An abnormal state checking method and a terminal
An abnormal state and terminal technology, applied in the field of security verification, can solve problems such as the impossibility of passing the chain of trust step by step, and achieve the effect of improving security and credibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
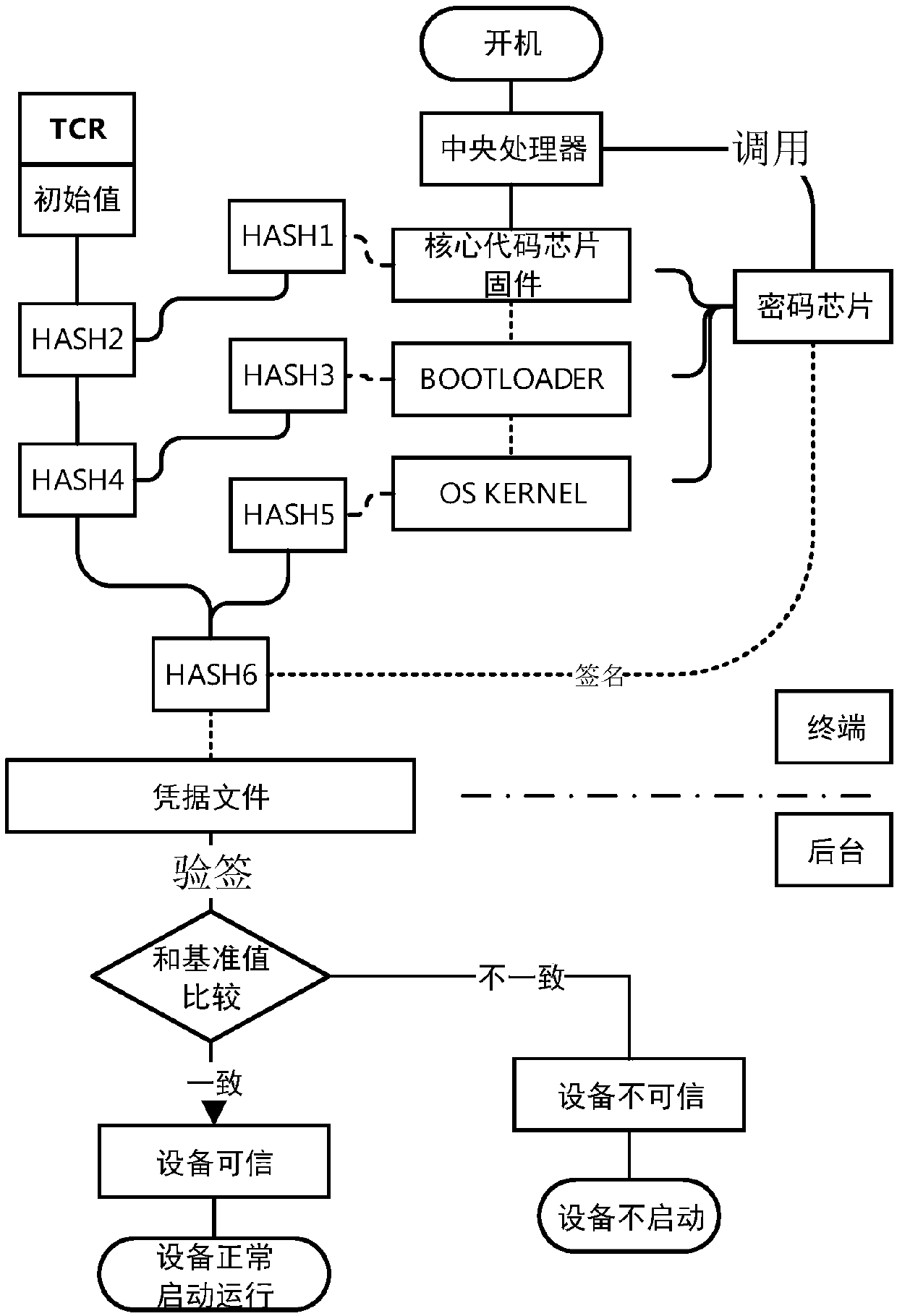
[0031] This embodiment provides a safety verification method, setting the first TCR in the chip of the safety device, please refer to Figure 1-2 , the security verification method, comprising the following steps:
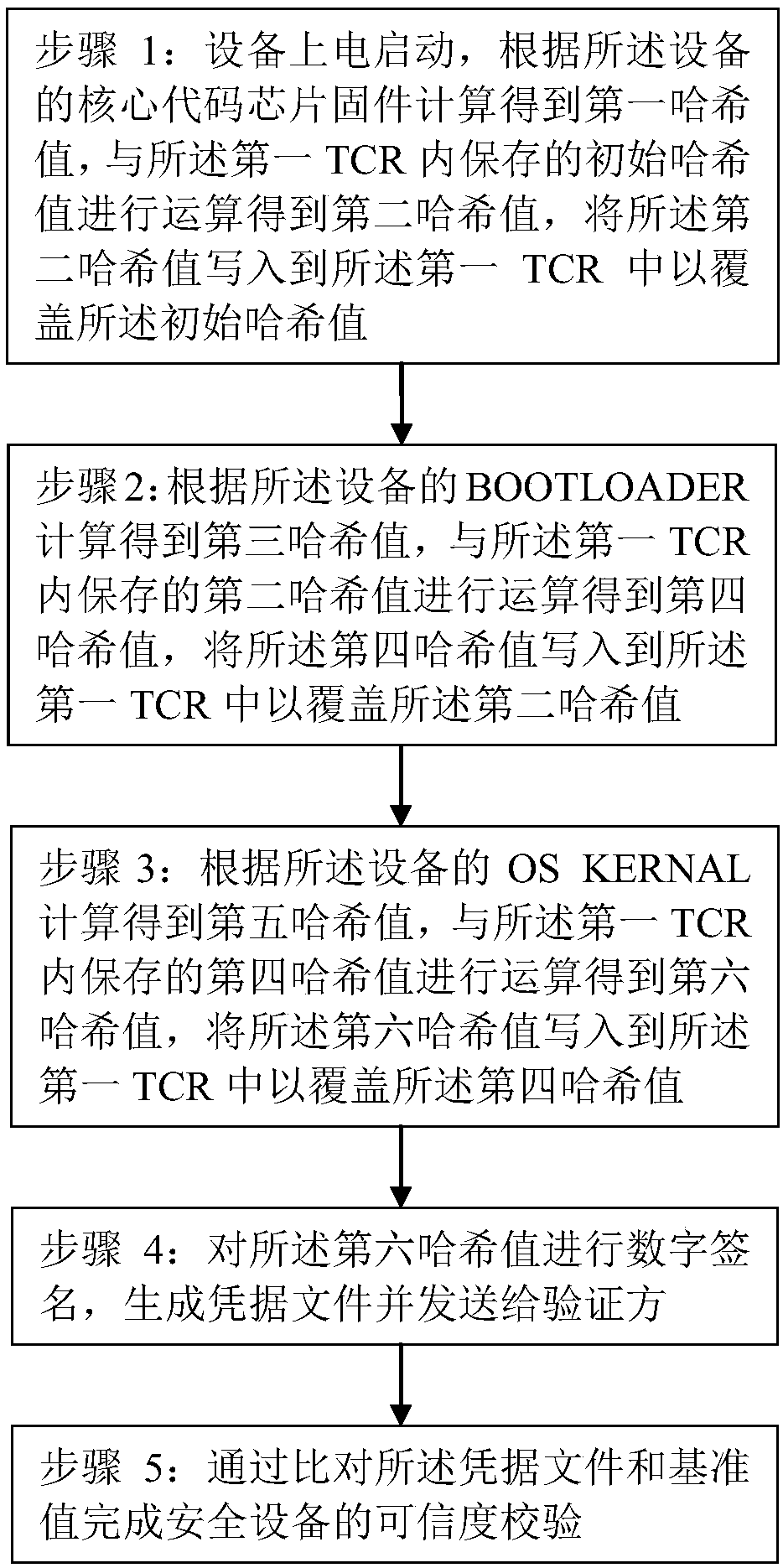
[0032] Step 1: The device is powered on and started, and the first hash value is calculated according to the core code chip firmware of the device, and the initial hash value stored in the first TCR is calculated to obtain the second hash value, and the A second hash value is written into the first TCR to cover the initial hash value.
[0033] Specifically, after the device is started, the central processing unit invokes the cryptographic chip to perform a hash operation on the core code chip firmware to obtain the first hash value, and then converts the initial value in the first TCR to the core code chip firmware through the TCR extension interface. The firmware performs hash operation to obtain the first hash value and performs hash operation together to obtain...
Embodiment 2
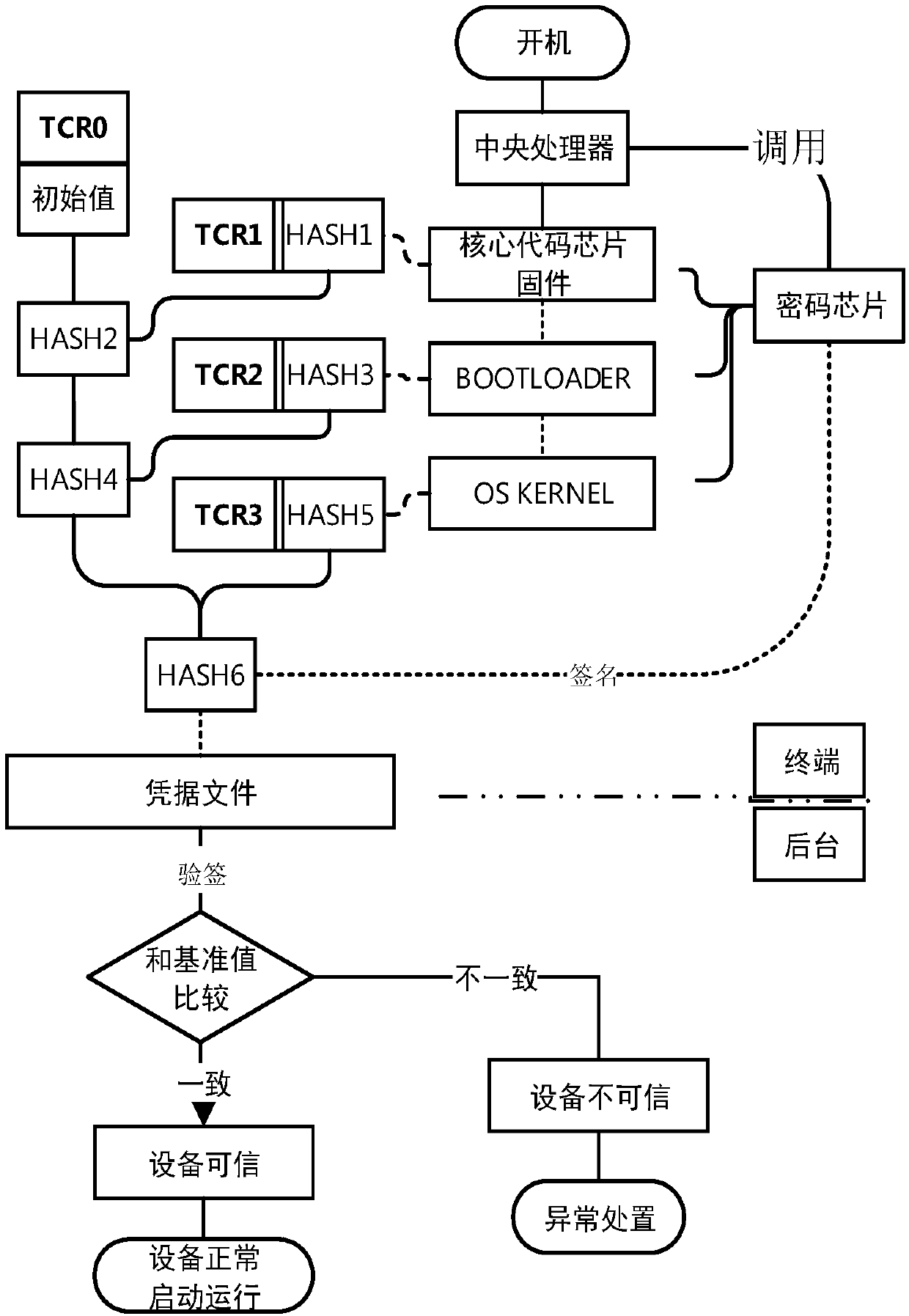
[0047] This embodiment provides another security verification method, setting the first TCR, the second TCR, the third TCR and the fourth TCR in the chip of the security device, please refer to Figure 3-4 , the security verification method, comprising the following steps:
[0048] Step 1: The device is powered on and started, and the first hash value is calculated according to the core code chip firmware of the device, and the initial hash value stored in the first TCR is calculated to obtain the second hash value, and the A second hash value is written into the first TCR to cover the initial hash value, and the first hash value is stored in the second TCR.
[0049] Specifically, after the device is started, the central processing unit invokes the cryptographic chip to perform a hash operation on the core code chip firmware to obtain the first hash value, and then converts the initial value in the first TCR to the core code chip firmware through the TCR extension interface. ...
Embodiment 3
[0066] This embodiment provides another security verification method, setting the first TCR, the second TCR and the third TCR in the chip of the security device, please refer to Figure 5-6 , the security verification method, comprising the following steps:
[0067] Step 1: The device is powered on and started, and the first hash value is calculated according to the core code chip firmware of the device, and the first hash value is written into the first TCR.
[0068] Specifically, after the device is started, the central processing unit invokes the cryptographic chip to perform a hash operation on the core code chip firmware to obtain the first hash value, and then uses the TCR extension interface to perform hash operation on the core code chip firmware to obtain the first hash value. A hash value is stored in the first TCR.
[0069] Specifically, the MD5 algorithm is used to perform the above hash value calculation.
[0070] Step 2: Calculate a second hash value according ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com