Network request control method, terminal and computer readable storage medium
A network request and control method technology, applied in the field of communication, can solve problems such as easy-to-access advertisements, pornography, fraud, untimely network requests, and network speed shunt effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
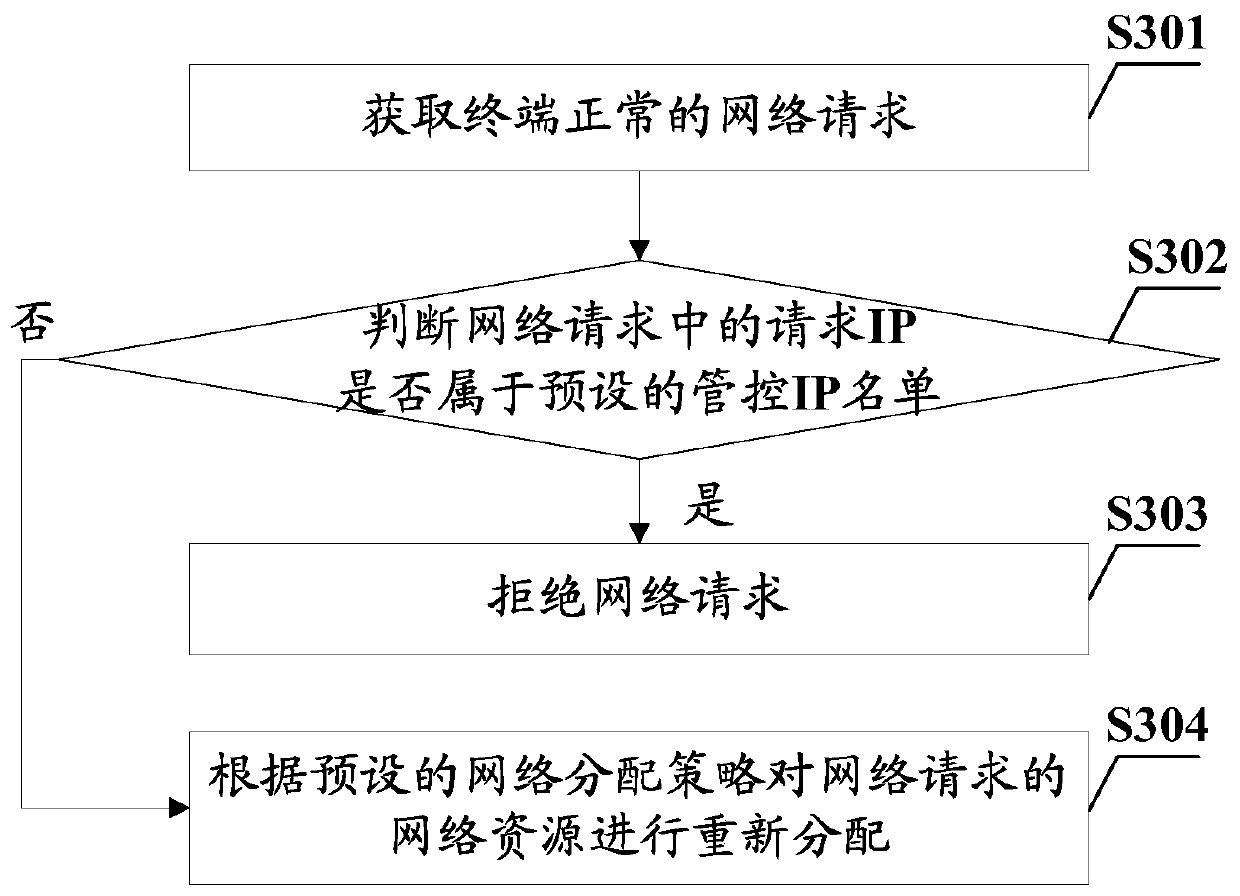
[0079] In order to solve the problem that existing smart terminals are easy to access "package" websites such as advertisements, pornography, and fraud when surfing the Internet, and the influence of network speed shunt caused by website access to background services or vicious downloads, resulting in untimely network requests, this embodiment provides A network request control method such as image 3 as shown, image 3 The basic flow chart of the network request control method provided in this embodiment, the network request control method includes:
[0080] S301. Obtain a normal network request of the terminal.
[0081] It is understandable that when users need to query content, they will visit some websites through the terminal, and the access method can be a dedicated webpage, such as "browser"; it can also be a webpage accessed through a certain application, such as "micro Bo” jumps to the web page.
[0082] In this embodiment, in the network request process, the termi...
no. 2 example
[0102] For ease of understanding, this embodiment provides a network request control method, such as Figure 6 As shown, the network request control method includes:
[0103] S601. Obtain a normal network request of the terminal.
[0104] In this embodiment, the ways to obtain network requests include but are not limited to special network requests for accessing webpages and network requests for application jumps. There may be one network request or multiple network requests, and one network request corresponds to the request IP.
[0105] S602. Determine whether the requested IP in the network request belongs to the preset control IP list, if yes, go to S603, if not, go to S605.
[0106] The terminal stores a control IP list in advance, and the terminal restricts the IP network in the control IP list. The IPs in the control IP list are "junk" IPs such as fraud, pornography, advertising, and phishing, which are set by the terminal according to the user's historical network acc...
no. 3 example
[0123] In order to facilitate understanding, this embodiment uses a more specific example to describe the network request control method, such as Figure 7 As shown, the network request control method includes:
[0124] S701. Obtain a normal network request of the terminal.
[0125] S702. Determine whether the requested IP in the network request belongs to the preset control IP list, if yes, go to S703, if not, go to S705.
[0126] During the request process, the system obtains the request IP through the network data packet, and matches it with the control IP list IPList (hereinafter referred to as IPList) maintained in the system to determine whether it belongs to the IPList.
[0127] S703. Determine whether a cancel instruction to cancel the restricted IP is received within the preset time period, if not, go to S704, if yes, go to S707.
[0128] If the currently requested IP exists in the IPlist, then the user is asked whether to cancel the restriction on the current IP, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com