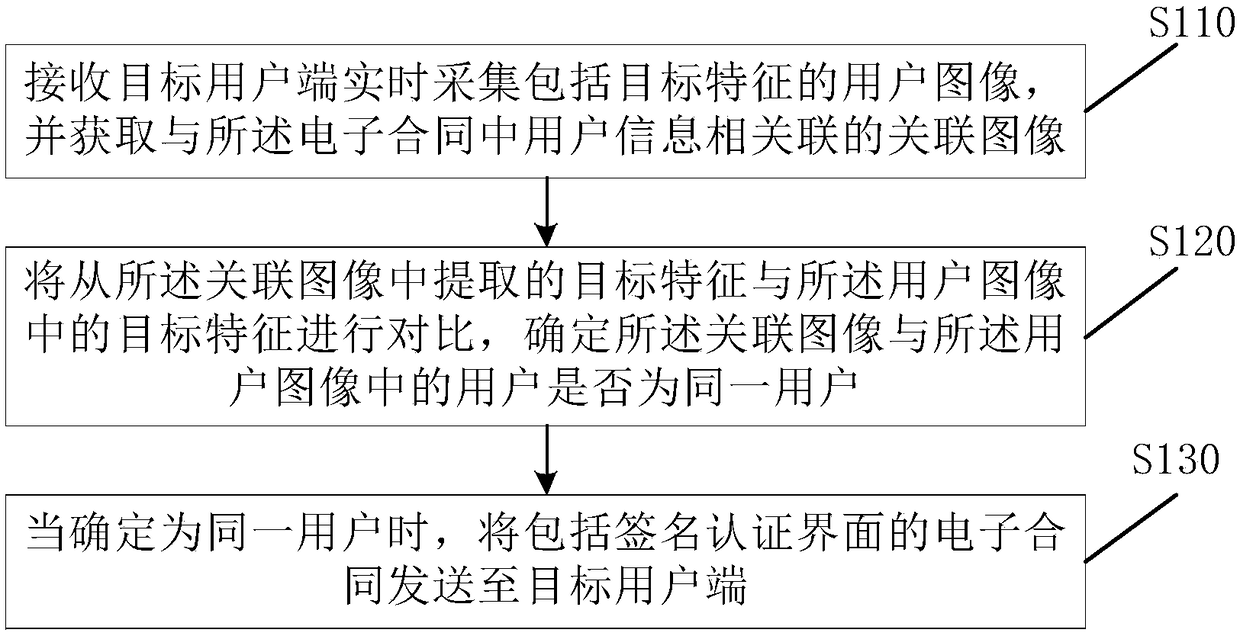
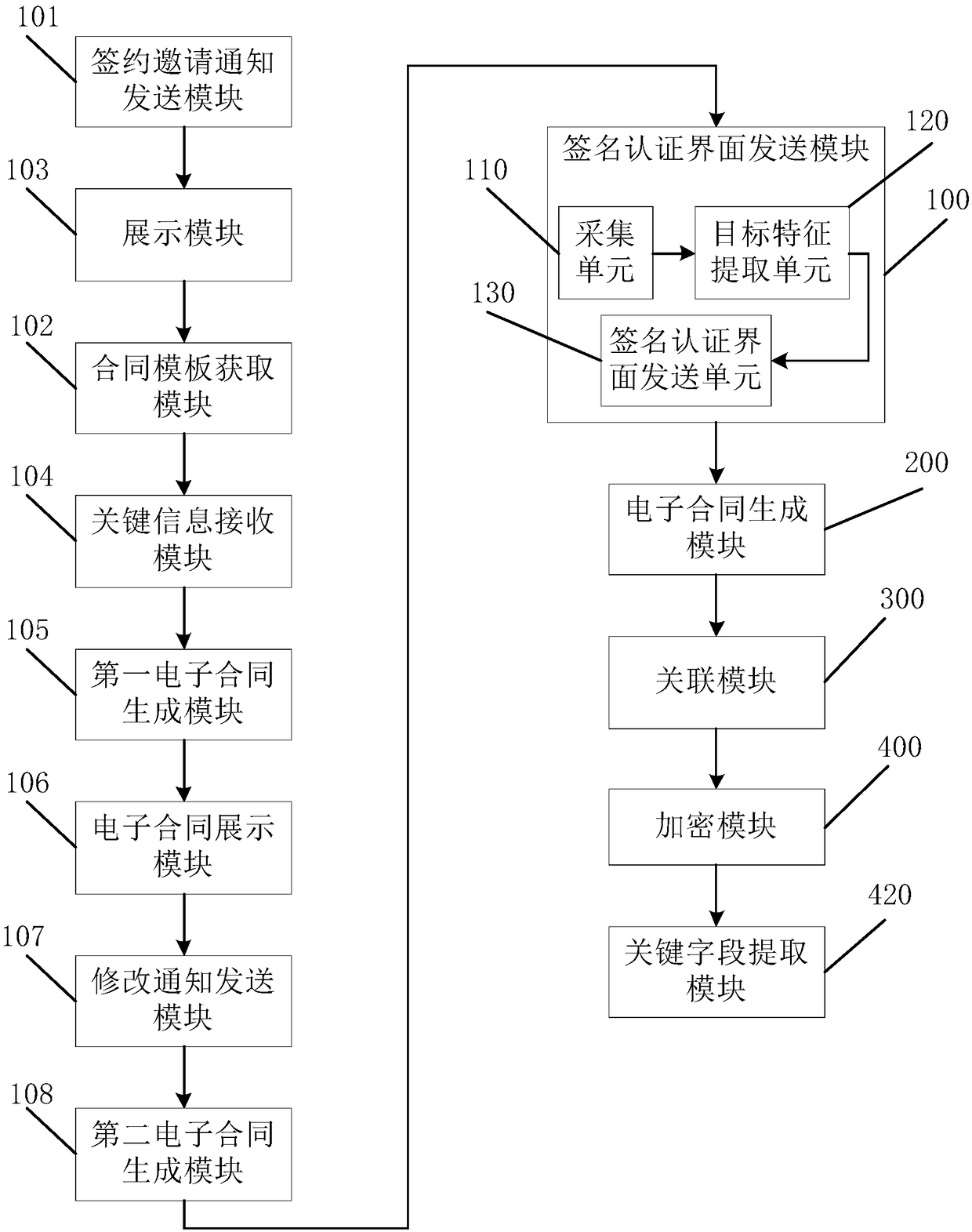
Electronic contract signing method, device and server
PendingCN109087056AGuaranteed tamper resistanceGuarantee the legal validity of online contractsUser identity/authority verificationOffice automationElectronic contractsEncryption
An electronic contract signing method provided in an embodiment of the present invention includes the steps of: sending the electronic contract including a signature authentication interface to a userin response to a user instruction; receiving a signature of a user on the signature authentication interface, and generating the signature into the electronic contract; acquiring a timestamp associated with the electronic contract and associating the timestamp with the electronic contract; an electronic contract including the signature and associated with the timestamp being encrypted by a presetencryption rule. The invention is applied to the field of house leasing. On the basis of electronically signing the contract, the invention ensures the tamperproof property of the electronic contractand the legal validity of on-line signing the contract through the time stamp and the encryption method.
Owner:PING AN TECH (SHENZHEN) CO LTD
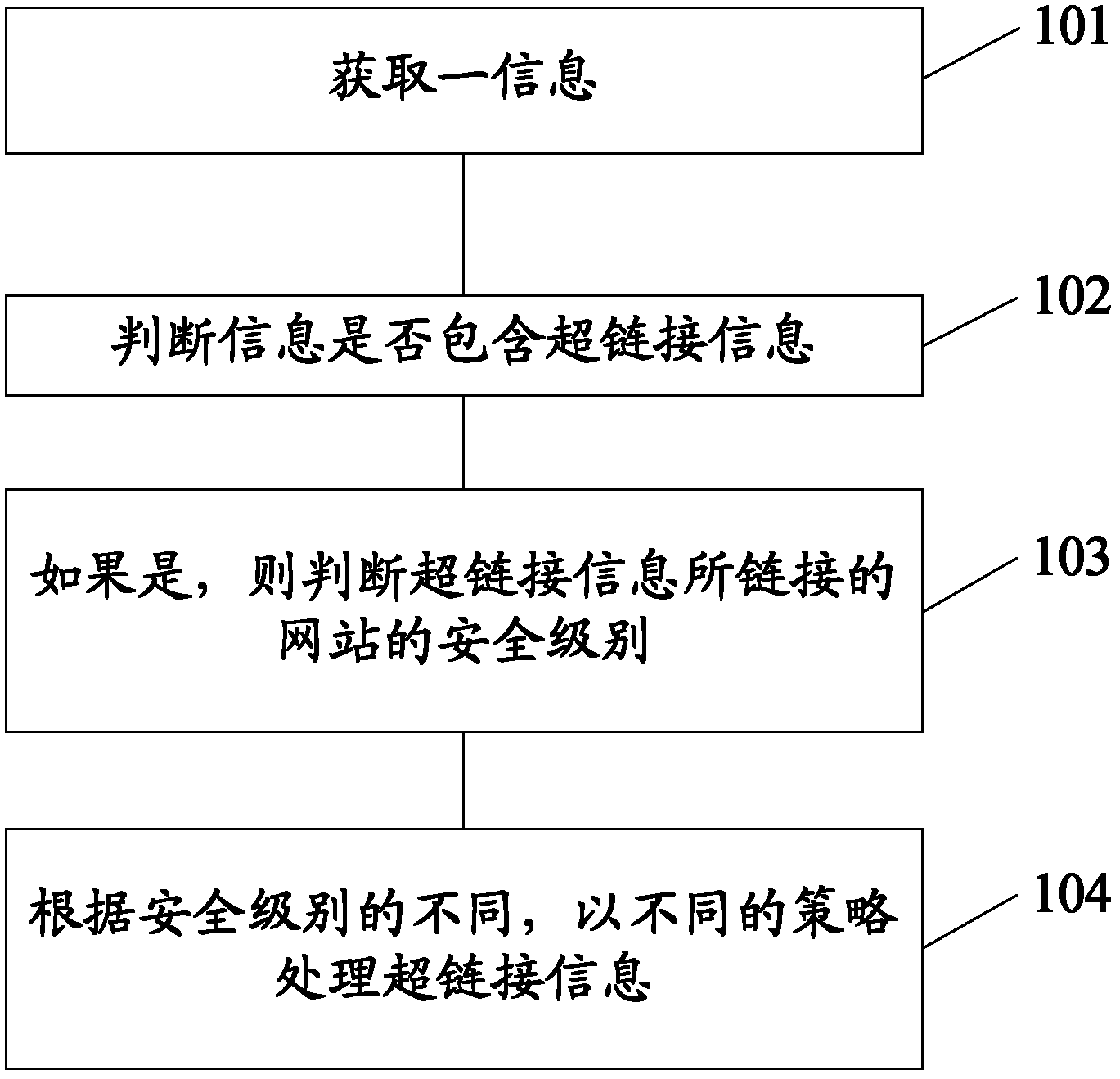
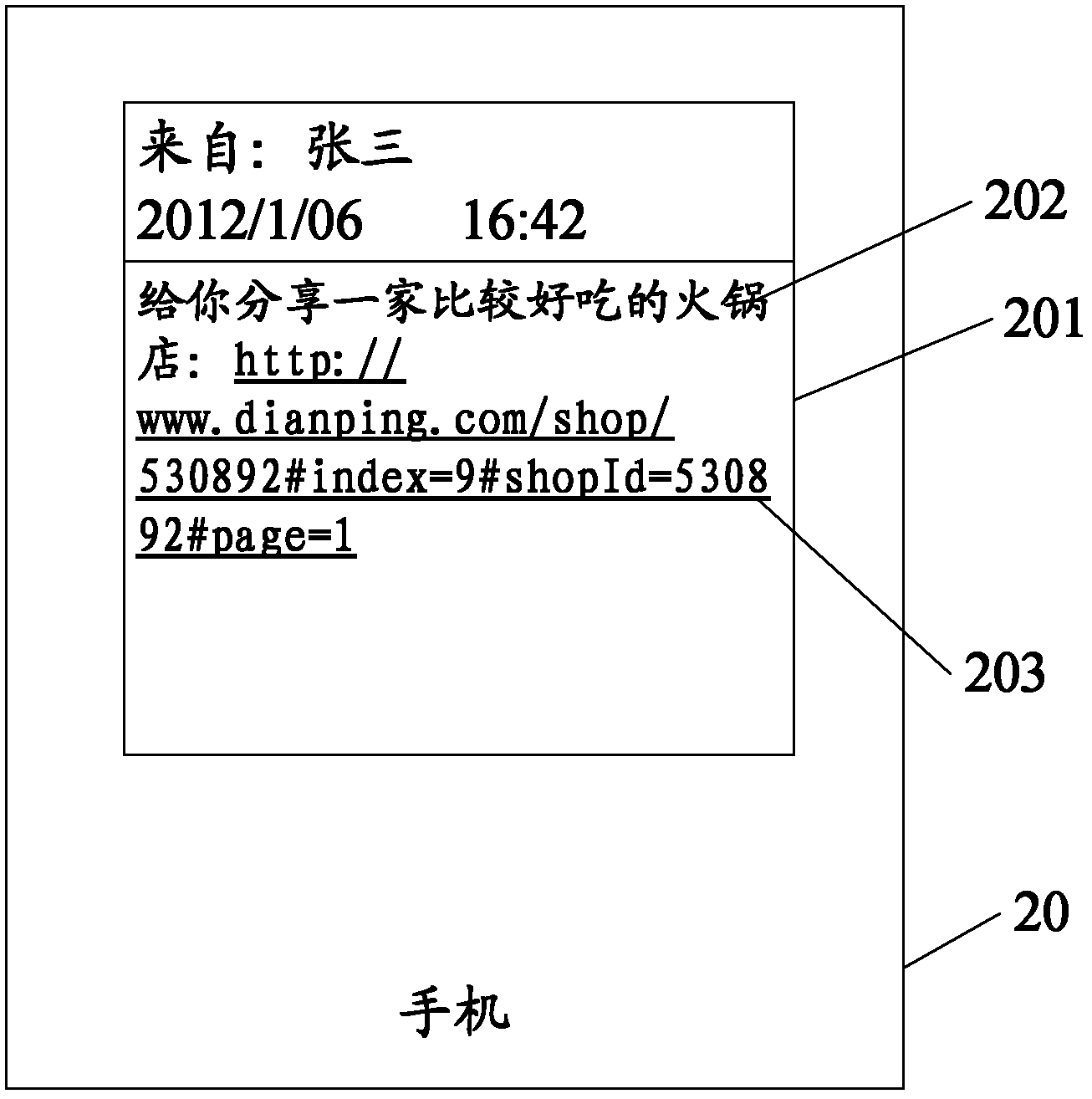
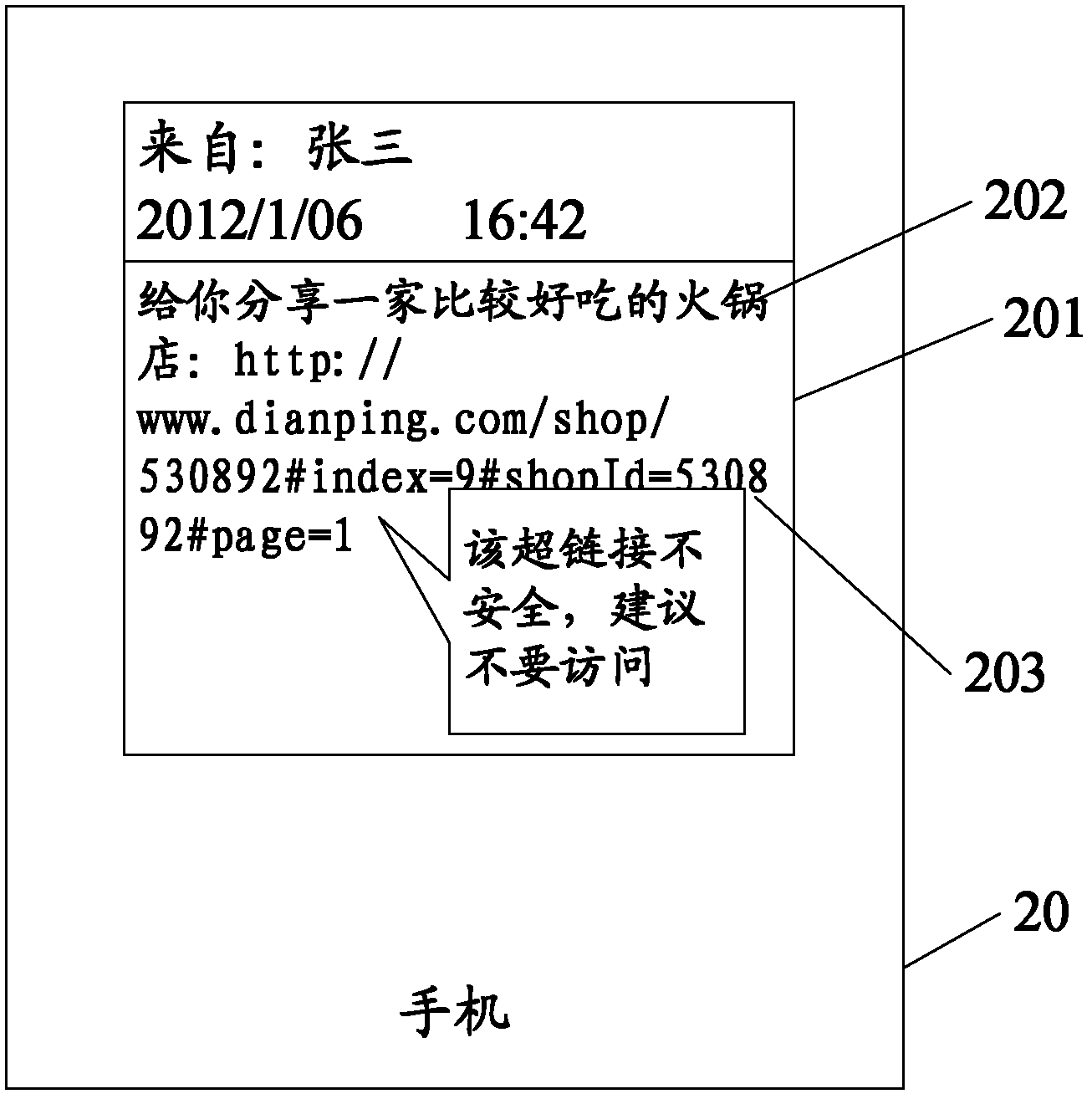
Information processing method and electronic terminal
InactiveCN103220641AEasy to useAvoid being scammedMessaging/mailboxes/announcementsSecurity arrangementWeb siteHyperlink
The invention discloses an information processing method and an electronic terminal. The information processing method comprises the steps of obtaining information, judging whether the information contains hyperlink information, judging the security level of a website linked with the hyperlink information if the information comprises the hyperlink information, and processing the hyperlink information with different strategies according to different security levels.
Owner:LENOVO (BEIJING) LTD
Information processing method, information processing device and terminal
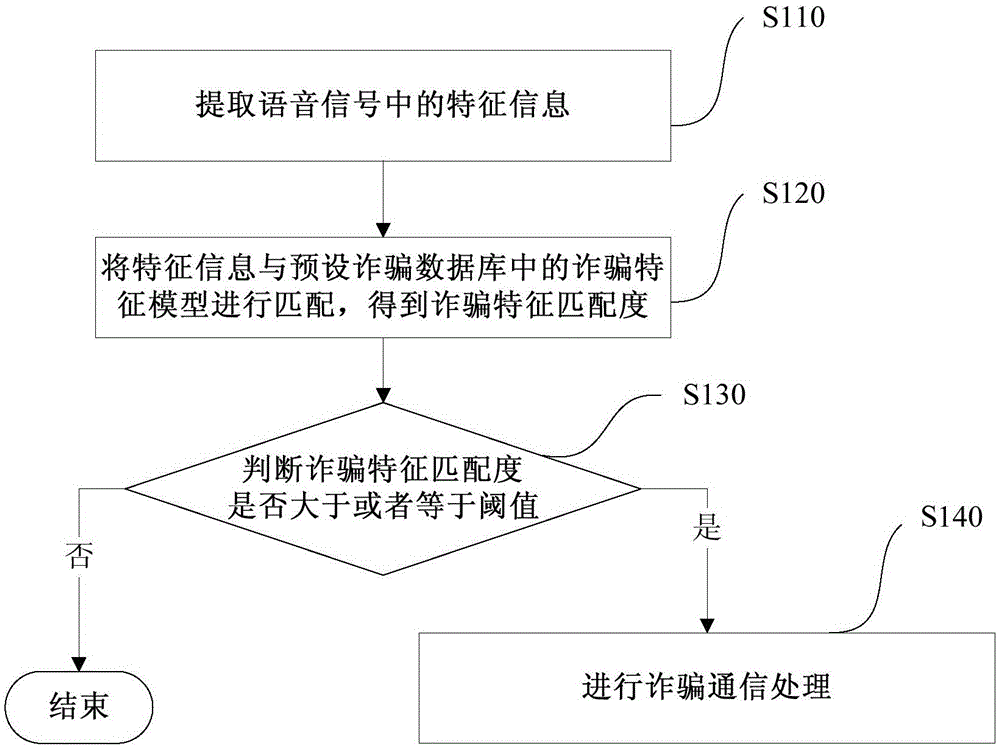
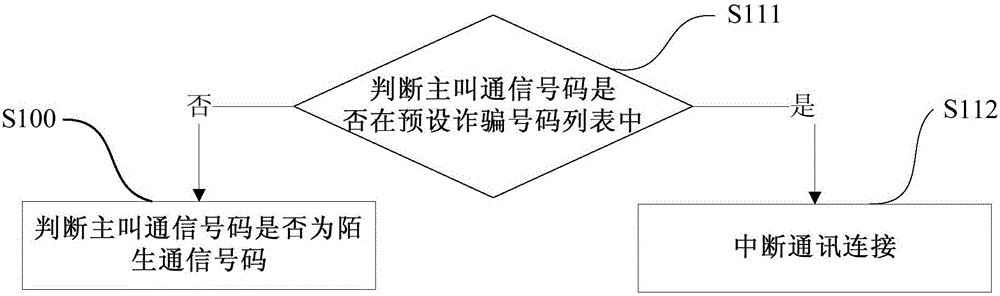
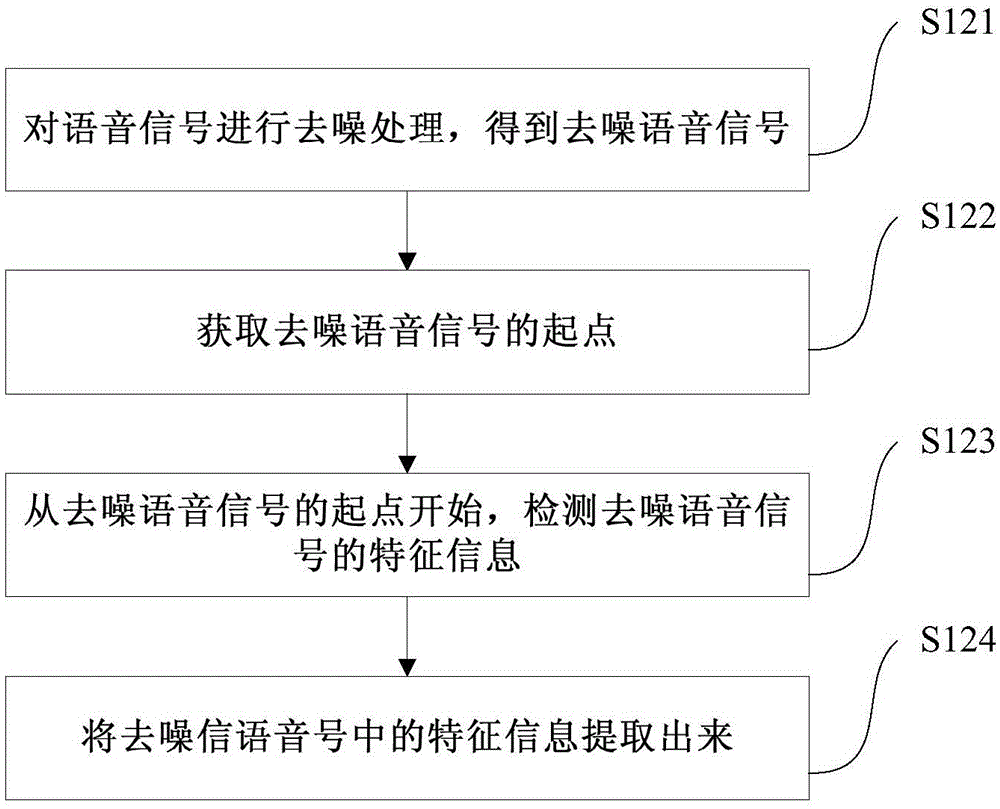
InactiveCN105100363ATimely processingAvoid being scammedUnauthorised/fraudulent call preventionInformation processingComputer terminal
The invention discloses an information processing method, an information processing device and a terminal. The information processing method comprises the steps of: extracting characteristic information in a voice signal; matching the characteristic information with a fraud characteristic model in a preset fraud database to obtain a fraud characteristic matching degree; judging if the fraud matching degree is greater than or equal to a threshold; when the fraud matching degree is greater than or equal to a threshold, carrying out a fraud communication treatment. By monitoring communication content of the terminal in real time as well as detecting and judging the communication content, the fraud communication treatment can be carried out in time to prevent a user from being tricked when the communication is regarded as fraud communication.
Owner:XIAOMI INC
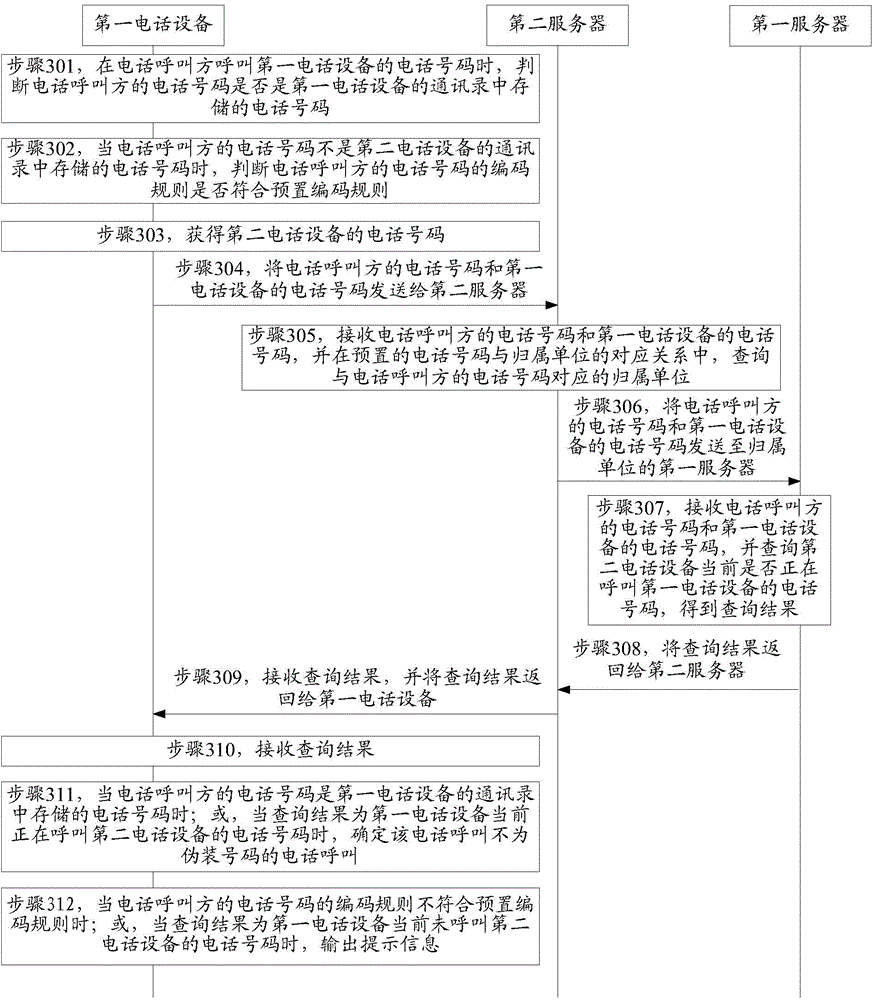
Telephone call identification method and device
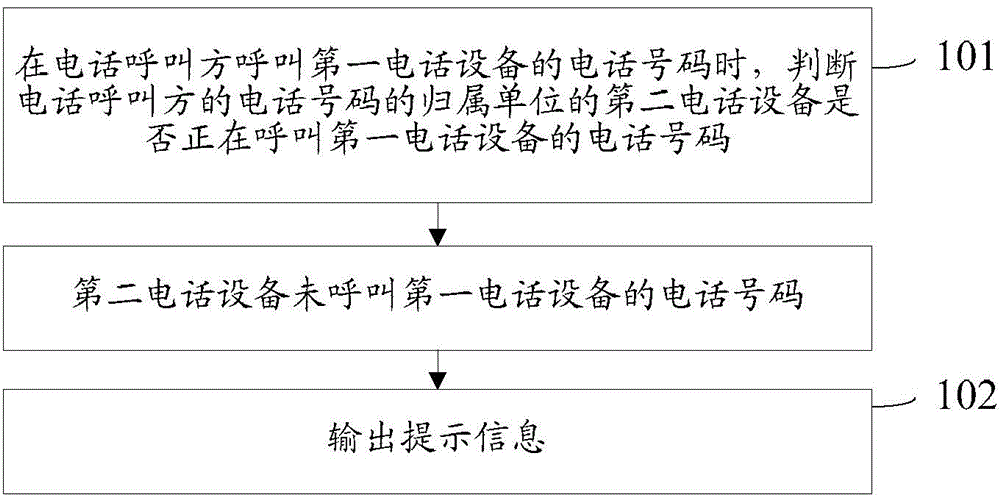
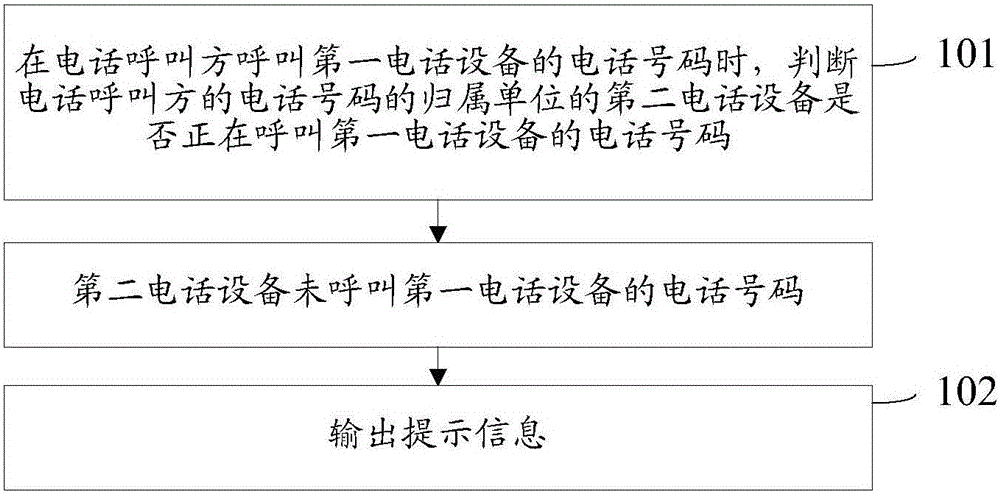
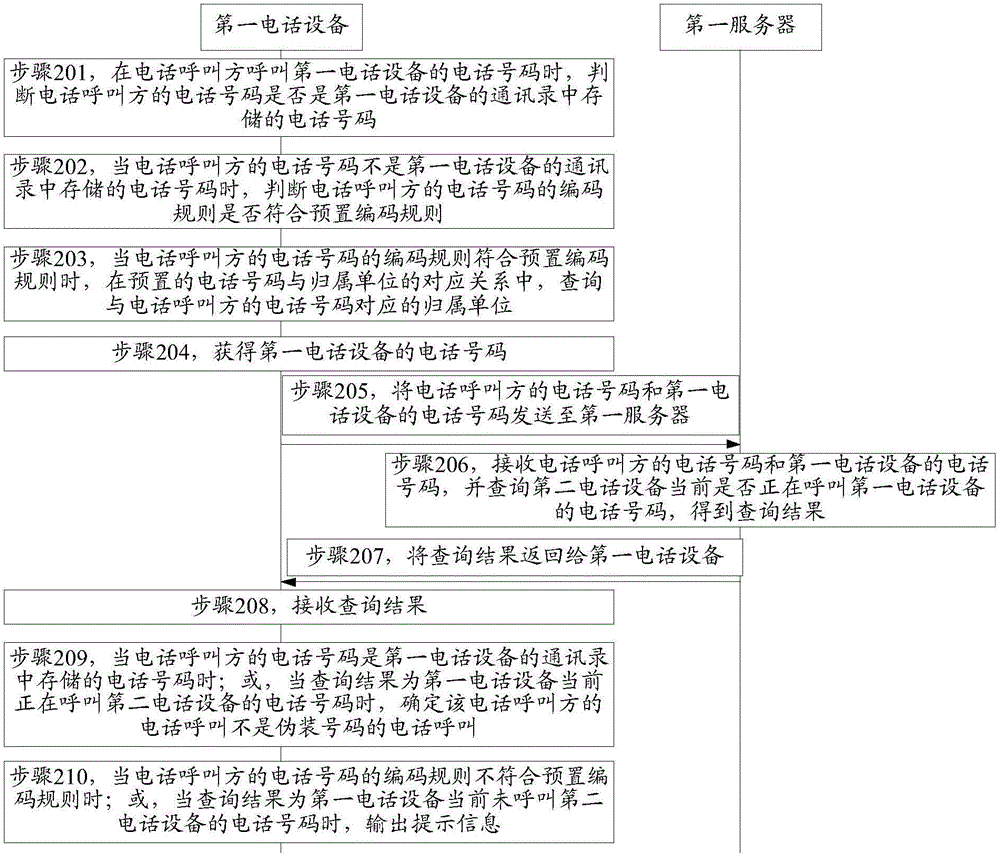
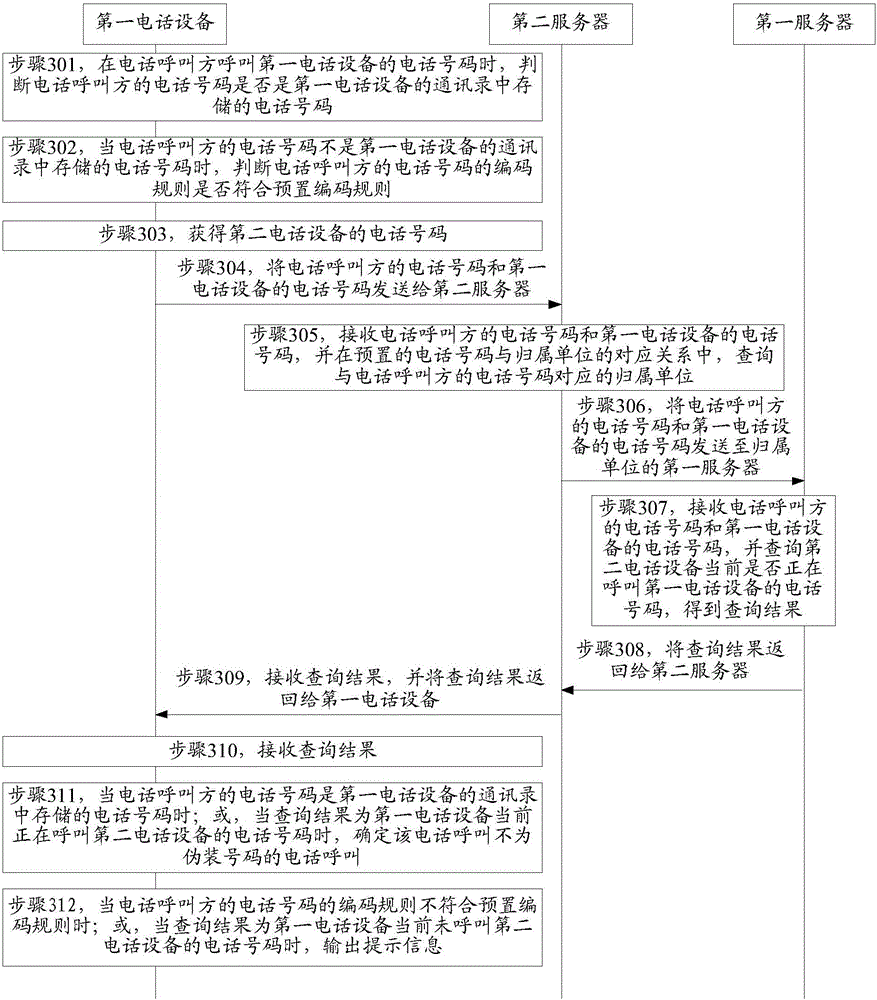
ActiveCN104159230AMake sure the results are real and validAvoid being scammedInterconnection arrangementsCalling susbscriber number recording/indicationEngineeringTelephony
The invention provides a telephone call identification method and device, and belongs to the field of communication. The method comprises the following steps: judging whether second telephone equipment belonging to the telephone number of a telephone calling party calls the telephone number of first telephone equipment when the telephone calling party calls the telephone number of the first telephone equipment, wherein the telephone number of the second telephone equipment is the telephone number of the telephone calling party; outputting prompting information when the second telephone equipment does not calls the telephone number of the first telephone equipment, wherein the prompting information is used for indicating that the telephone call of the telephone calling party is that of a fake number. The device comprises a first judge module and an output module. The method and device can be used for rightly identifying a telephone call of the fake number; moreover, the identification method is suitable for identifying all telephone numbers, and can prompt a called party to prevent the called party from being tricked.
Owner:XIAOMI INC
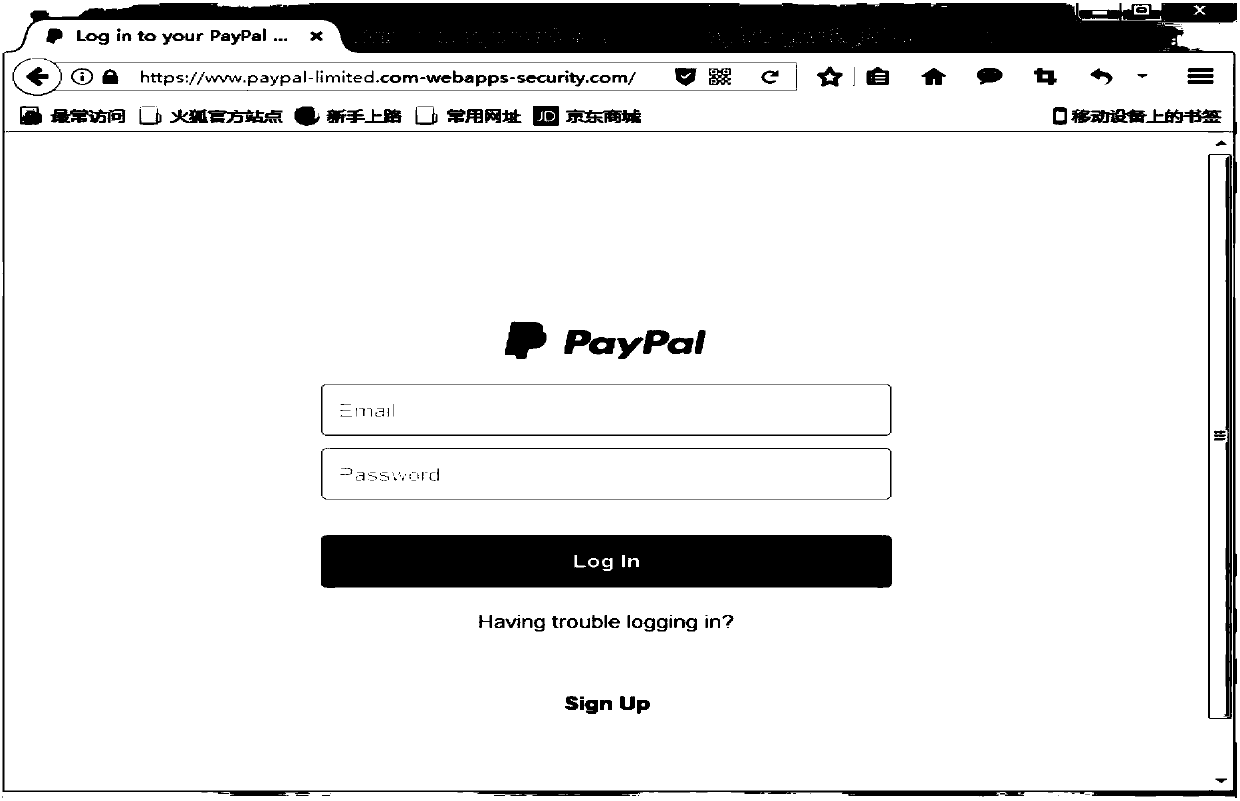
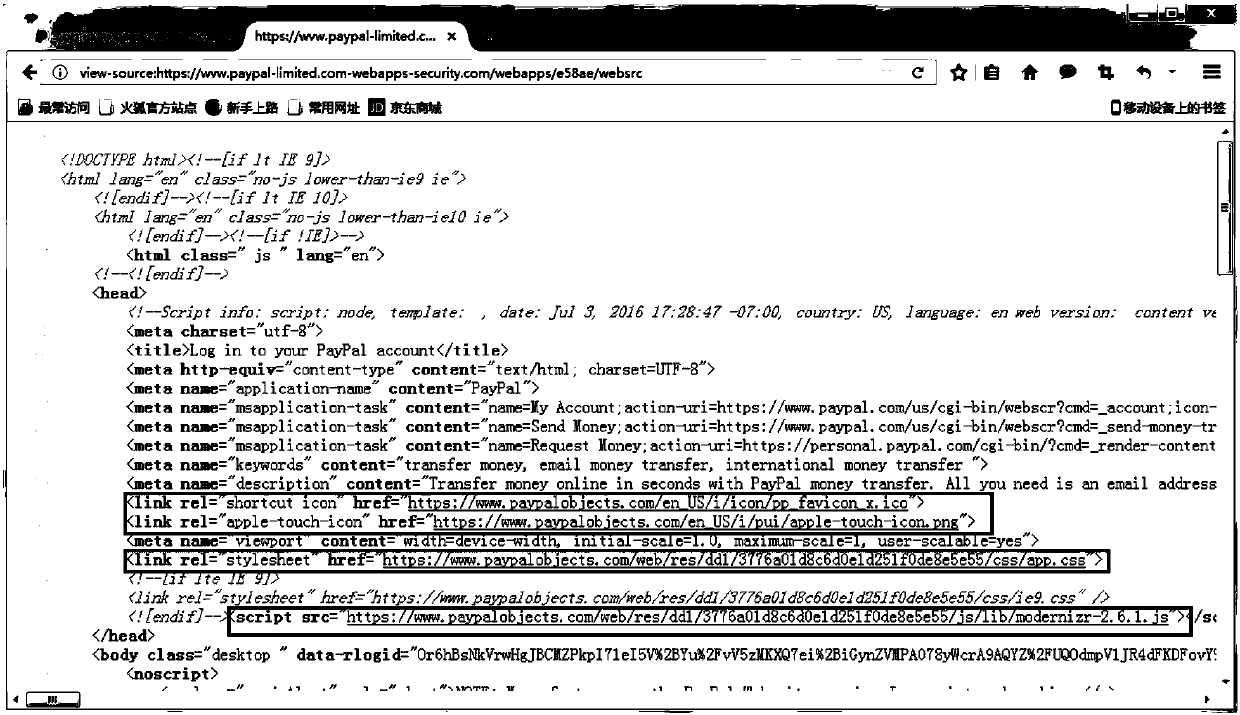
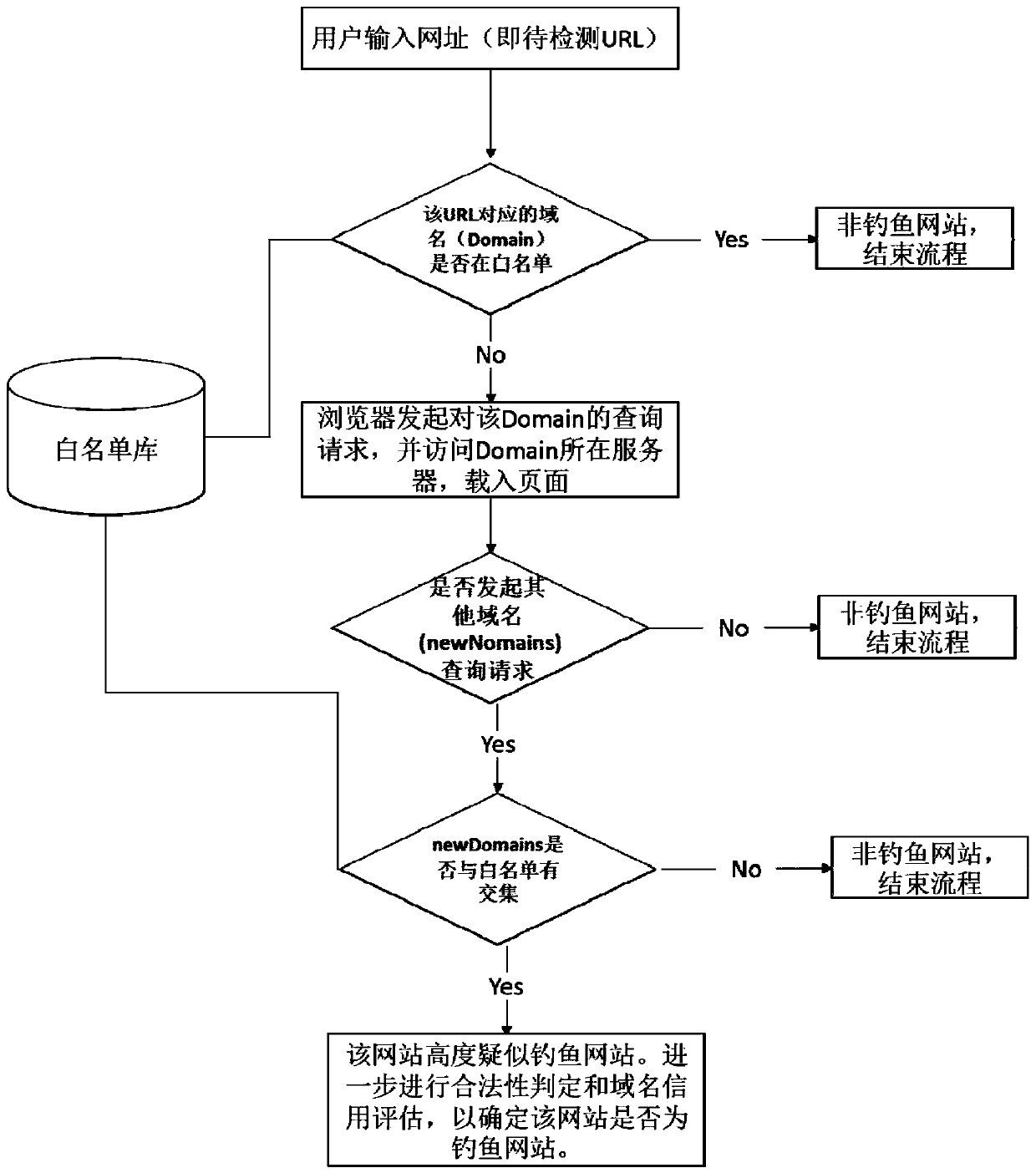
Phishing website recognition method and device
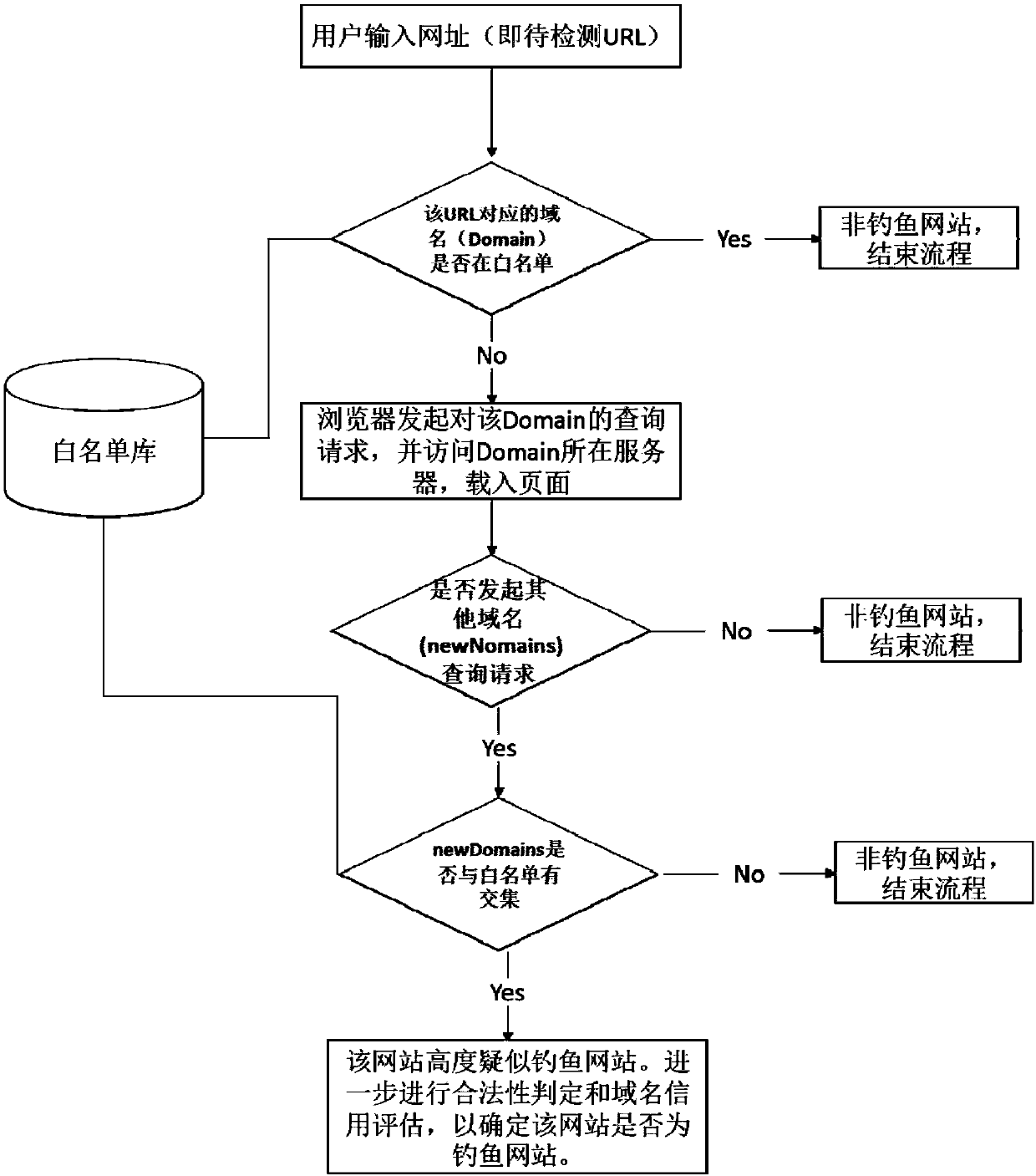
ActiveCN107800686ARealize online real-time identificationAvoid being scammedTransmissionDomain namePhishing
The invention relates to a phishing website recognition method and device. The method comprises the steps that whether or not resources of other websites are embedded into a to-be-detected website isdetected; and if the resources of the other websites are not embedded into the to-be-detected website, it is judged that the to-be-detected website is a non-phishing website; if the resources of the other websites are embedded into the to-be-detected website, whether or not domain names of the other websites intersect with a white list is judged; if the domain names of the other websites do not intersect with the white list, it is judged that the to-be-detected website is the non-phishing website; if the domain names of the other websites intersect with the white list, it is judged that the to-be-detected website is a highly-suspected phishing website; and legality judgment and domain name credit assessment are conducted on the highly-suspected phishing website to determine whether or notthe to-be-detected website is a phishing website. According to the method and device, the defect that in a black list technology, newly-presented phishing websites cannot be filtered can be overcome,the phishing websites in which elements and resources of brand websites are embedded can be recognized efficiently, and the phishing filtering performance can be improved.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Chinese surname recognition method and device, as well as server
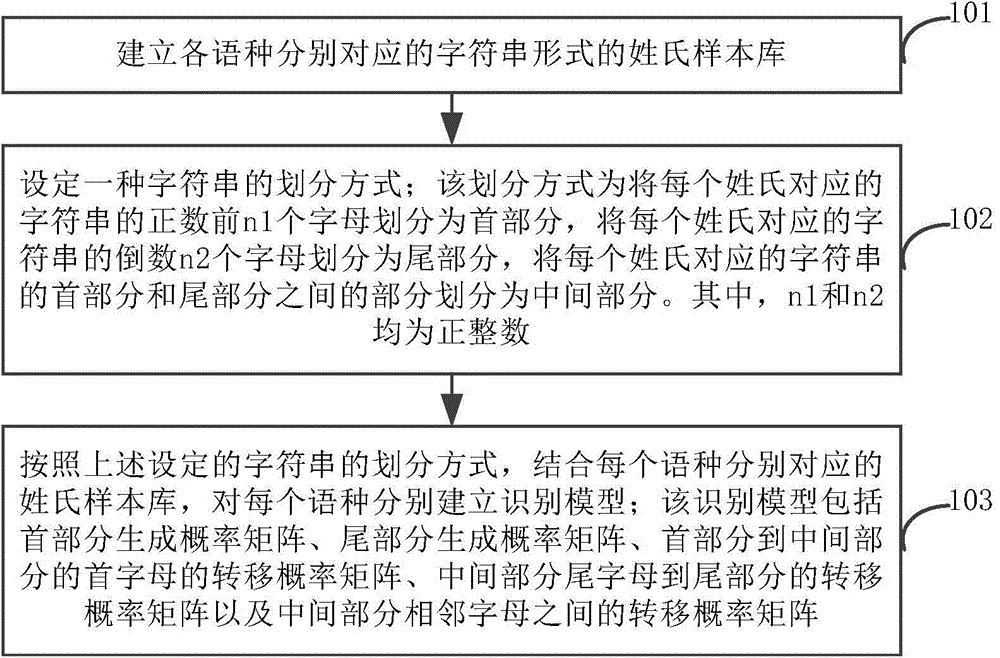
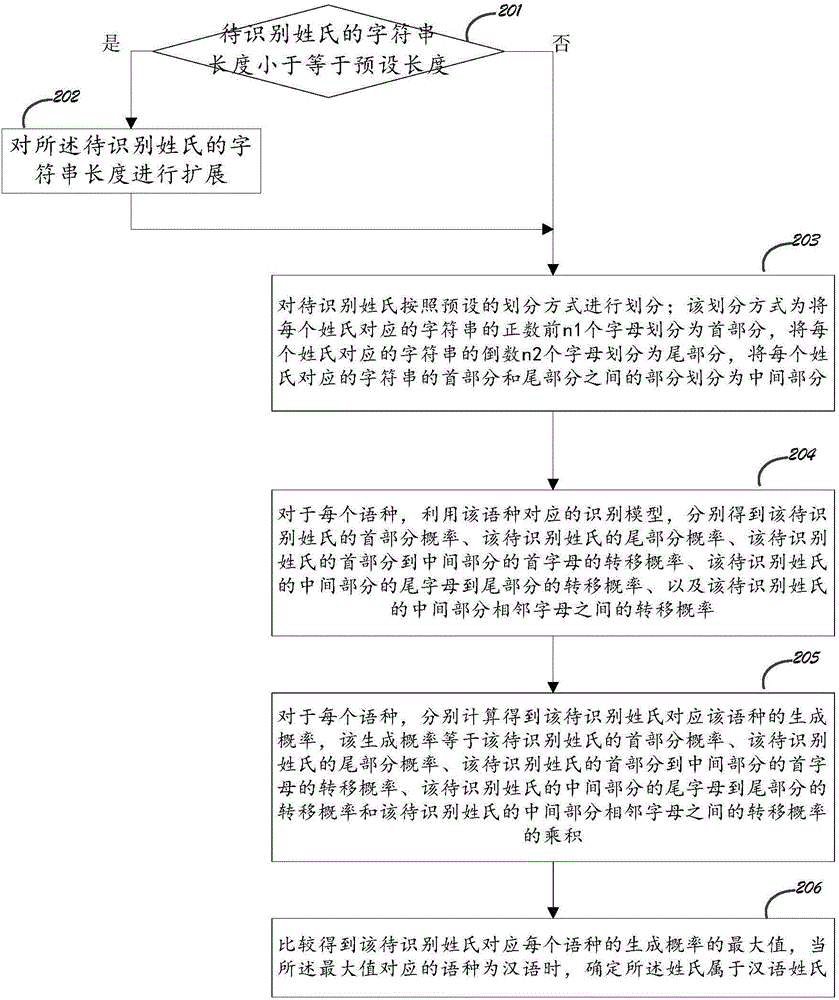
ActiveCN105988989AImprove securityImprove reliabilityCommerceSpecial data processing applicationsAlgorithmData mining
The invention discloses a Chinese surname recognition method and device, as well as a server. The method comprises the steps of performing language recognition on an extended surname to be recognized when the length of a character string of the surname to be recognized is less than or equal to a preset length; or otherwise, directly performing language recognition, wherein the language recognition comprises the steps of dividing the surname according to a preset mode; obtaining a front part probability, a tail part probability, a transition probability of a first letter from the front part to the middle part, a transition probability of a last letter of the middle part to the tail part, and a transition probability of neighboring letters of the middle part of the surname corresponding to all languages according to a recognition model corresponding to each language; and obtaining generation possibilities of the surname corresponding to the all languages by calculating the possibilities, comparing to obtain the maximum value, and determining that the surname belongs to Chinese surnames if the language corresponding to the maximum value is Chinese. Through adoption of the embodiment of the invention, whether the surname represented by the character string provided by a user belongs to Chinese or not can be recognized, so that a technical problem in the prior art is solved.
Owner:ADVANCED NEW TECH CO LTD
Fraud call record analysis system
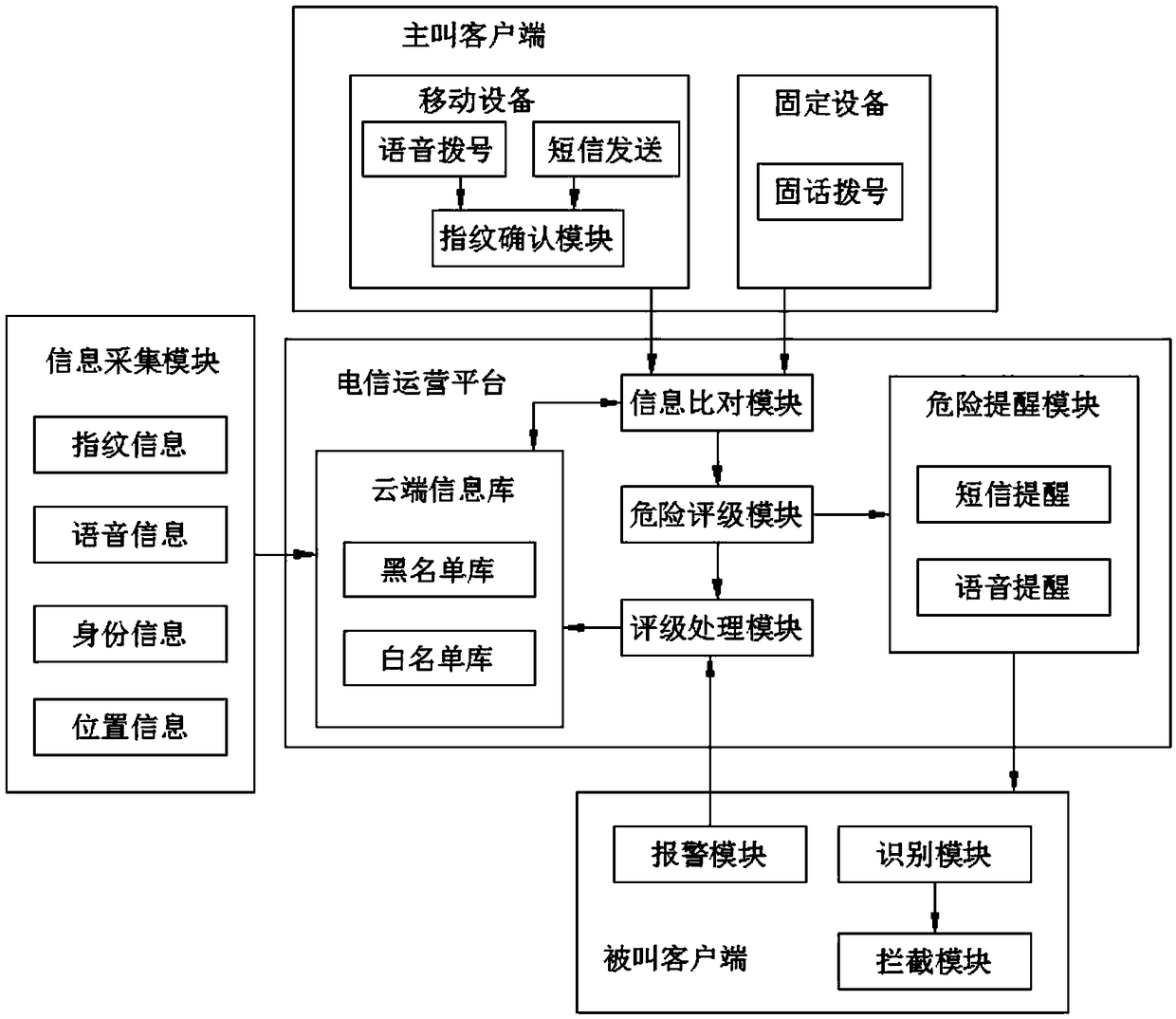
InactiveCN108616890AAvoid being scammedReduce fraud casesSpecial service for subscribersSupervisory/monitoring/testing arrangementsInformation repositoryComputer module
The invention discloses a fraud call record analysis system, which comprises a telecom operation platform, an information collection module, a calling client and a called client, wherein the telecom operation platform comprises a cloud information database, an information comparison module, a risk rating module, a rating processing module and a risk warning module; the output end of the information comparison module is connected with the input end of the risk rating module; the output end of the risk rating module is connected with the input ends of the rating processing module and the risk warning module; the output ends of the rating processing module and the information collection module are connected with the input end of the cloud information database; the cloud information database and the information comparison module are in two-way communication connection; and the output end of the calling client is wirelessly connected with the information comparison module. Comparison analysis and risk rating can be carried out on the information of the calling client, abnormal calls are interrupted, the user at the called client is warned, and happening of fraud cases is reduced.
Owner:中山易美信息技术有限公司
Antiforge method for commodities
InactiveCN1342950AReduce manufacturing costAnti-counterfeiting is reliableCoding/ciphering apparatusVerifying markings correctnessTelecommunicationsCipher
An antiforge method for commodities is disclosed. When a commodity is made up, a unique cipher is provided to it. Said cipher along with the name, weight, data, etc of the commodity is inputted to a networked inquiry system. If the commodity is bought by a buyer, the buyer can open the cipher to inquire if the commodity is true.
Owner:胡小平
Remote guard method and apparatus, terminal and storage medium
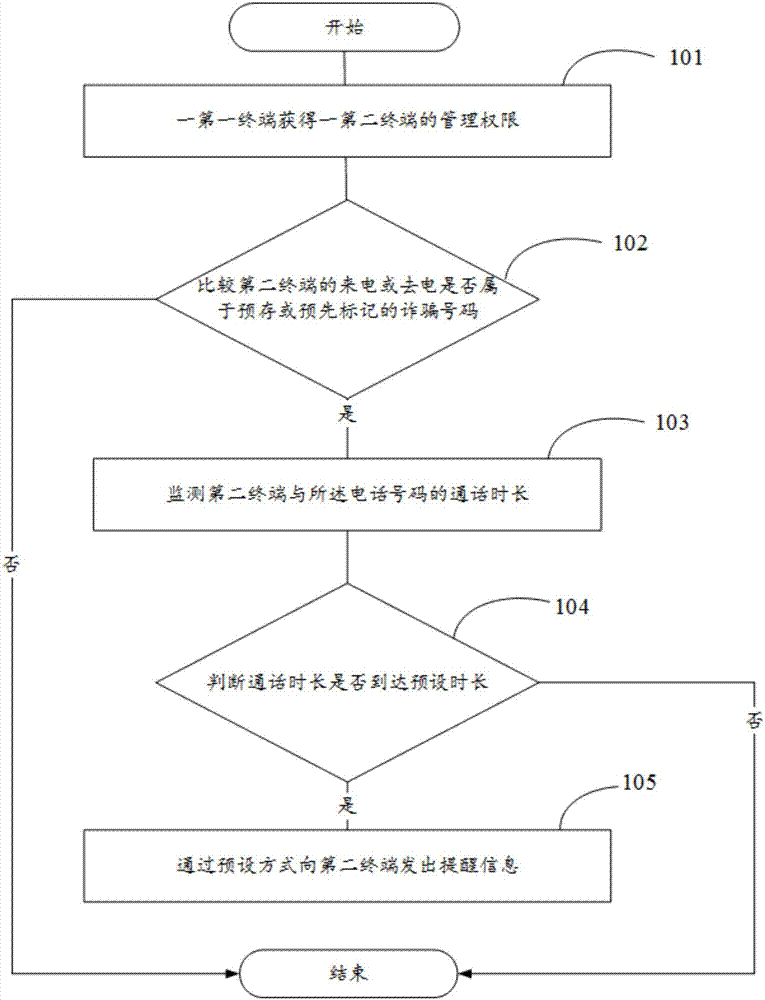
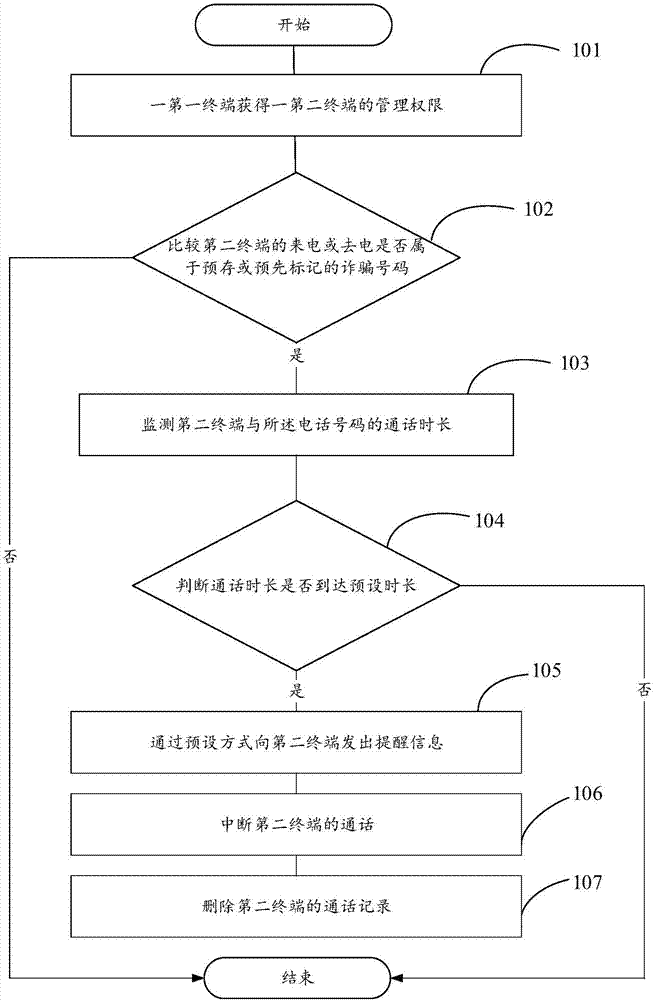
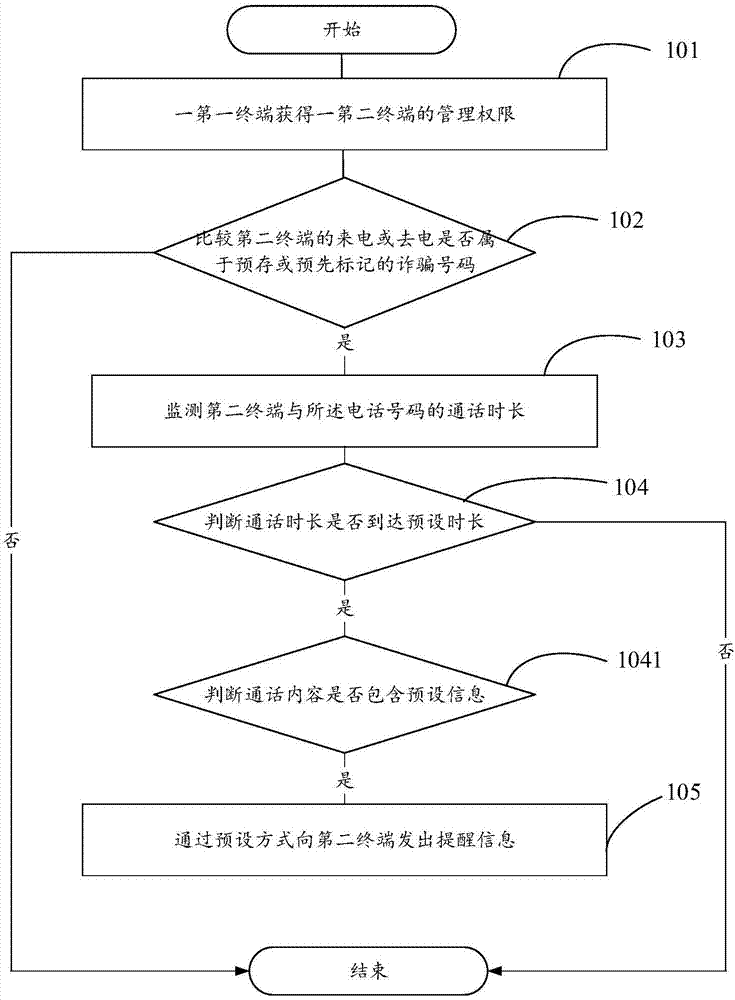
InactiveCN107580121AAvoid being scammedReduce the chance of being scammedTelemetry/telecontrol selection arrangementsUnauthorised/fraudulent call preventionTelecommunicationsComputer science
The invention provides a remote guard method and apparatus, a terminal and a storage medium. The remote guard method is applied to a first terminal and a second terminal, which are associated with each other, and the method comprises the following steps: obtaining the management authority of the second terminal by the first terminal; when a telephone number of an incoming call or an outgoing callof the second terminal belongs to a pre-stored or pre-marked fraud number, monitoring the call time length of the second terminal with the telephone number; and if the call time length of the second terminal with the telephone number reaches a preset time length, sending reminding information to the second terminal in a preset manner. By adoption of the method provided by the invention, the firstterminal can monitor and control the call of the second terminal so as to reduce the probability that the users are fucked.
Owner:MEIZU TECH CO LTD
Early warning method and system for identifying click farming shop based on e-commerce operation data
InactiveCN113393245AImprove shopping experienceReduce transaction riskCharacter and pattern recognitionMachine learningInformation technologyUnique identifier
The invention discloses an early warning method and system for identifying a click farming shop based on e-commerce operation data, belongs to the technical field of e-commerce platform information, and aims to solve the technical problem of how to timely remind a consumer of whether a shop operator carries out farm clicking on commodities in the shop or not, and reduce the transaction risk of the consumer. According to the technical scheme, the method comprises the steps of collecting comprehensive information of commodities and shops of an e-commerce platform, carrying out centralized analysis on top commodities of the shops, recognizing whether the commodity sales volume displayed on a page is the real sales volume or not, and carrying out click farming early warning according to the recognition result. The method specifically comprises the following steps: information crawling: crawling shop and commodity information of a mainstream e-commerce platform to obtain a shop unique identifier id, a commodity id and commodity sales information; shop screening: according to the formulated screening rule, narrowing the check range of the click farming shop by means of a database tool; and establishing a shop click farming early warning model.
Owner:浪潮卓数大数据产业发展有限公司
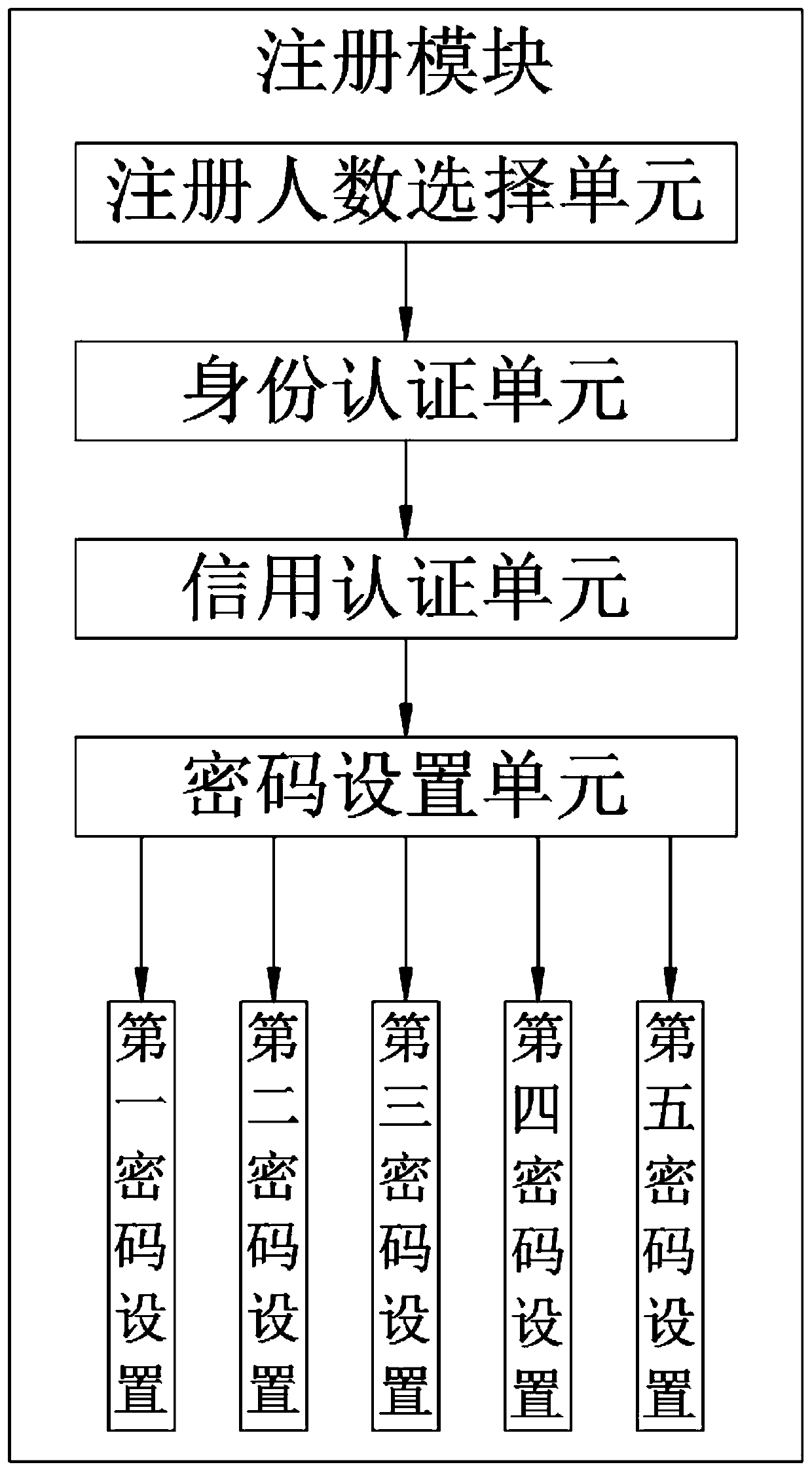
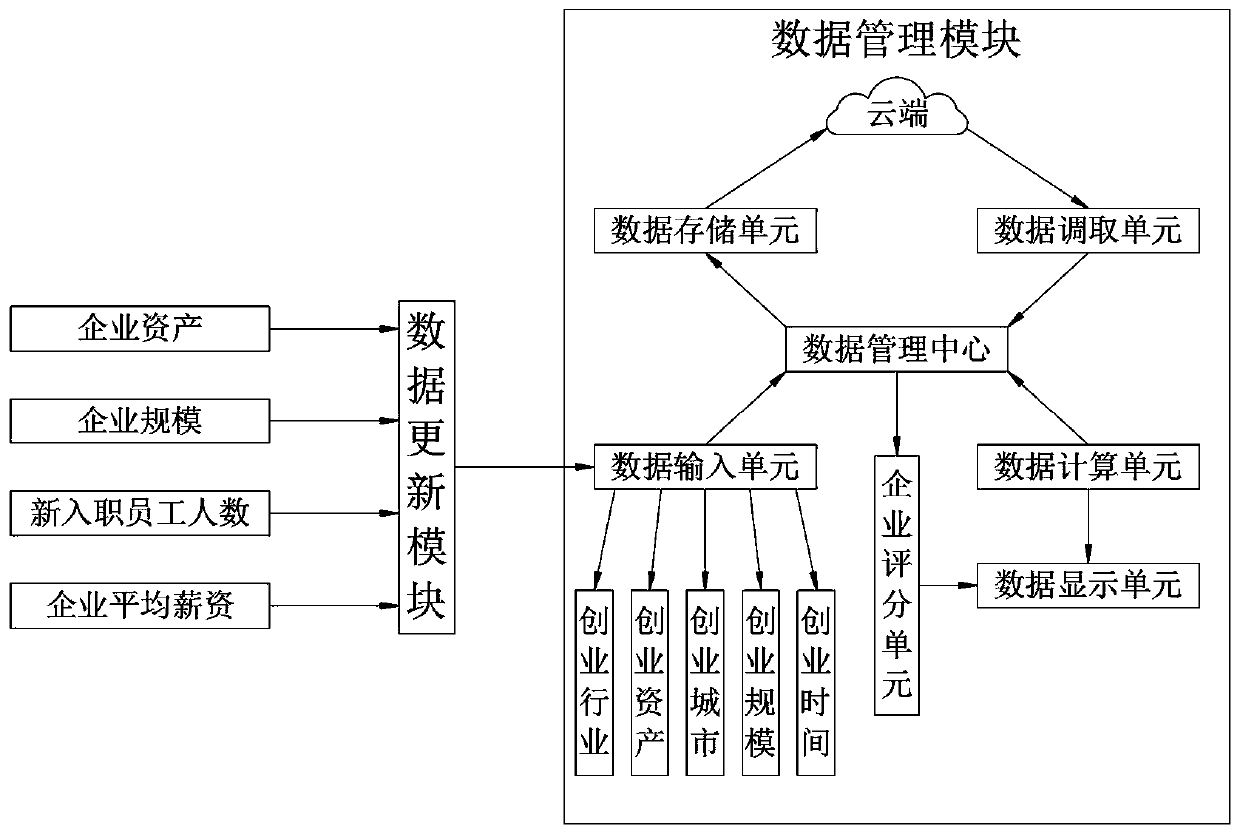
Entrepreneurship registration data management platform based on cloud computing
The invention discloses an entrepreneurship registration data management platform based on cloud computing, the entrepreneurship registration data management platform comprises a registration module,a data management module, a recruitment module, a data updating module and a cloud, and the cloud is used for storing and recording entrepreneurship registration data; the method is scientific and reasonable, safe and convenient to use, credit authentication unit, the credit is verified one by one according to the number of people selected by the registered people number selection unit; maliciousregistration and use of an entrepreneurship registration data management platform can be effectively avoided; waste of resources, the password setting unit is arranged, password setting can be conducted on registered accounts, the safety performance of the accounts can be effectively guaranteed, information leakage is avoided, the safety of the accounts can be effectively protected, the rights andinterests of partners can be effectively guaranteed, the contradiction between the partners is reduced, and the success rate of entrepreneurship is increased.
Owner:汤勤
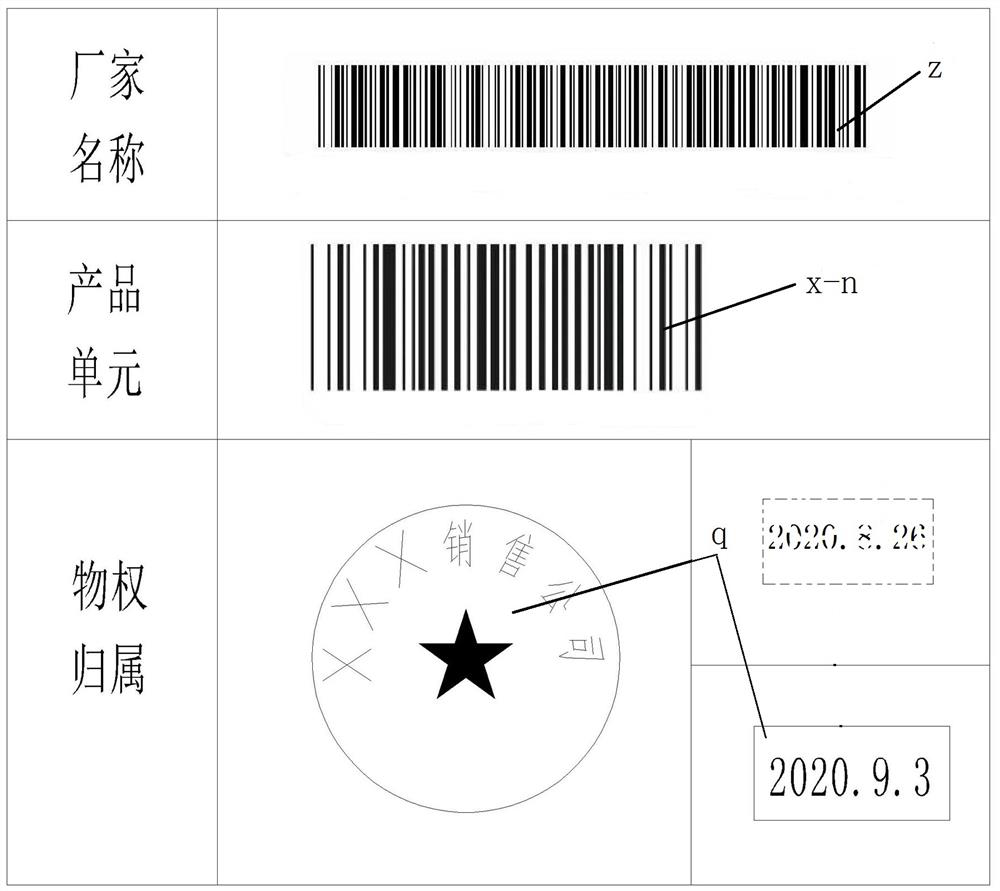
Dynamic tracer code-based transaction settlement, blocking and checking fake goods mixing method
PendingCN114463017AAvoid being scammedBeware of phishingBuying/selling/leasing transactionsPaymentFinancial transaction
The invention relates to a method for transaction settlement based on dynamic tracer codes and blocking and checking mixing of counterfeit goods. Through a transaction settlement management system which is established for a manufacturer and comprises a database, a settlement account specially used for receiving and transferring transaction payment and matched software, feature information codes are configured and marked for commodity units, and matched dynamic tracing codes are generated and randomly updated. By means of the transaction settlement management system, identity legality and rationality of all online transaction commodity units and sellers can be randomly checked, and confirmation of the management system is obtained. And after the buyer responds to the confirmation, the payment of goods is transferred to the seller through the special account of the manufacturer, so that the information recorded in each transaction is complementarily recorded into the read-only memory of the system. The method is easy to popularize and apply and remarkable in effect, and even if the scale of counterfeit goods is reduced, the counterfeit goods can be checked by means of ultimate identification performed by means of a photoelectric technology and sampling transaction products.
Owner:HEBEI GAOPAI NETWORK TECH CO LTD
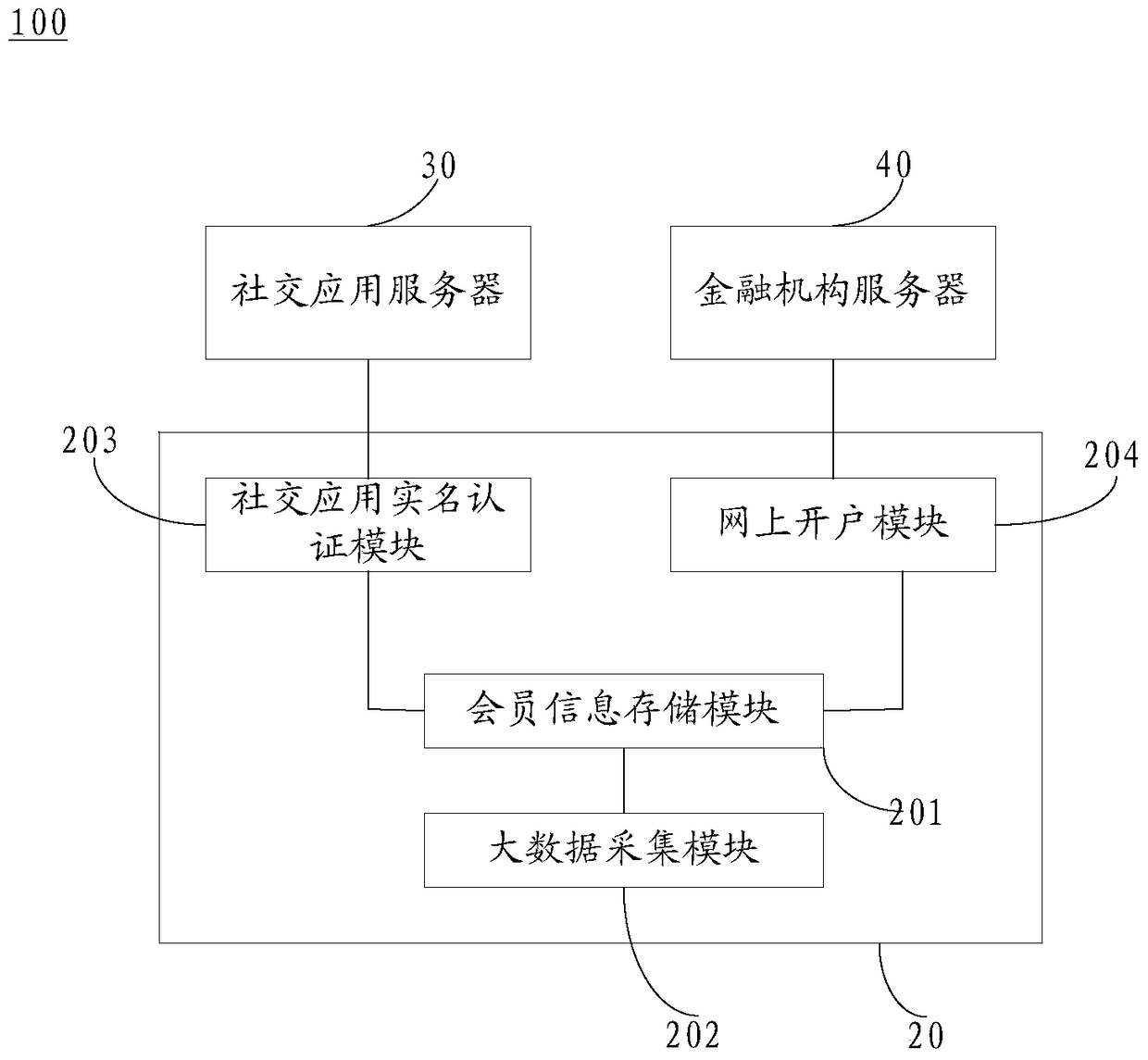
Personal information sharing system, personal information sharing method and identity authentication method thereof
ActiveCN104717073BAchieve sharingEasy constructionUser identity/authority verificationApplication serverInternet privacy
The invention discloses a personal information sharing system which comprises a personal identity authentication system, a social contact application server and a financing institution server. The social contact application server and the financing institution server are related to the personal identity authentication system. The personal identity authentication system comprises a member information storing module, a big data collecting module, a social contact application autonym authentication module and an online account opening module, wherein the social contact application autonym authentication module can receive autonym authentication requests from the social contact application server and feed personal information back to carry out autonym authentication, the online account opening module can send account opening requests to the financing institution server, and the financing institution server can inquire personal information stored in the member information storing module or an opened account organization, confirm the member identities and duplicate the personal information to finish online account opening. Compared with the prior art, the personal information sharing system achieves autonym authentication and online account opening of social contact application accounts, improves social contact safety and reduces the work amount of workers of an account opening organization. The invention further discloses a personal information sharing method and a personal information authentication method.
Owner:张文
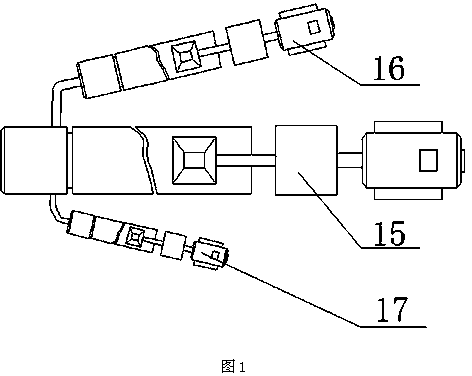
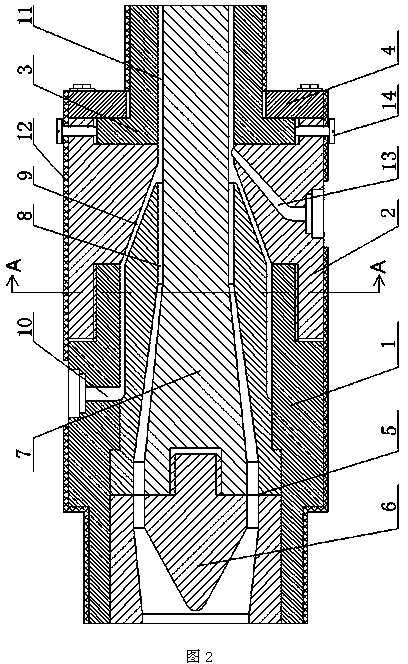
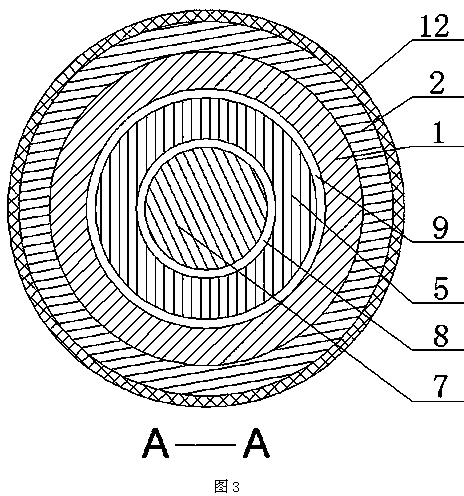
Two-color tube processing equipment
InactiveCN104290307AEasy to distinguishAvoid being scammedTubular articlesEngineeringMechanical engineering
The invention discloses two-color tube processing equipment which comprises an inner pipeline extruding machine. An outer pipeline extruding machine is arranged on one side of the inner pipeline extruding machine; the machine head end of the outer pipeline extruder is connected with the machine head of the inner pipeline extruding machine; the machine head comprises a first machine head part and a second machine head part connected to the first machine head part; the other end of the second machine head part is provided with a mounting base; a clamping ring sleeves the mounting base; the clamping ring is connected with the second machine head part; an outer mold core and a distributor are arranged inside a machine head body; the distributor is connected with an inner mold core placed inside the outer mold core; an inner pipeline cavity is arranged between the outer mold core and the distributor body as well as the inner mold core; an outer pipeline cavity is arranged between the outer mold core and the machine head body; the head end of the outer pipeline cavity is communicated with an outer glue filling channel on the first machine head part; a pipeline molding cavity is arranged between the mounting base and the inner mold core; the inner pipeline cavity and the outer pipeline cavity are of an annular structure; the head ends of the two cavities are intersected at the head end of the pipeline molding cavity; a heating coil is arranged outside the machine head body.
Owner:GUIZHOU CHENGYANG PIPELINE SCI & TECH
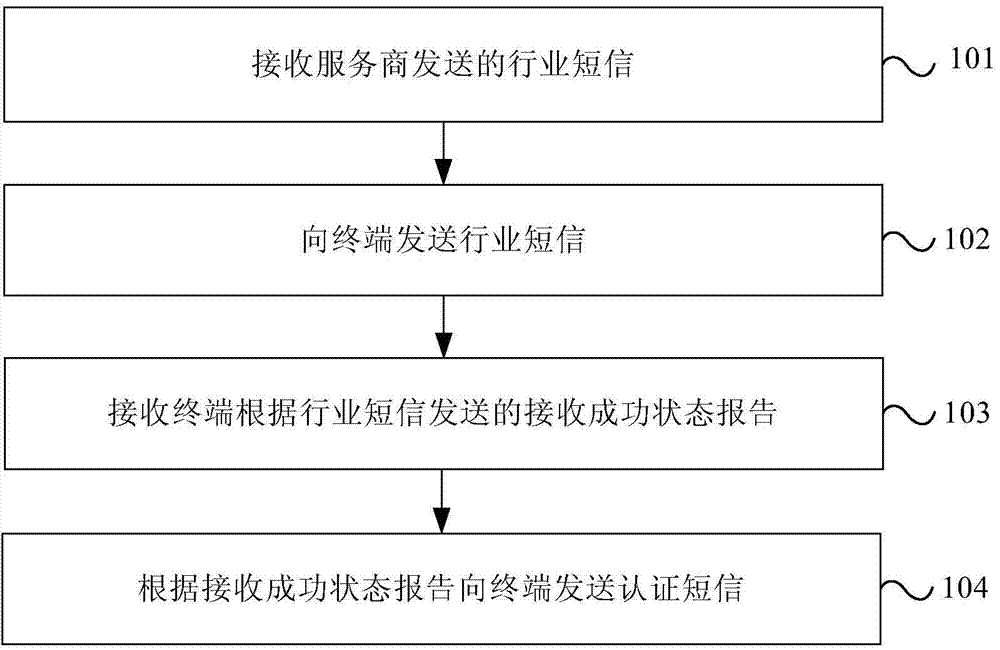
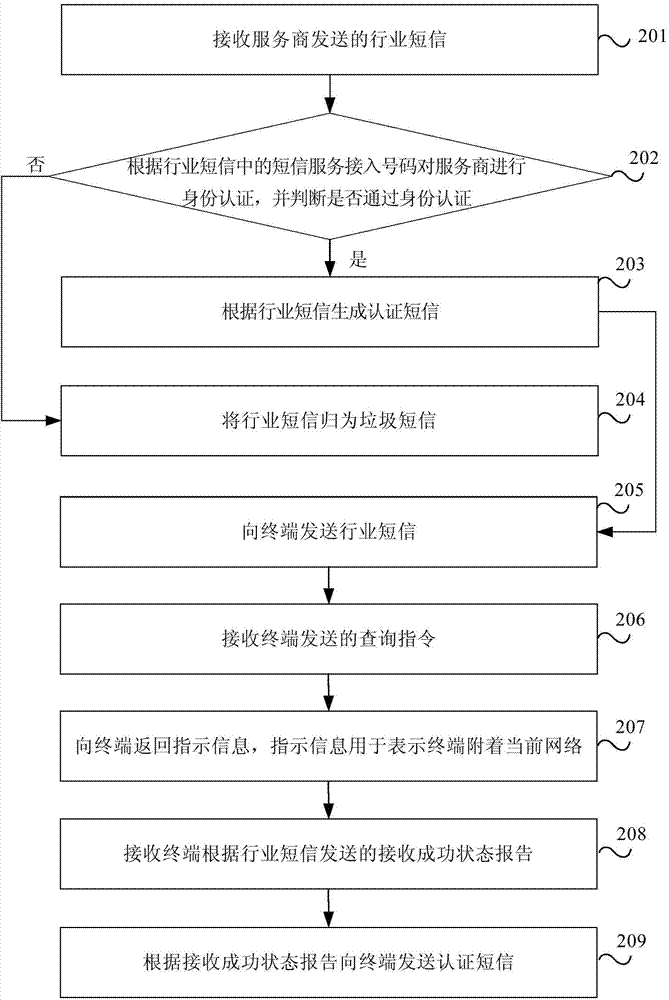
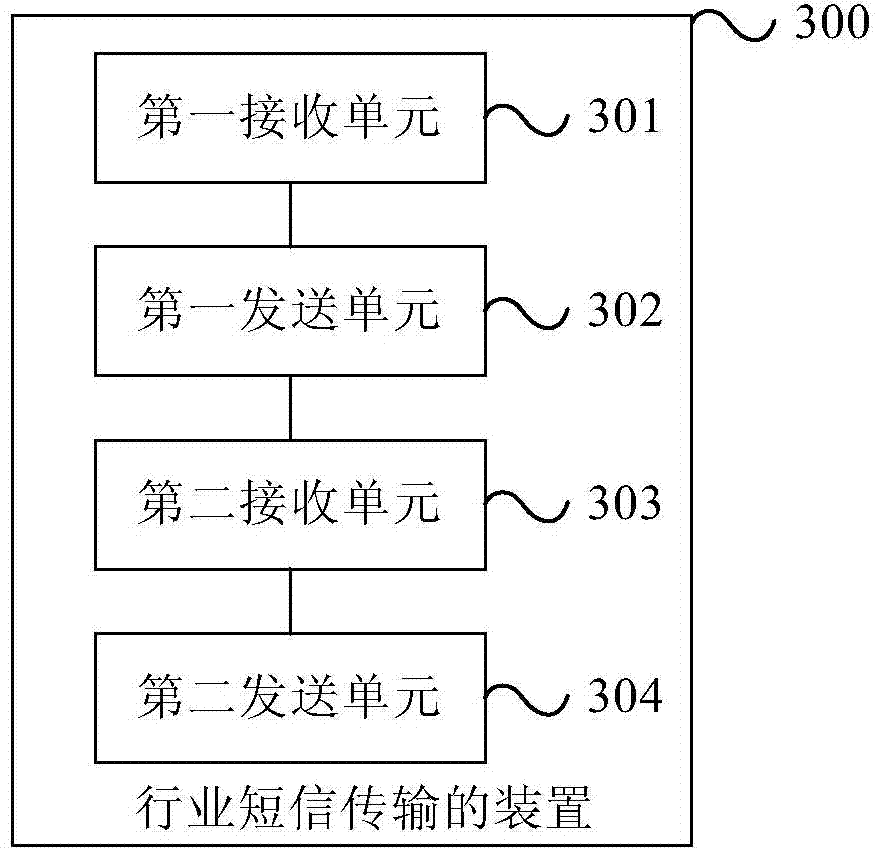
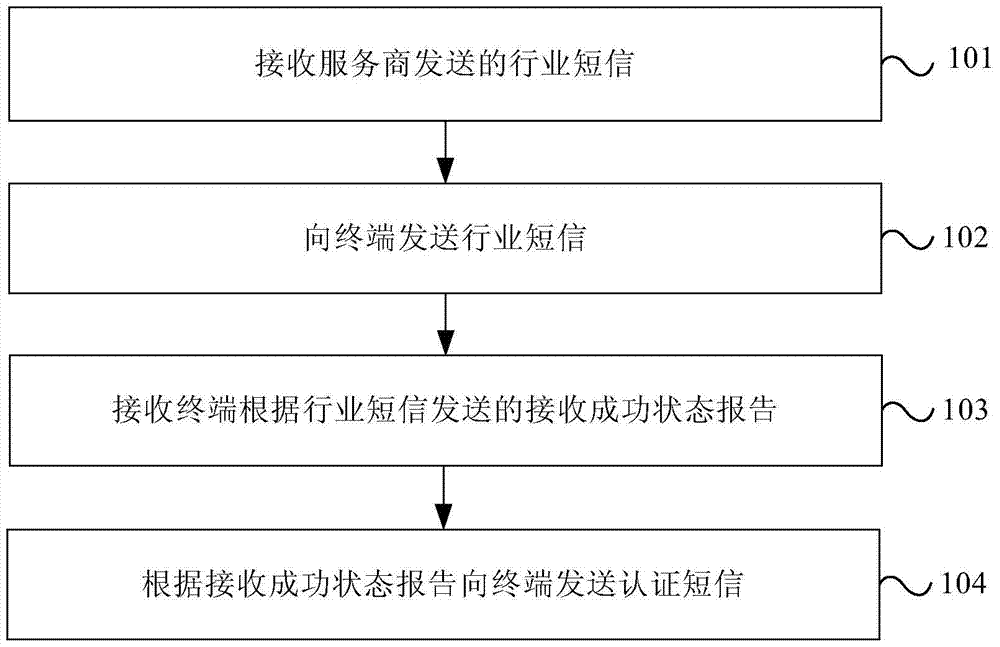
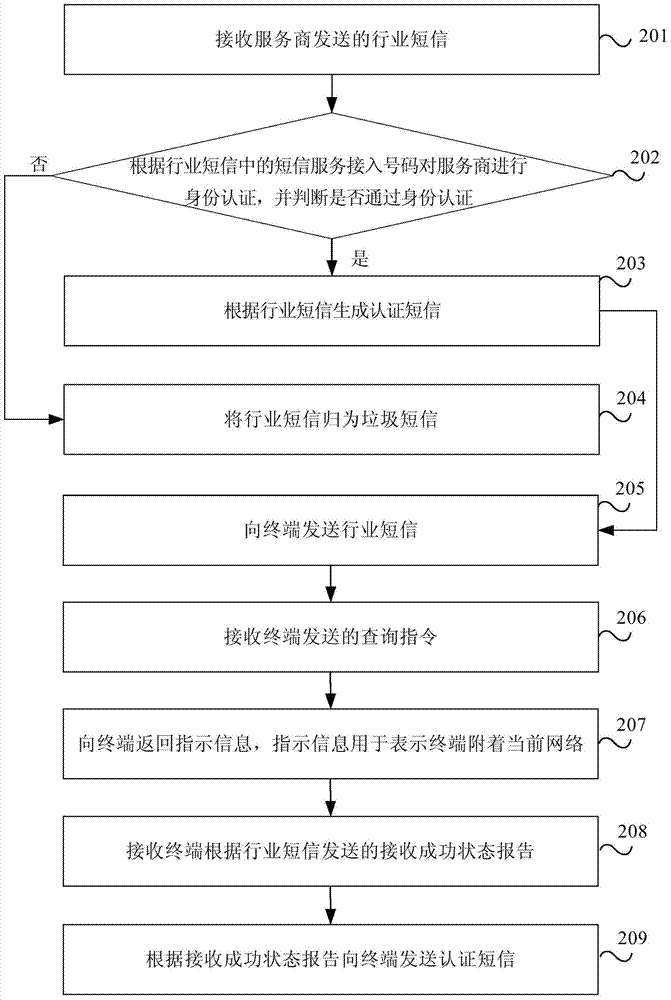
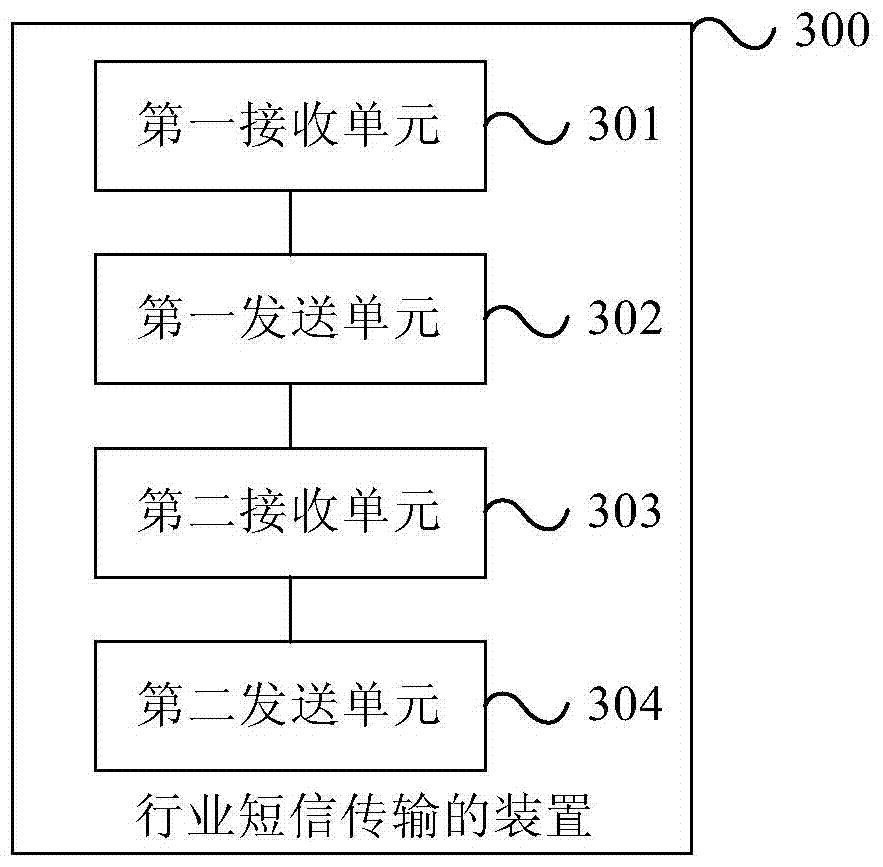
Method and device for industrial text message transmission
ActiveCN104244209AAvoid being scammedMessaging/mailboxes/announcementsSecurity arrangementWorld Wide WebService provider
The invention provides a method and a device for industrial text message transmission. The method includes receiving industrial text messages sent from a service provider, sending the industrial text messages to a terminal, receiving receive-success state reports sent from the terminal according to the industrial text messages, and sending certificate text messages corresponding to the industrial text messages to the terminal according to the receive-success state reports. According to the method and the device for industrial text message transmission, the certificate text messages corresponding to the industrial text messages are sent to the terminal, so that the terminal learns that the industrial text messages are normal test messages but test messages sent from fake base stations and fraud is avoided.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Method and system for initiating return type crowd funding and computer readable storage medium
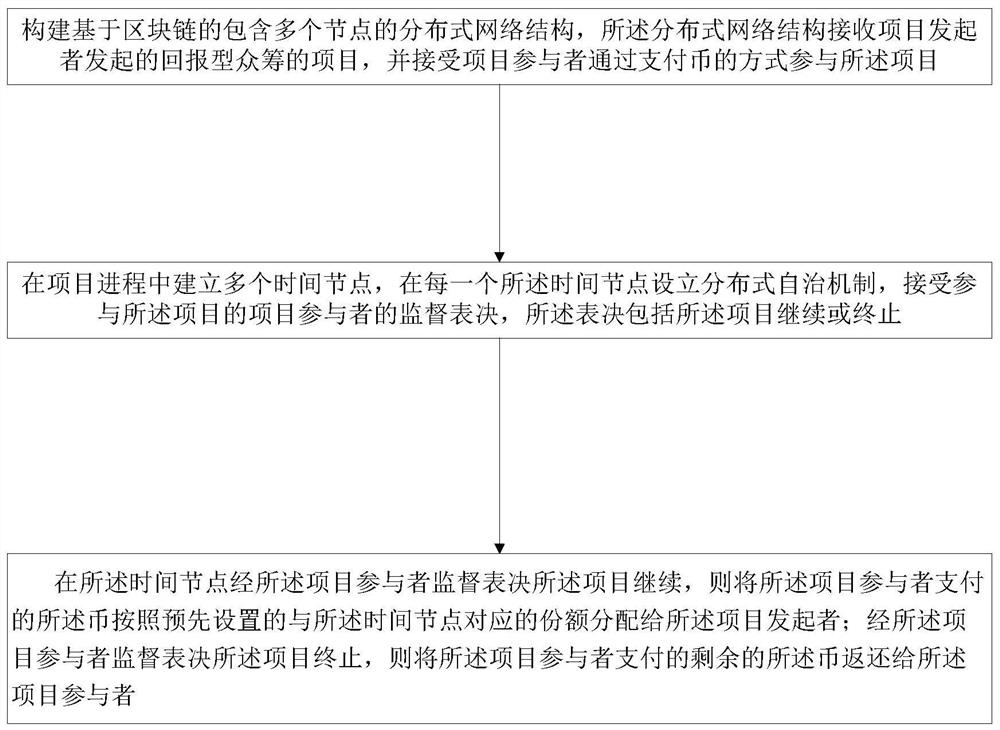
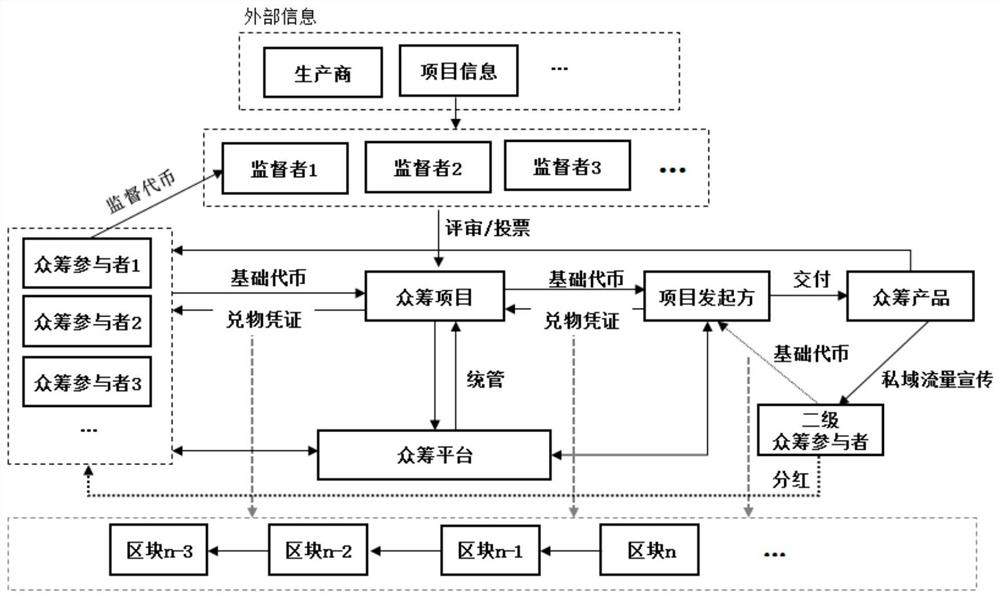
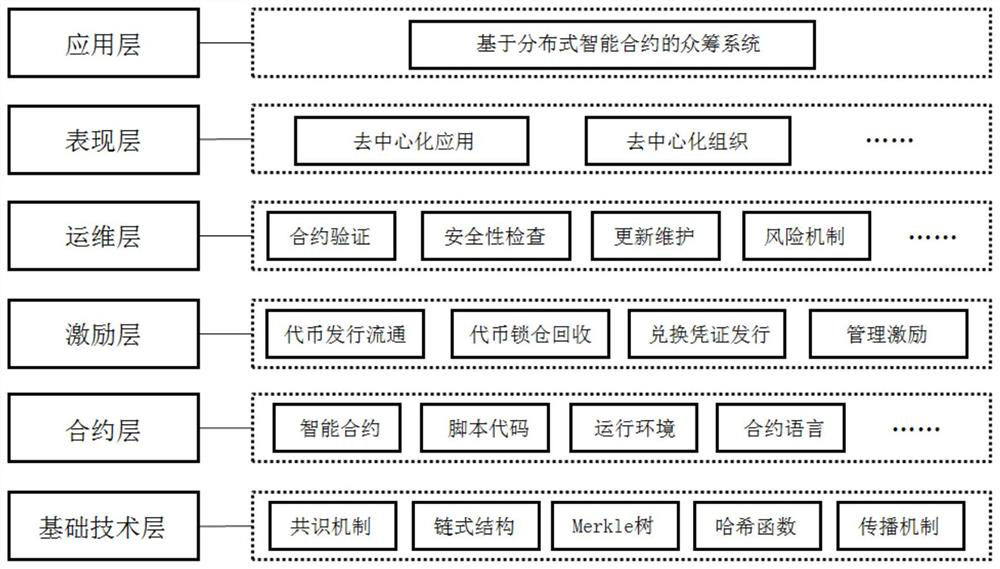
PendingCN111652602AAvoid being scammedGuarantee authenticityFinancePayment protocolsPaymentComputer network
The invention provides a method and system for initiating return type crowd funding and a computer readable storage medium. The method comprises: constructing a block chain-based distributed network structure comprising a plurality of nodes, receiving a return crowd funding project initiated by a project initiator by the distributed network structure, and receiving participation of project participants in the project in a coin payment mode; establishing a plurality of time nodes in the project process, setting a distributed autonomous mechanism at each time node, and receiving supervision voting of project participants participating in the project, wherein voting comprises project continuing or stopping; if the project continues to be supervised and voted by the project participant at thetime node, allocating the currency paid by the project participant to the project initiator according to a preset share corresponding to the time node; and returning the residual money paid by the project participant to the project participant if the project participant supervises that the voting project is ended. And the passive situation of the participant and the possible fraudulent problem areavoided.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Enterprise financial sharing evaluation method and system based on big data
InactiveCN112905663ADeepen understandingInvestment prudentDigital data information retrievalFinanceBusiness enterpriseData profiling
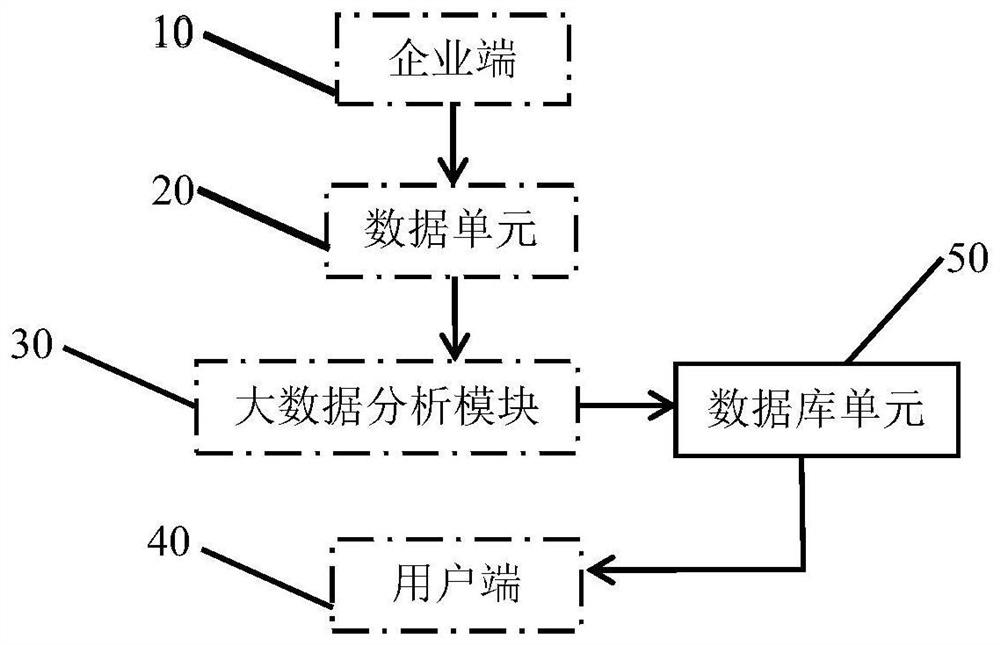
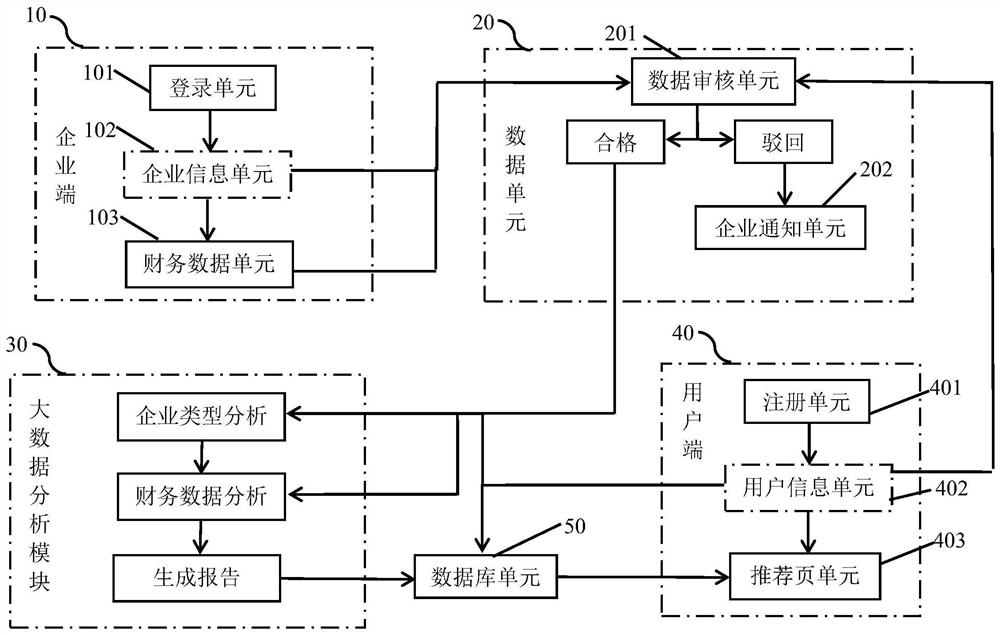
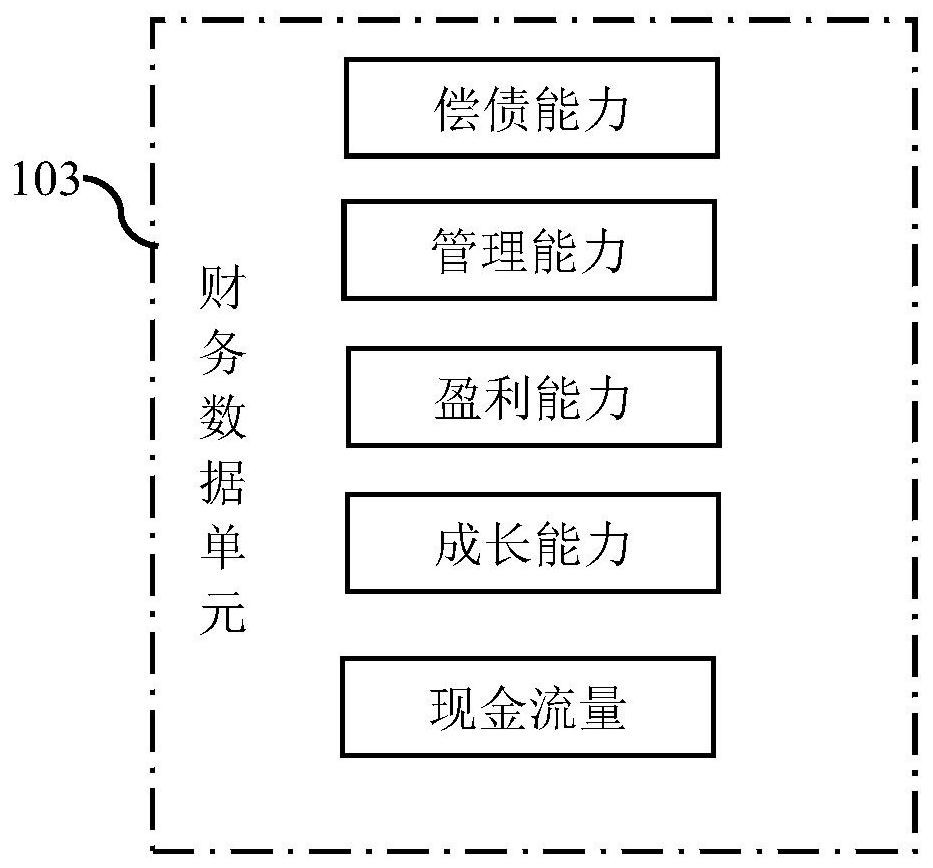
The invention discloses an enterprise finance sharing evaluation system based on big data, and belongs to the technical field of enterprise finance analysis, and the system comprises an enterprise terminal, a data unit, a big data analysis module, a user terminal and a database unit. The enterprise terminal comprises a login unit and an enterprise information and financial data unit; analysis of personal information of a user is realized through cooperative use of the units, an enterprise most suitable for investment can be recommended after analysis according to the investment tendency and the investment amount of the user, selection for the user is more diversified, and the enterprise can be directly contacted through the contact information input by the enterprise in the system, so that the safety of the investment process is enhanced; the invention further discloses a using method of the system. By means of the using method, enterprises and individual users can know the working process of the system more visually.
Owner:广州华商职业学院
Network false information prevention technology
The invention discloses a network false information prevention technology, which is mainly applied to the field of Internet information publishing. After an information publisher publishes information, a third party verifies the truth of information publishing contents and uniformly marks accurately-verified information with symbols and characters which can represent verification property or uniformly saves the accurately-verified information in an independent information saving area which can represent the verification property, so that the verified information can be marked, an information user can recognize the information for using, so as to avoid being taken.
Owner:胡萍
Portable Safety Hammer
The invention belongs to the technical field of tools and hardware and relates to a portable safety hammer comprising a tip, a body, a handle sliding post, a telescopic handle, finger grooves, a handle cavity, a carrier ring, bag cord grooves, a ring stem, a hollow handle segment, a solid handle segment shaft, a solid handle segment, a stop button, a stop button slide, a stop button fixing groove, a hollow handle segment cavity, a hollow handle segment wall, a stop button head, a stop button cavity top hole, a stop button cavity top, a stop button head seat, a stop button spring, a stop button wall, and a stop button cavity. The portable safety hammer is characterized in that the tip is a taper tip part of one end of the portable safety hammer, the body is cylindrical with diameter of 1-5cm and is a main part of the portable safety hammer, the top of the body is provided with one row of bag cord grooves, the other side, opposite to the bag cord grooves, is provided with one row of finger grooves, the center of the body is provided with the handle cavity used for accommodating the telescopic handle, one end of the body is provided with the tip, and the other end of the body is connected with the carrier ring through the ring stem. The portable safety hammer is simple to produce, versatile, highly operable, low in cost, and significantly effective.
Owner:常熟紫金知识产权服务有限公司
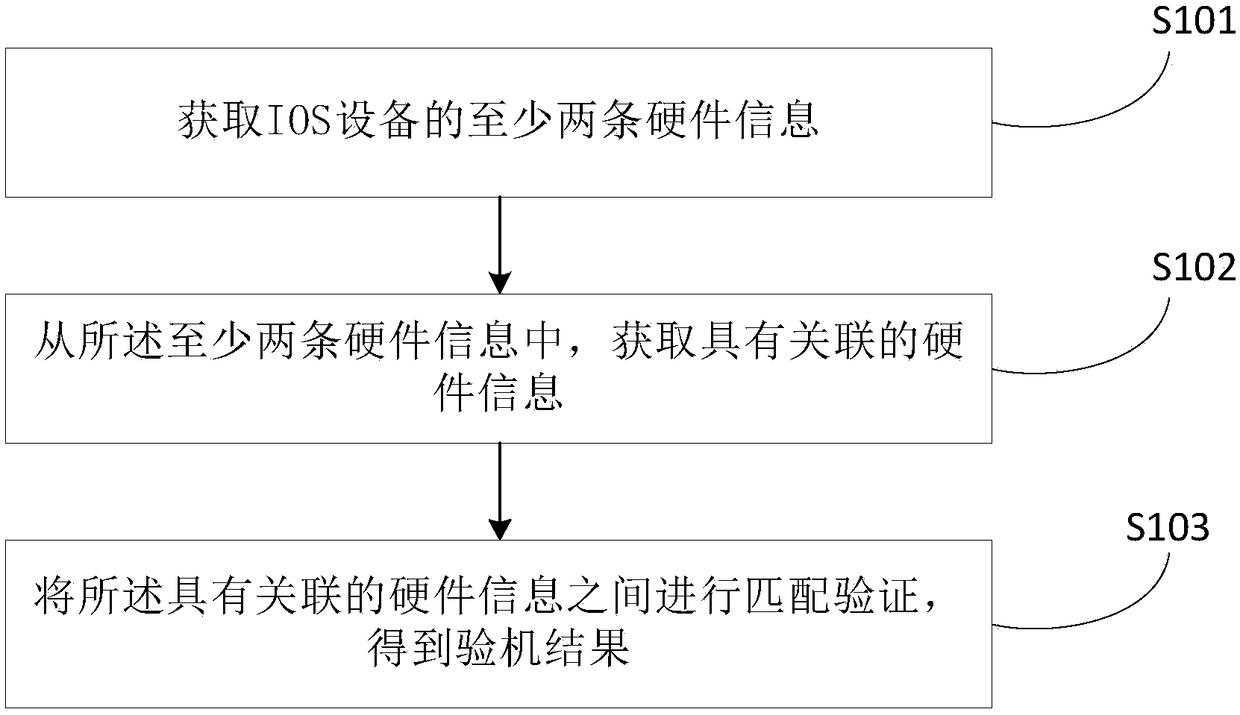
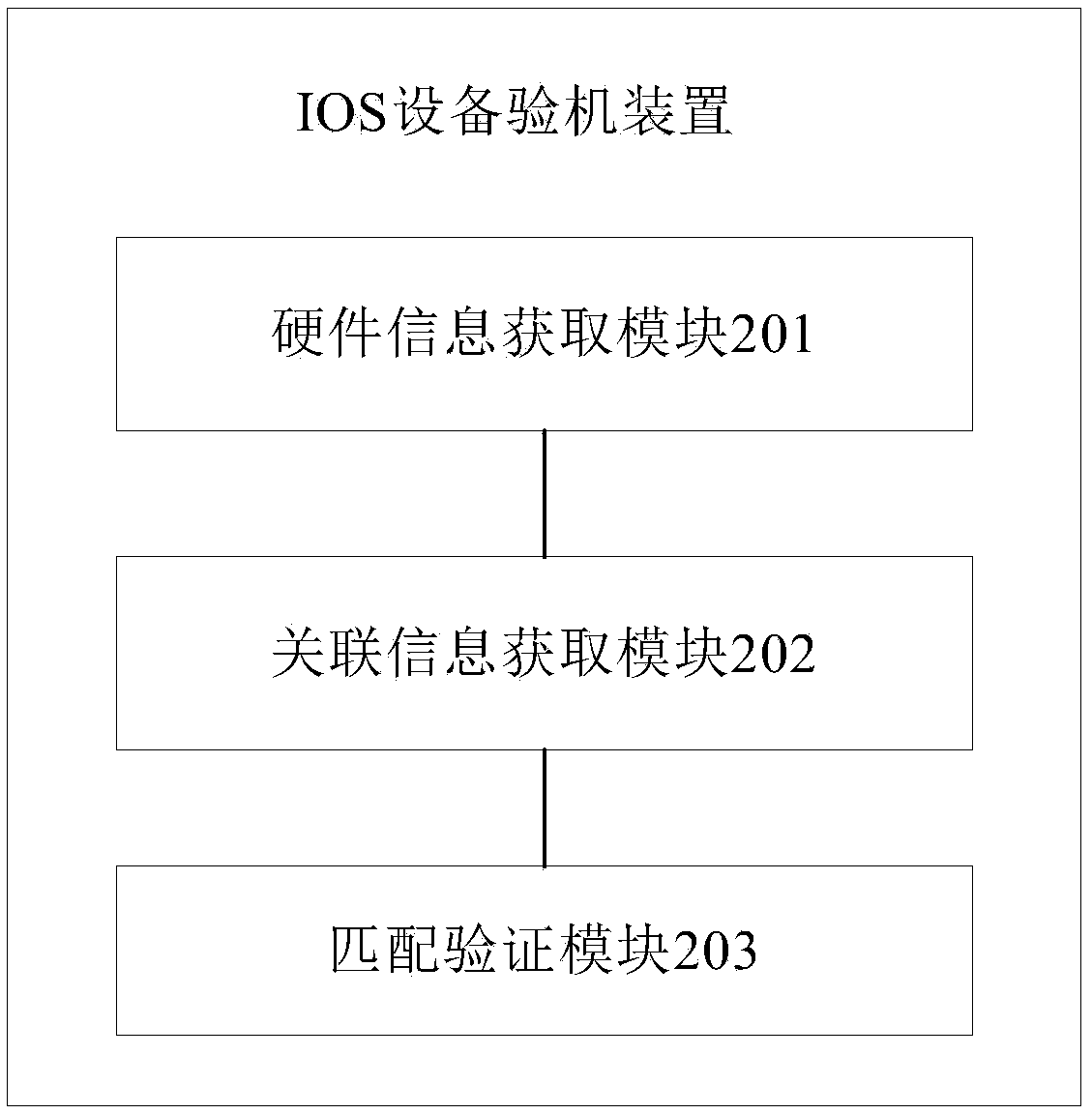
IOS device machine verification method and device, and terminal
InactiveCN108510289AProtect interestsAccurate identificationSustainable waste treatmentProduct appraisalComputer terminalEmbedded system
The present invention provides an IOS device machine verification method. The device comprises the steps of: obtaining at least two hardware information of an IOS device; obtaining hardware information having association from the at least two hardware information; and performing matching verification of the hardware information having association to obtain a machine verification result. The matching verification of the hardware information having association is performed to rapidly and accurately identify the original machine type of the purchased IOS device and automatically identify whetherthe IOS device is abnormal or not on the premise that a user does not dismount the machine so as to guarantee the user's benefit and avoid being tricked.
Owner:ALIBABA (CHINA) CO LTD
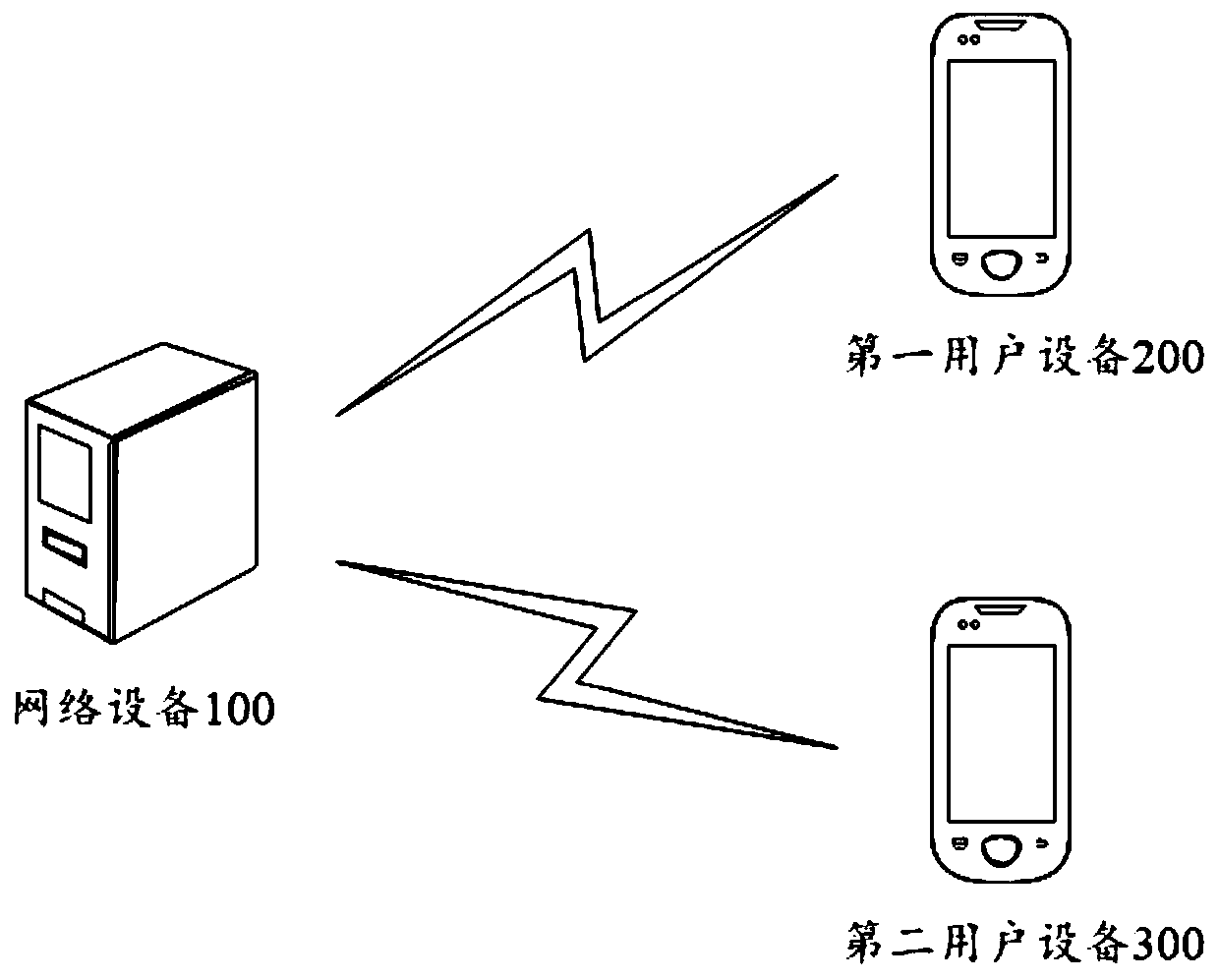
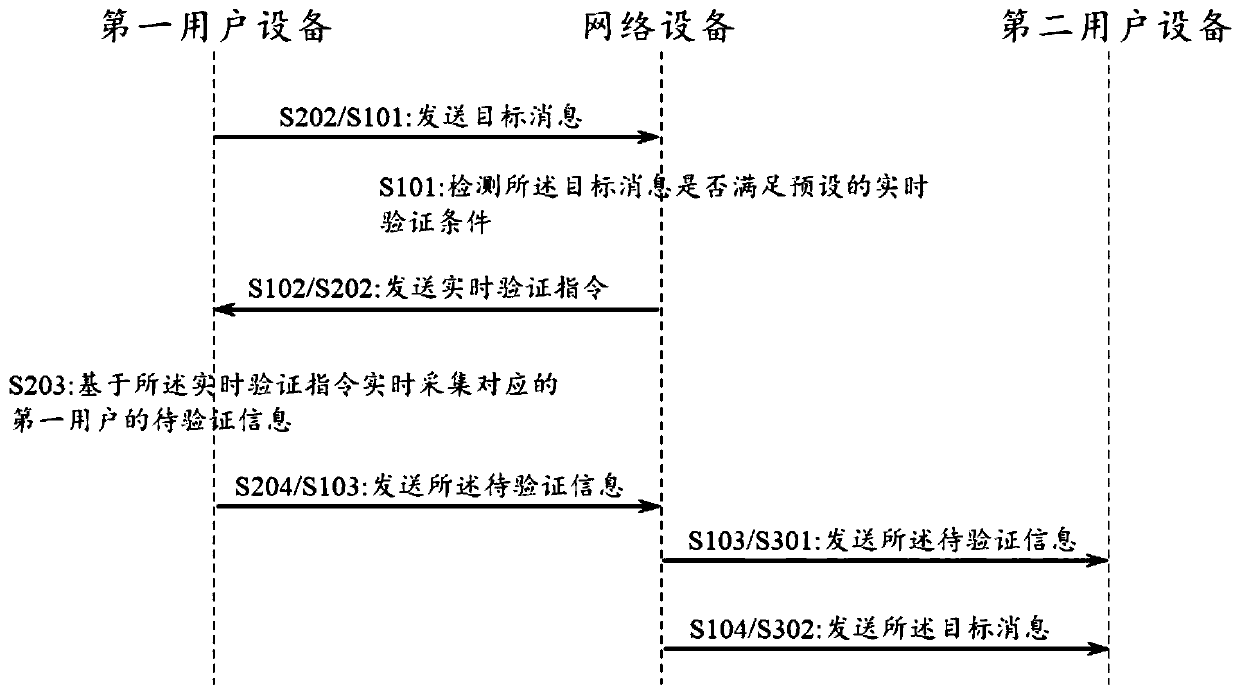
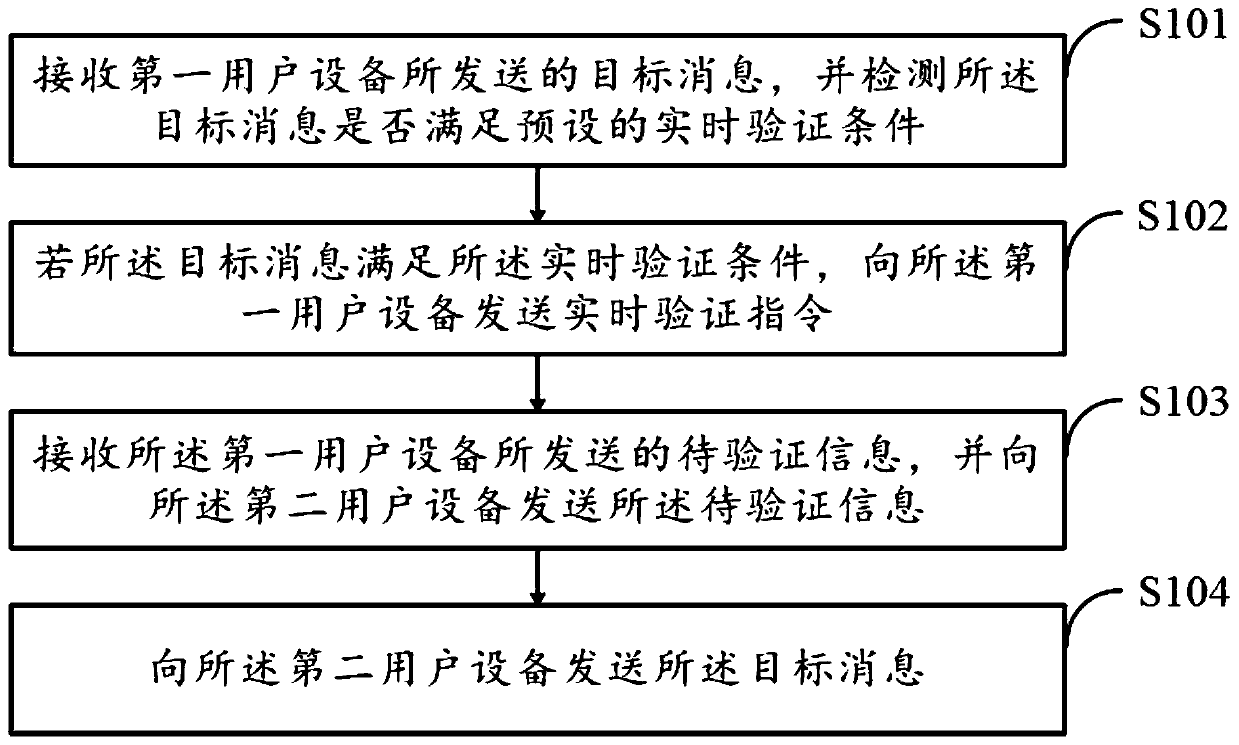
A method and apparatus for transmitting target message
ActiveCN109981644ASafeguard information and property securityAvoid being scammedData switching networksReal time acquisitionComputer network
The invention aims to provide a method and apparatus for sending a target message. The method comprises the following steps: first user equipment sends the target message to network equipment; the network equipment detects whether the target message satisfies a preset real-time verification condition, and sends a real-time verification instruction to the first user equipment; the first user equipment collects to-be-verified information of a corresponding first user in real time based on the real-time verification instruction, and sends the to-be-verified information to the network equipment; the network equipment sends the to-be-verified information and the target message to the second user equipment; and the second user equipment receives the to-be-verified information and the target message. According to the method, the receiver of the message can verify the identity of the sender according to the received content, so that the receiver of the message is prevented from being cheated.
Owner:SHANGHAI ZHANGMEN TECH
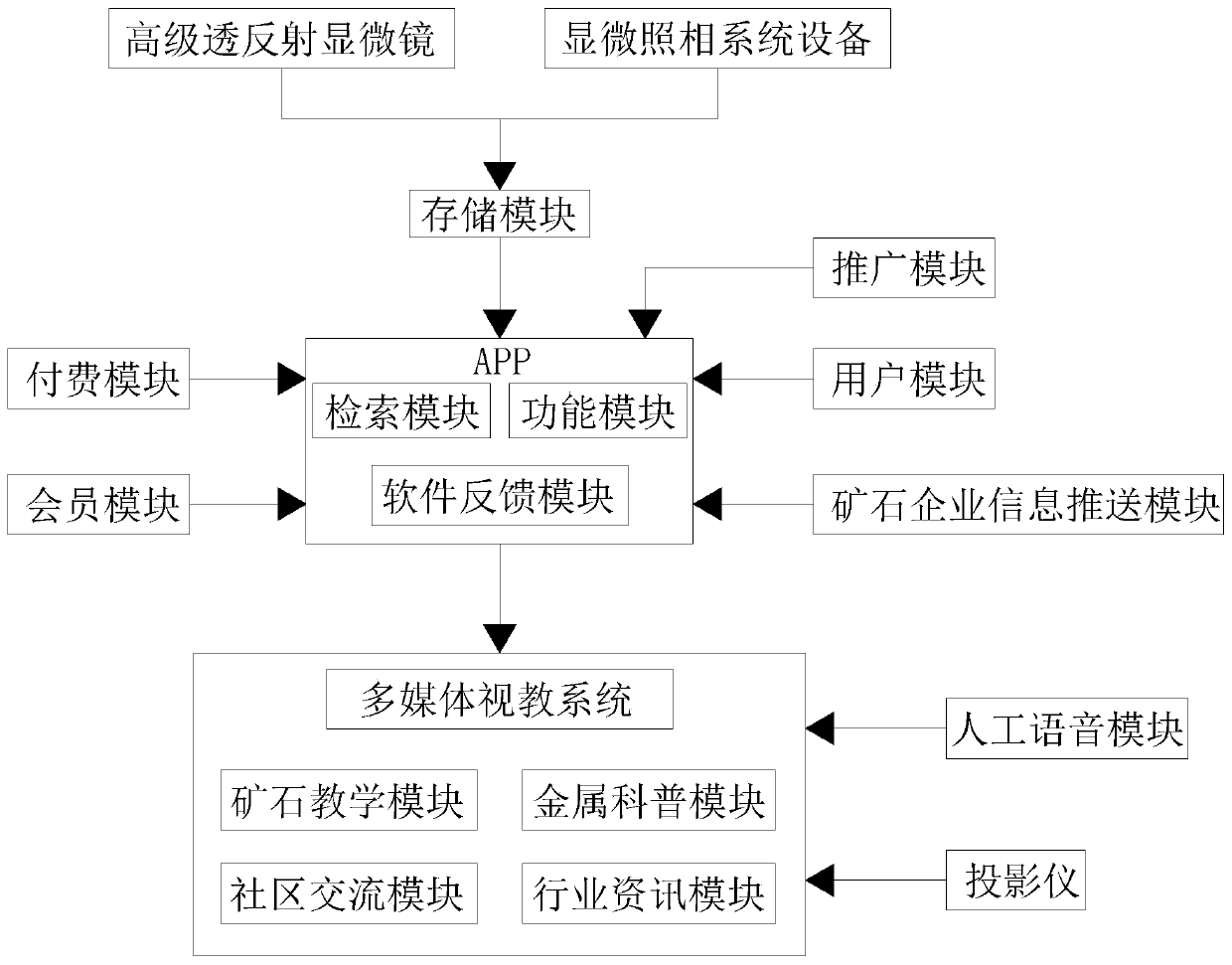
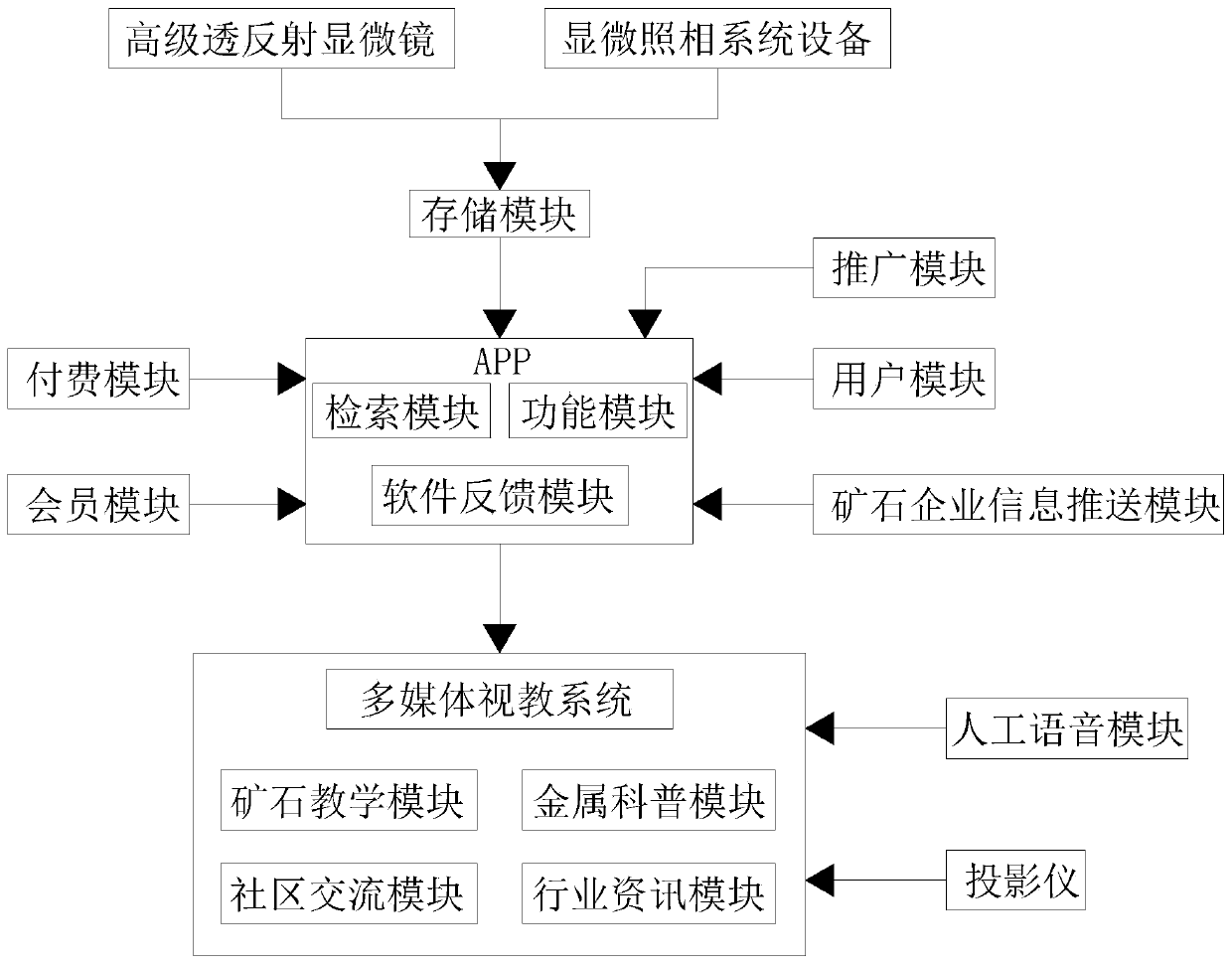
Visual retrieval system for geoscience metal minerals
PendingCN110032653AImprove discriminationEasy to watchData processing applicationsMetadata multimedia retrievalPaymentX-ray
The invention discloses a visual retrieval system for geoscience metal minerals. The system comprises an APP and a multimedia visual education system, the output end of the APP is connected with the input end of a multimedia visual education system, and the input end of the APP is separately connected with the output ends of the storage modules in a high-level transflective microscope and a microphotography system device, the input end of the APP is connected with the output end of a popularization module, and the input end of the APP is connected with the output end of a user module. According to the invention, by the cooperation of the APP, the multimedia visual education system, the storage module, the promotion module, the user module, an ore enterprise information push module, a payment module and a member module, different ore X-ray plates can be displayed, students can watch and learn the ore X-ray plates conveniently, the problems that teaching resources are rich but not systematic, and the previous teaching process is single in means are solved, meanwhile, teachers can teach conveniently, people can judge the types of ores conveniently, and the cheating condition is avoided.
Owner:CHENGDU UNIVERSITY OF TECHNOLOGY
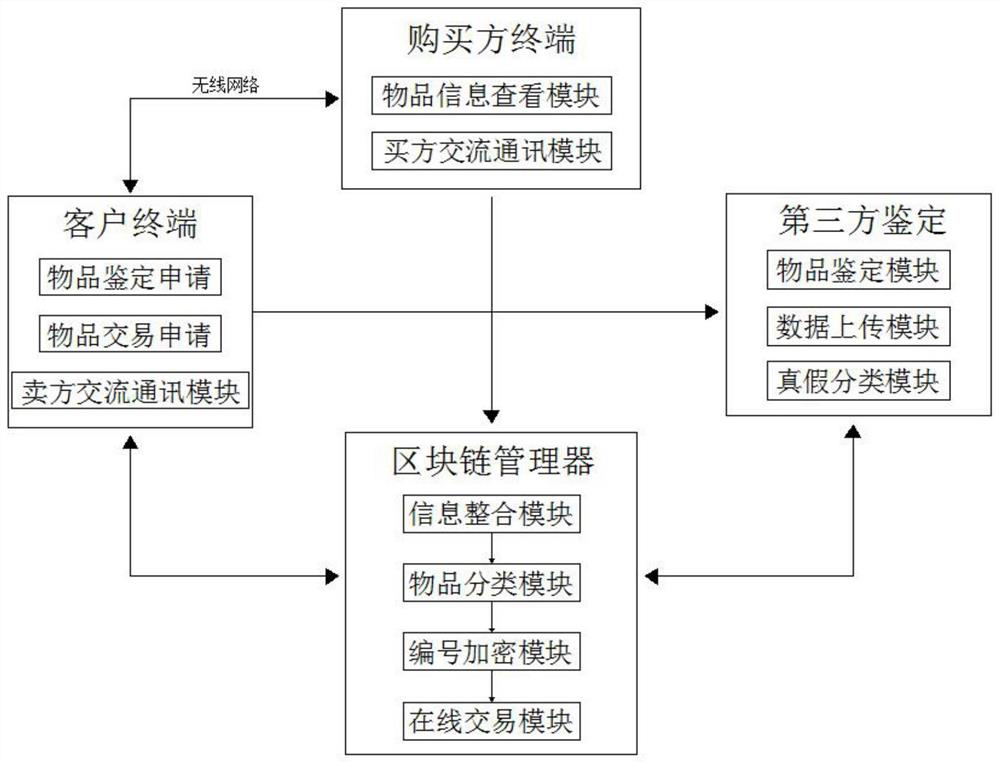
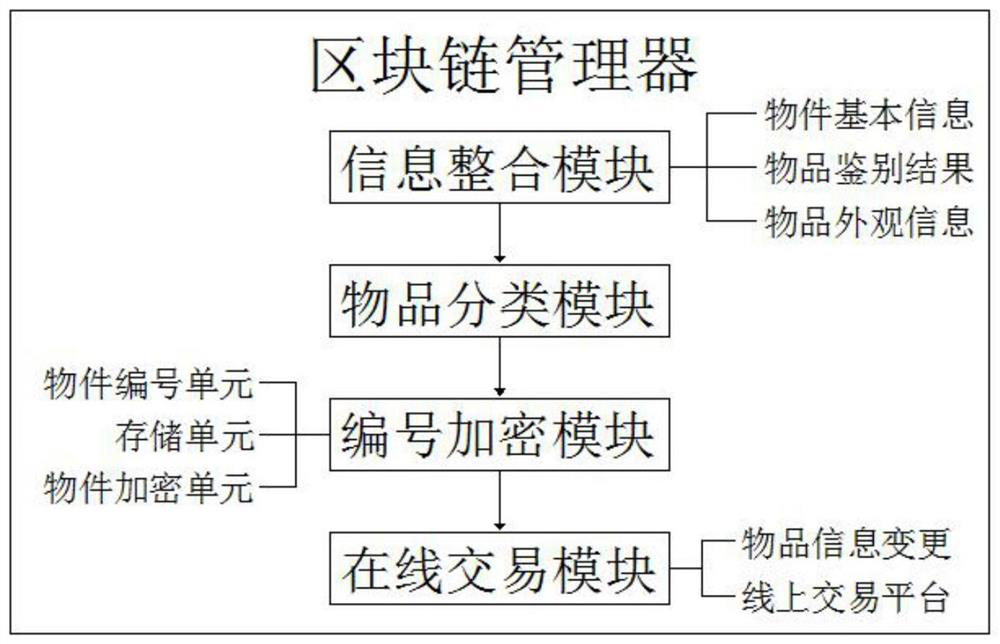
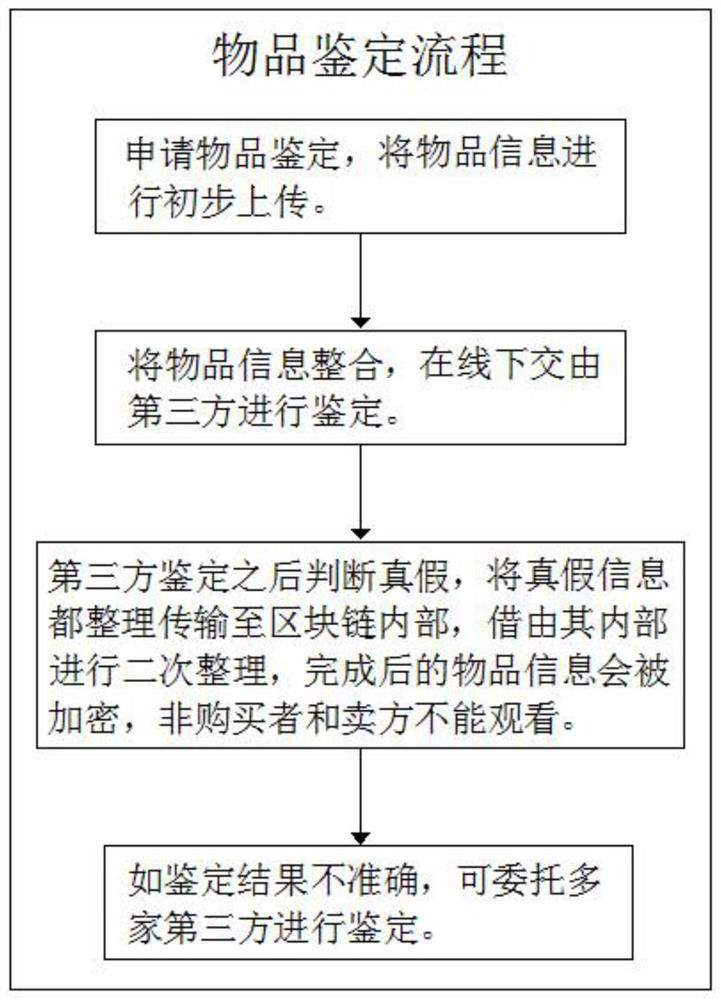
Article identification and transaction system based on block chain
InactiveCN111768209AImprove transaction success rateEasy to watchDatabase distribution/replicationPayment protocolsThird partyFinancial transaction
The invention discloses an article identification and transaction system based on a block chain. The system comprises a client terminal, a purchaser terminal, a blockchain manager and a third-party identification, the client terminal is in bidirectional connection with the blockchain manager, the blockchain manager is in bidirectional connection with the third-party identification, and the outputend of the client terminal is connected with the input end of the third-party identification. According to the article identification and transaction system based on a block chain, firstly, the systemcan synchronously update the information of the purchaser and the seller in real time; synchronous communication between the two parties during transaction is facilitated; the transaction success rate of the articles is improved; at the same time, there is no more than one third-party identification, multi-party identification can be carried out according to needs, each three-party identificationperson cannot see the data of the other party, the accuracy of each identification result is ensured, then according to the result, the authenticity classification module can price the article, and finally the seller considers the pricing.
Owner:JIANGSU RONGZE INFORMATION TECH CO LTD
Phone call identification method and device
ActiveCN104159230BMake sure the results are real and validAvoid being scammedInterconnection arrangementsCalling susbscriber number recording/indicationTelephonyTelephone call
Owner:XIAOMI INC
Second-hand vehicle trading information online management platform system
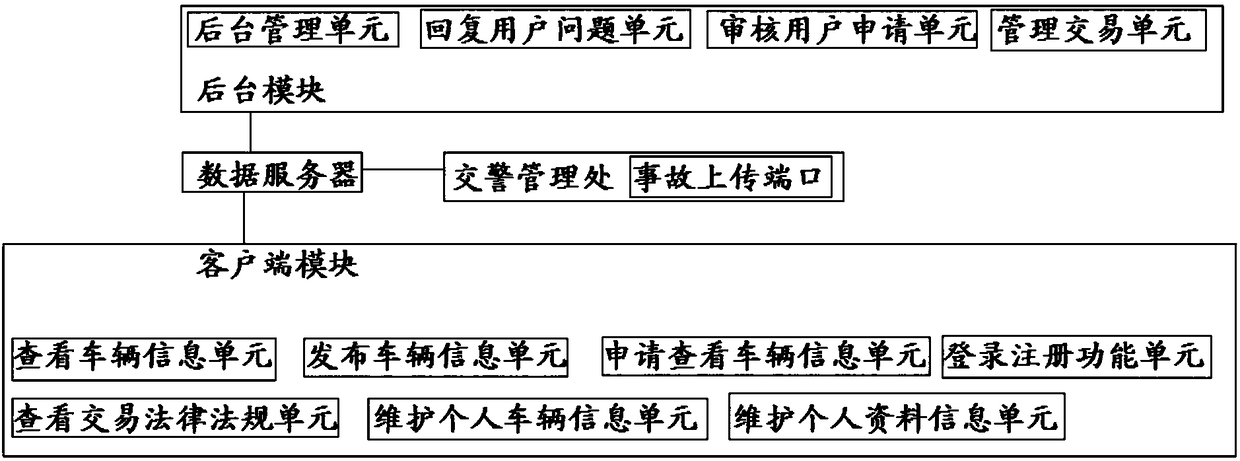
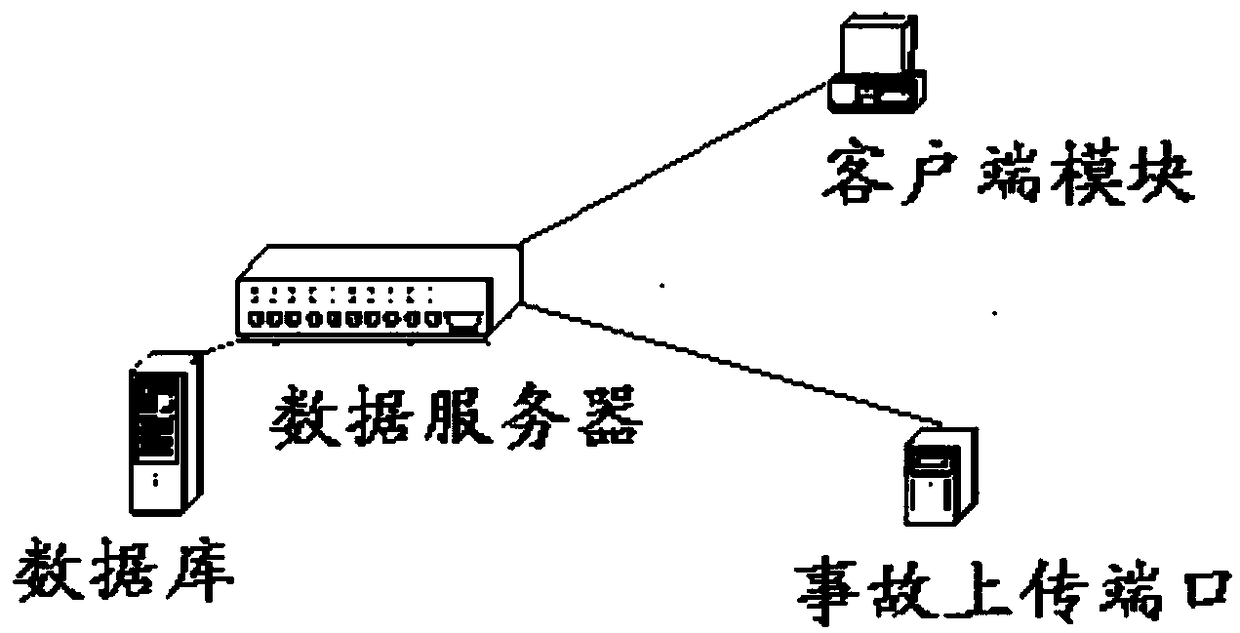
InactiveCN108416654AEliminate Fraudulent TransactionsConvenient queryBuying/selling/leasing transactionsManagement unitAccidents vehicle
The invention discloses a second-hand vehicle trading information online management platform system comprising a background module, a data server and a client side module. The background module comprises a background management unit, a user question reply unit, a user application review unit and a trading management unit. The client side module comprises a vehicle information viewing unit, a vehicle information releasing unit, a vehicle information viewing application unit, trading law and regulation viewing unit, a personal vehicle information maintenance unit, a personal data information maintenance unit and a login registration function unit. The data sever is connected with the traffic police administrative office. The traffic police administrative office is provided with an accident upload port. The traffic police inputs and uploads the accident vehicle information through the accident upload port. The background module and the client side module are connected with the data sever.Whether the vehicle to be purchased is the accident vehicle can be inquired in second-hand vehicle trading so that great development of the second-hand vehicle market can be guaranteed and the traffic control department is enabled to inquire the governed vehicle information.
Owner:陕西有顺信息科技有限公司
Method and device for identifying phishing websites
ActiveCN107800686BRealize online real-time identificationAvoid being scammedTransmissionDomain nameWeb site
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Negative pressure degassing-based detector for bubbles in hydrogen water and detection method thereof
PendingCN112973197AAvoid being scammedEasy to observeComponent separationMaterial analysis by optical meansAir pumpAnalytical chemistry
The invention relates to a detector for bubbles in hydrogen water based on negative pressure degassing, which is characterized by comprising a headspace bottle, a sucking pump and a controller for controlling the sucking pump to work, the headspace bottle is provided with a water inlet and a gas outlet, and the gas inlet end of the sucking pump is communicated with the gas outlet of the headspace bottle; when the device is used, quantitative hydrogenation water is injected into the headspace bottle, and the controller controls the sucking pump to suck out nanoscale bubbles in the hydrogenation water. The garbage can is high in practicability and easy to popularize.
Owner:浙江读氢科技有限公司
Method and device for industry short message transmission
ActiveCN104244209BAvoid being scammedMessaging/mailboxes/announcementsSecurity arrangementShort Message ServiceComputer terminal
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com