Log acquisition method, terminal and computer readable storage medium
An acquisition method and log technology, applied in electrical components, transmission systems, etc., can solve problems such as inability to locate and solve network abnormalities, and failure to open wireless network logs in time, so as to improve network experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
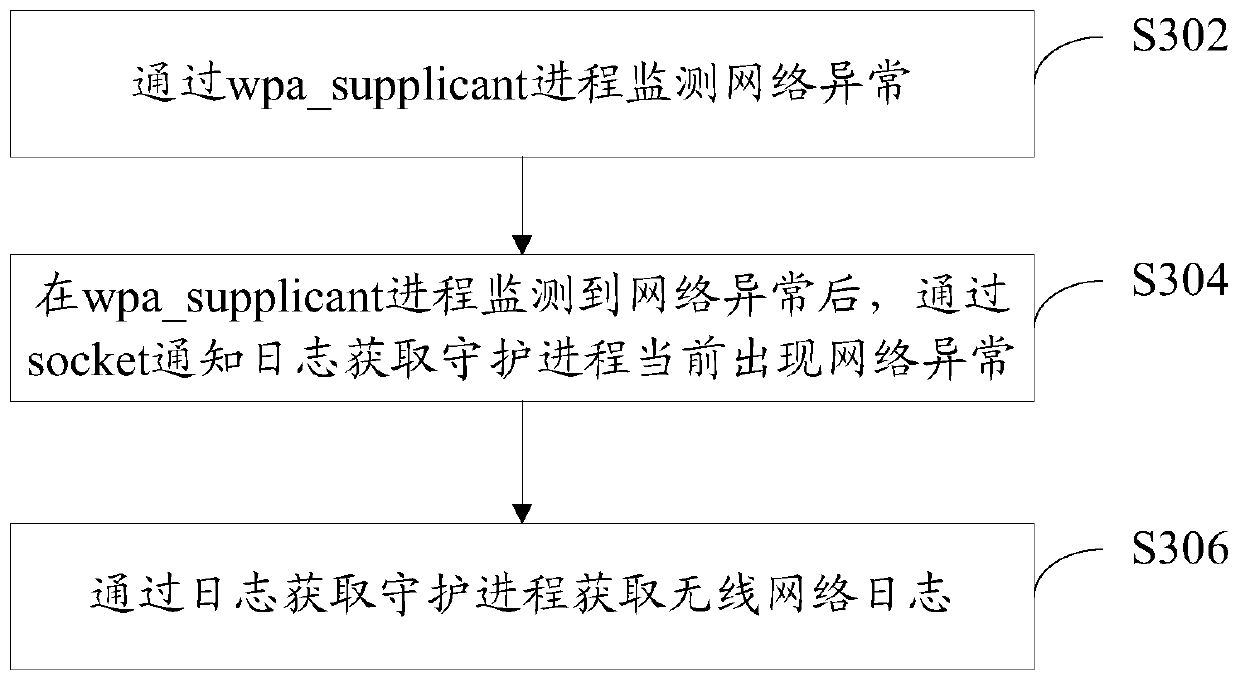
[0067] In order to solve the problem that the opening of the wireless network log in the prior art depends on the manual operation of the user, the wireless network log cannot be opened at the first time after the network abnormality, and the relevant information of the wireless network abnormality cannot be collected in time to provide R&D personnel with the ability to locate and solve problems. Based on the solution to the abnormal problem affecting the wireless network and the problem affecting the user's wireless network experience, this embodiment provides a log acquisition method, image 3 The basic flowchart of the log acquisition method provided in this embodiment:
[0068]S302: Monitor network anomalies through the wpa_supplicant process.
[0069] In the Android (Android) system, there is a wpa_supplicant process. The wpa_supplicant process is an independently running daemon process, and its core is a message loop, which processes WPA state machine, control commands,...
no. 2 example
[0092] In order to make the advantages and details of the log acquisition method provided in the first embodiment clearer to those skilled in the art, this embodiment will further illustrate the log acquisition method with examples, see Figure 7 A flow chart of the log acquisition method shown:
[0093]S702: The wpa_supplicant process performs network monitoring.
[0094] It can be understood that when the wpa_supplicant process monitors the abnormality of the wireless network, as long as one of the two situations of abnormal interruption of the wireless network and abnormal interruption of wireless network access occurs, it can be determined that there is currently an abnormality in the wireless network. Of course, under normal circumstances, these two situations will not occur at the same time.
[0095] Assuming that the terminal in this embodiment is the user's mobile phone, the user connects the mobile phone to the WiFi hotspot "11-12" at home, and then accesses the netw...
no. 3 example
[0114] This embodiment will provide a computer-readable storage medium and a terminal. First, the computer-readable storage medium will be introduced:
[0115] The computer-readable storage medium stores one or more computer programs that can be read, compiled or executed by the memory, including a log acquisition program, and the display control program can be executed by a processor to realize the first or second embodiment The log acquisition method provided in .
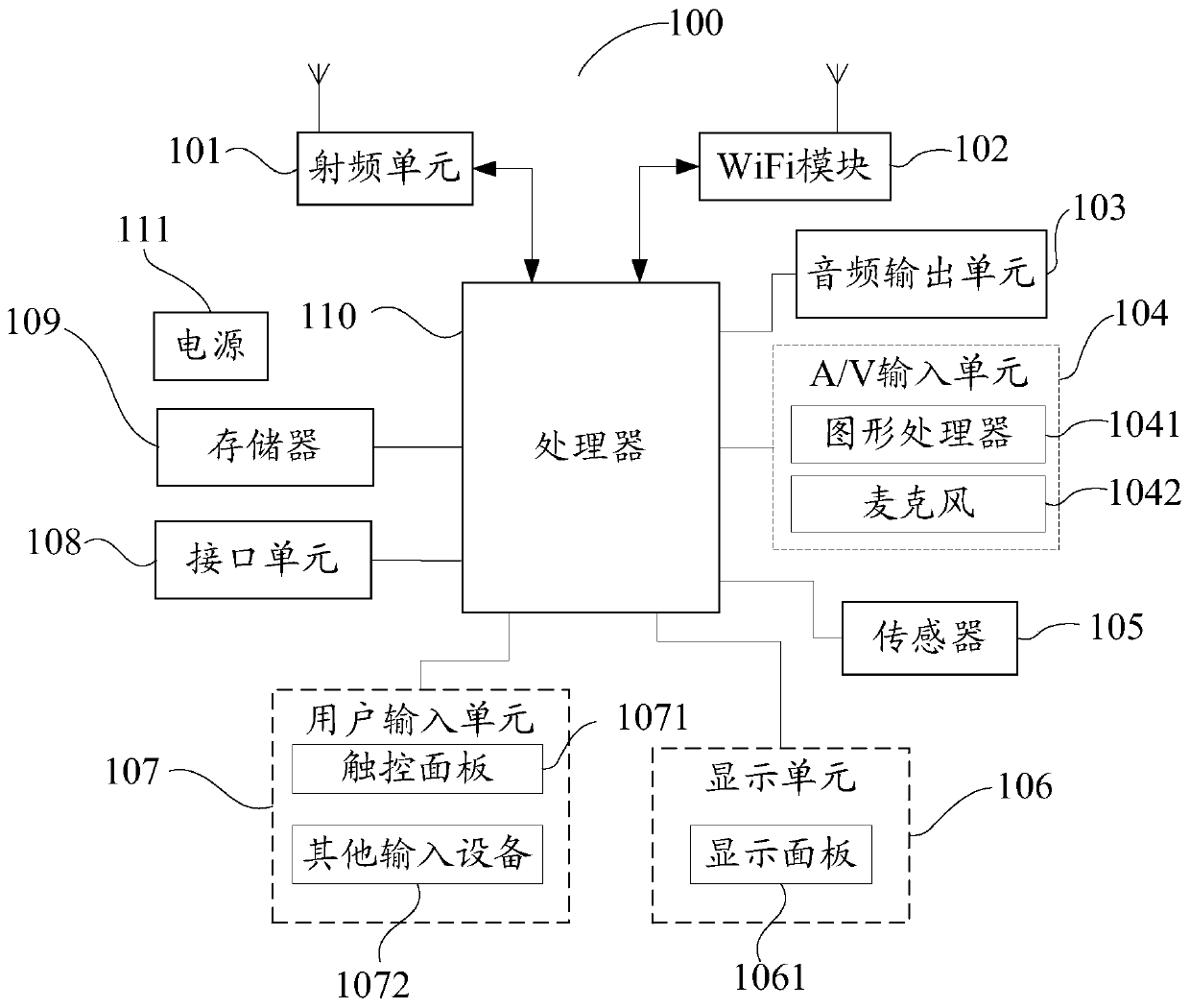
[0116] See Figure 8 Provided schematic diagram of the hardware structure of the terminal: the terminal 80 includes a processor 81, a memory 82, and a communication bus 83 for connecting the processor 81 and the memory 82, wherein the memory 82 can be the aforementioned computer-readable storage medium storing the log acquisition program. The processor 81 of the terminal 80 can execute the log acquisition program stored in the memory 82 to implement the log acquisition method in the foregoing embodiments:
[01...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com