A blockchain-based IoT device identity authentication method
An Internet of Things device and identity authentication technology, which is applied in the field of blockchain-based Internet of Things device identity authentication, can solve problems such as large computing overhead, key distribution, and key leakage, and achieve low overhead requirements, small computing overhead, and The effect of low storage overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be described in detail below with reference to the accompanying drawings and specific embodiments:
[0044] An identity authentication method based on the block chain based on the block chain, including:
[0045] Initialization phase: Select multiple block chain networks to build a block chain network;
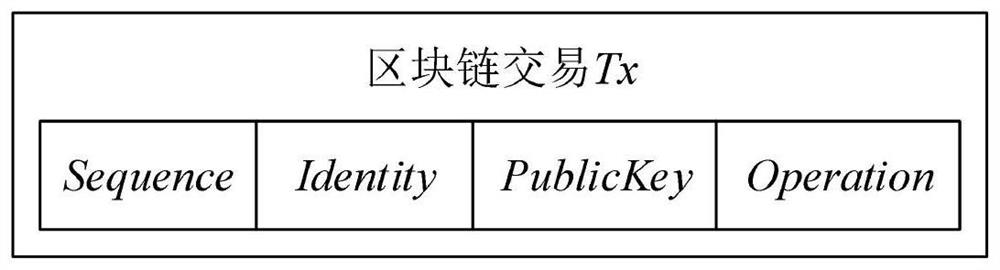
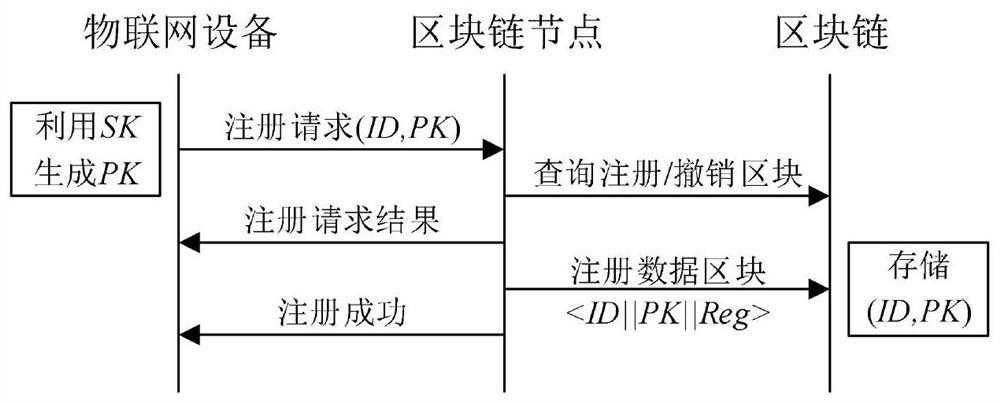
[0046] Registration Stage: Store the identity and public key pair of the Internet of Things devices in the block chain to complete the Internet device registration;
[0047] Authentication phase: The block link node is authenticated according to the stored public key Pk.
[0048] figure 1 A schematic diagram of the system model in the present invention. The block chain node in the system model can be actually acting as a host, server, etc., which is considered to be powerful, and is always secure, the block chain in the present invention is a league chain. The system model running process is: generates information such as the Internet of Things d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com