Ssh-based data security protection method and device
A technology for data security and protection devices, which is applied to secure communication devices, encryption devices with shift registers/memory, and key distribution, which can solve problems such as unreliable certification of certificates, attacks, and poor feasibility, so as to improve security High performance, easy to build, and strong reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
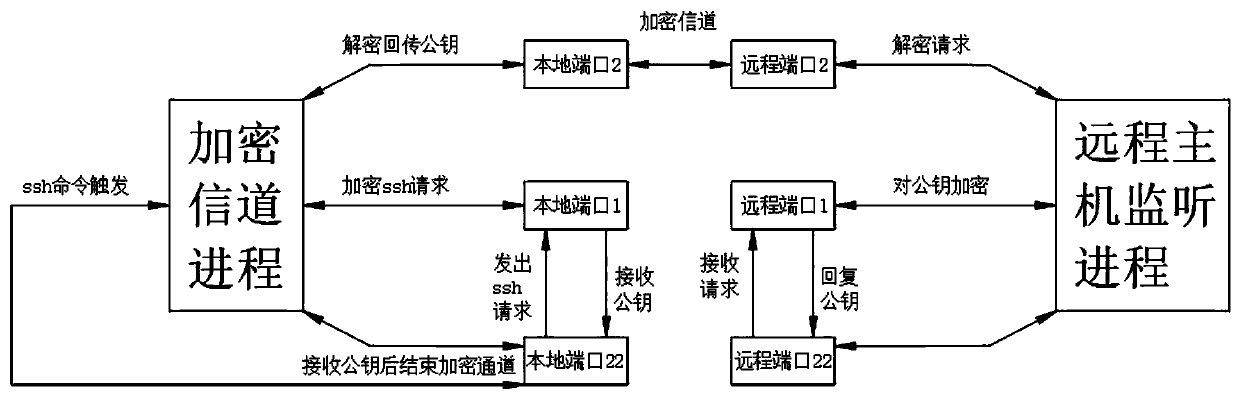
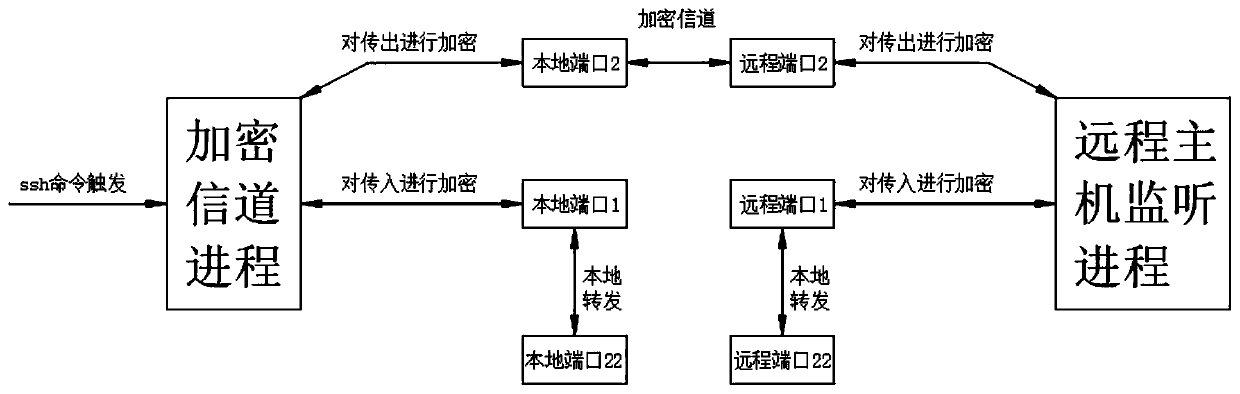
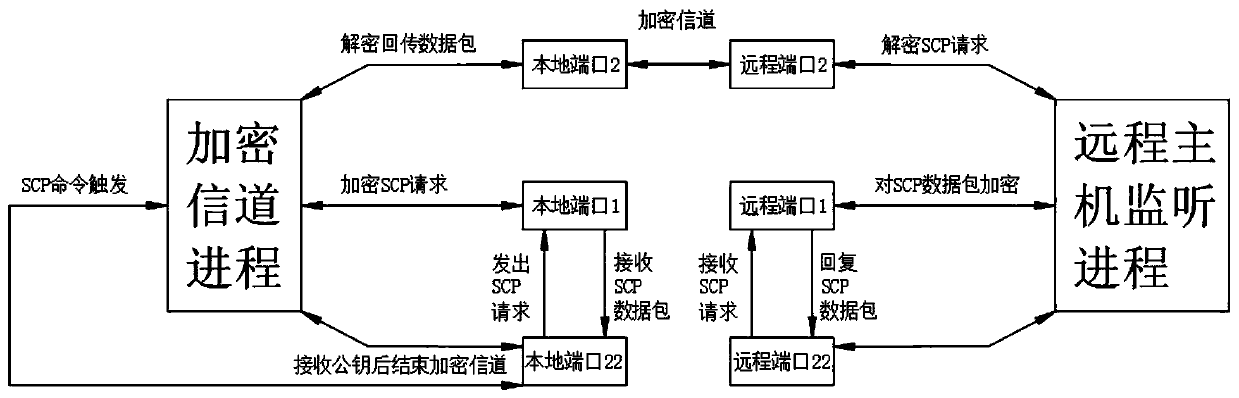
[0036] See Figure 1-3 , The present invention provides the following technical solutions: a data security protection method based on SSH, including the following steps:
[0037] S1, establish an encrypted channel using a one-time password
[0038] S2. Use the configuration file to store the six-digit short password in the remote host in advance to generate the secret key
[0039] S3. Configure a one-time six-digit short password consisting of letters and numbers,
[0040] And use the SHA-1 value of the short password to encrypt the encrypted channel using the ECC algorithm (key encryption)
[0041] S4. Then transmit the key to the client via the encrypted channel (key transmission)
[0042] S5, deploy multiple one-time passwords (key deployment)
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com