Threat information exchange sharing method based on block chain
A blockchain and intelligence technology, applied in transmission systems, instruments, finance, etc., can solve the lack of unified and automated evaluation standards for intelligence supply capabilities, feedback capabilities, and emergency response capabilities, threat intelligence coverage, timeliness, and accuracy. Lack of problems such as lack of threat intelligence assessment effect quantification standards, etc., to achieve the effect of promoting effective utilization and automated transactions, improving automation and objectivity, and promoting effective consumption and high-value utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the purpose, features and advantages of the present invention more obvious and easy to understand, the technical core of the present invention will be further described in detail below in conjunction with the accompanying drawings and examples instruction of.
[0021] In the present invention, a method for exchanging and sharing threat information based on blockchain is proposed.
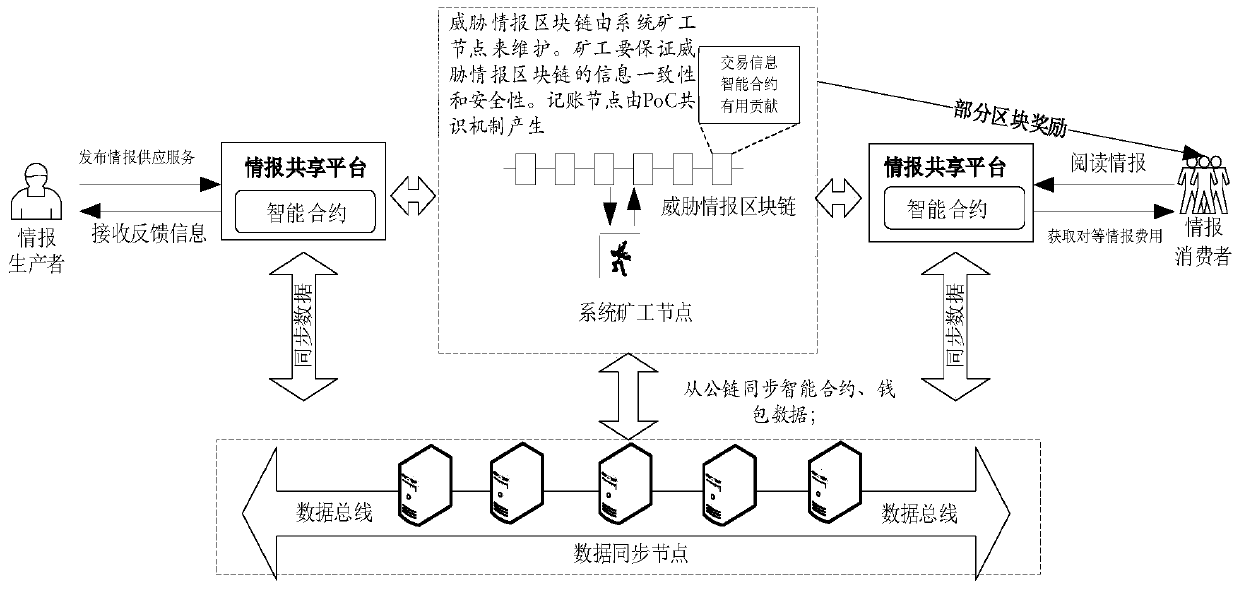
[0022] Such as figure 1 Shown is the overall framework diagram of this method. There are six steps:
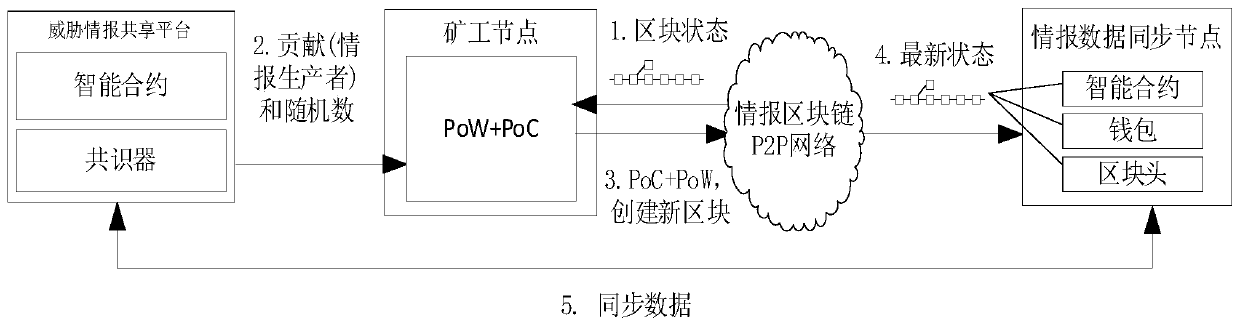
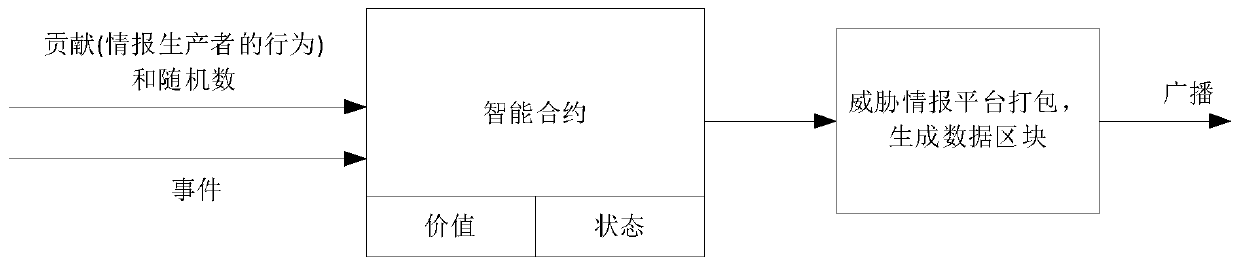
[0023] Step 1. Construct threat intelligence blockchain nodes. In order to solve the problem of low mining efficiency and resource consumption of PoW, the present invention combines the behavior of users of the threat intelligence blockchain system to access the threat intelligence blockchain system (it can be understood that the useful contribut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com