Electronic signature method and system for a fire checklist
An electronic signature and checklist technology, which is applied in the fields of electrical digital data processing, data processing applications, instruments, etc., can solve the problem that the fire checklist does not have legal effect, and achieve the effect of improving enthusiasm.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
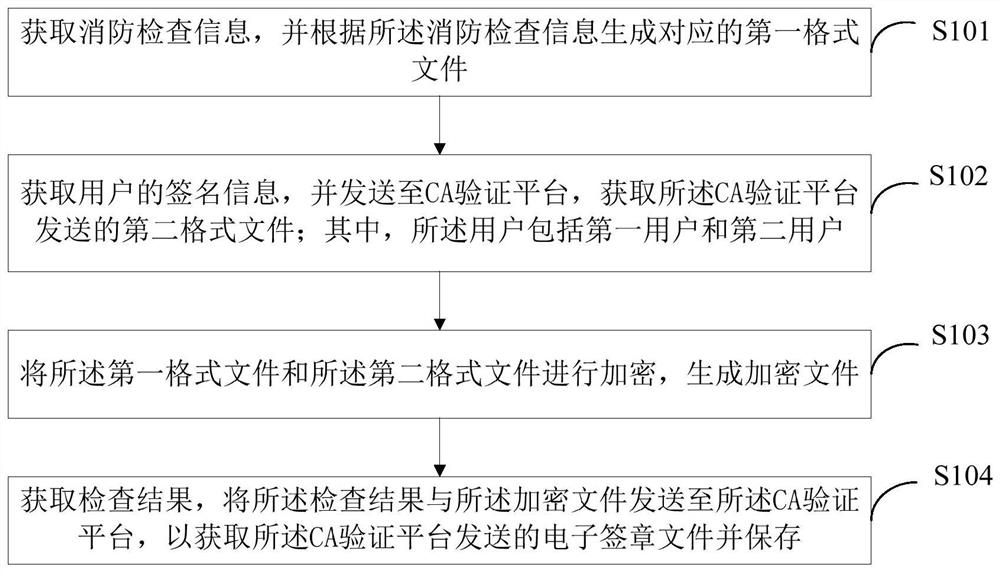
[0063] Such as figure 1 As shown, this embodiment provides a method for electronically signing a fire checklist, which can be applied to terminal devices such as mobile phones, PCs, and tablet computers. The electronic signature method of the fire checklist provided by this embodiment includes:
[0064] S101. Acquire fire inspection information, and generate a corresponding first format file according to the fire inspection information.
[0065] In a specific application, the fire inspection information input by the user is obtained, and a corresponding first format file is generated according to the input fire inspection information; wherein, the user includes the first user and the second user; in this embodiment, the first user and the second user The second user is the grid operator and operator of the fire monitoring grid, or the first user and the second user can be set as other fire inspection users; fire inspection information includes but not limited to whether the f...
Embodiment 2
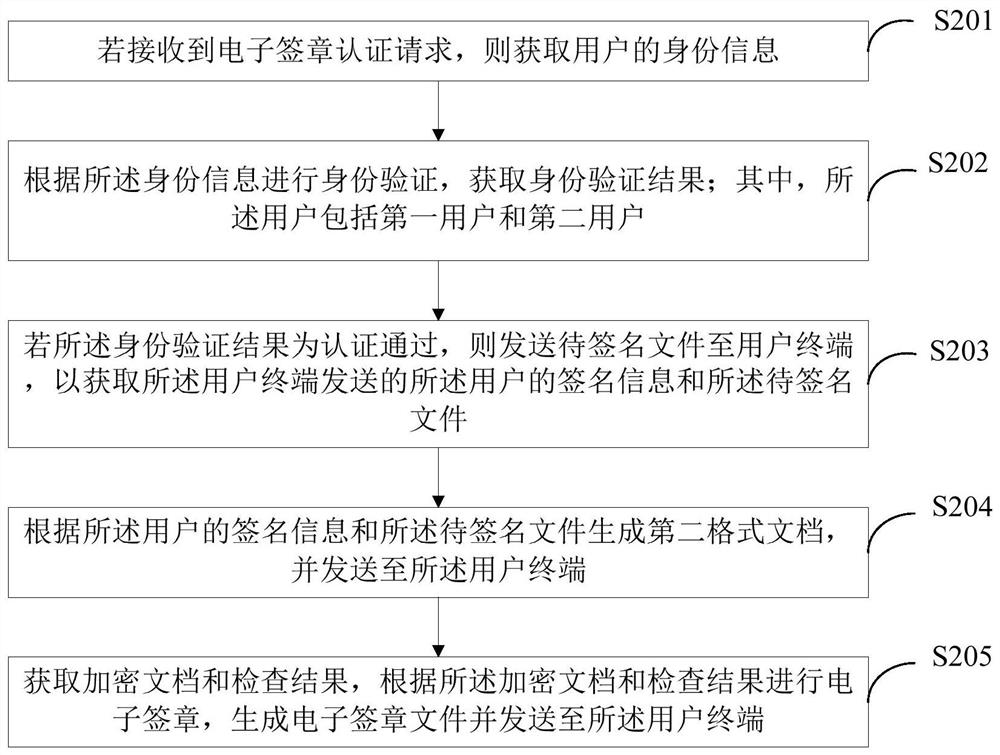
[0083] Such as figure 2 As shown, this embodiment is a further description of the method steps in the first embodiment. In this embodiment, the electronic signature method of the fire checklist can be applied to terminal devices such as a CA verification platform. The electronic signature method of the fire checklist also includes:
[0084] S201. Obtain the identity information of the user if an electronic signature authentication request is received.
[0085] In a specific application, if the electronic signature authentication request sent by the user terminal is received, the user's identity information is obtained to verify the user's identity information; wherein, the user's identity information includes but is not limited to ID number, identity card At least two of photos, names, fingerprints, image data or audio data, wherein the users include the first user and the second user, in this embodiment, the first user and the second user are grids of the fire monitoring g...
Embodiment 3
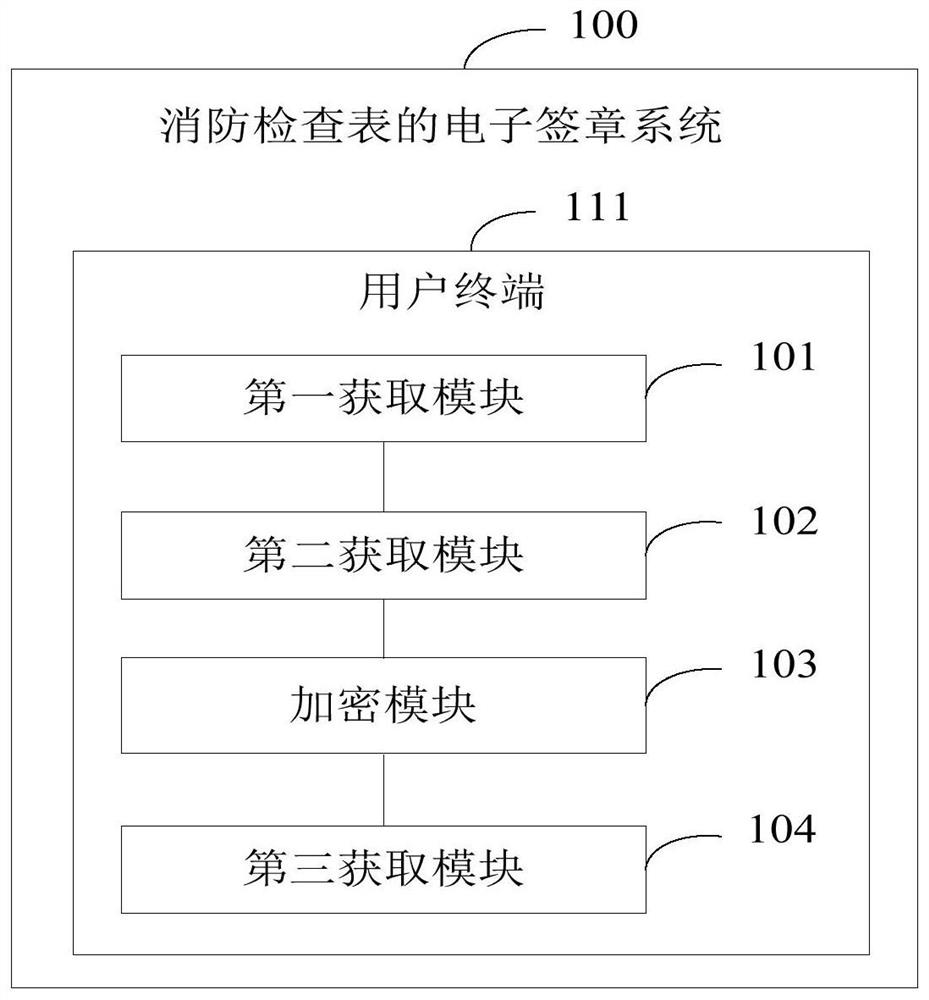
[0103] Such as image 3 As shown, this embodiment provides an electronic signature system 100 for a fire checklist, which is used to execute the method steps in Embodiment 1. The electronic signature system 100 of the fire checklist provided in this embodiment includes a user terminal 111 and a CA authentication platform, and the user terminal 111 includes:
[0104] The first acquiring module 101 is configured to acquire fire inspection information, and generate a corresponding first format file according to the fire inspection information;
[0105] The second obtaining module 102 is used to obtain the signature information of the user, and send it to the CA verification platform, and obtain the second format file sent by the CA verification platform; wherein, the user includes the first user and the second user;
[0106] An encryption module 103, configured to encrypt the first format file and the second format file to generate an encrypted file;
[0107] The third obtainin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com