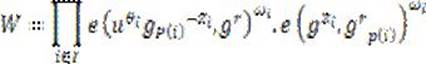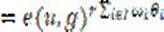A Scalable Access Control Method for Fog Computing
An access control and fog computing technology, which is applied in the transmission system, electrical components, etc., can solve the problem that the access control strategy cannot be directly applied, and achieve the effect of integrity protection and reduction of computing overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to describe the technical solutions disclosed in the present invention in detail, further elaboration will be made below in conjunction with the accompanying drawings and embodiments.
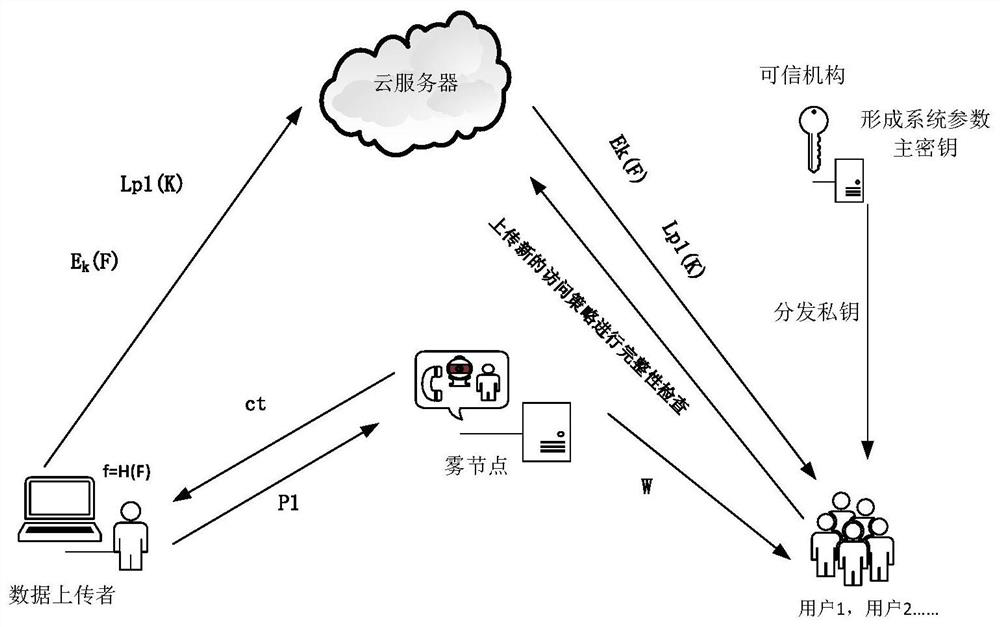
[0043] What the present invention discloses is an extensible access control method oriented to fog computing. The schematic diagram of the model of multi-keyword sortable ciphertext retrieval method oriented to cloud computing is as follows figure 1 As shown, it specifically includes the following steps:
[0044] Step1: Enter security parameters 1 λ , the number of attributes N set in the access policy, the system parameter m and the master key mk are generated by the trusted institution, where the system parameter m is arbitrarily disclosed, and the master key mk is kept by the trusted institution. The specific determination methods include the following:
[0045] The system parameter m is (PG, g, u, g 1 , g 2 ,..., g N , h, g α , e(h, h) α ,(E,D));
[0046] master key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com