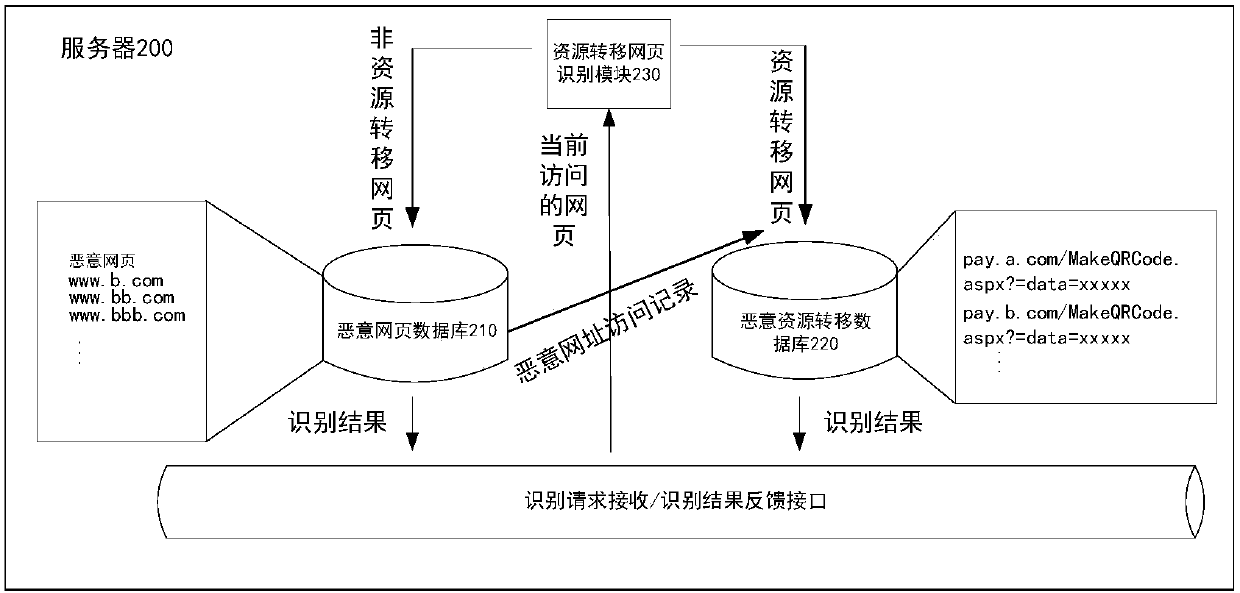
Malicious resource transfer webpage identification method and device
A technology of resource transfer and malicious web pages, applied in the field of network security, can solve the problems of low recognition efficiency and achieve the effect of improving recognition efficiency, timeliness and coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0032] The "plurality" mentioned herein means two or more. "And / or" describes the association relationship of associated objects, indicating that there may be three types of relationships, for example, A and / or B may indicate: A exists alone, A and B exist simultaneously, and B exists independently. The character " / " generally indicates that the contextual objects are an "or" relationship.
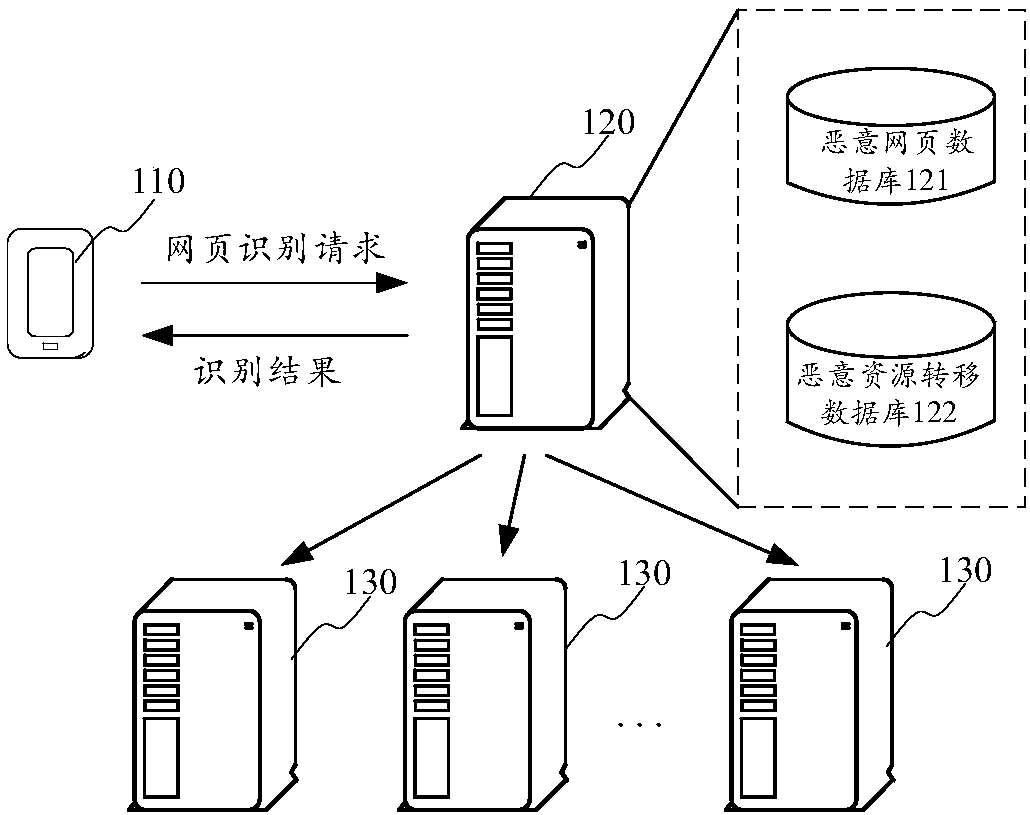
[0033] Please refer to figure 1 , which shows a schematic diagram of an implementation environment provided by an embodiment of the present invention, where the implementation environment includes a terminal 110 and a server 120 .
[0034] Terminal 110 is an electronic device having an Internet access function. The electronic device is played by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com