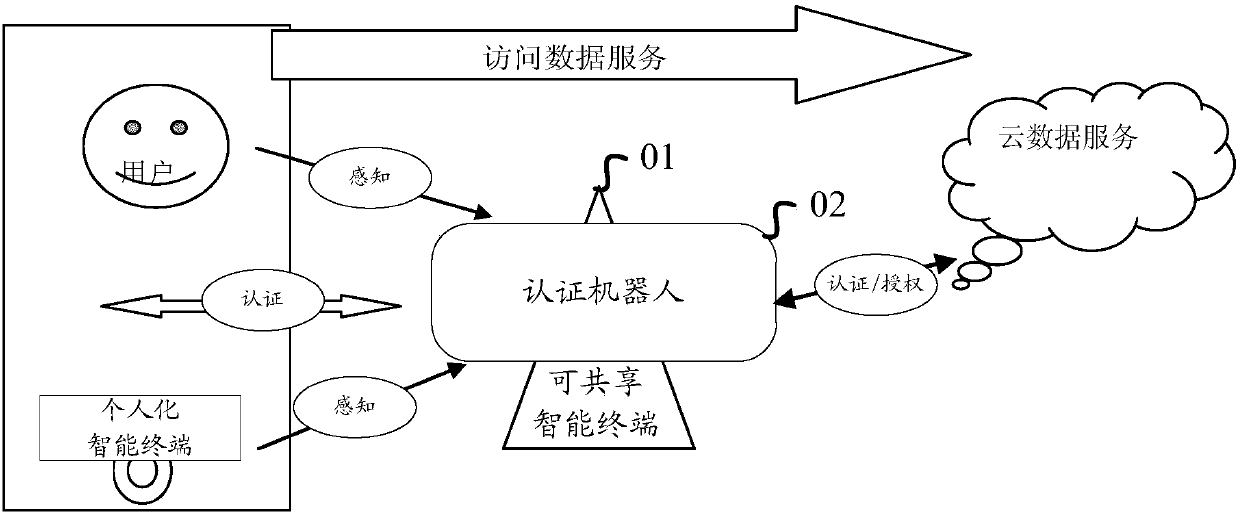
Identity authentication method, device, medium, robot and system
An identity authentication and identity information technology, applied in the field of intelligent terminals, can solve the problems of cumbersome user operations, inability to obtain personalized data, and ineffective record protection of personalized data, so as to reduce complexity, protect privacy and data. effect of personality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
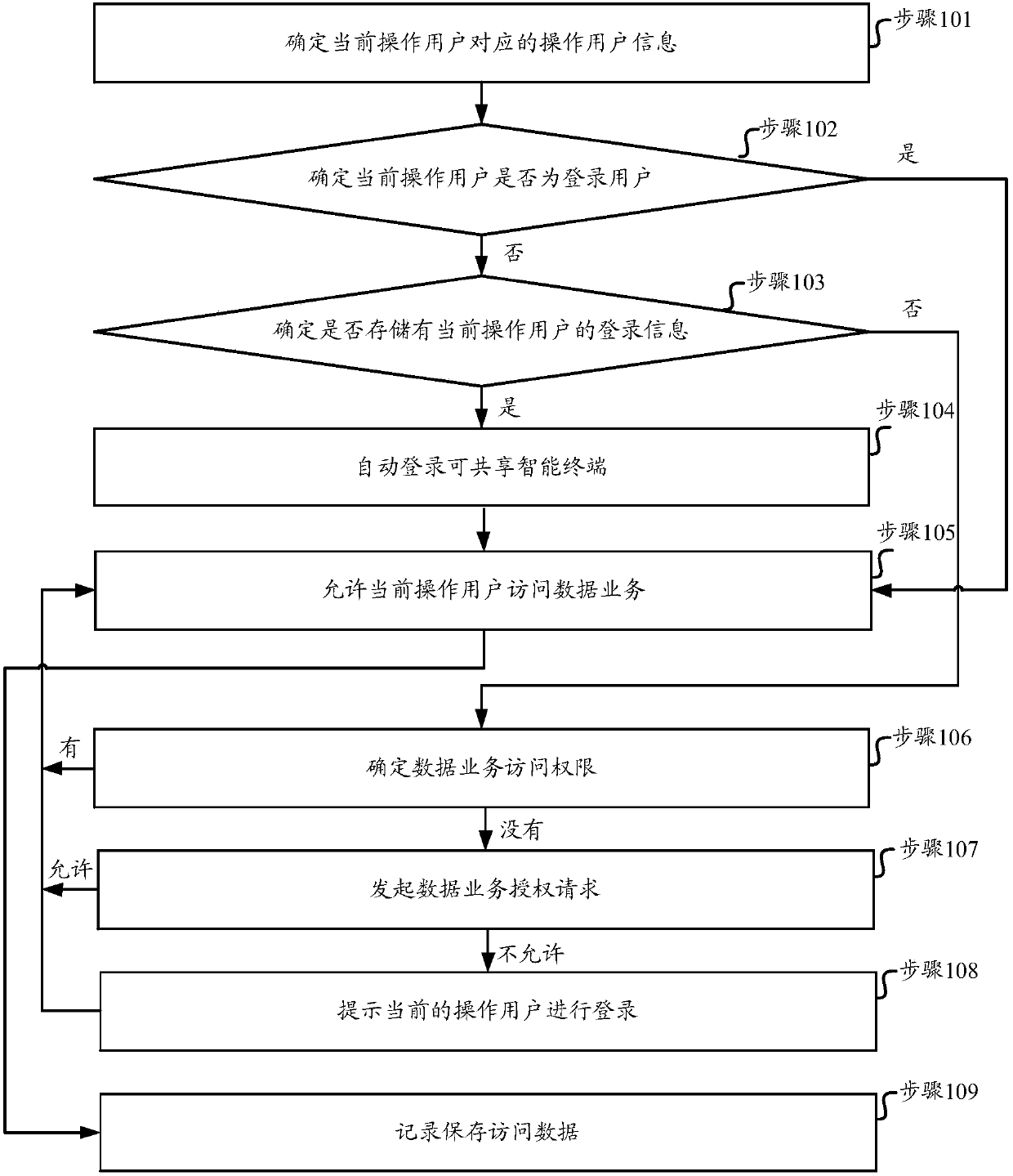
[0049] Such as figure 2 As shown, it is a flow chart of an identity authentication method for a shareable smart terminal provided in Embodiment 1 of the present invention. The method includes the following steps:
[0050] Step 101. Determine the operating user information corresponding to the current operating user.
[0051] In this step, when receiving the access data service request sent by the operating user of the sharable smart terminal, the operating user information corresponding to the operating user is determined, and the operating user information is information capable of identifying the characteristics of the operating user.
[0052] Since the operating users will basically use the personalized smart terminal, it is possible to establish a correspondence between the personalized smart terminal identifier and the operating user. In various embodiments of the present invention, the operating user information may include a personalized smart terminal identifier.
...
Embodiment 2
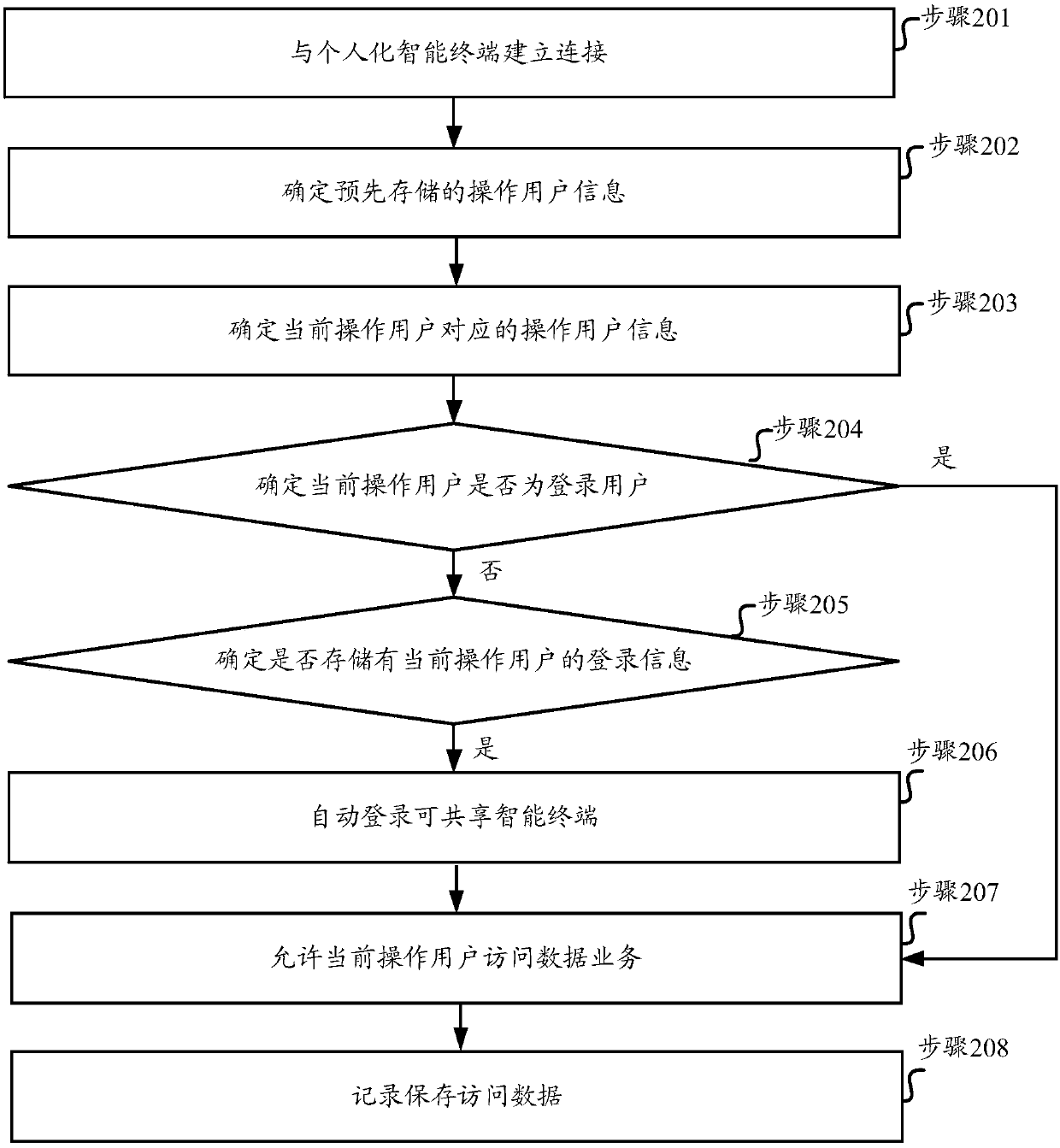
[0098] Embodiment 2 of the present invention provides an identity authentication method oriented to a shareable smart terminal, and the flow chart of the steps of the method can be as follows image 3 As shown, the method includes:
[0099] Step 201, establish a connection with a personalized smart terminal.
[0100] In this step, a connection can be established with a personalized smart terminal within a specified range.
[0101] The operation of establishing a connection with a personalized smart terminal can be performed regularly, for example, once every two hours, or it can be triggered, for example, when the user clicks a set button, it can be triggered once, or it can be continuously detected. As long as it is found that there is a personalized smart terminal that has not been connected, a connection is established with the personalized smart terminal. In this way, the operating user information can be continuously determined, the stored operating user information can...
Embodiment 3
[0148] Such as Figure 4 As shown, it is a schematic structural diagram of an identity authentication device oriented to a shareable smart terminal provided in Embodiment 3 of the present invention, and the device includes:
[0149] The first determining module 11 is used to determine the operating user information corresponding to the operating user when receiving the access data service request sent by the operating user of the sharable smart terminal, and the operating user information is information that can identify the characteristics of the operating user; the second The determining module 12 is used to determine whether the current operating user is a logged-in user according to the operating user information determined by the first determining module 11, and the operating user information corresponding to the logged-in user in the pre-stored operating user information; the third determining module 13 If the second determination module 12 determines that the current op...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com