Upgrade package encryption and decryption method, electronic device and storage medium
An encryption method and upgrade package technology, applied in security devices, electrical components, wireless communications, etc., can solve problems such as large memory dependence, affecting upgrade efficiency, and inapplicability to models with lower configuration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0047] This embodiment shows an encryption method for an upgrade package, which can realize fast encryption of the upgrade package, shorten the encryption time, and also reduce the dependence of the upgrade package decryption on the memory of the electronic device when the electronic device uses the upgrade package, and shorten the decryption time. Time to improve upgrade efficiency.
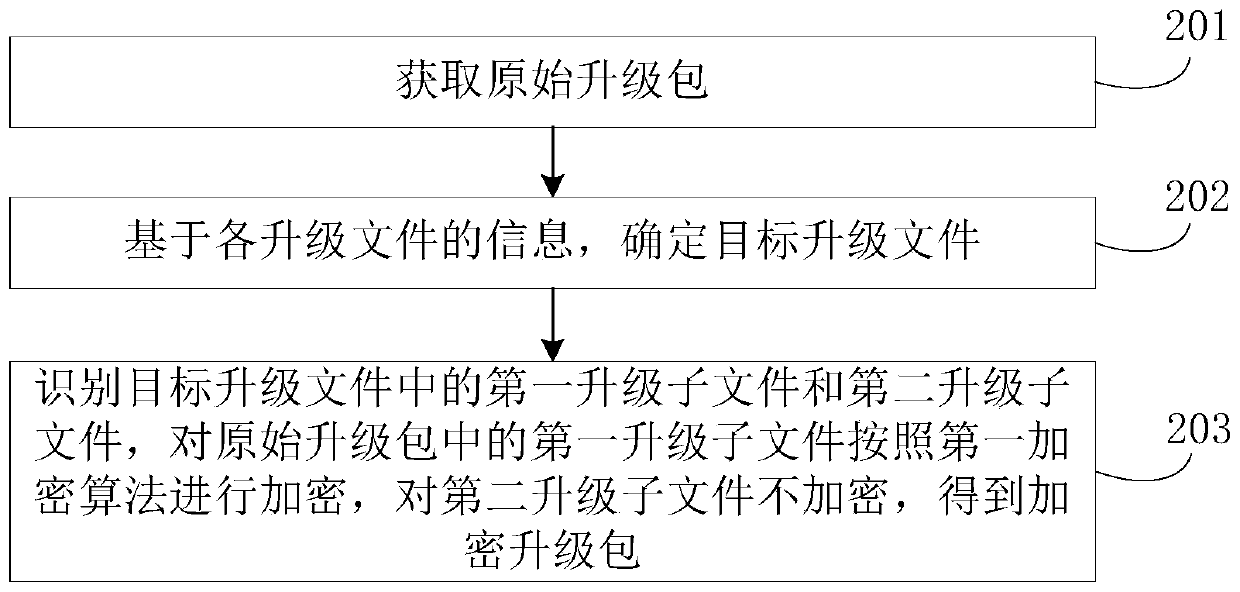
[0048] see figure 2 , the encryption method of the upgrade package includes:
[0049] Step 201, obtaining an original upgrade package, wherein the original upgrade package includes upgrade files of each partition to be upgraded of the operating system;
[0050] In this embodiment, the operating system applicable to the original upgrade package includes, but is not limited to, the Android system. Types of original upgrade packages include but are not limited to OTA upgrade packages. It can be understood that the original upgrade package in this embodiment is an uncompressed upgrade package. ...
no. 2 example
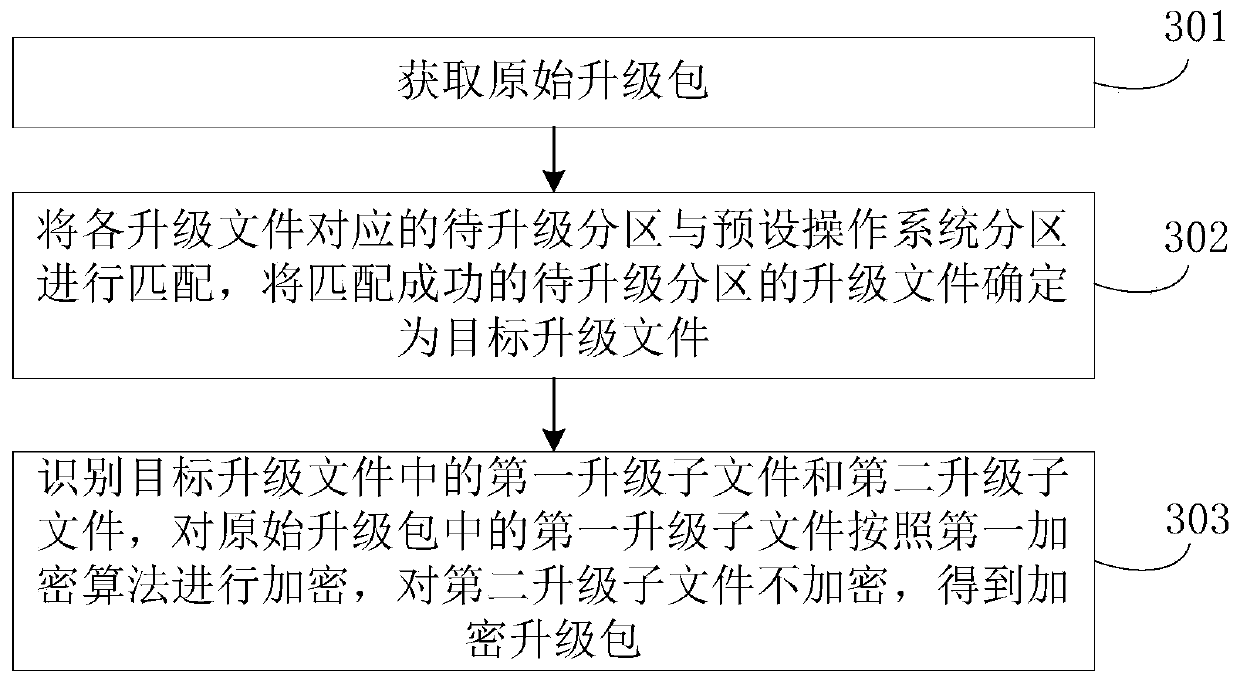
[0063] This embodiment proposes a refined encryption method for the upgrade package, see image 3 , the encryption method includes:
[0064] Step 301. Obtain the original upgrade package, wherein the original upgrade package contains the upgrade files of each partition to be upgraded;
[0065] In this embodiment, for the explanation of the original upgrade package, the operating system partition and the upgrade file, refer to the related description of the first embodiment, and this embodiment will not be repeated here.
[0066] Step 302, matching the partition to be upgraded corresponding to each upgrade file with the preset operating system partition, and determining the upgrade file of the successfully matched partition to be upgraded as the target upgrade file;
[0067] Optionally, in an example, the preset operating system partitions include but are not limited to system partitions and vendor partitions.
[0068] Optionally, in one embodiment, in step 302, the target up...
no. 3 example
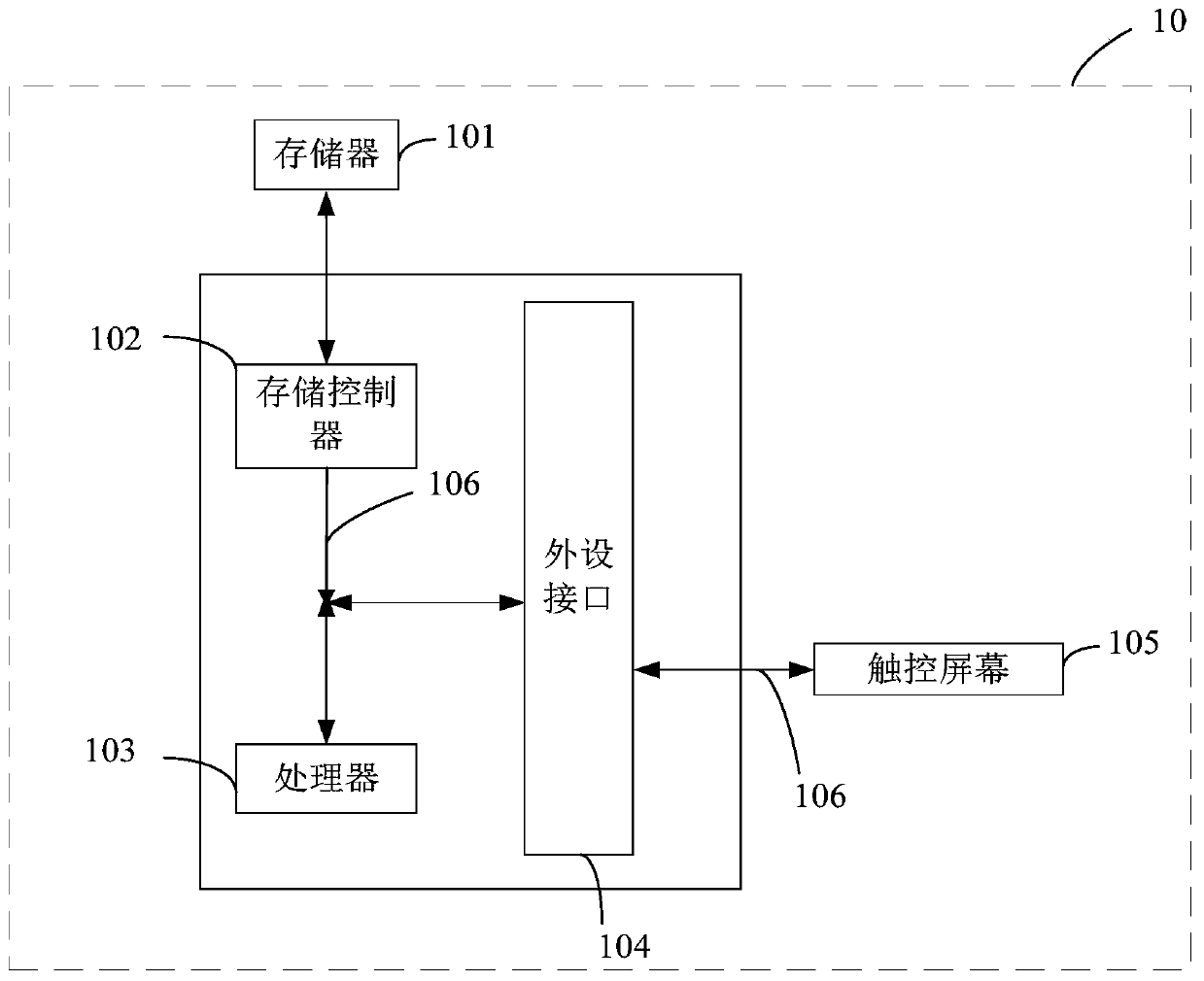
[0100] This embodiment provides an electronic device, which may be a server provided by an electronic device manufacturer, see Figure 5 , the electronic device includes:
[0101] The first acquiring module 501 is configured to acquire an original upgrade package, wherein the original upgrade package includes upgrade files of each partition to be upgraded of the operating system;
[0102] The first determination module 502 is configured to determine the target upgrade file based on the information of each upgrade file;
[0103] An encryption module 503, configured to identify the first upgrade subfile and the second upgrade subfile in the target upgrade file, encrypt the first upgrade subfile in the original upgrade package according to the first encryption algorithm, and not encrypt the second upgrade subfile Encrypt to obtain an encrypted upgrade package, wherein the second upgrade subfile contains data to be written into the partition to be upgraded of the operating system...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com